Patents
Literature
154results about How to "Normal access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
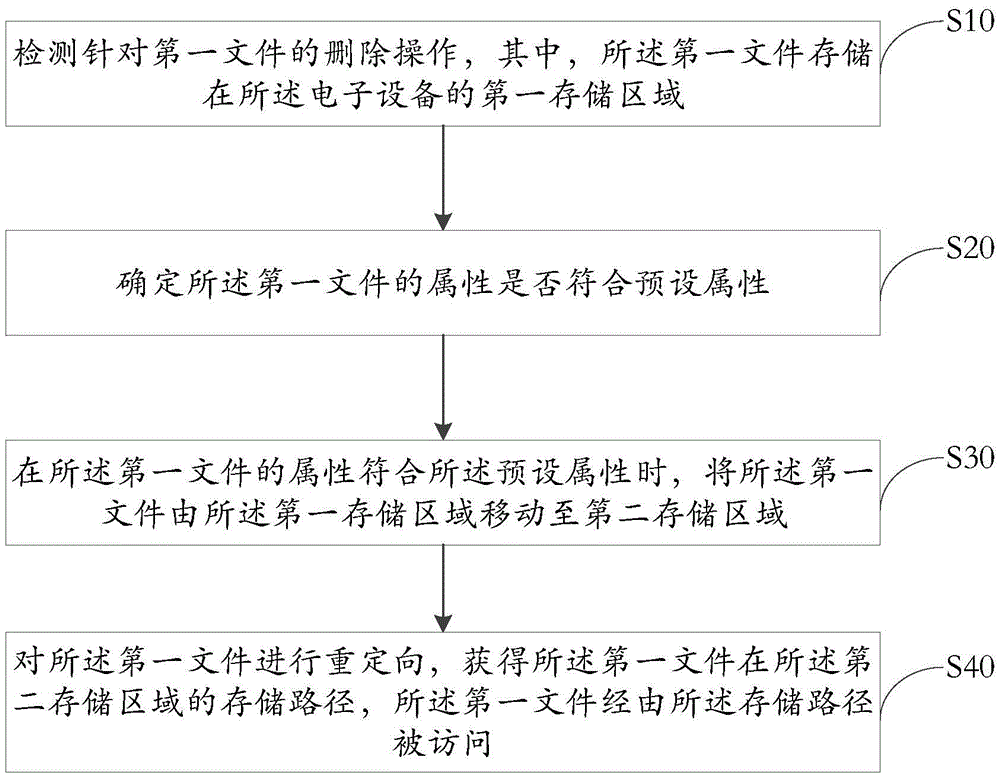
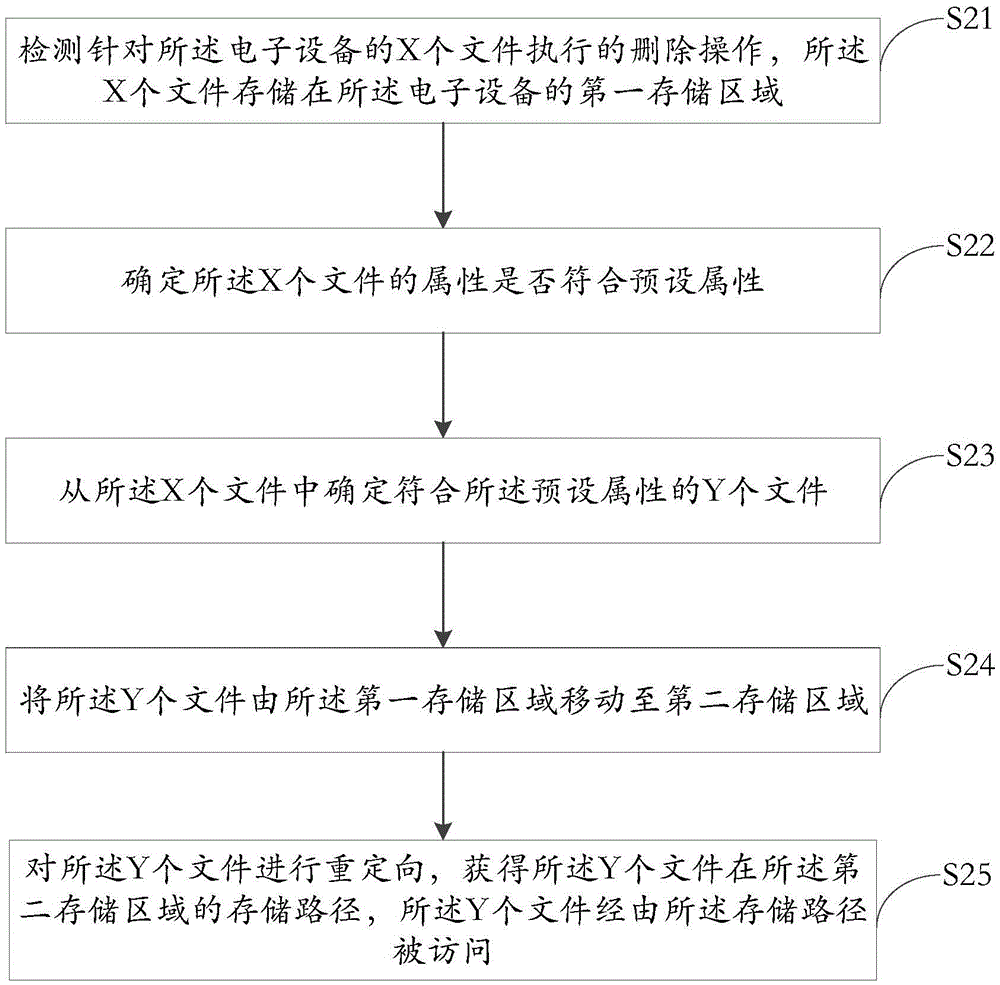
File management method of electronic equipment and electronic equipment
InactiveCN105653582ANormal accessRealize temporary storageSpecial data processing applicationsElectronic equipmentFile storage
The invention discloses a file management method of electronic equipment and the electronic equipment. The method comprises the following steps: detecting a deletion operation in allusion to a first file, wherein the first file is stored in a first storage area of the electronic equipment; determining whether the attribute of the first file accords with a preset attribute; when the attribute of the first file accords with the preset attribute, moving the first file from the first storage area to a second storage area; and redirecting the first file to obtain a storage path of the first file in the second storage area, wherein the first file is accessed through the storage path. The method provided by the invention is used for solving the technical problem that related applications cannot run normally as the files cannot be accessed after being deleted, so that the technical effect that the deleted files are temporarily stored and then the related applications still can normally access to the files is realized.
Owner:LENOVO (BEIJING) CO LTD
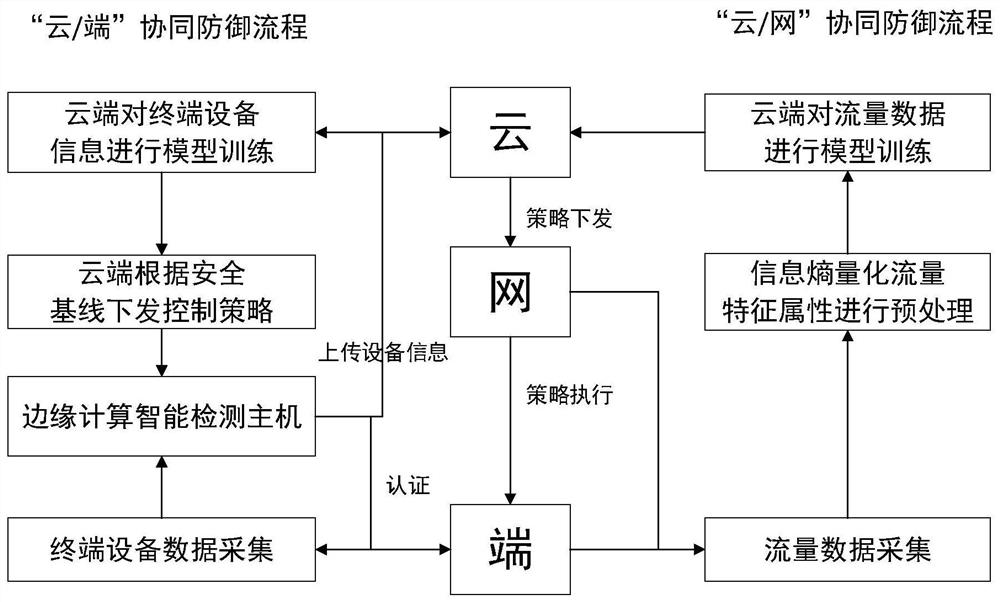
Cloud network end cooperative defense method and system based on end-side edge computing
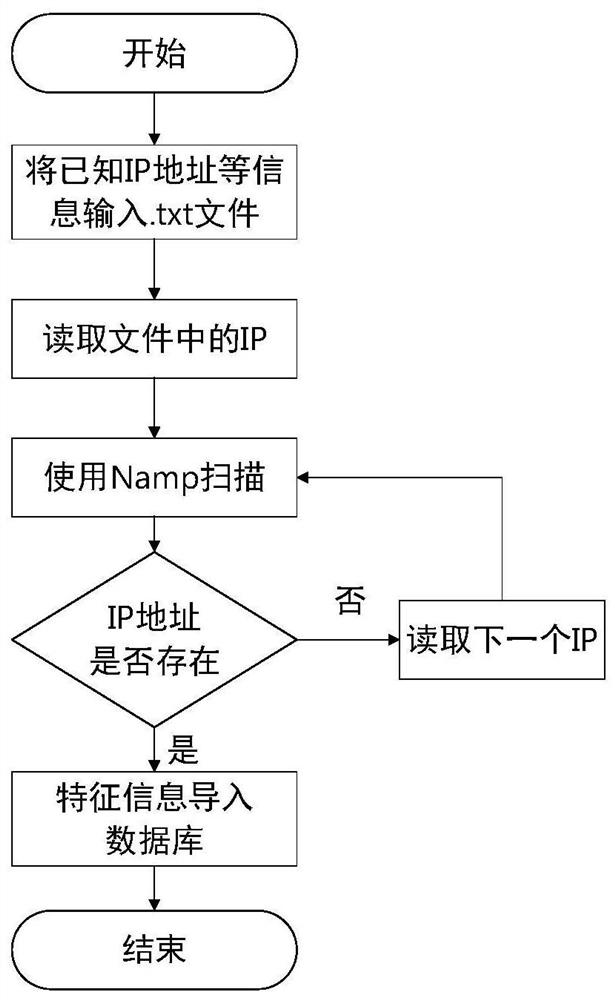
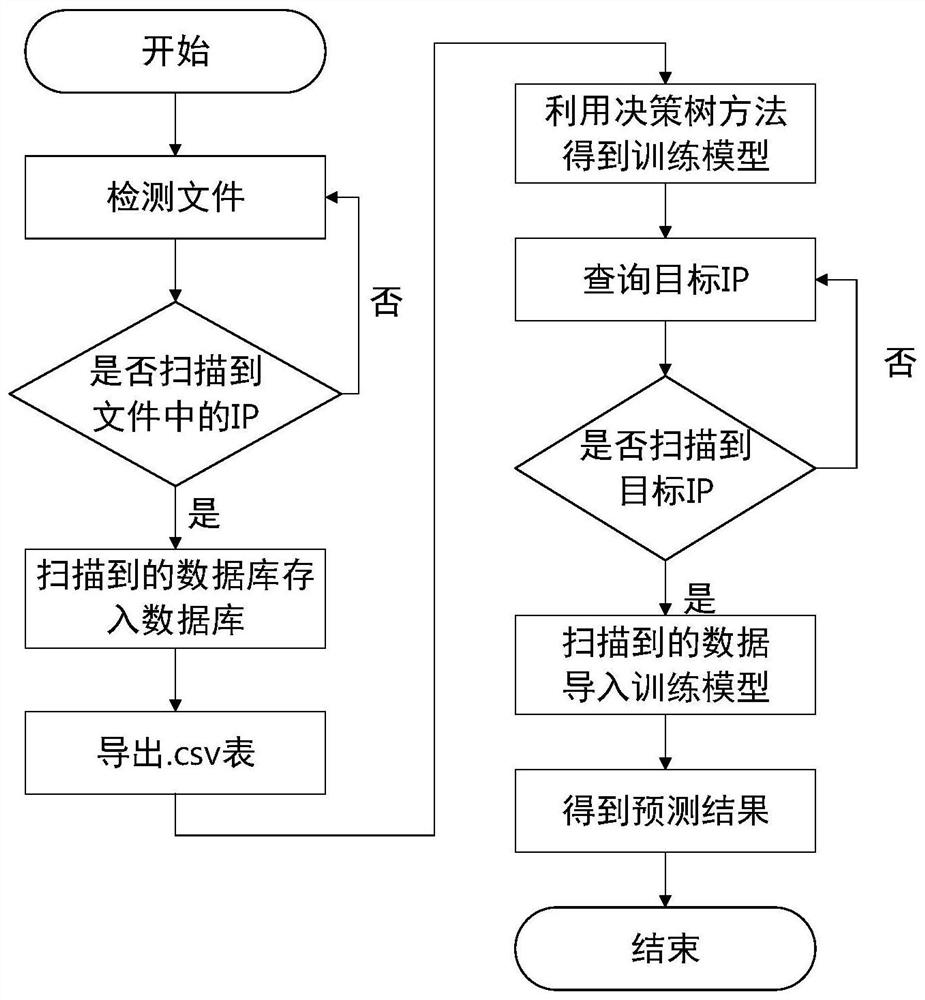
ActiveCN112769796AReal-time detectionGuaranteed uptimeCharacter and pattern recognitionMachine learningSimulationData acquisition
The invention discloses a cloud network end cooperative defense method and system based on end-side edge computing, and relates to information security of an electric power industrial control system. The method comprises the following steps: setting an edge computing center at a terminal side, collecting industrial control system terminal equipment information and communication flow information, defining and identifying attribute characteristics of an electric power industrial control terminal by utilizing equipment fingerprints, automatically collecting the fingerprints of the electric power industrial control terminal equipment by utilizing an Nmap scanning method, establishing a training model by a decision tree algorithm, and achieving the dynamic fingerprint authentication of the terminal equipment; through setting a switch mirror image, intelligent monitoring host flow control and cloud computing center training flow baseline, industrial control terminal equipment flow anomaly detection is realized, and a cloud cooperative defense technology based on edge computing is realized. Through flow data acquisition, information entropy quantification flow characteristic attribute preprocessing and improved semi-supervised clustering K-means algorithm training, abnormal flow detection of the electric power industrial control intranet is realized, and cloud network real-time defense based on abnormal flow detection is realized.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +3
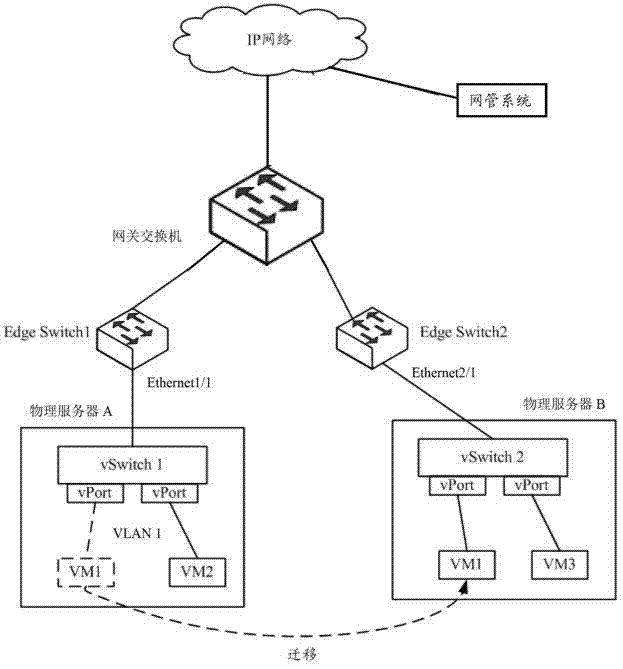
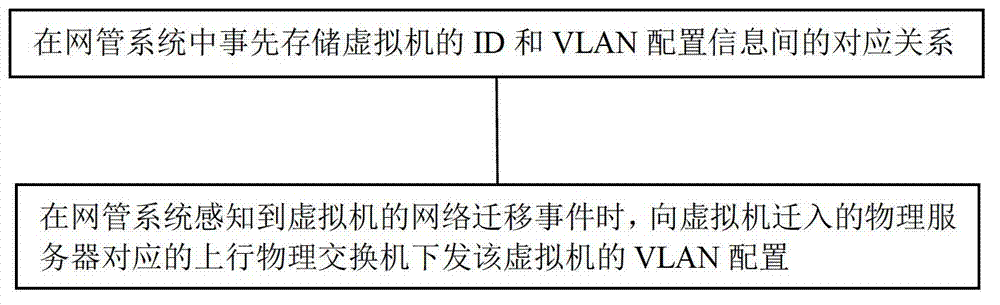
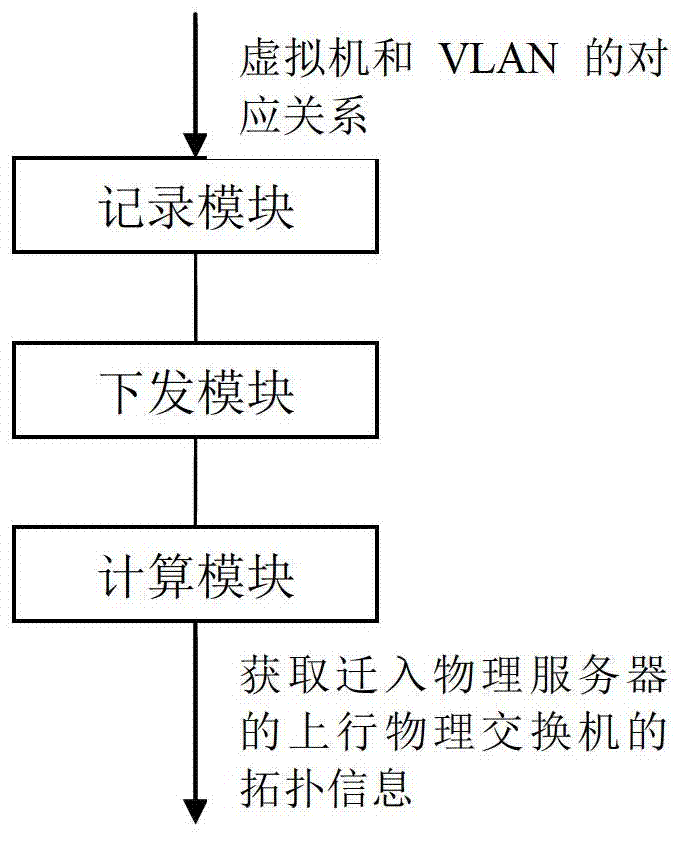
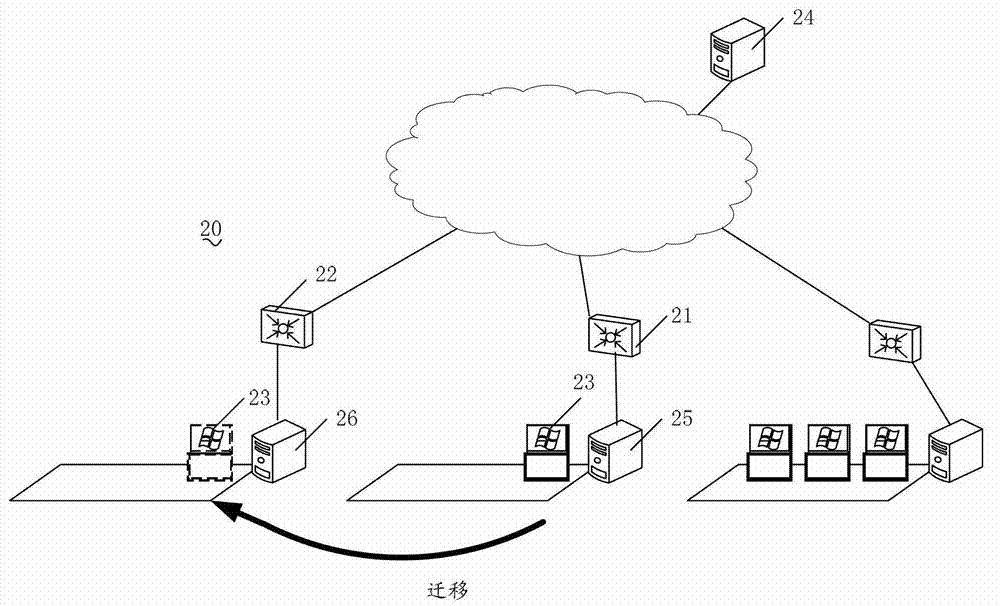
Method and device for dynamically migrating VLAN (virtual local area network) configuration
ActiveCN102821023ANormal accessNetworks interconnectionSimple Network Management ProtocolVirtual machine
The invention provides a method and device for dynamically migrating VLAN (virtual local area network) configuration. The method comprises the following steps of: storing virtual machine ID and corresponding VLAN configuration information in a network management system in advance; transmitting the VLAN configuration of a virtual machine to an upstream physical switch corresponding to a migrated physical server of the virtual machine when the network management system senses out a network migration event of the virtual machine, wherein the migrated physical server transmits an RARP (reverse address resolution protocol) message so as to update ARP tables of all the upstream physical switches after the migration of the virtual machine is finished; and if the migration event is finished before the network management system finishes transmitting the VLAN configuration, the network management system ages the ARP table on a physical switch by an SNMP (simple network management protocol) or command line so as to update the ARP tables of all the upstream physical switches of the migrated physical server. According to the invention, the VLAN configuration of the virtual machine can be migrated dynamically along with the migration of the virtual machine.
Owner:NEW H3C TECH CO LTD
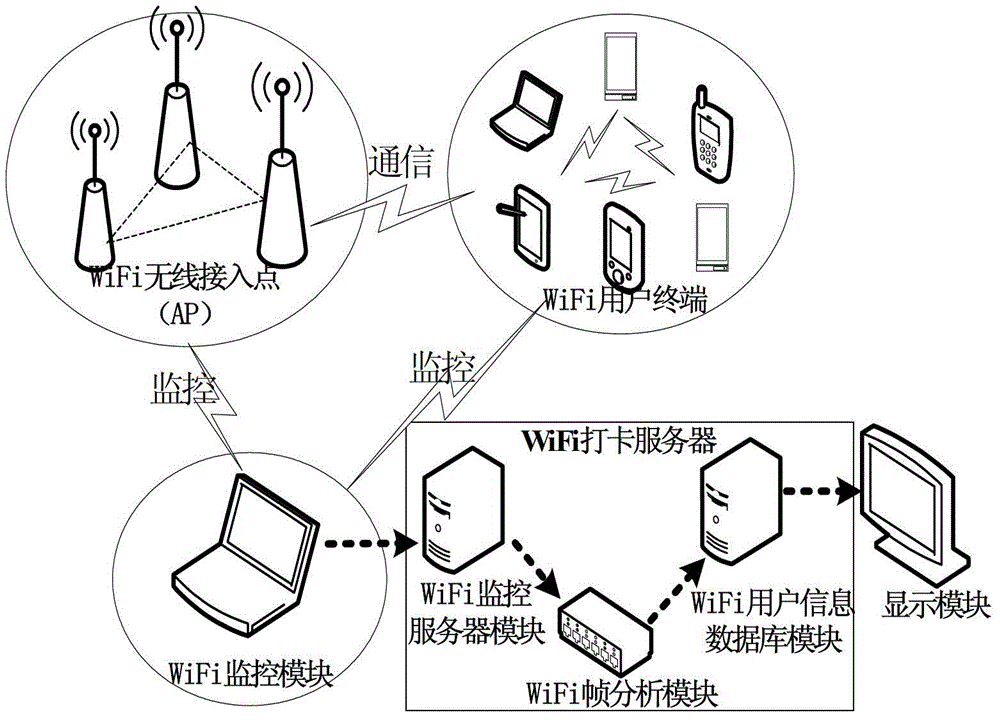
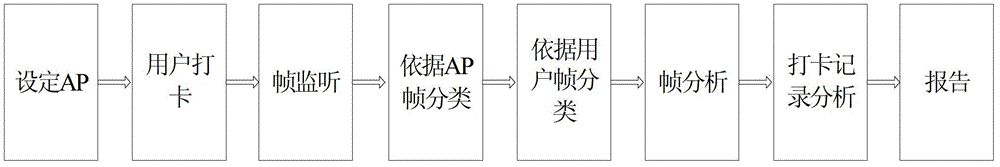
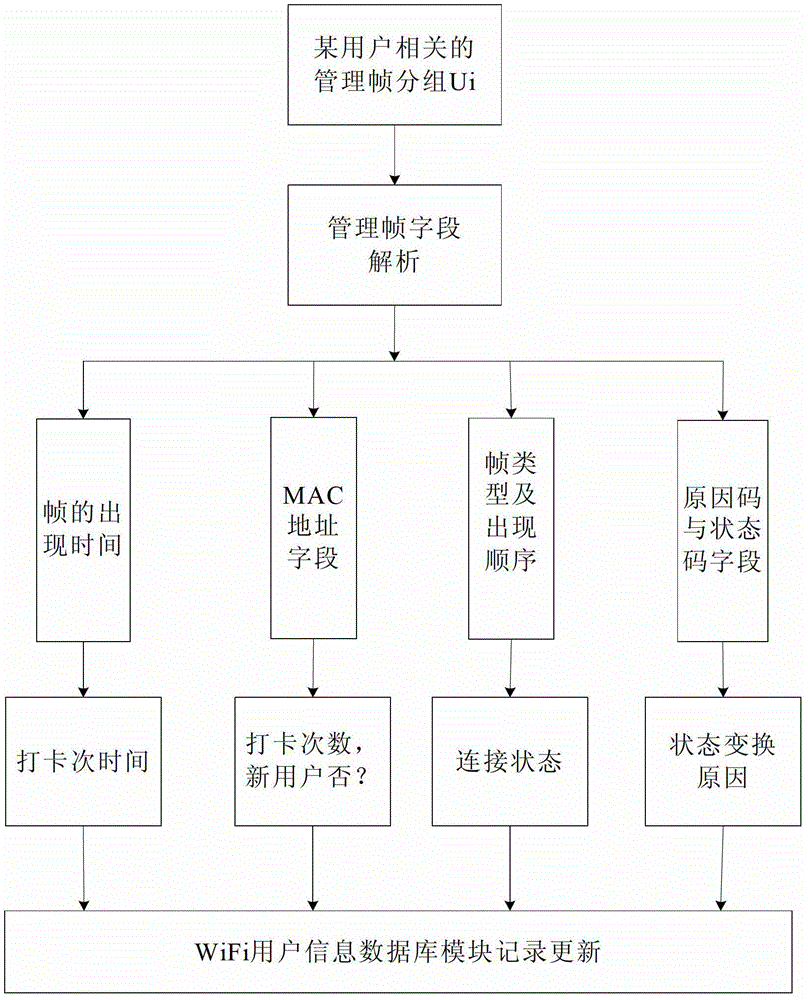
Punch card method based on Wi-Fi and system thereof
InactiveCN102750750ADoes not affect normal operationNormal accessChecking time patrolsWi-FiMAC address
The invention discloses a punch card method based on Wi-Fi and a system thereof. The punch card method acquires management frames in preset access points (AP) according to methods of data packet monitor and data packet capture, and determines punch card information of users through frame classifications according to AP, classifications according to MAC addresses of users and frame analysis. In the punch card system, users only need to try to connect AP in operation processes to complete the punch card. A fast punch card method for staff users is provided. The punch card method does not influence normal operation of a network, and can be realized by employing a usual wireless network card supporting a monitoring mode at a Wi-Fi monitoring terminal.
Owner:PEKING UNIV
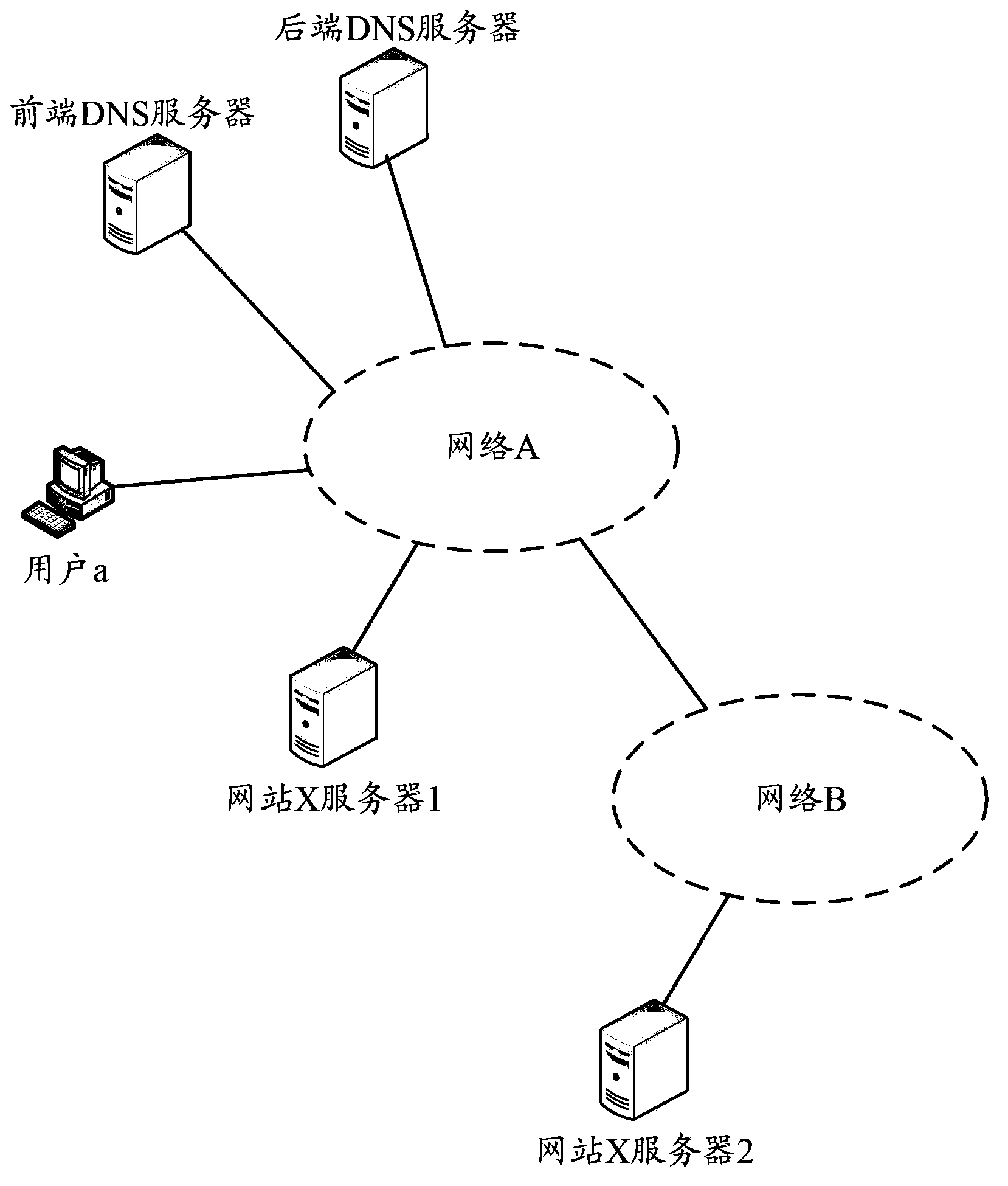
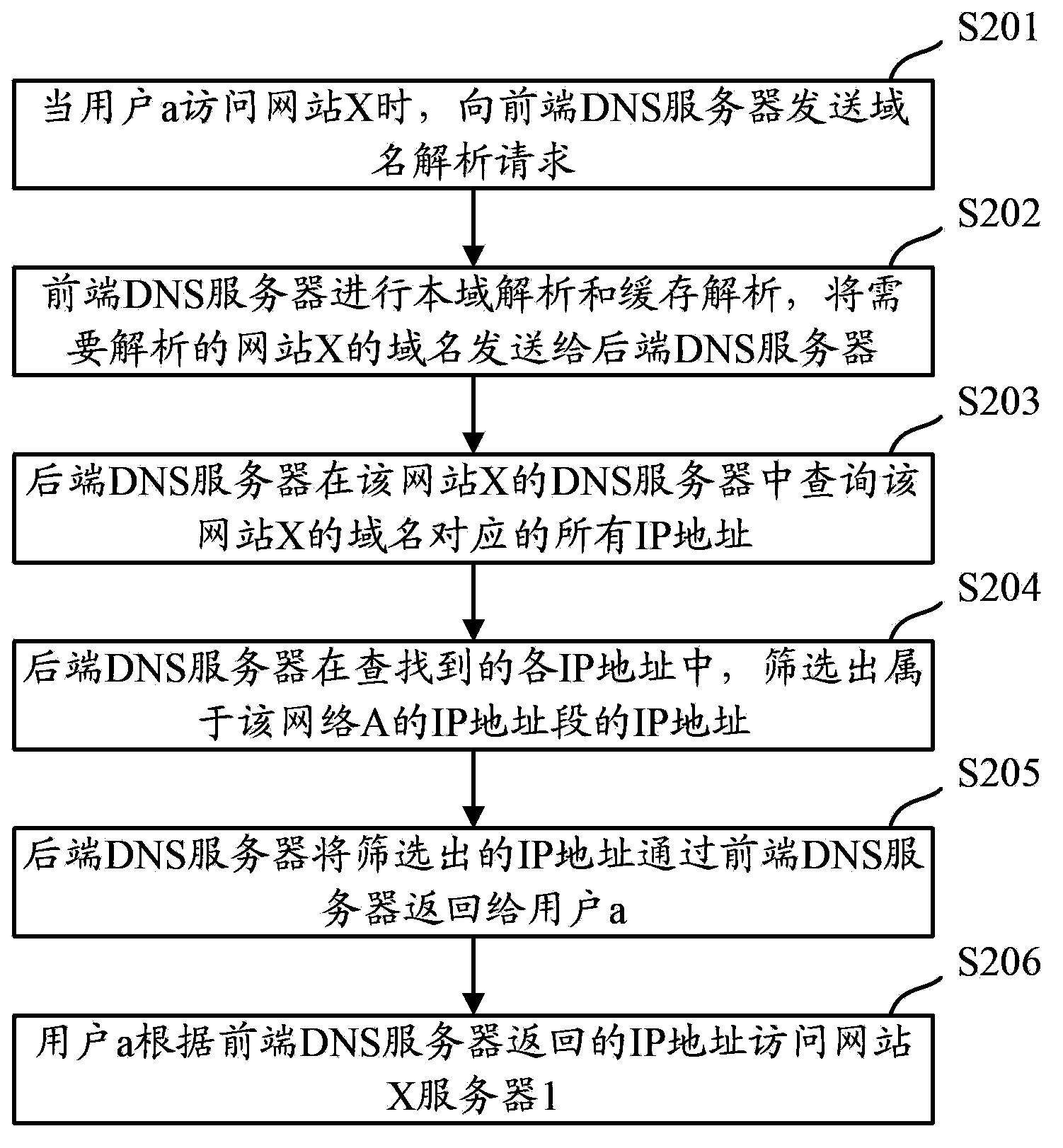
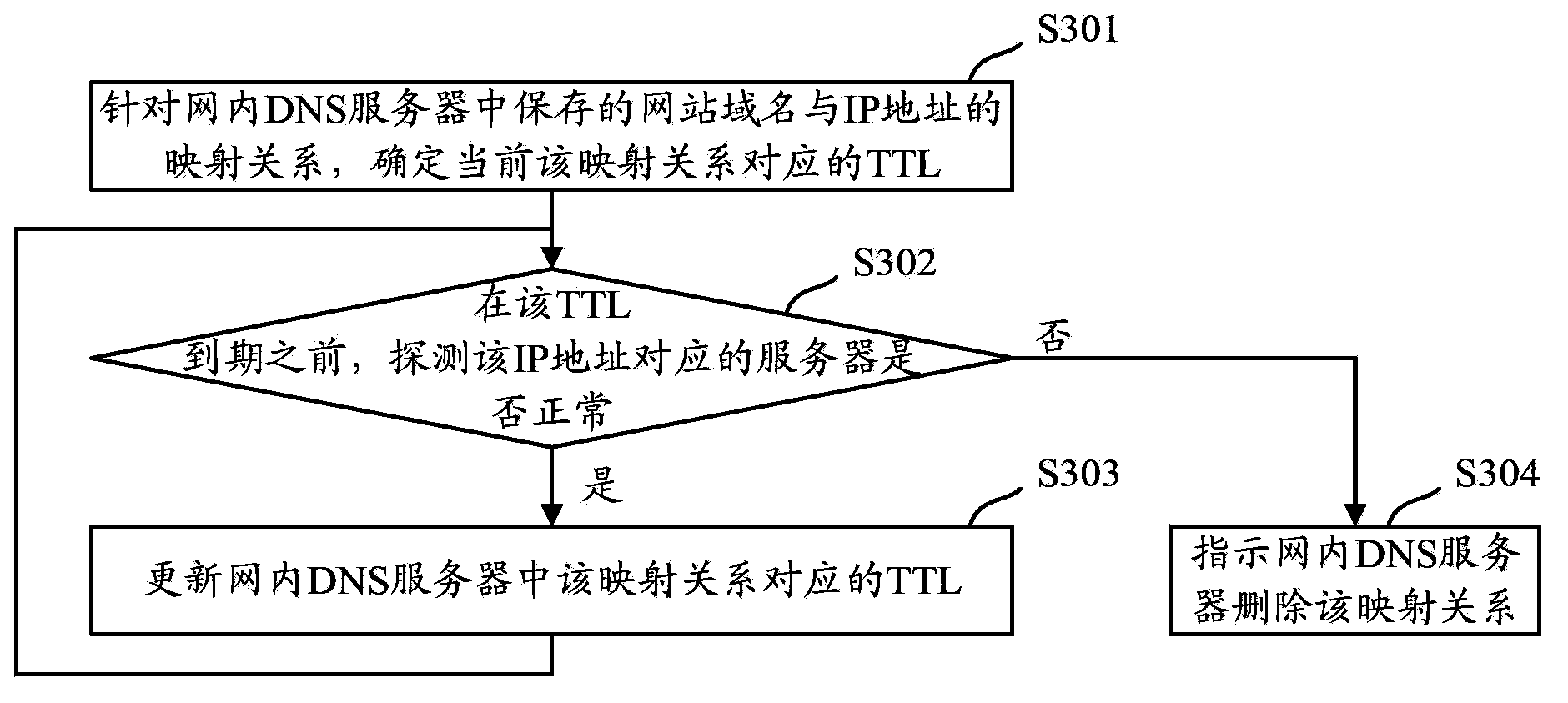
Method and apparatus for probing DNS server
The invention discloses a method and apparatus for probing a DNS server in order to resolve a problem that a user cannot normally have access to the resource of a website in the prior art. According to a mapping relation between website domain names stored in an in-network DNS server and IP addresses, a server corresponding to an IP address is probed before TTL corresponding to the mapping relation expires. If the probed server corresponding to the IP address is normal, the TTL corresponding to the mapping relation is updated and probing is kept before the updated TTL expires, or the in-network DNS server is asked to delete the mapping relation. By means of the above method, if a server corresponding to a corresponding IP address cannot provide service before the TTL corresponding to the mapping relation expire, the in-network DNS server may delete the mapping relation timely. Thus, the IP address is inquired in the DNS server of a website which a user has access to and is returned back to the user. Therefore, the user may normally have access to the website.
Owner:CHINA MOBILE GRP BEIJING
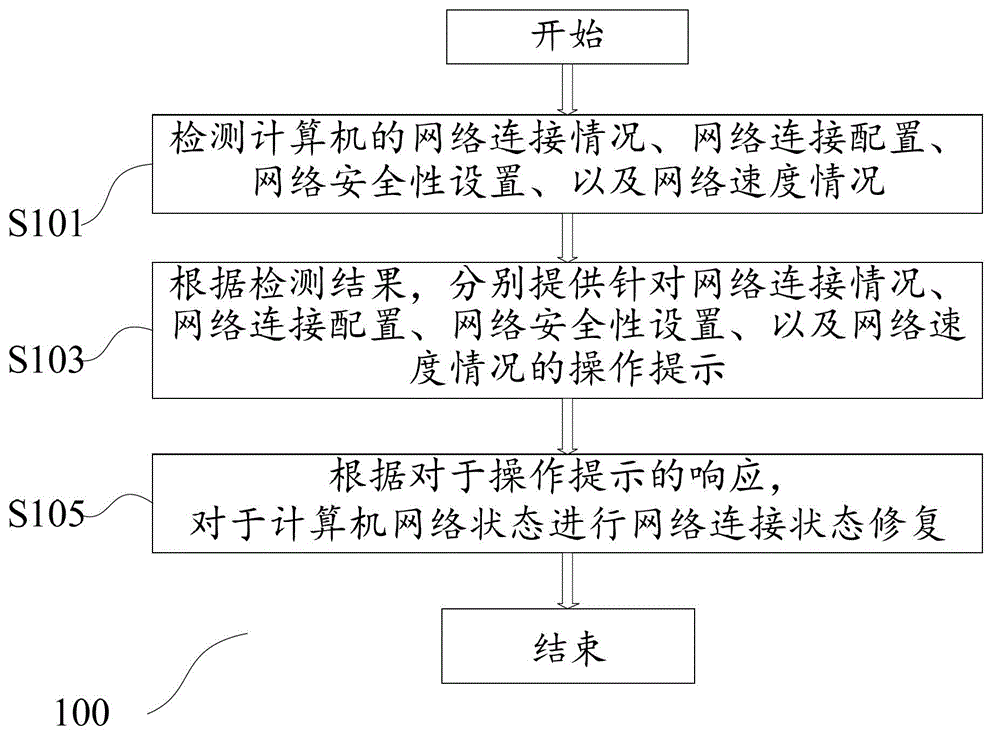
Method and device for inspecting and restoring computer network state
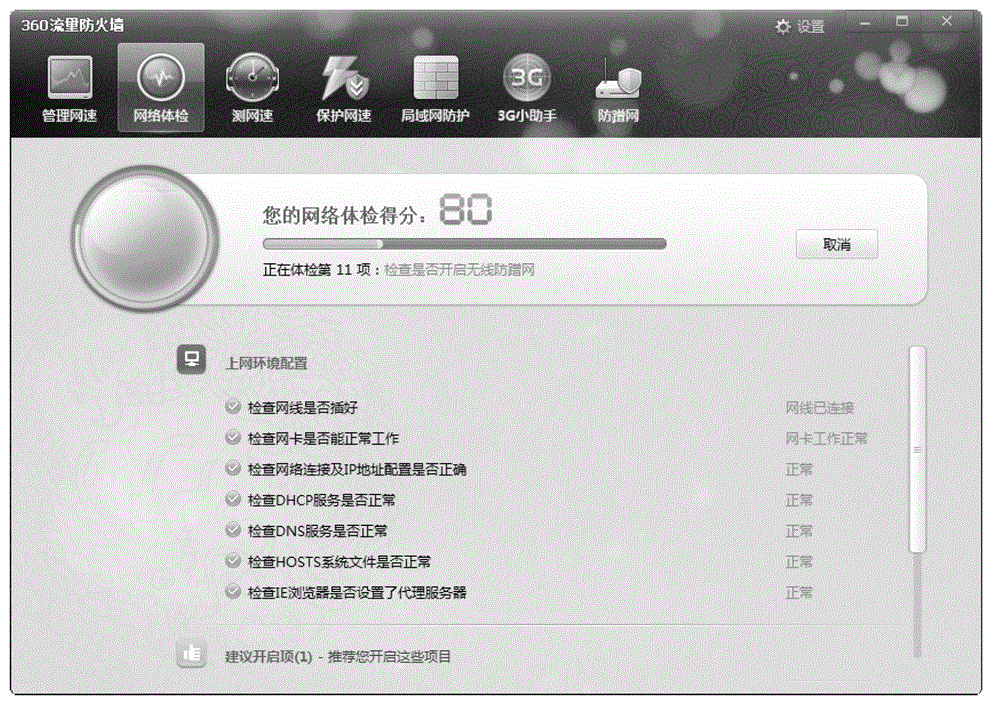
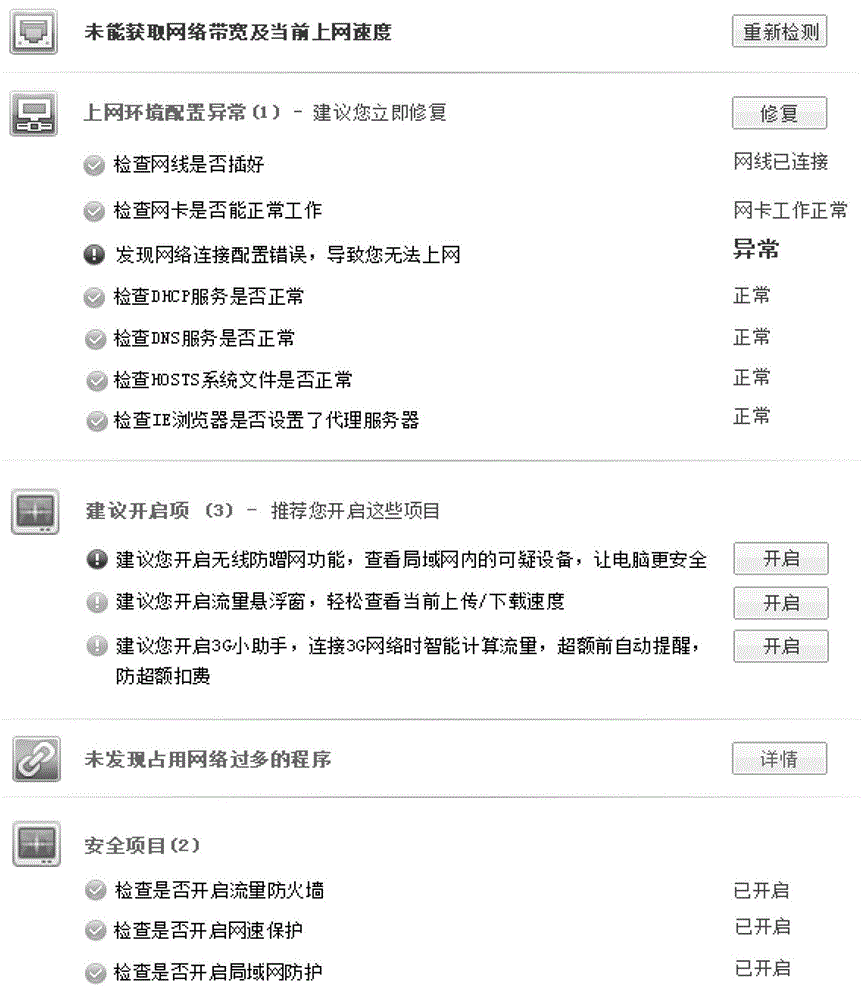
ActiveCN103152218ANormal accessIntuitive and Accurate EvaluationData switching networksAccess networkNetwork connection
The invention discloses a method and a device for inspecting and restoring a computer network state, wherein the method comprises the steps of inspecting a network connection condition, network connection configuration, network safety setting and a network speed condition of a computer, respectively supplying operating prompts aiming at the network connection condition, the network connection configuration, the network safety setting and the network speed condition according to inspection results, and restoring the network connection state for the computer network state according to responses of the operating prompts. According to the method and the device for inspecting and restoring the computer network state, various aspects of the computer network state can be comprehensively inspected, and the corresponding operating prompts according to the inspection results are offered to a user of the computer for reference. Meanwhile, the aspects where the problems exist in the computer network state can be comprehensively restored according to user selection, and the user is capable of normally accessing network resources by using the computer.
Owner:BEIJING QIHOO TECH CO LTD
Resource operation method and device
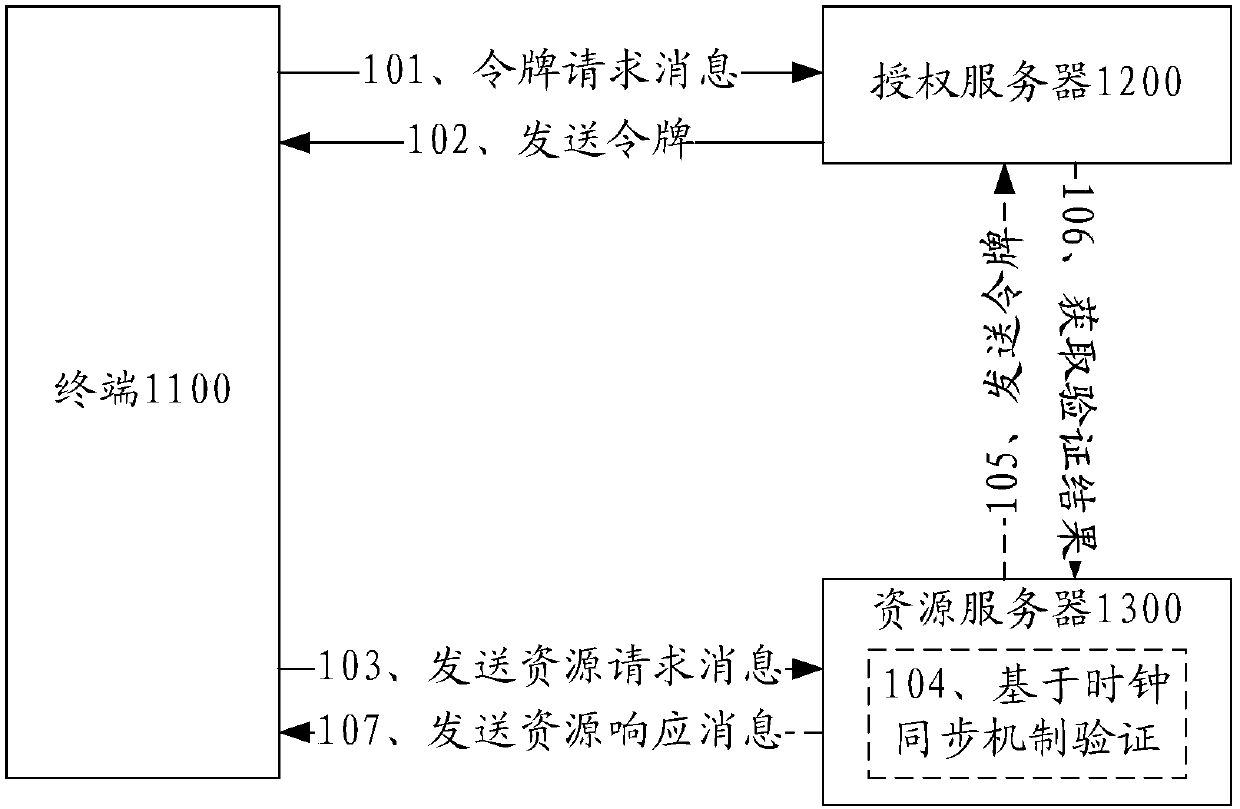
ActiveCN107659406AVerify validityFlexible settingUser identity/authority verificationCiphertextThe Internet
The embodiment of the invention provides a resource operation method and device, and relates to the technical field of the internet of things. A resource server can perform validity verification on atoken sent by a terminal when the resource server cannot connect with an authorization server in real time. A specific scheme is as follows: the resource server receives a resource request message sent by the terminal, the resource request message carries the token and ciphertext information, and the ciphertext information is the encrypted information of the token verification information; the ciphertext information is decrypted according to a decryption key negotiated between the resource server and the authorizations server, thereby acquiring the token verification information; whether the token is valid is determined according to the token verification information, and a resource response message is sent to the terminal when the token is valid. The resource operation method and device provided by the embodiment of the invention are used for the resource operation.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
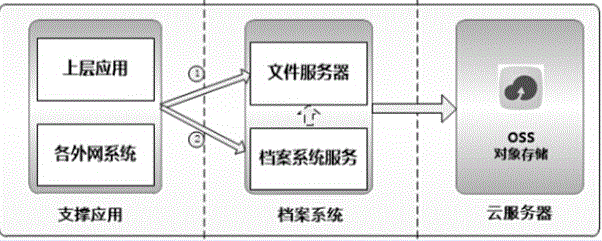
Archive system based on AliCloud OSS (Object Storage Service)
InactiveCN105824932ANormal accessLive viewSpecial data processing applicationsRelevant informationWork flow
The invention discloses an archive system based on AliCloud OSS (Object Storage Service), and belongs to the technical field of cloud storage. The work flow of the archive system comprises the following steps: 1) an application uploads a picture or file which needs to be uploaded to a file server of the archive system through an own way; 2) after the picture or the file is successfully uploaded, the application calls the service of the archive system and provides basic information of the file for the service of the archive system, and the archive system stores relevant information of the file into a database; 3) after the basic information of the file is successfully stored, the archive system loads the file to an OSS server; 4) the archive system provides a management platform for an administrator, can check the state of a current file, a logic name of the file in the OSS, the physical name of the file and the like, and also can check whether a deleted file is started or not. The archive system based on the AliCloud OSS is mass, provides safe and high-safety cloud storage service which is provided by the AliCloud for outside. The capacity and the handling ability can be subjected to elastic expansion.
Owner:INSPUR QILU SOFTWARE IND
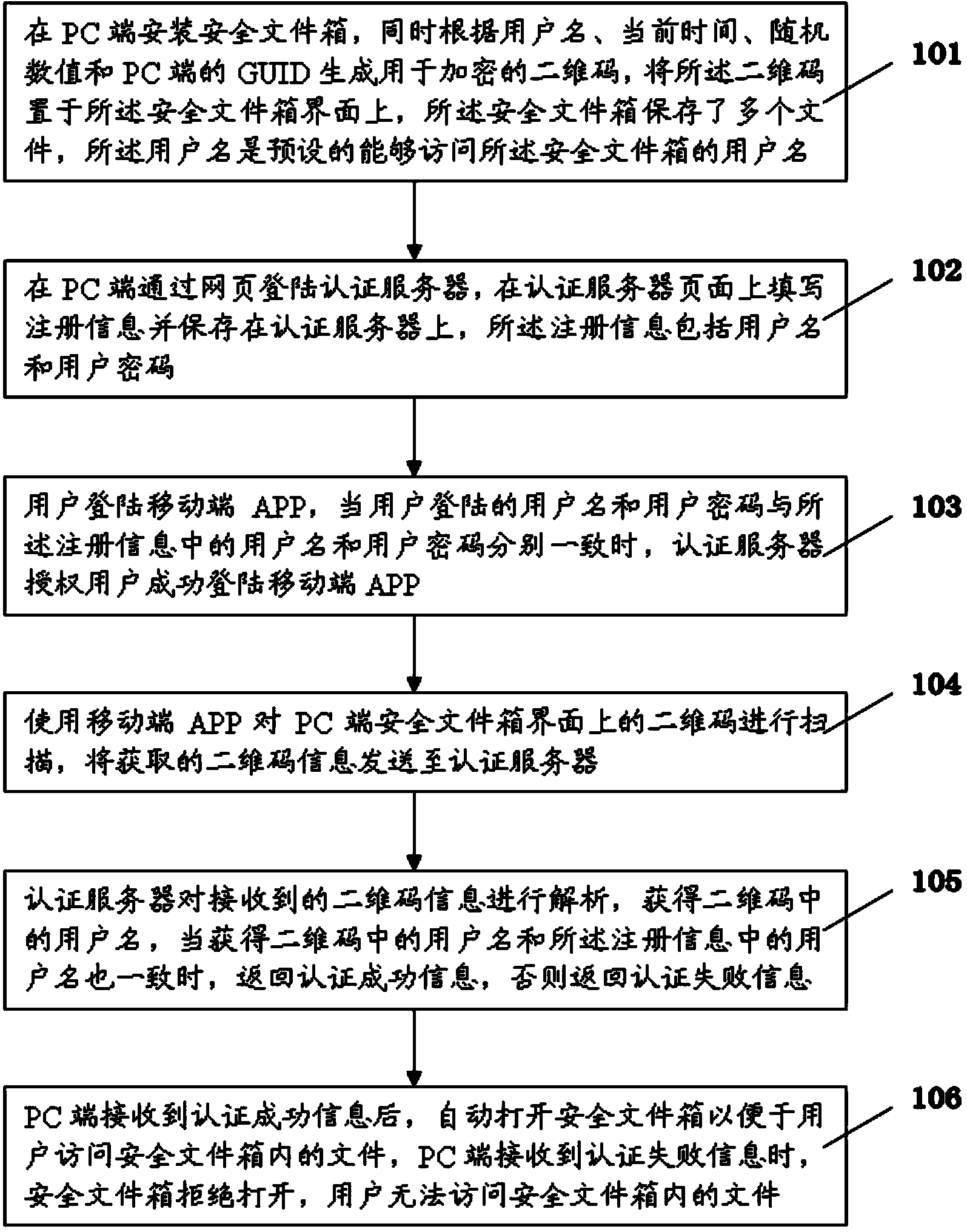
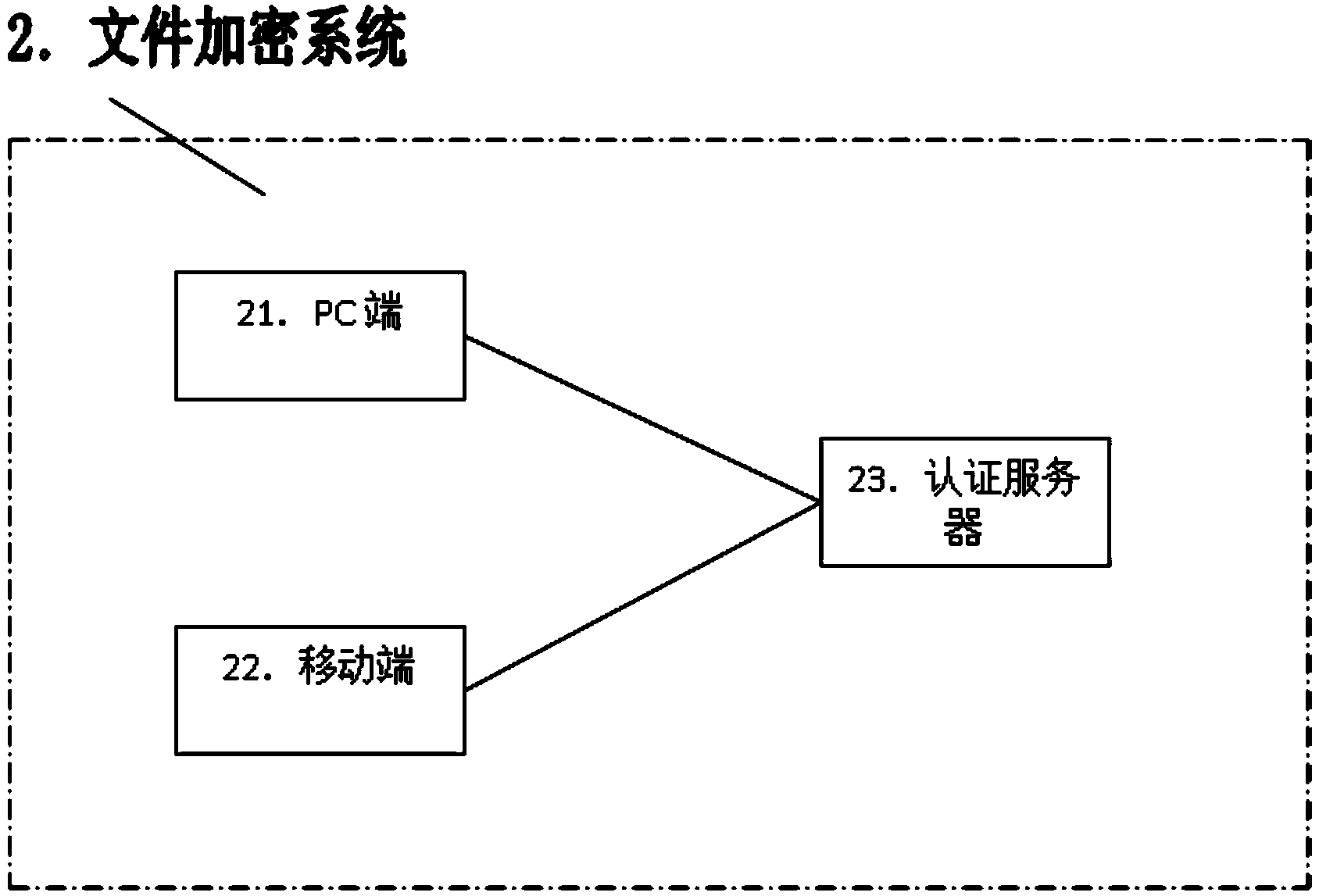
File encryption method based on two-dimension code scanning
ActiveCN103685255AImprove reliabilityNormal accessUser identity/authority verificationSensing by electromagnetic radiationPasswordMobile end
The invention discloses a file encryption method based on two-dimension code scanning. The file encryption method comprises the steps that a safe file box storing a plurality of files is installed on a PC, a two-dimension code for encryption of the safe file box is generated based on a user name, current time, a random value and the overall unique identification GUID of the PC, the user name and a user password are used as a log-on message and are stored on an authentication server, when a user name and a user password for logging onto an APP of a mobile terminal are identical to the user name and the user password of the log-on message respectively, a user is authorized to successfully log onto the APP of the mobile terminal, the APP of the mobile terminal scans the two-dimension code and sends the scanned two-dimension code to the authentication server, the authentication server analyzes the scanned two-dimension code to obtain the user name, and when the user name obtained through analysis is identical to the user name of the log-on message, the user is authorized to access the files stored in the safe file box. According to the file encryption method, the PC and the mobile terminal are coordinated, the user is authorized to access the files stored in the safe file box of the PC based on two-dimension code scanning, and therefore the password for file encryption is prevented from being forgotten or stolen.
Owner:SHANGHAI PEOPLENET SECURITY TECH
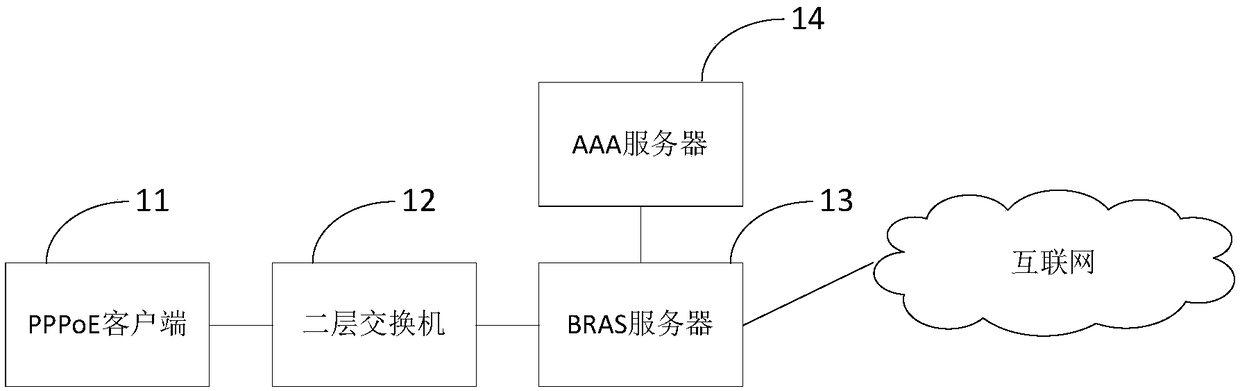
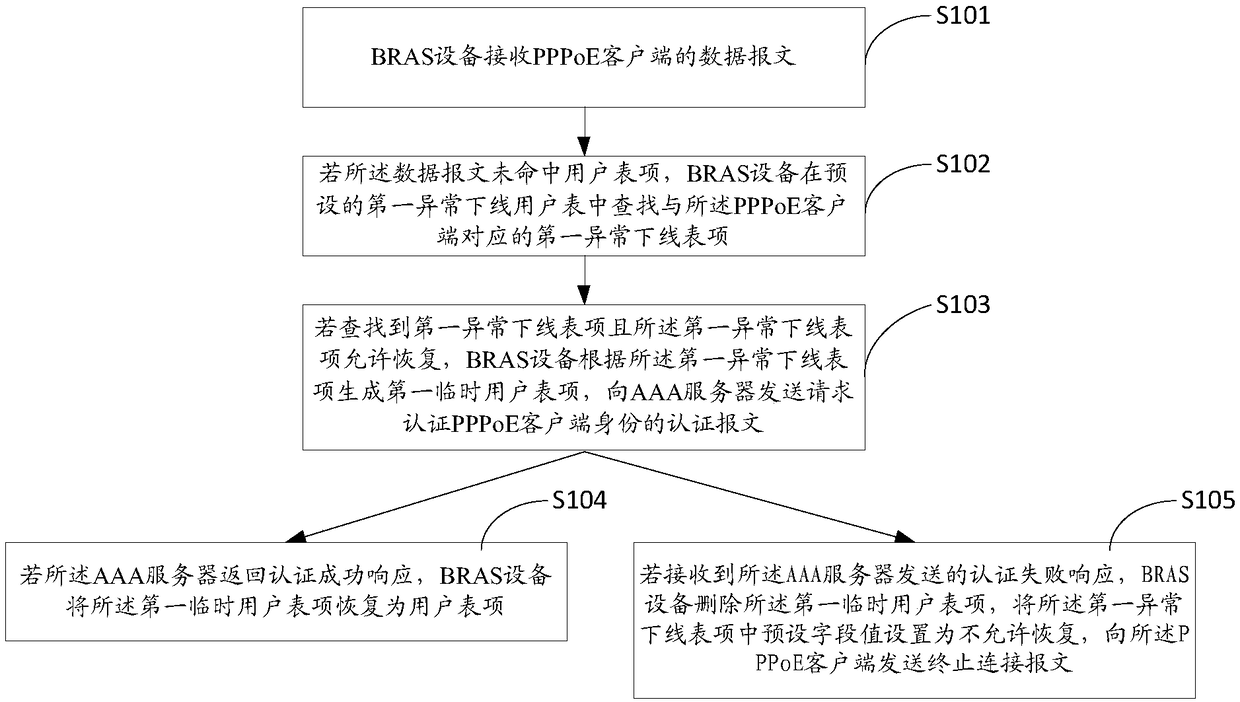
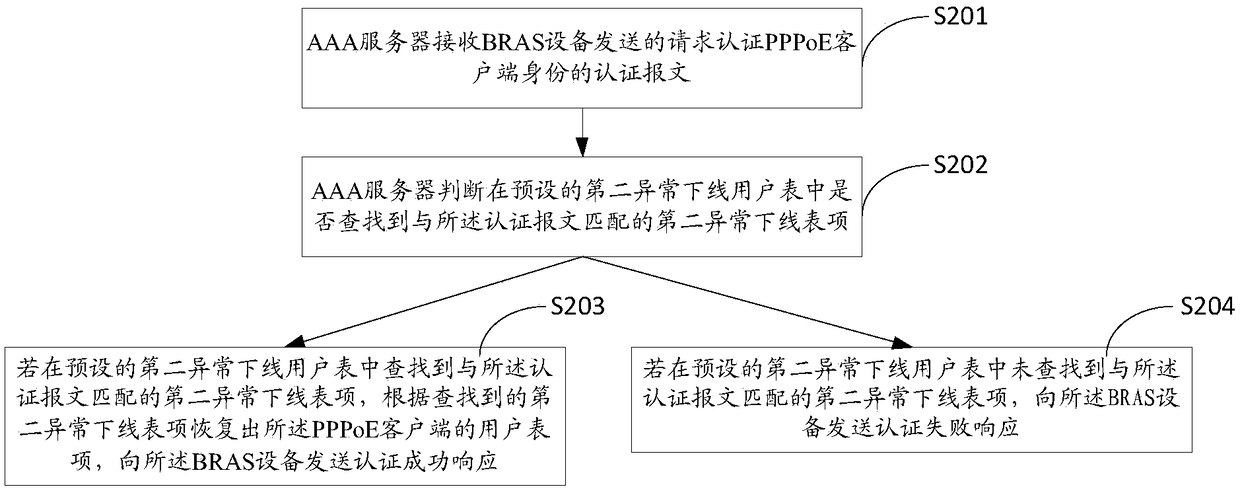
Online recovery method for PPPoE (Point-to-Point Protocol over Ethernet), BRAS (Broadband Remote Access Server) equipment and AAA (Authentication, Authorization and Accounting) server
The invention provides an online recovery method for a PPPoE (Point-to-Point Protocol over Ethernet), BRAS (Broadband Remote Access Server) equipment and an AAA (Authentication, Authorization and Accounting) server. The online recovery method for the PPPoE comprises the following steps: receiving the data message of a PPPoE client side; if the data message does not name a user table item, searching a first abnormal offline table item corresponding to the PPPoE client side in a preset first abnormal offline user table; if the first abnormal offline table item is searched and the first abnormaloffline table item is permitted to recover, according to the first abnormal offline table item, generating a first temporary user table item, and sending a request to the AAA server to authenticate the authentication request of the identity of the PPPoE client side; if the AAA server returns an authentication success response, recovering the first temporary user table item as the user table item.According to the online recovery method for the PPPoE, the technical effects that an access side link is immediately recovered after being cut off, the client side does not sense a broken line and cannormally access the network, and the user can conveniently use the online recovery method can be achieved.
Owner:XINHUASAN INFORMATION TECH CO LTD
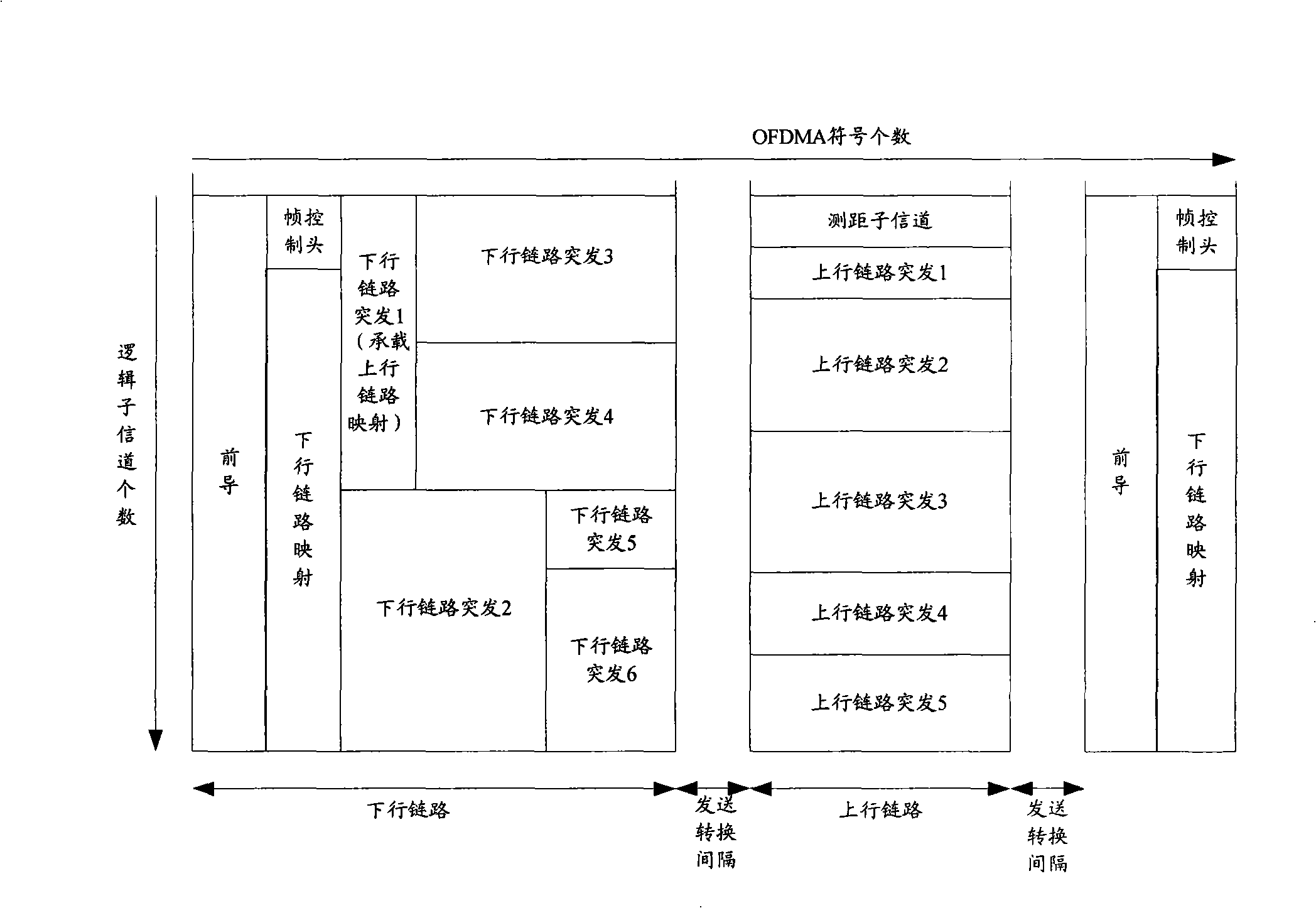
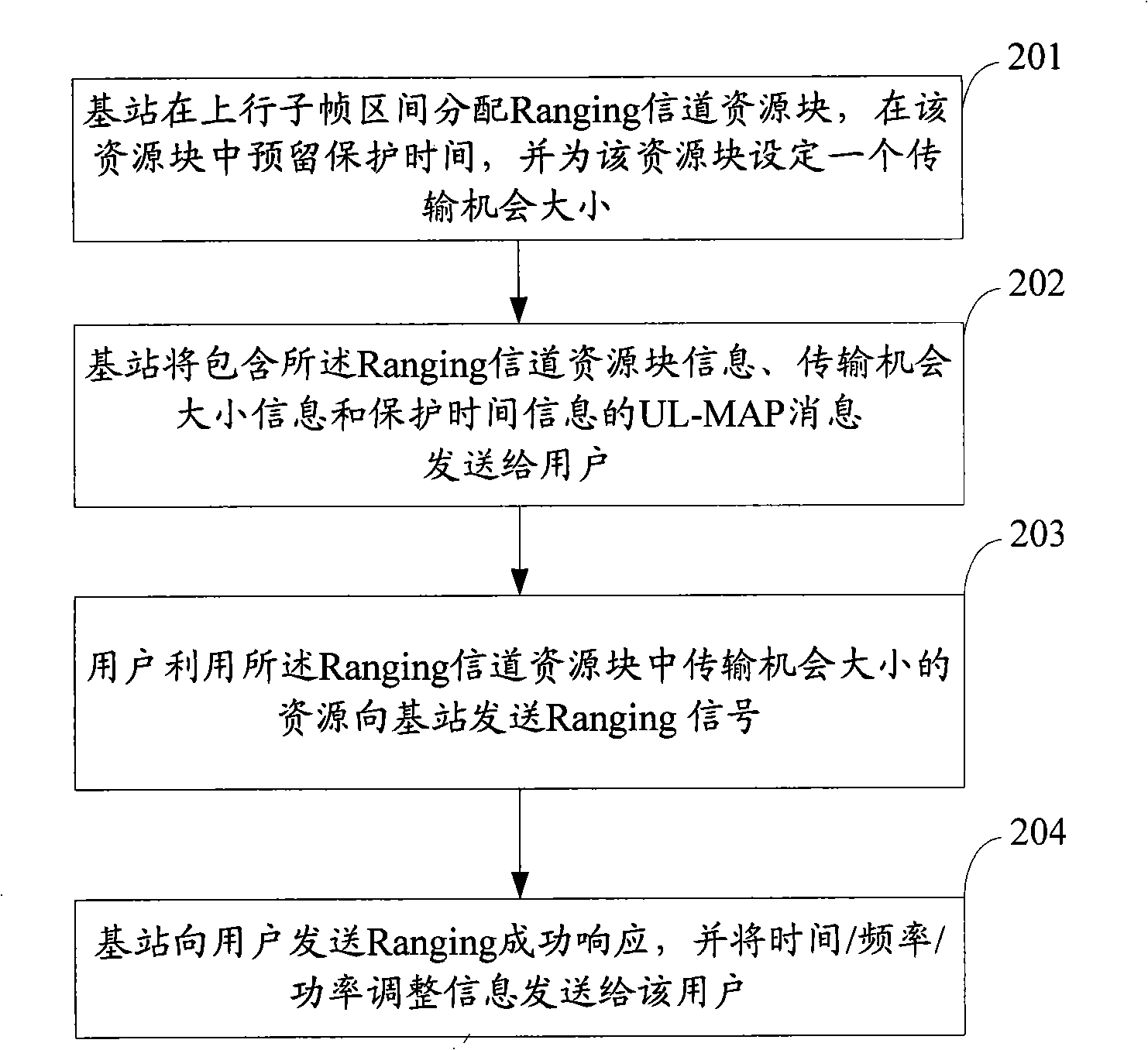
Distance measuring signal transmitting method, system and apparatus in OFDM system
ActiveCN101335977ANormal accessData switching by path configurationRadio/inductive link selection arrangementsResource blockGuard time
An embodiment of the invention discloses a method of range signal transmission in an orthogonal frequency division multiplexing system, comprising that: a district of a base station includes at least two areas, and each area is provided with a distance range channel time resource block in an upstream sub-frame section, and guard time is obligated in each distance range channel time resource block. A terminal determines oneself area according to the receiving intensity of the current signal, transmits the range signal to the base station through the time resource beside the guard time in the range channel time resource block distributed for the area. The embodiment of the invention also discloses a system of range signal transmission, a base station and a terminal in the orthogonal frequency division multiplexing system. According to the invention, reverse access of the terminal in different area is flexibly supported.
Owner:XFUSION DIGITAL TECH CO LTD
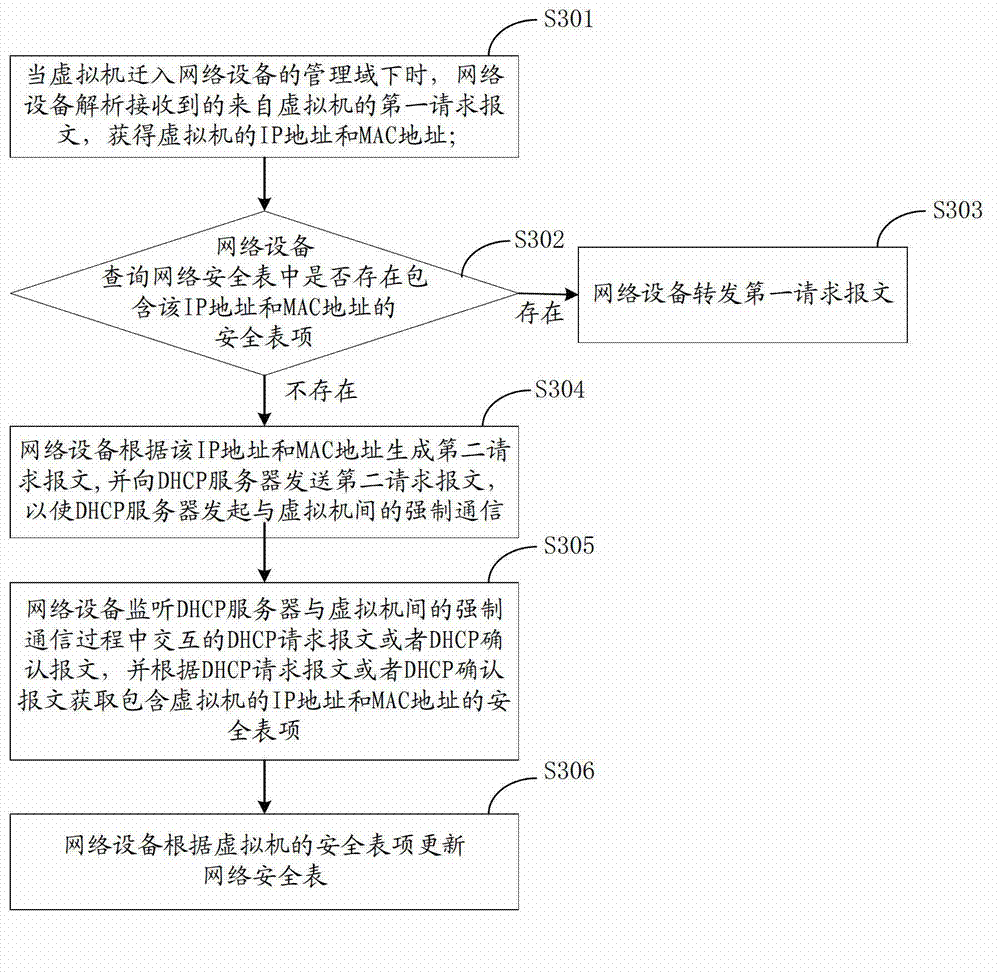
Method for updating network security table and network device and dynamic host configuration protocol (DHCP) server
InactiveCN103095722AGuaranteed reliabilityEnsure network securityTransmissionNetwork security policyMedia access control
The invention discloses a method for updating network security table, a network device and a dynamic host configuration protocol (DHCP) server. When a virtual machine moves in a management domain of a network device, the network device analyses a first received request message from the virtual machine, an internet protocol (IP) address and a medium access control (MAC) address of the virtual machine are obtained, when a security table item including the IP address and the MAC address doesn't exist in a network security table of the network device, the network device sends a second request message generated according to the IP address and the MAC address to the DHCP server, so that the DHCP server is enabled to launch mandatory communication between the DHCP server and the virtual machine, the network device monitors an interactive message between the DHCP server and the virtual machine to obtain the security table item of the virtual machine, the network security table is updated according to the security table item. Through the above mode, the method for updating network security table, the network device and the DHCP server ensure that the virtual machine can access the network normally when the virtual machine moves in the management domain of the network device, reliability of the network security table is also ensured, and therefore network security is ensured.
Owner:HUAWEI TECH CO LTD
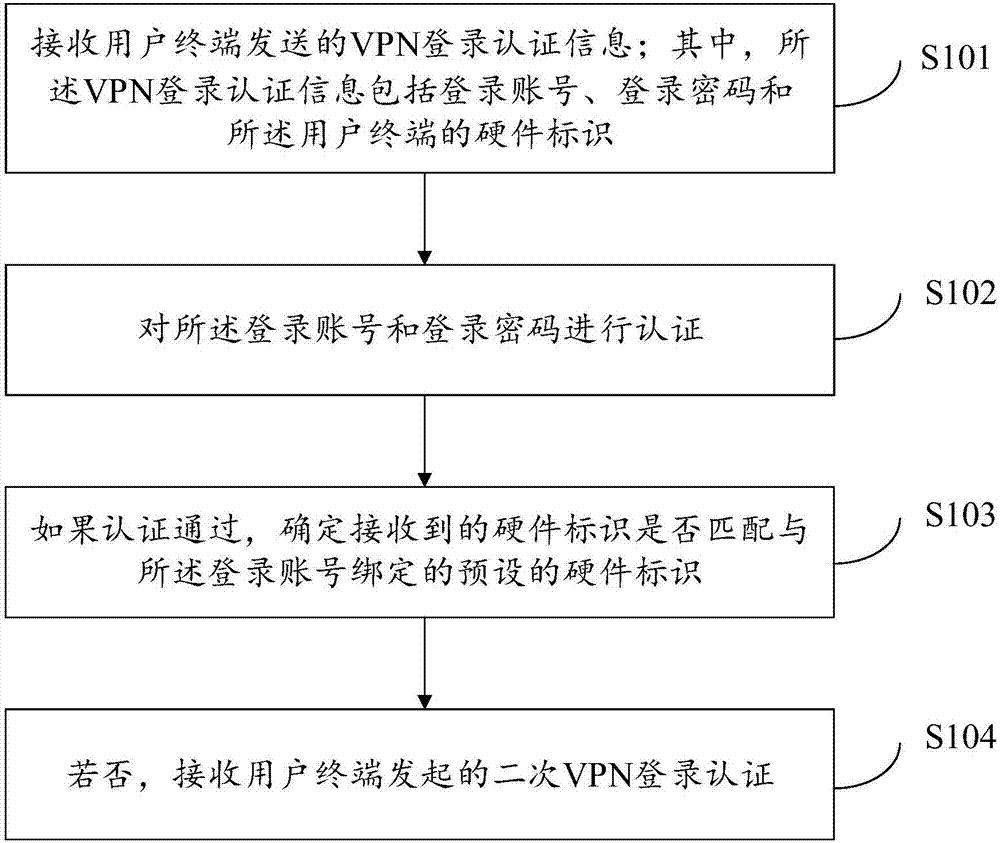
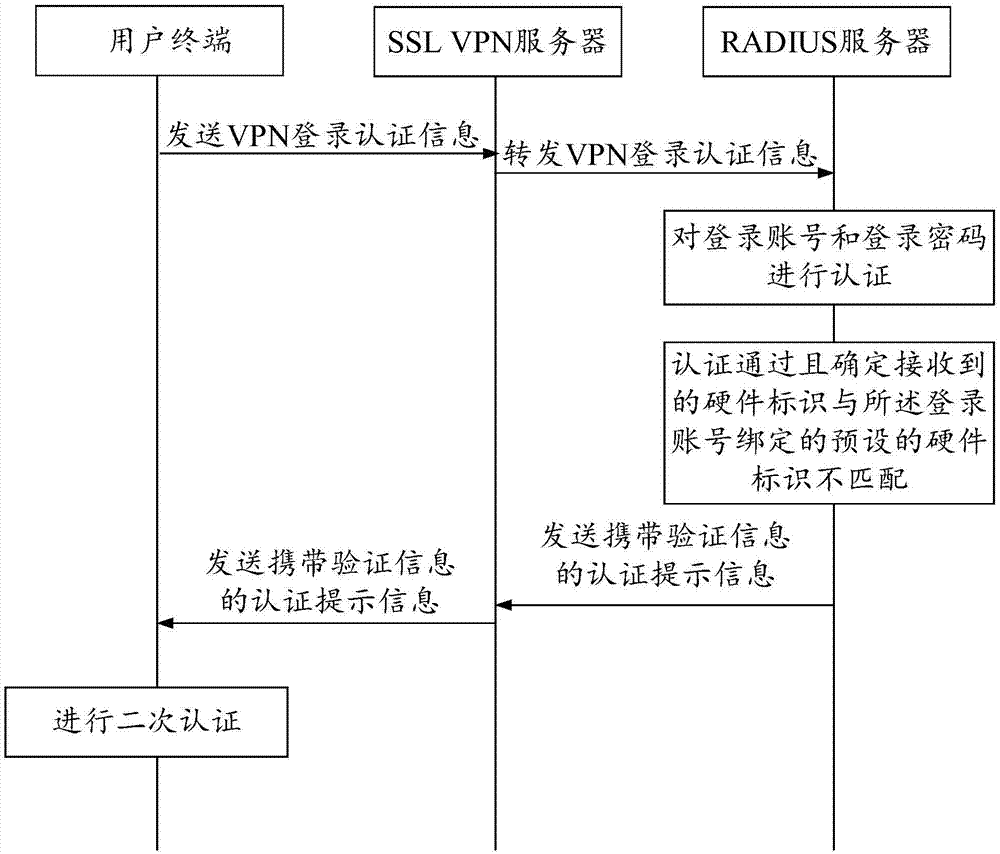
VPN login authentication method and apparatus
The invention discloses a VPN login authentication method, applied to an authentication server. The method comprises the following steps: receiving VPN login authentication information sent by a userterminal, wherein VPN login authentication information comprises a login account, a login password and a hardware identifier of the user terminal; authenticating the login account and the login password; determining whether the received hardware identifier is matched with a preset hardware identifier bound with the login account in the case of authentication success; and otherwise, receiving secondary VPN login authentication initiated by the user terminal. By adoption of the VPN login authentication method, on the premise of considering the security, it is ensured that when the user logs in different terminals by using the same account, the user can still normally access VPN.
Owner:HANGZHOU DPTECH TECH
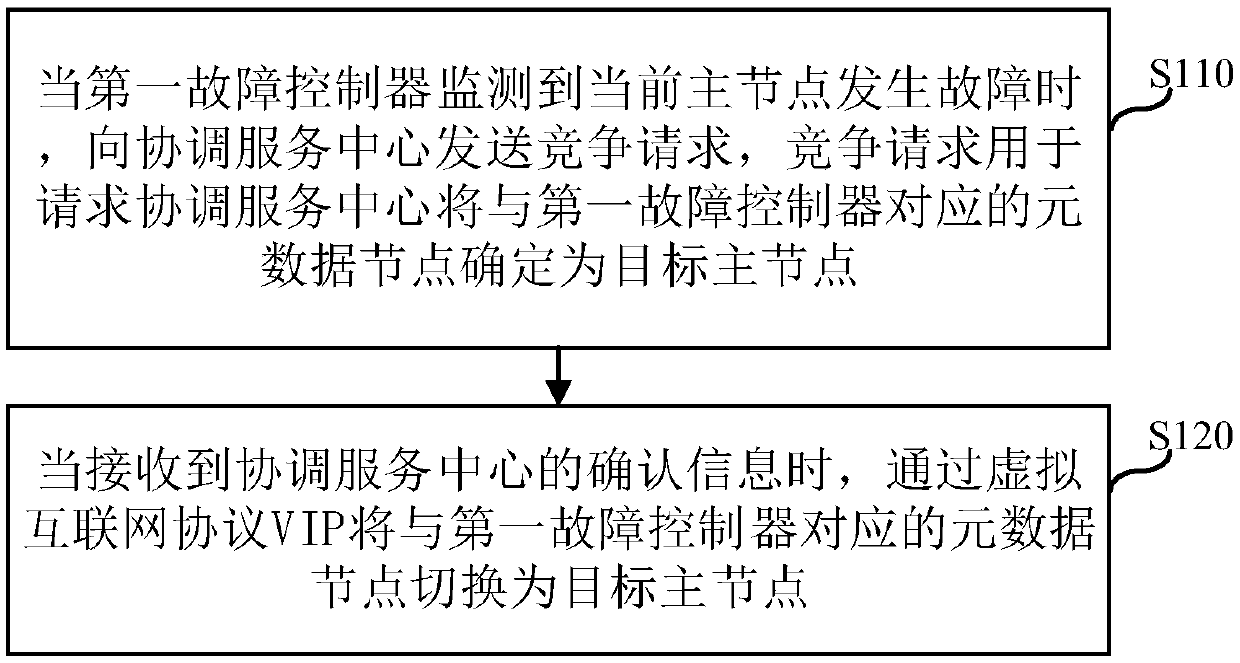
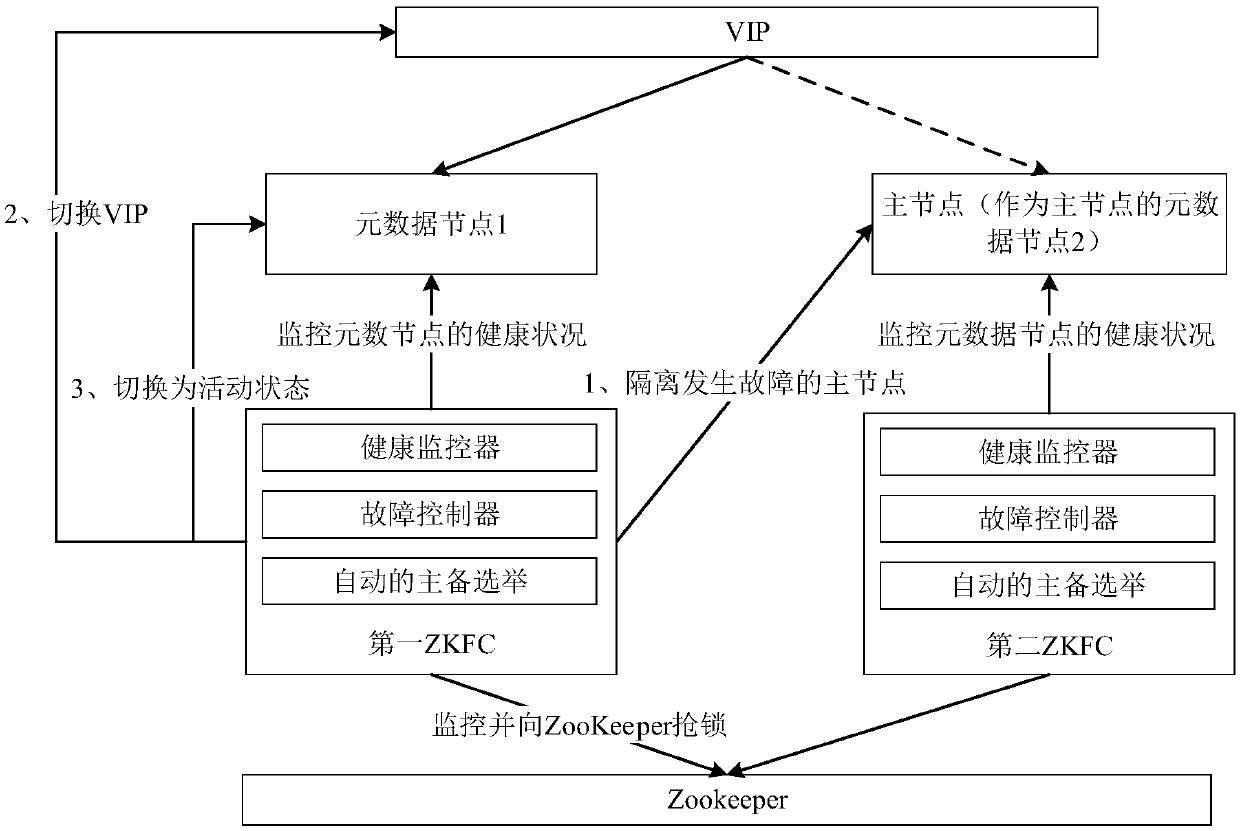
Host node switching method, device, electronic device, and computer storage medium
InactiveCN109101196ANormal accessImprove compatibilityInput/output to record carriersThe InternetClient-side
The present application relates to the field of Internet technology, and discloses a host node switching method, a device, an electronic device, and a computer storage medium. The master node switching method comprises the following steps: when the first fault controller detects that the current master node fails, sending a contention request to the coordination service center, wherein the contention request is used for requesting the coordination service center to determine the metadata node corresponding to the first fault controller as the target master node; then, when receiving the acknowledgement information from the coordination service center, the metadata node corresponding to the first failure controller is switched to the target master node through the virtual Internet protocolVIP. The method of the embodiment of the present application enables the existing low-version client to normally access the switched master node even if the master-standby handover of the metadata node occurs, thereby achieving compatibility for the low-version client to access the master node.
Owner:BEIJING QIHOO TECH CO LTD
Processing method and device for kernel crash field data
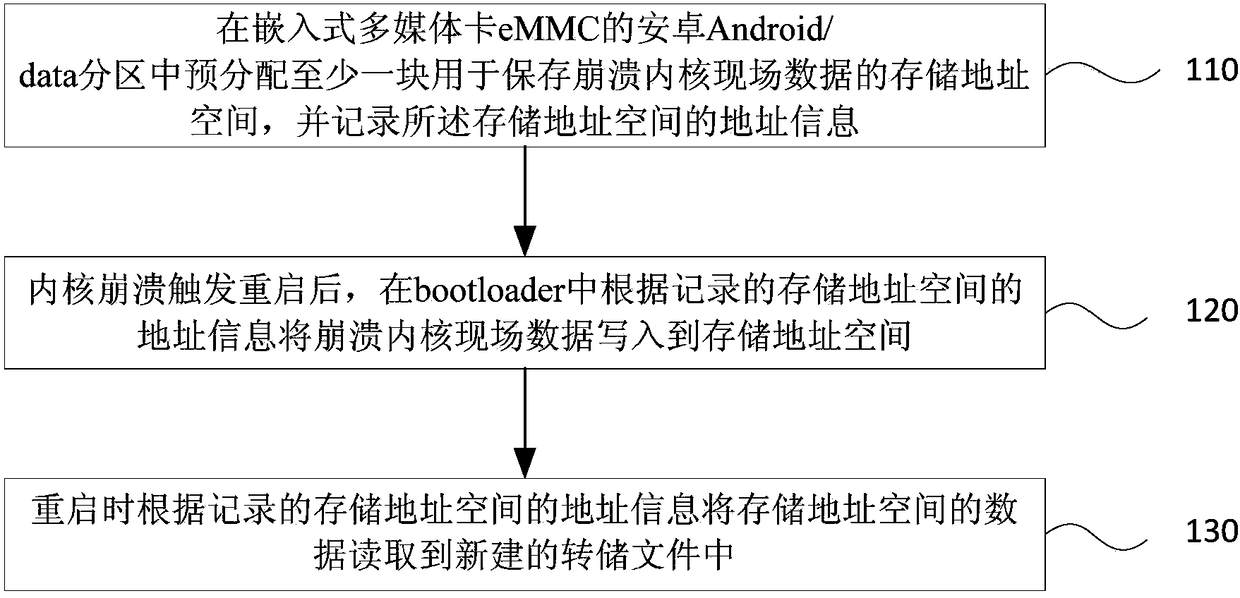
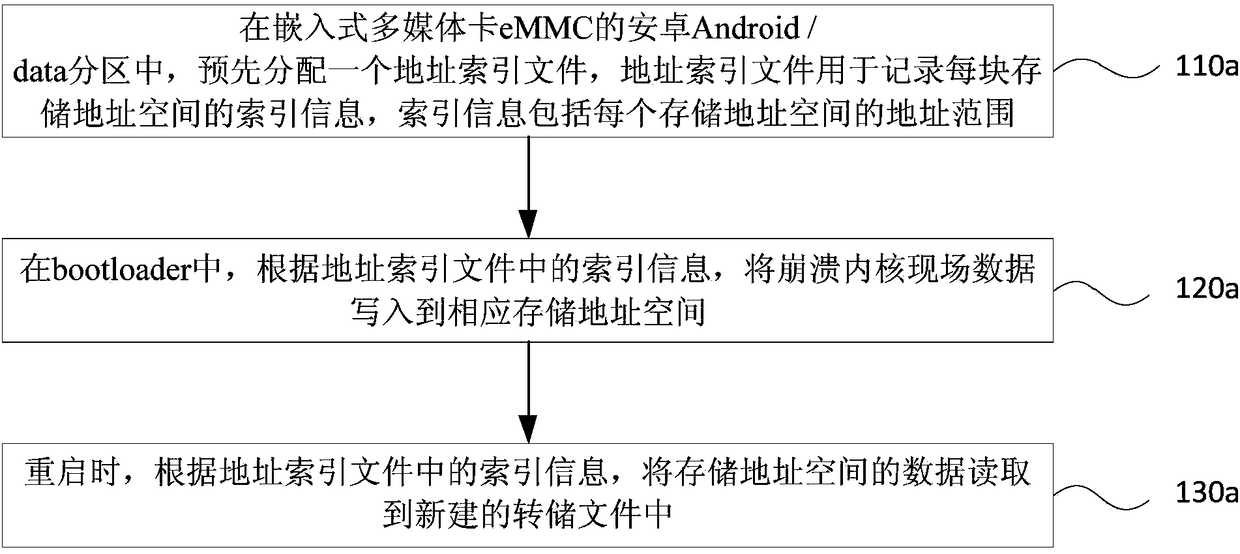
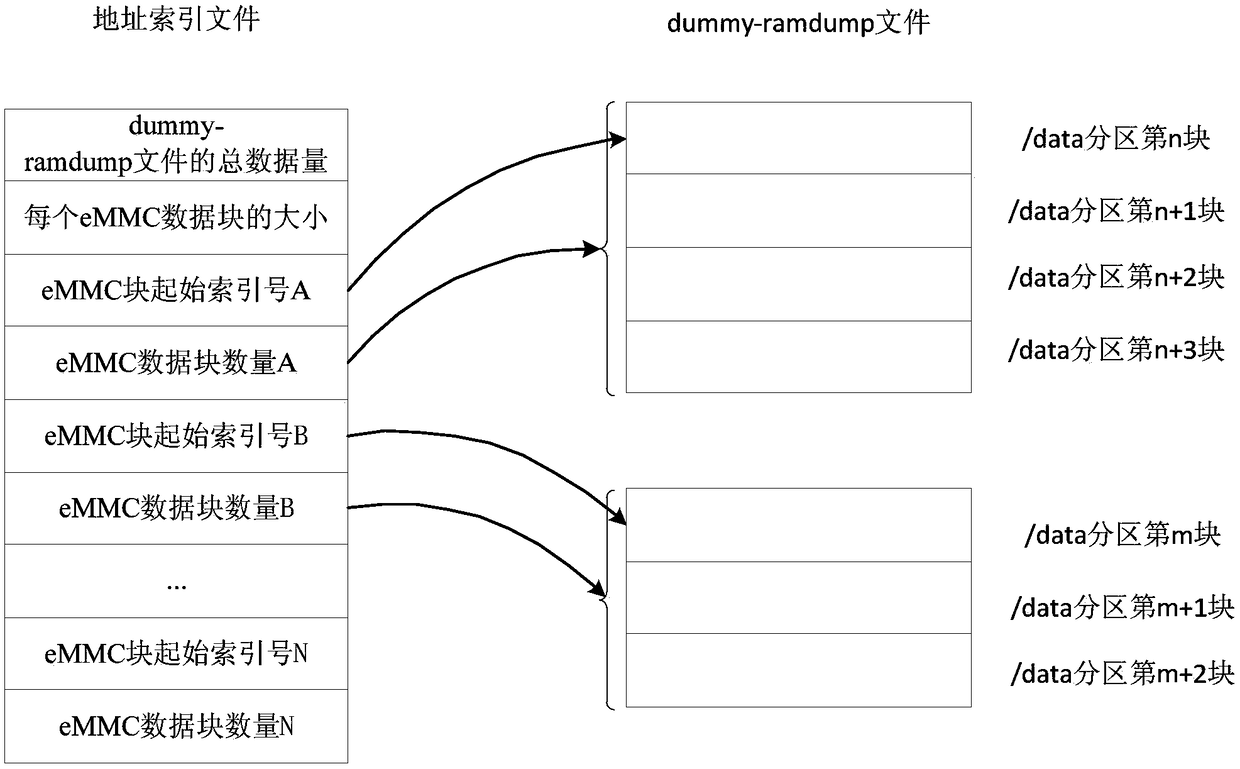
The invention discloses a processing method and device for kernel crash field data. The method comprises the following steps that: in the Android / data partition of an eMMC (Embedded Multi Media Card), pre-distributing at least one storage address space used for storing the kernel crash field data, and recording the address information of the storage address space; after the kernel crash is triggered and restarted, in a bootloader, according to the recorded address information of the storage address space, writing the kernel crash field data into the storage address space; and during restarting, according to the recorded address information of the storage address space, reading the data of the storage address space into a new dump file. The technical scheme provided by the embodiment of the invention can be suitable for all Linux kernel crash scenes, is wide in coverage scene and is high in applicability. Meanwhile, when the kernel crash field data is stored, a fourth-generation expansion file system and an encryption algorithm which is put forward by the Android6.0 do not need to be additionally transplanted, and therefore, cost for storing the kernel crash field data is lowered so as to be convenient in use.
Owner:LEADCORE TECH +1
WLAN (wireless local area network) channel and power distribution method and system for mobile terminal
InactiveCN103024887ANormal accessAutomatically adapt to WLAN channelPower managementNetwork topologiesDistribution methodPower parameter
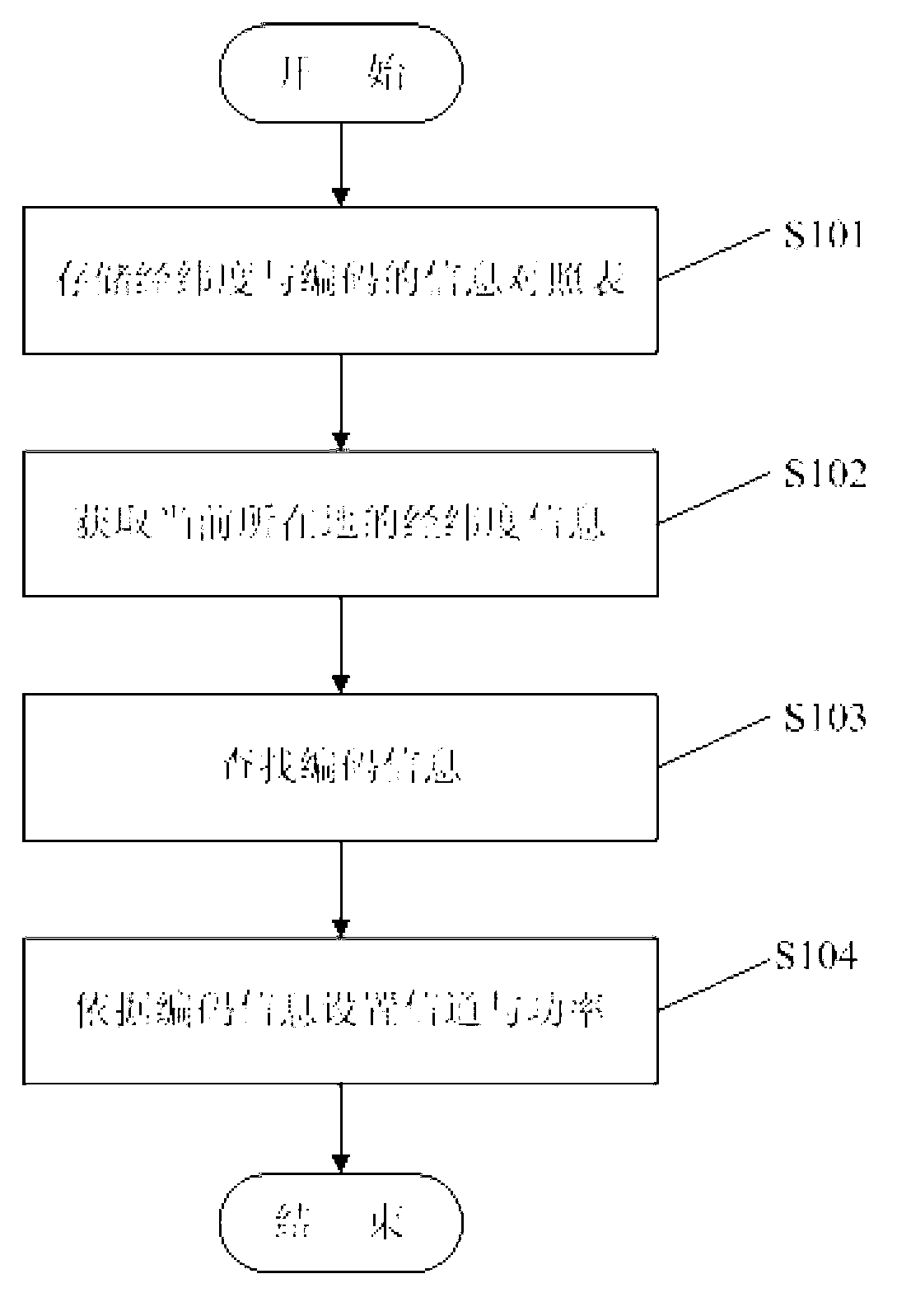
The invention discloses WLAN (wireless local area network) channel and power distribution method and system for a mobile terminal. The method includes: storing a latitude-longitude and code comparison table, allowing for correspondence between codes of nations or areas and latitude-longitude ranges of the nations or areas, in the mobile terminal; starting a GPS (global positioning system) of the mobile terminal to acquire latitude and longitude of a current location, and searching the latitude-longitude and code comparison table to obtain a code of a nation or area corresponding to the latitude and longitude; setting WLAN channels and power parameters of the mobile terminal through a WLAN device according to the code. The method and system allow the mobile terminal to acquire the latitude and longitude through the GPS so as to configure the WLAN channels and power parameters for itself, allow the mobile terminal to automatically adapt to the WLAN channels and powers of different nations or areas so as to normally access WLANs.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
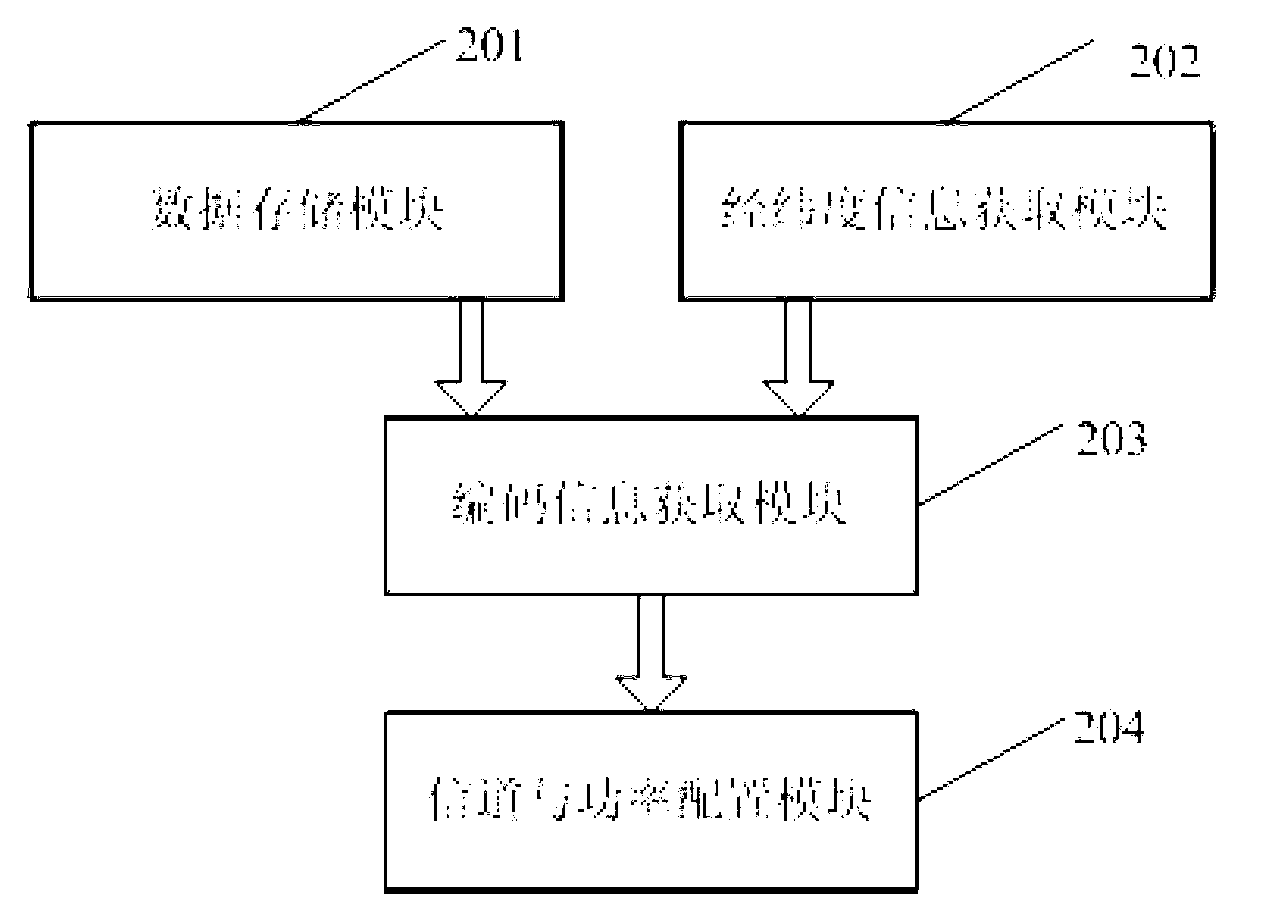
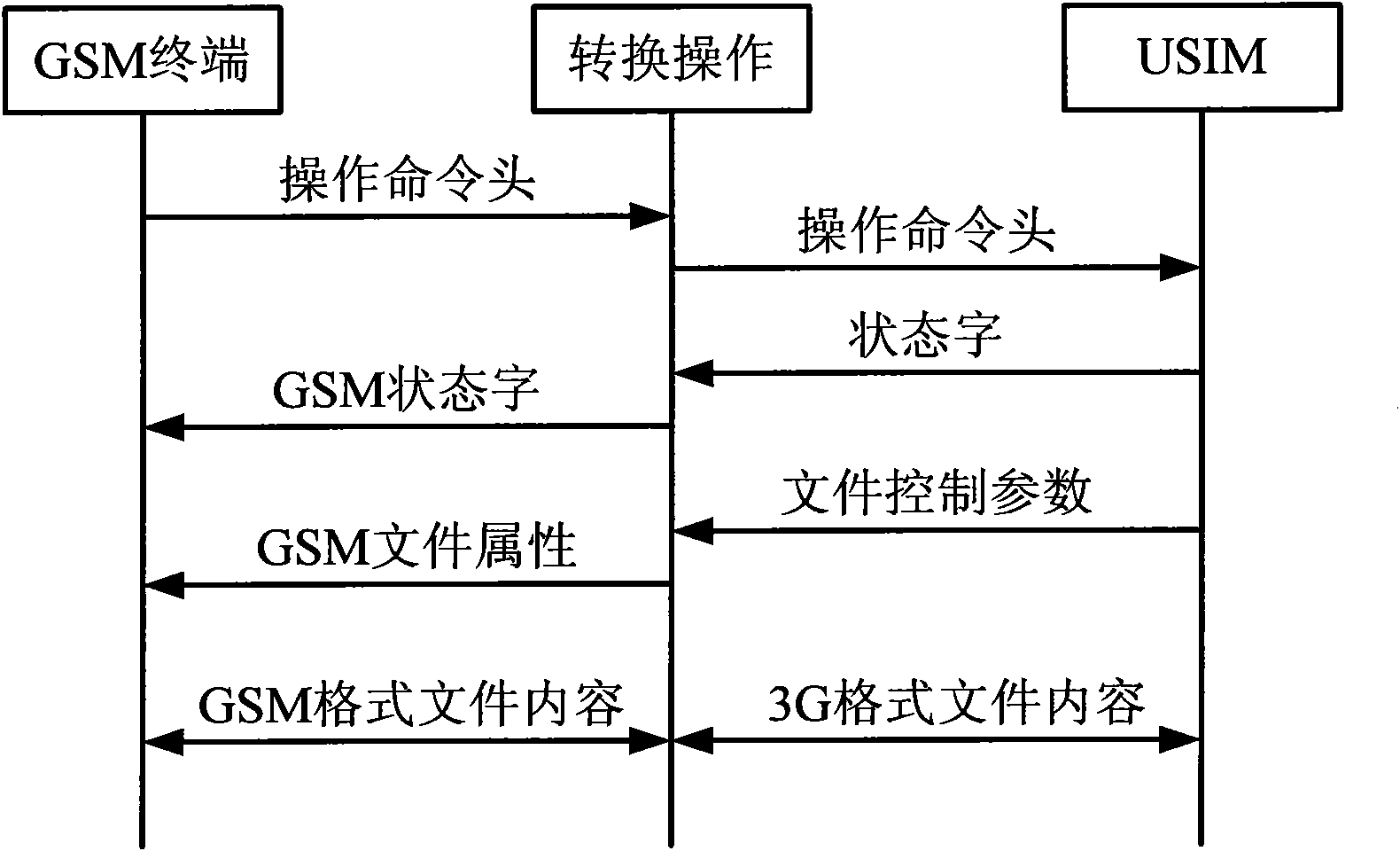
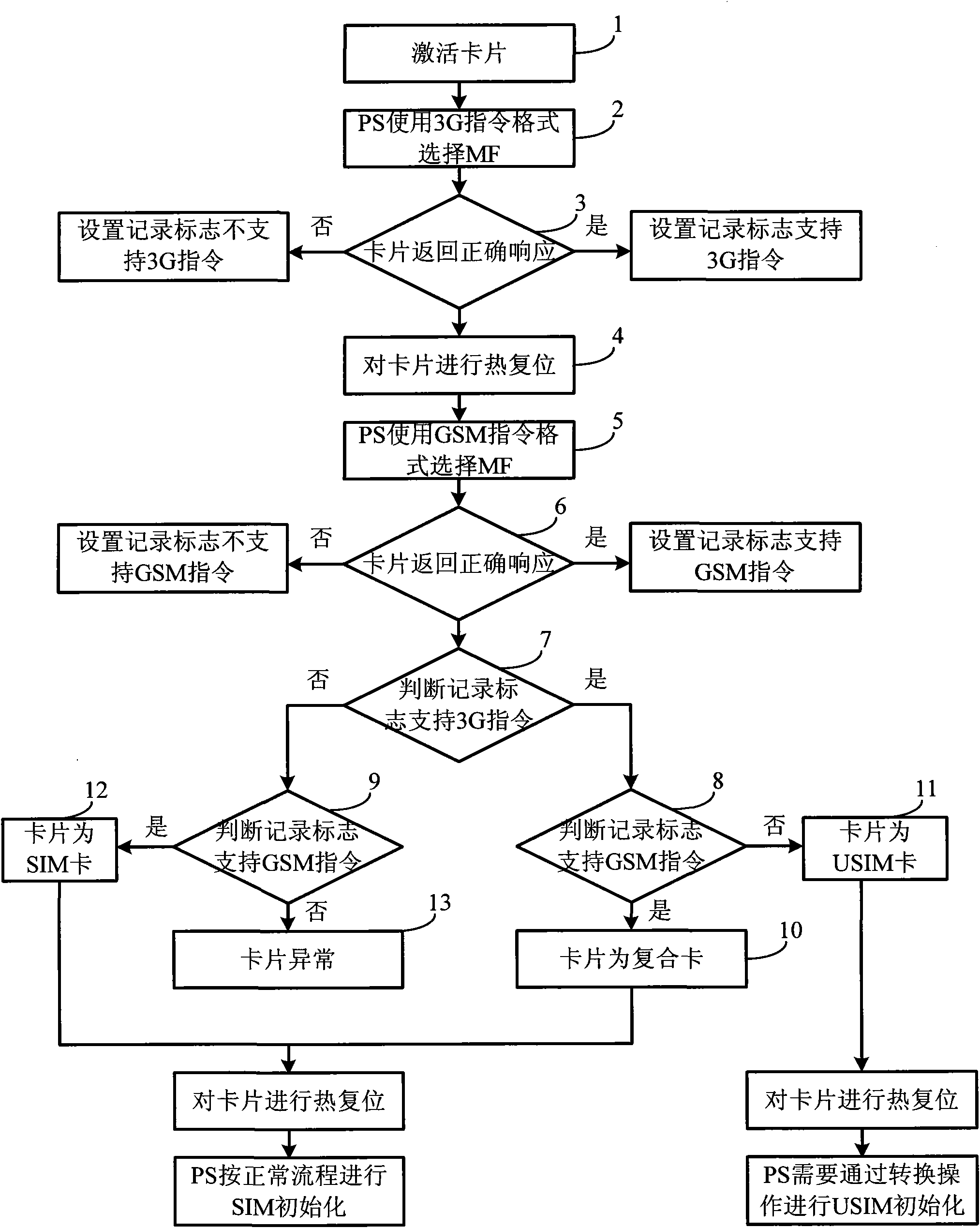
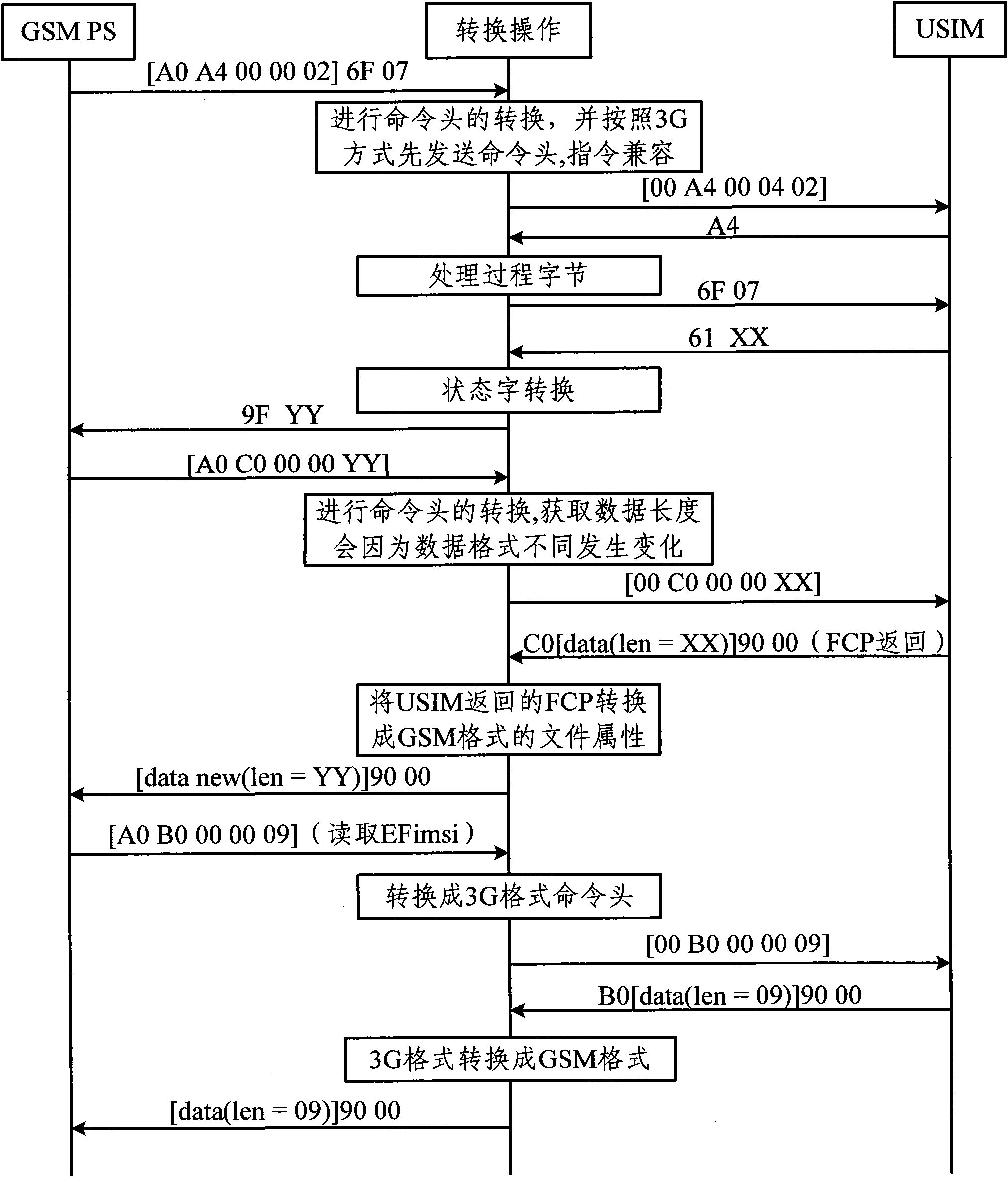
Method and device for realizing global system for mobile communications (GSM) terminal to access 3G universal subscriber identity module (USIM) card
ActiveCN102111487ANormal accessSubstation equipmentNetwork data managementControl parametersBusiness function
The invention provides a method and device for realizing a global system for mobile communications (GSM) terminal to access a 3G universal subscriber identity module (USIM) card. The method comprises the following steps: after a starting terminal activates a card, judging the type of a smart card which is inserted into a terminal in accordance with instruction conditions supported by the card; and if the smart card is the 3G USIM card, realizing information interaction between a GSM protocol stack and the card by conversion operations, wherein the conversion operations comprise the conversion of operating command heads which are sent to a USIM from the GSM terminal, the conversion of status words returned by the USIM into GSM status words, the conversion of file control parameters returned by the USIM into GSM file attributes, and the mutual conversion of 3G formatted file contents and GSM formatted file contents when the GSM terminal modifies or acquires USIM file contents. According to the invention, the protocol stack of the GSM terminal can access the 3G USIM card normally and acquire corresponding information from the 3G USIM card; and the 3G USIM card can realize fundamental service functions.
Owner:芯鑫融资租赁(天津)有限责任公司
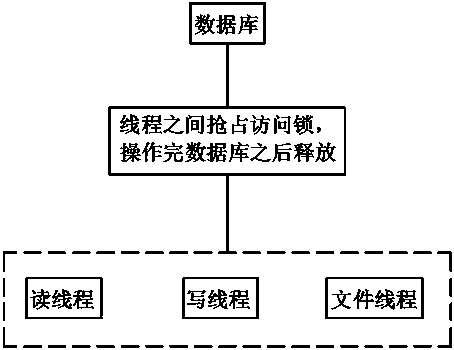
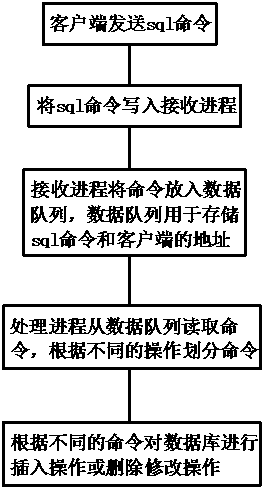
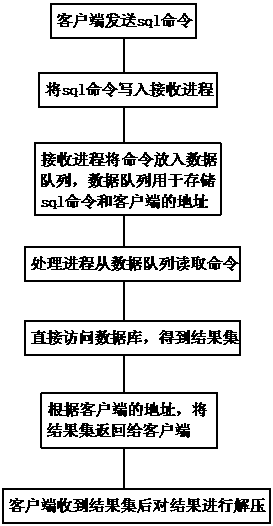
Method of securely accessing sqlite by multiple processes
InactiveCN109033359ANormal accessImprove access efficiencySpecial data processing applicationsWait stateComputer science
Owner:北京天地和兴科技有限公司
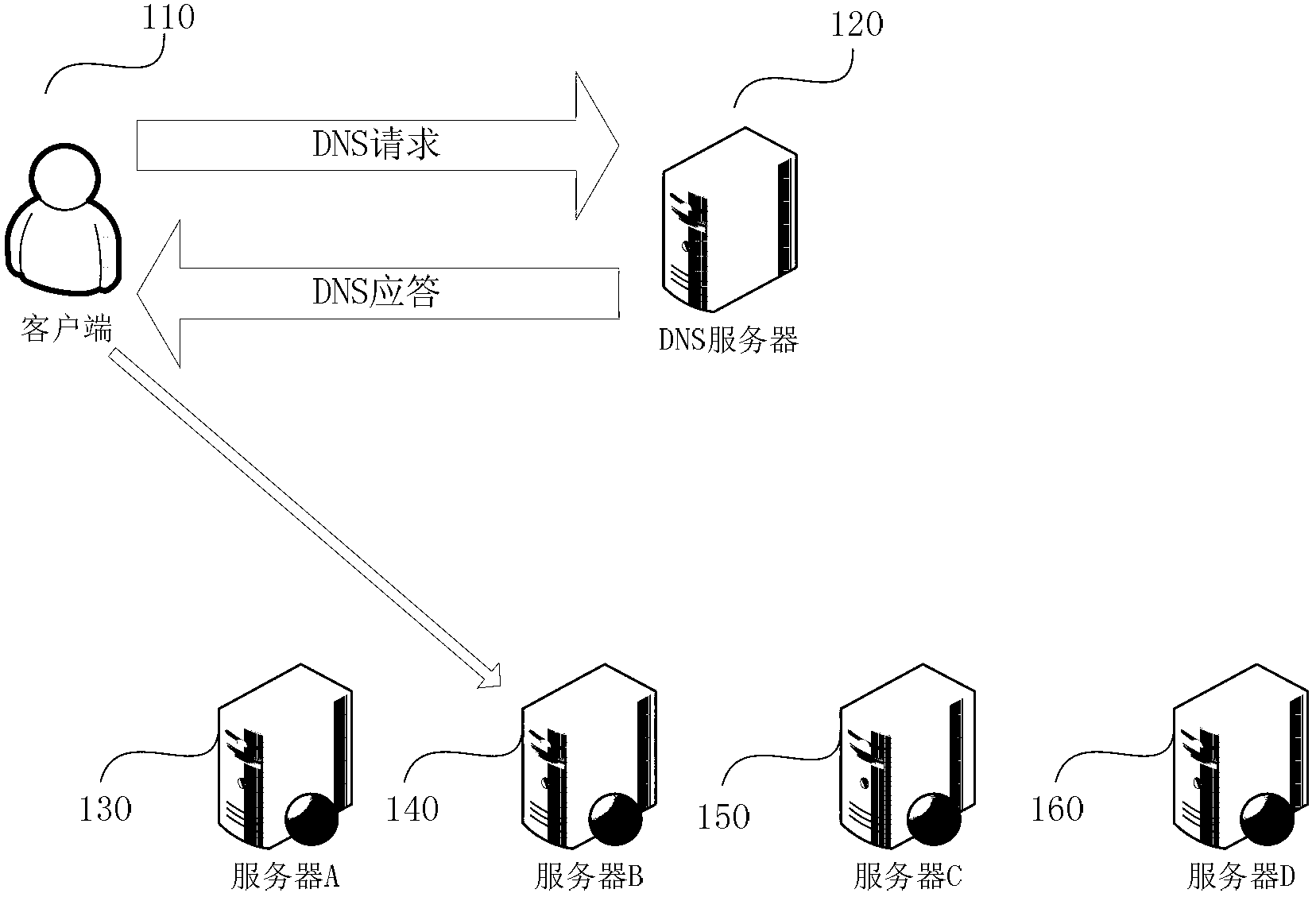
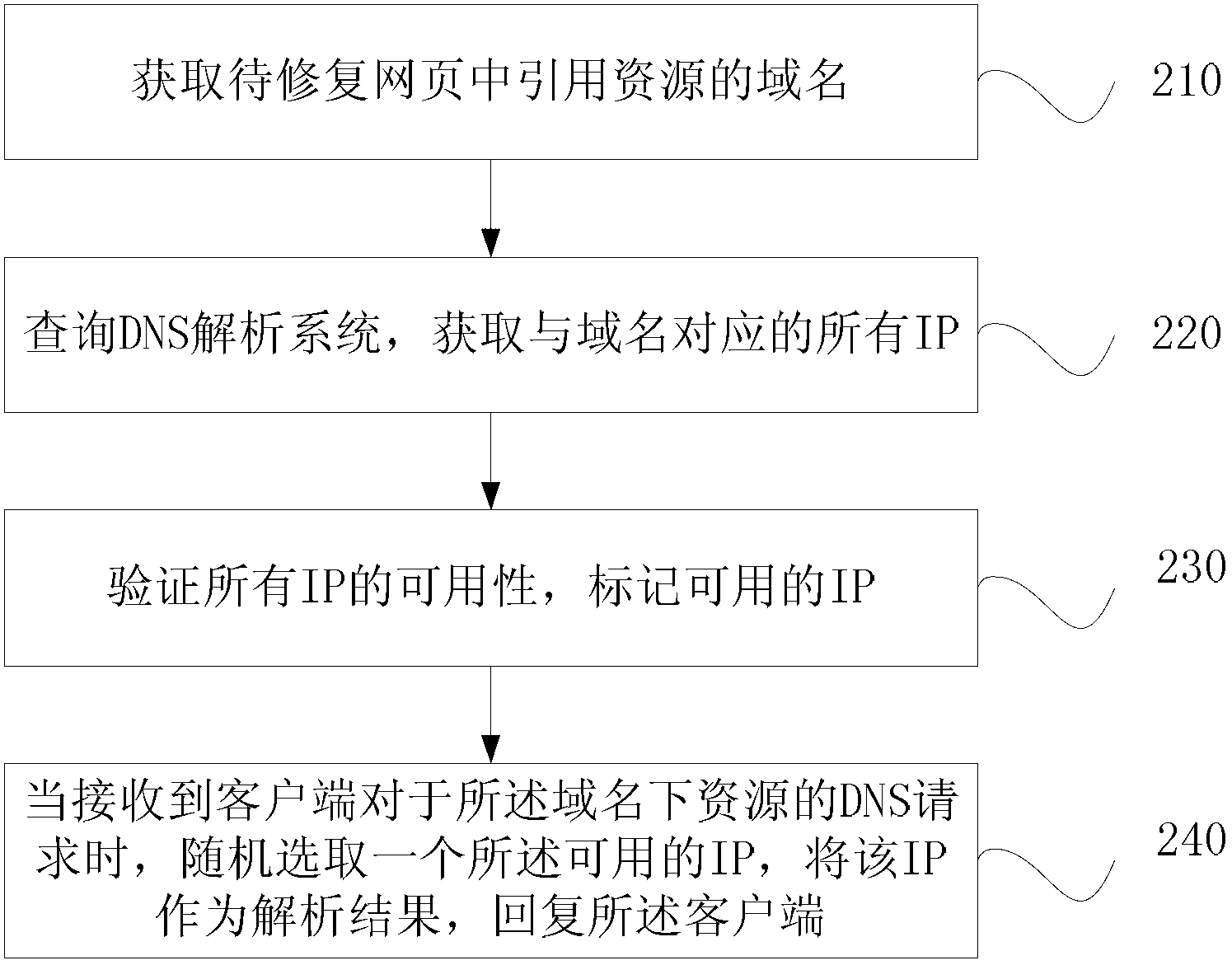
Method and device for repairing domain name system (DNS) polling mode-based webpages and server
The embodiment of the invention discloses a method and a device for repairing domain name system (DNS) polling mode-based webpages and a server. The method comprises the following steps of acquiring domain names of reference resources in to-be-repaired webpages; inquiring a DNS resolution system to acquire all internet protocols (IP) which correspond to the domain names; verifying the availability of all the IPs, and marking available IPs; and randomly selecting one available IP when a DNS request of a client side for the resources under the domain names is received, and replying the client side by taking the IP as a resolution result. According to the method disclosed by the embodiment of the invention, the problem that certain webpages can be normally visited sometimes, but cannot be visited sometimes due to the technology that DNS polling serves as load balancing is solved, so that users can visit the webpages more fluently.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
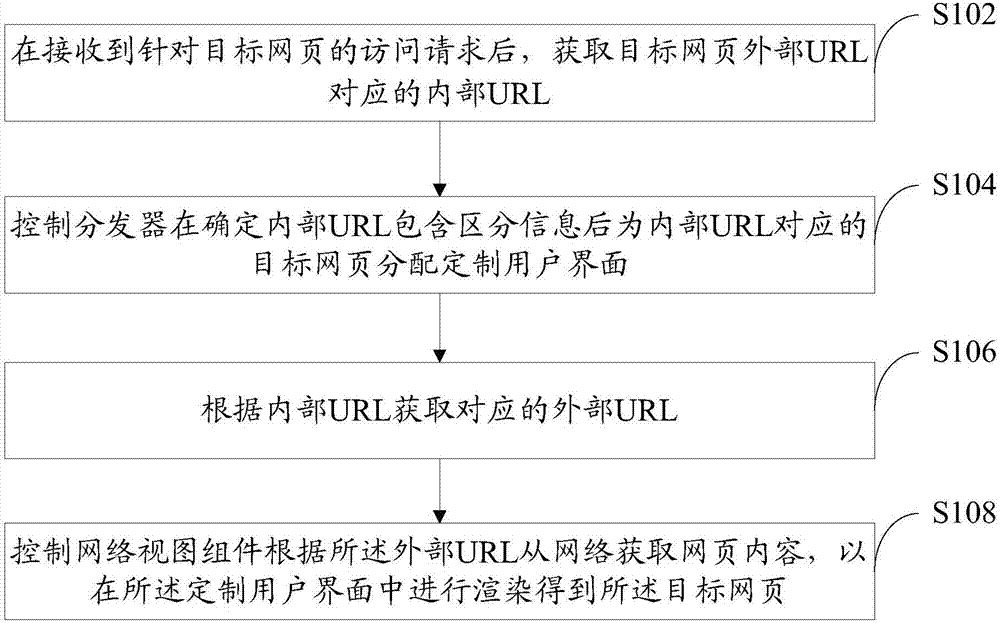
Webpage access method, terminal and computer readable storage medium
ActiveCN107423365ANormal accessShorten the timeSpecial data processing applicationsAccess methodUniform resource locator
The invention provides a webpage access method, a terminal and a computer readable storage medium. After receiving an access request for a target webpage from a user, the terminal acquires an internal URL according to an external URL of the target webpage, and distinguishes information via the condition that whether distinguishing information is carried in the internal URL to give a hint that the target webpage is an information stream webpage or a non-information stream webpage to a distributor, so that the distributor can directly determine that which kind of user interface should be distributed to the current target webpage according to the received internal URL; before access to the network for acquiring webpage content, the external URL can be recovered according to the internal URL, and normal network accessing is ensured. Therefore, according to the scheme of the method provided by the invention, a plenty of necessary retrieval work in existing schemes are avoided, time consumed for distribution the user interface in webpage accessing is saved, and waiting time of the user is reduced; meanwhile, consumption of processing resources is also reduced, blockage of a terminal browser is avoided, and user experience is further enhanced.
Owner:SHENZHEN FOUNTAIN HEAD TECH DEV CO LTD
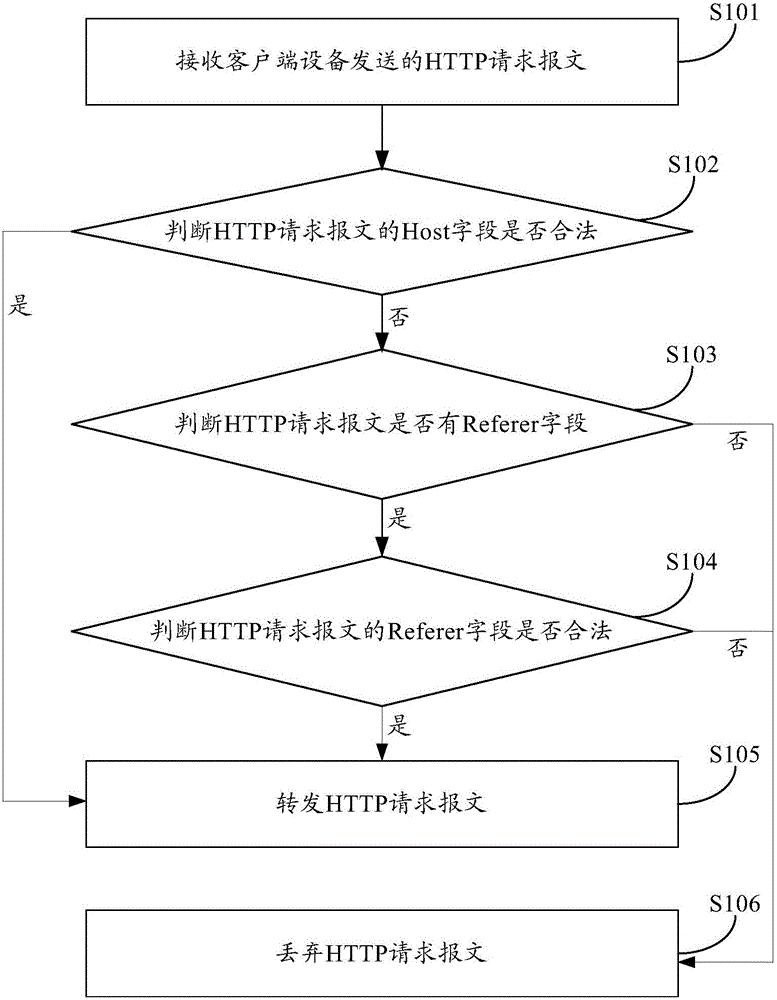
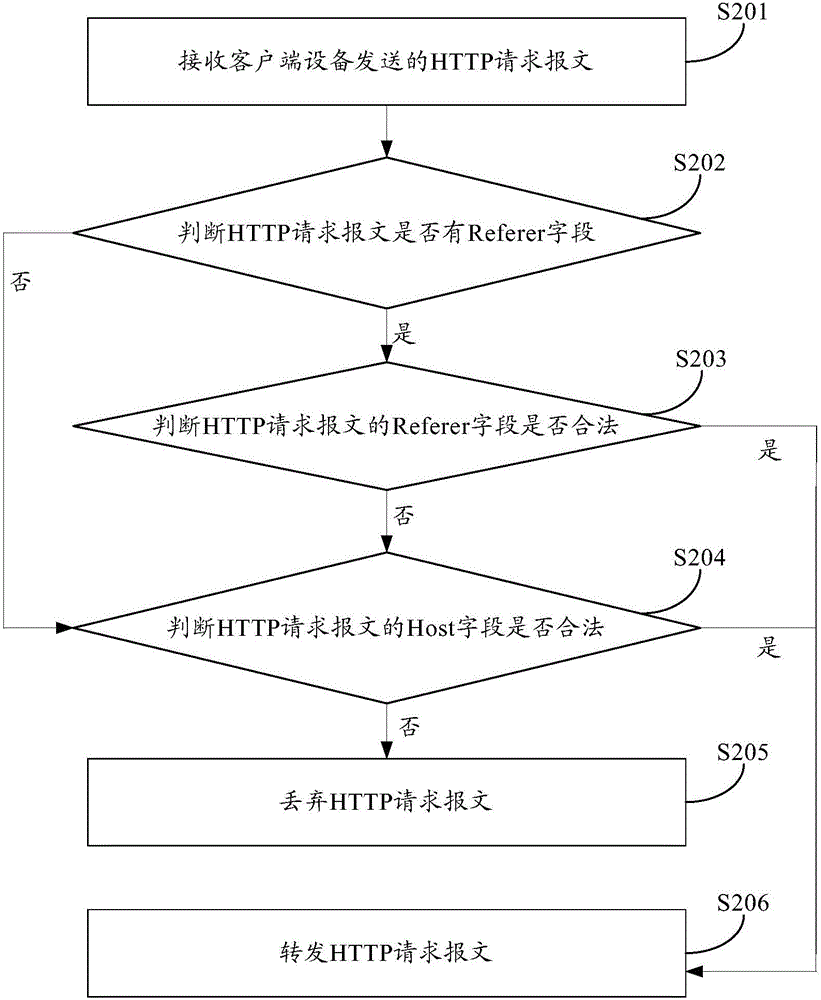
Access control method and apparatus
The present invention provides an access control method and an access control apparatus. The method includes the following steps that: a HTTP request message sent by a client device is received; and when it is determined that at least one of a Referer field and a Host field which are carried by the HTTP request message is legitimate, the HTTP request message is forwarded. With the access control method and the access control apparatus provided by the embodiments of the invention, the legitimacy of the Referer field and the Host field which are carried by the HTTP request message is judged, when at least one of the Referer field and the Host field is legitimate, the HTTP request message is forwarded, and therefore, the client device can normally access corresponding websites, and a situation that legitimate websites are mistakenly judged as illegal websites can be avoided to the greatest extent, and the false alarm rate of website filtering can be reduced, and the client device can normally access the legitimate websites, and user experience can be improved.
Owner:HANGZHOU DPTECH TECH
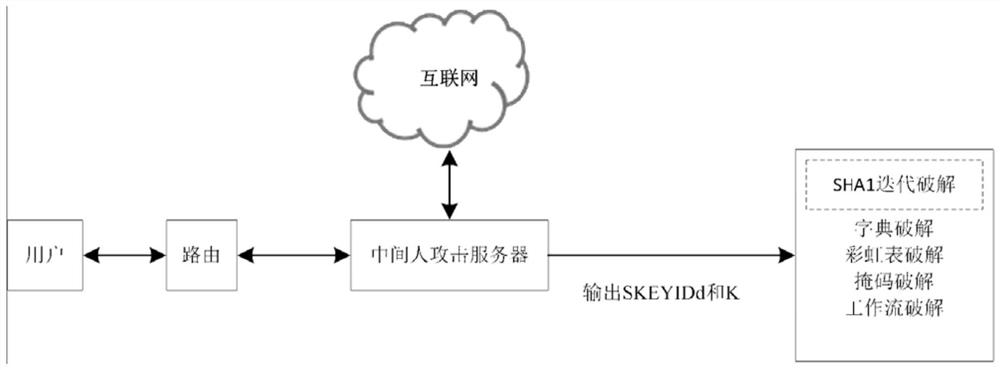
L2TP/IPSEC cracking method and system based on high-performance computing
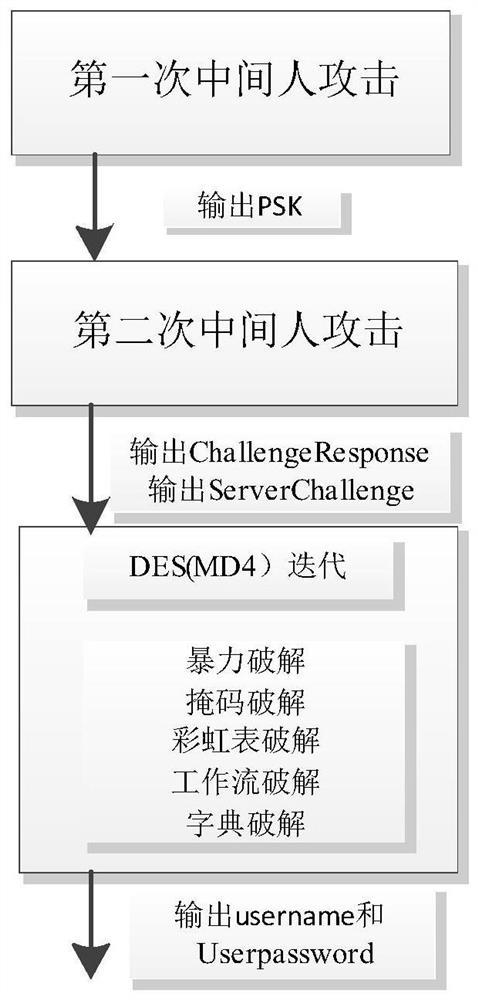
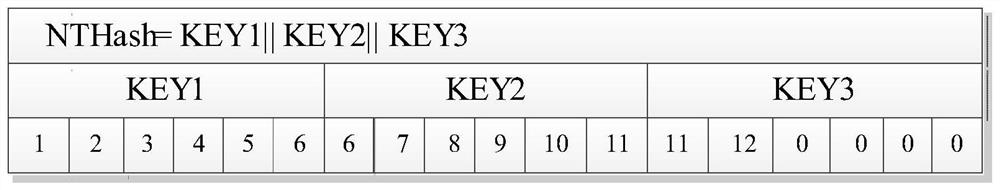
InactiveCN111835499ANormal accessDoes not affect normal useCryptographic attack countermeasuresServer agentData stream
The invention relates to the technical field of information security. The invention discloses an L2TP / IPSEC cracking method and system based on high-performance computing. The cracking method comprises the steps of cracking a pre-shared key, cracking a login password and realizing encryption information decryption in combination with data flow redirection. The cracking system comprises a traffic intercepting and forwarding module, a man-in-the-middle server management end and a man-in-the-middle server proxy end. According to the invention, man-in-the-middle attack is adopted firstly and thena violent cracking mode is adopted; the weakness of Diffie-Hellman is utilized to carry out man-in-the-middle attack for three times; the cracking of the pre-shared key is completed by the first man-in-the-middle attack; the second man-in-the-middle attack completes cracking of the login password, the third man-in-the-middle attack is combined with data flow redirection to achieve encryption information decryption, in the password cracking process, a user can normally access the Internet, and the method is a cracking method which is free of perception and does not have influence on the user touse the VPN.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method, gateway and network access system for controlling data acquired by mobile terminal
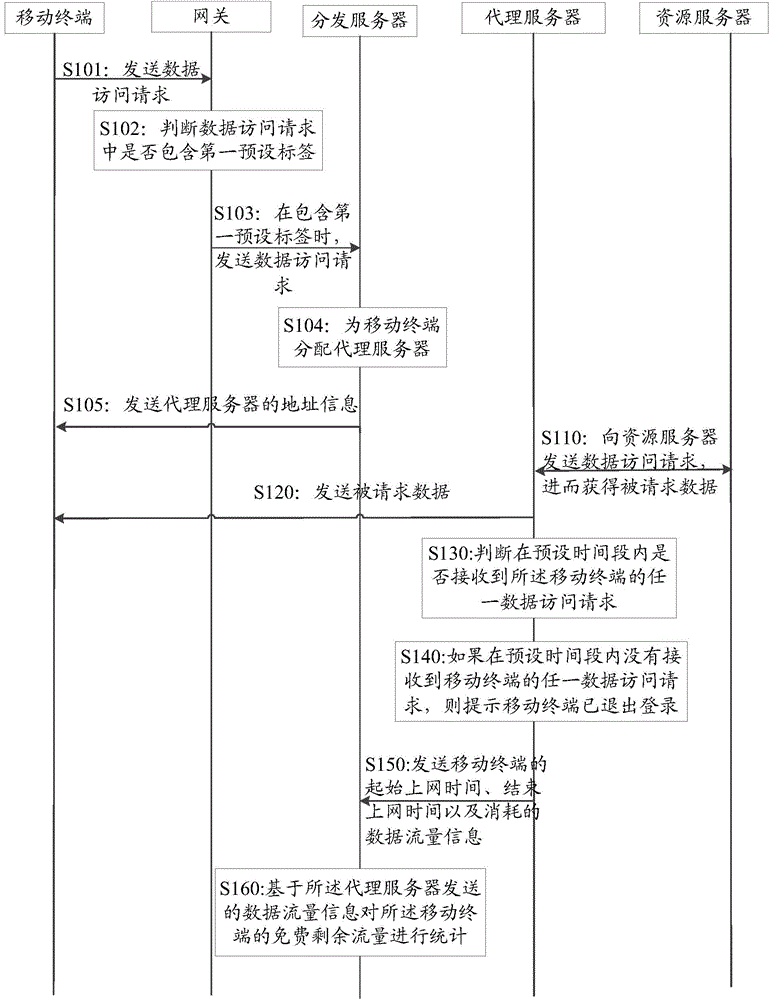
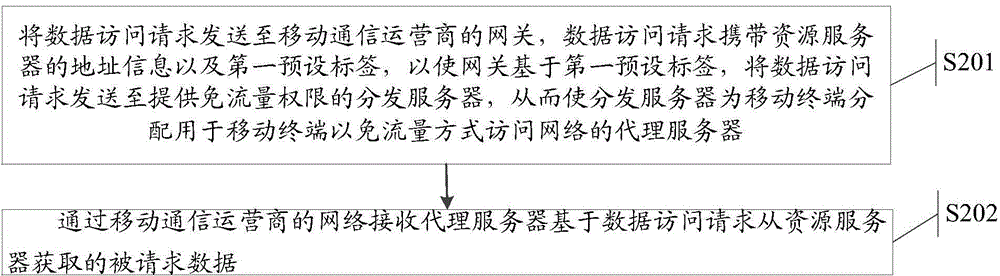
ActiveCN104902454AIncrease motivationData Access Request PreciseAccounting/billing servicesNetwork data managementTraffic capacityNetwork access server
The invention relates to the field of communication, and discloses a method, a gateway and a network access system for controlling data acquired by a mobile terminal. The technical problem that network access in the prior art needs to consume a large amount of data flow of a mobile terminal is solved. The method comprises the following steps of receiving a data access request transmitted by the mobile terminal by using the gateway; judging whether the data access request contains a first preset label or not; transmitting the data access request to a distribution server providing flow-free authority if the data access request contains the first preset label so that the distribution server is an agency server which is used for the mobile terminal to visit a network in a flow-free mode; and reckoning all or part of data flow which is consumed in a network access process of the mobile terminal through the agency server in an appointed service provider by a mobile network operator on the basis of a flow-free mark. The data access request contains address information of a resource server. The technical effect of reducing data flow consumed in the network access process of the mobile terminal is achieved.
Owner:北京鸿享技术服务有限公司
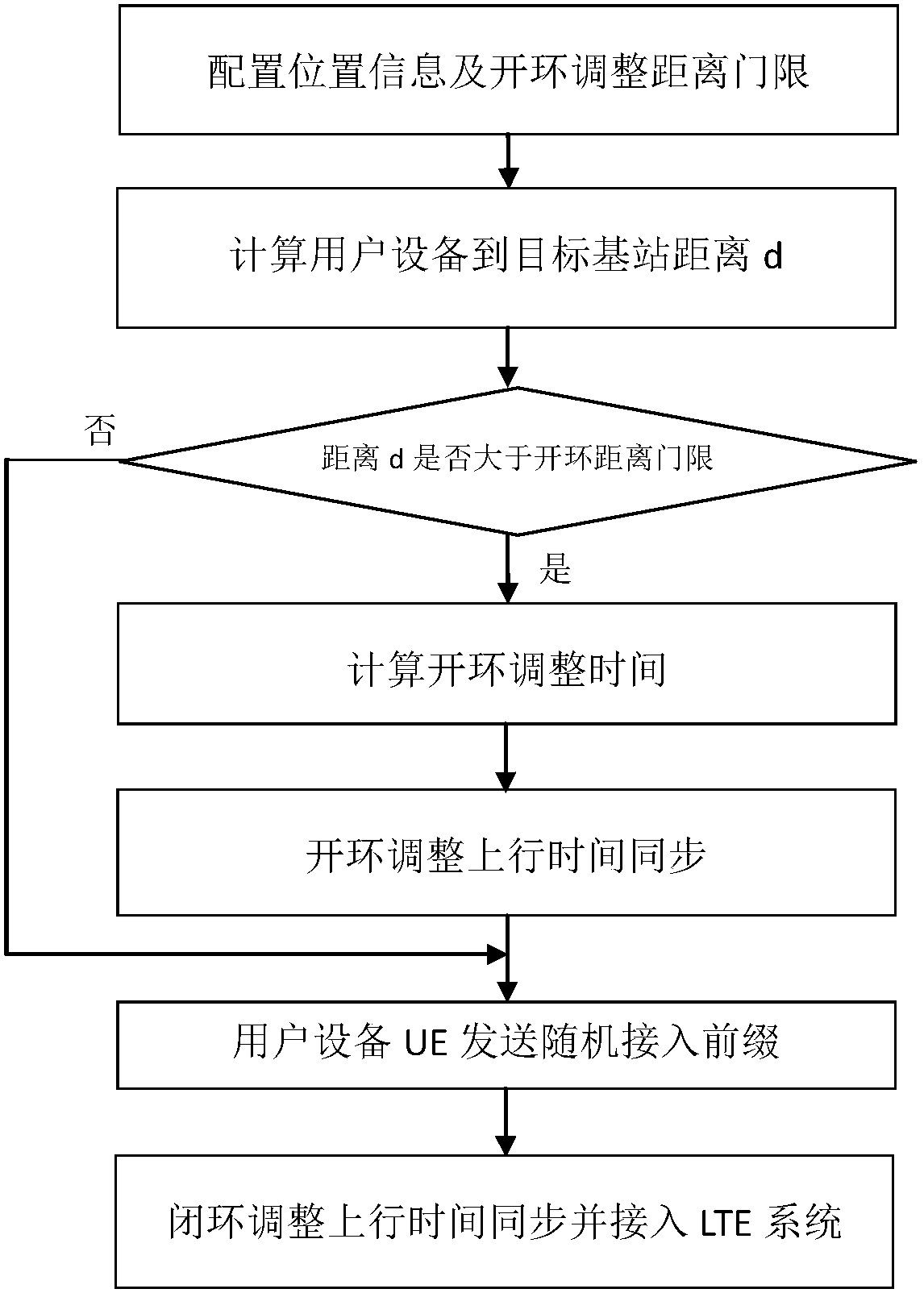
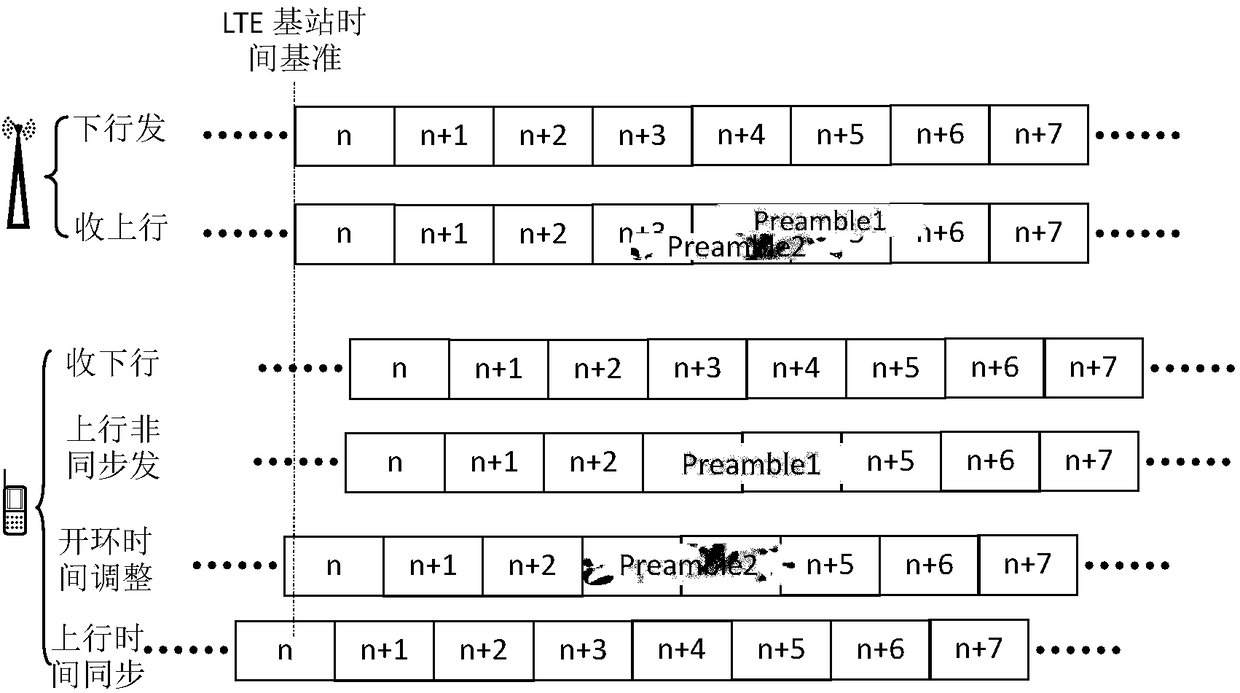
GPS assistance-based LTE ultra-long-distance coverage random access method
InactiveCN108737963AExpand coverageNormal accessSynchronisation arrangementTime-division multiplexRADIUSRandom access
The invention discloses a GPS assistance-based LTE ultra-long-distance coverage random access method, which mainly solves the problem that the LTE coverage area in the prior art is small, and the userequipment UE outside the maximum coverage radius cannot successfully access the network. The technical scheme is as follows: 1) configuring location information and an uplink timing open loop adjustment distance threshold; 2) calculating the distance from the user equipment to a target base station; 3) judging whether the distance from the user equipment to the target base station is greater thanthe open loop distance threshold; 4) calculating open loop adjustment time; 5) synchronizing the open loop adjustment uplink time; 6) sending a random access prefix sequence; 7) synchronizing closedloop adjustment uplink time and accessing to an LTE system. The GPS assistance-based LTE ultra-long-distance coverage random access method in the invention expands the coverage area of the LTE base station and improves the uplink resource utilization, so that the user equipment UE located outside the maximum coverage area of the existing LTE can successfully complete network access process and uplink time synchronization with the assistance of the GPS.
Owner:XIDIAN UNIV
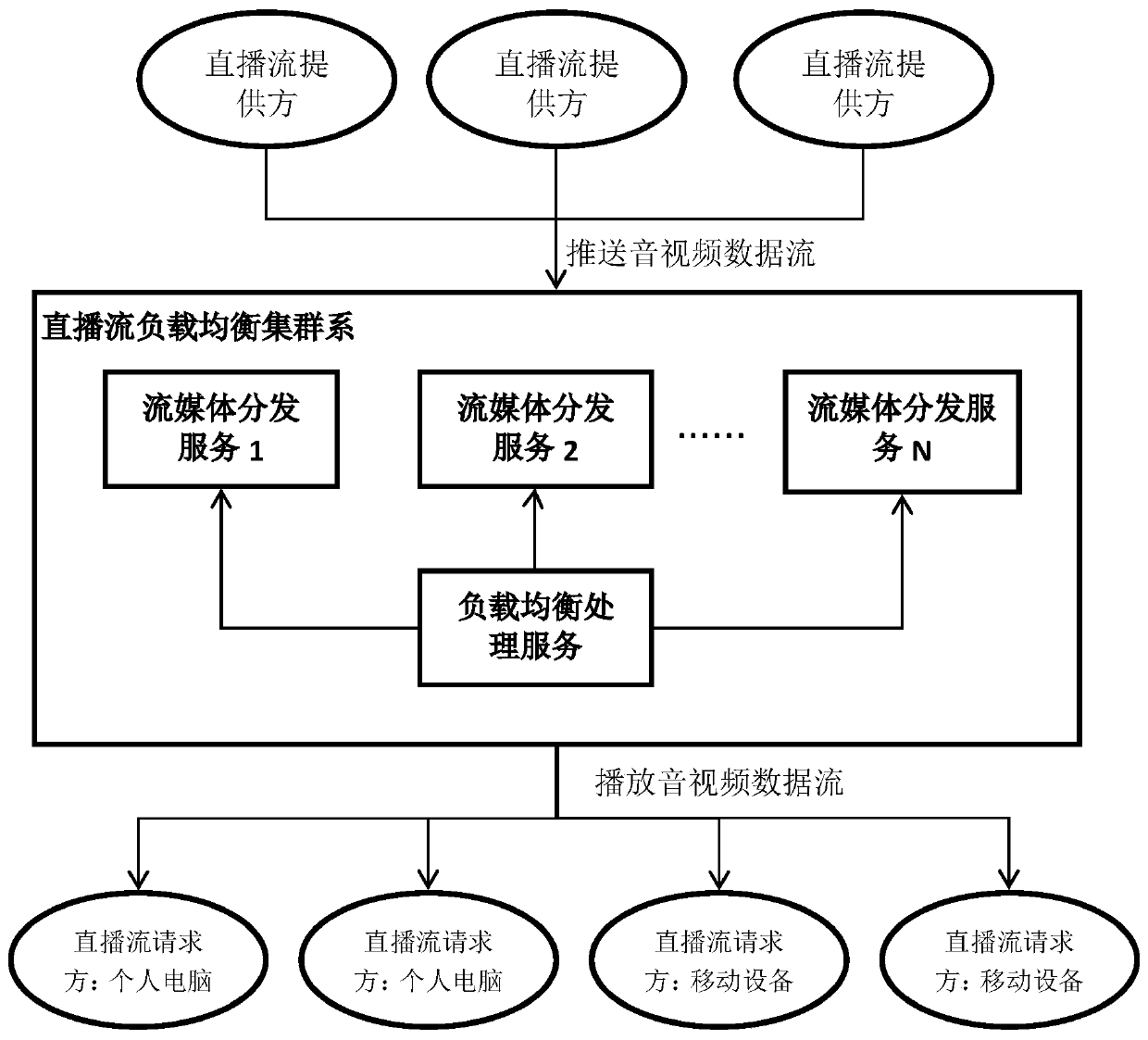
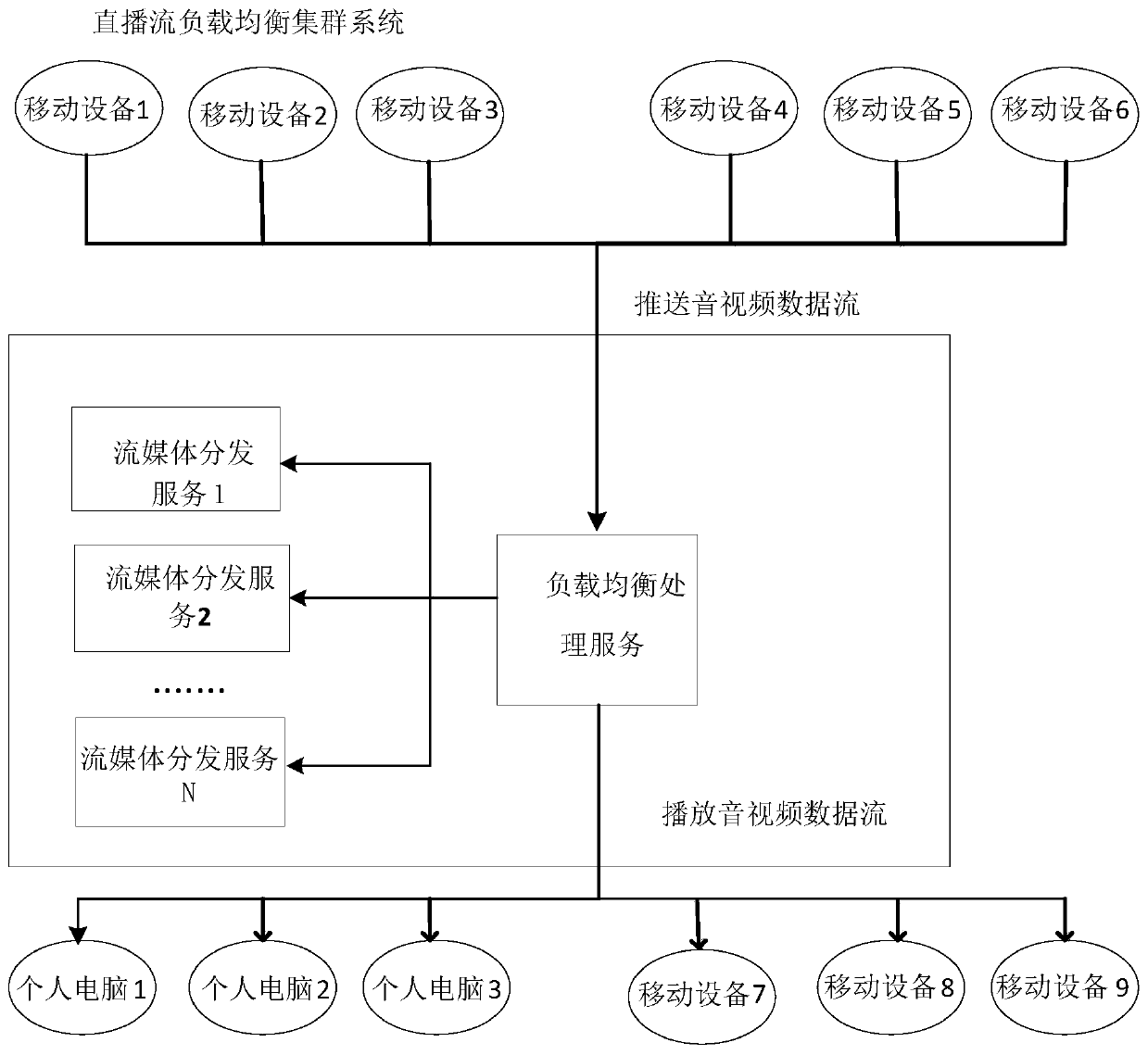
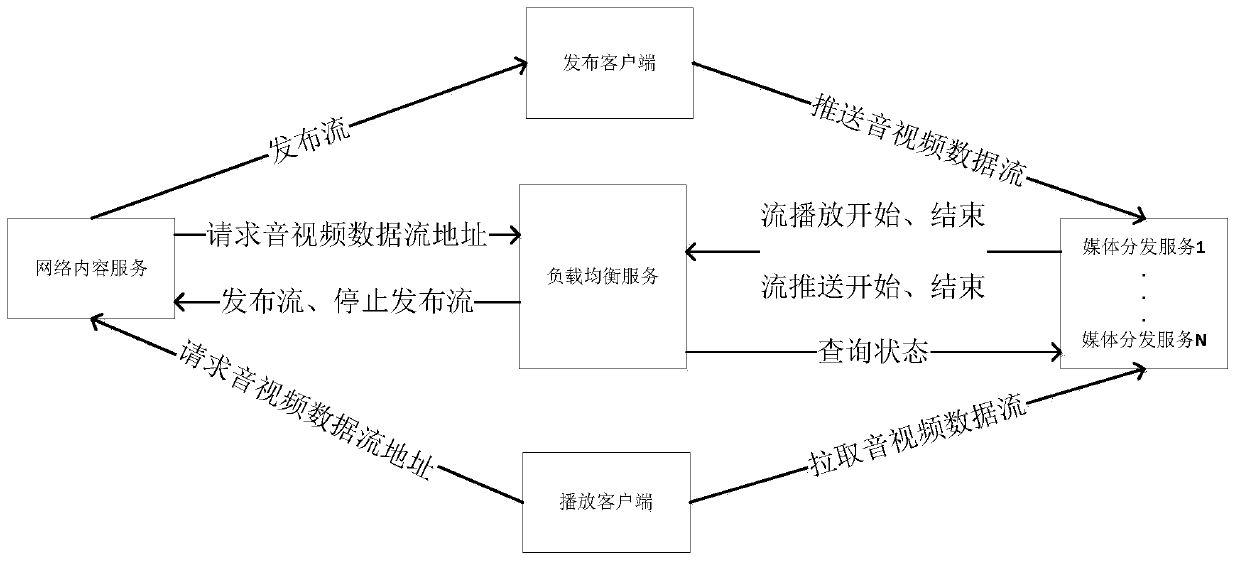
Live stream load balancing algorithm based on RTMP
ActiveCN110300306ANormal accessImprove fault toleranceSelective content distributionComputer networkSingle point of failure
The invention discloses a live stream load balancing specific implementation algorithm based on an RTMP protocol. The method is applied to an engineering application scene deployed by a plurality of streaming media distribution servers, through the load balancing processing algorithm, services of different live streams can be uniformly shared to all streaming media distribution servers in a project, the maximum utilization of server hardware resources is ensured, and the problem that the live streams cannot be normally supported due to a single point fault is effectively solved; meanwhile, thealgorithm also supports reuse and distribution of the live streams with the same repeated requests for multiple clients at the streaming media distribution server, thereby reducing the pressure of alive stream provider and optimizing the live stream playing efficiency.
Owner:武汉微创光电股份有限公司
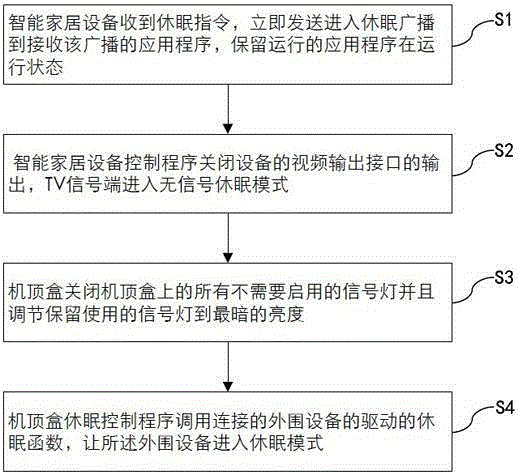
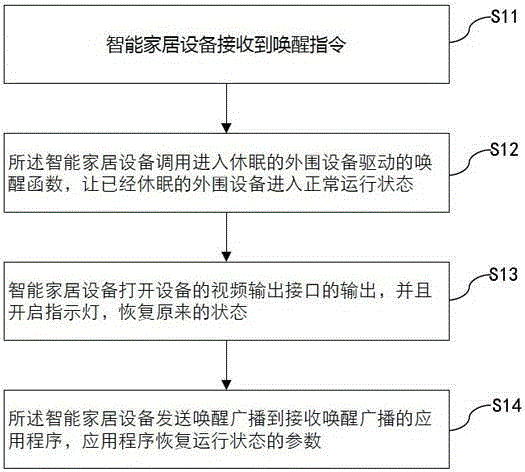
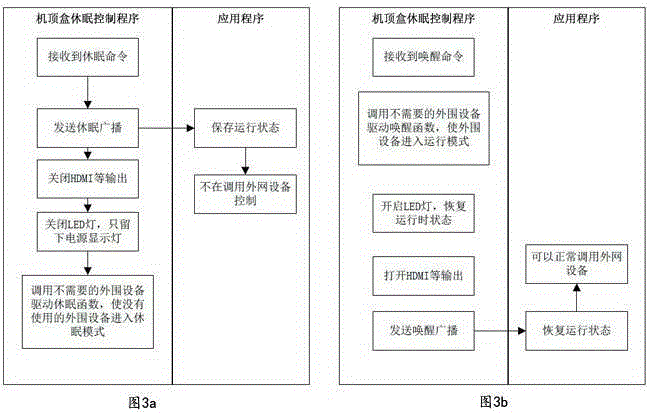
Intelligent household equipment sleep method capable of performing network accessing
The invention provides an intelligent household equipment sleep method capable of performing network accessing. The method comprises the steps that intelligent household equipment receives a sleep instruction and instantly transmits sleep entering broadcast to an application program receiving the broadcast, and the operating application program is maintained at the operating state; an intelligent household equipment control program shuts down output of the video output interface of the equipment, and a TV signal side enters a no signal sleep mode; a set top box shuts down all the signal lamps, which are not required to be started, on the set top box and adjusts the reserved signal lamps to be the lowest brightness; and a set top box sleep control program calls the sleep function of the driver of the connected peripheral equipment so that the peripheral equipment is enabled to enter the sleep mode. With application of the intelligent household equipment sleep method capable of performing network accessing, the set top box is enabled to be normally accessed through the network under the premise of guaranteeing power saving in comparison with methods in the prior art.
Owner:MEIBEIKE TECH CO LTD
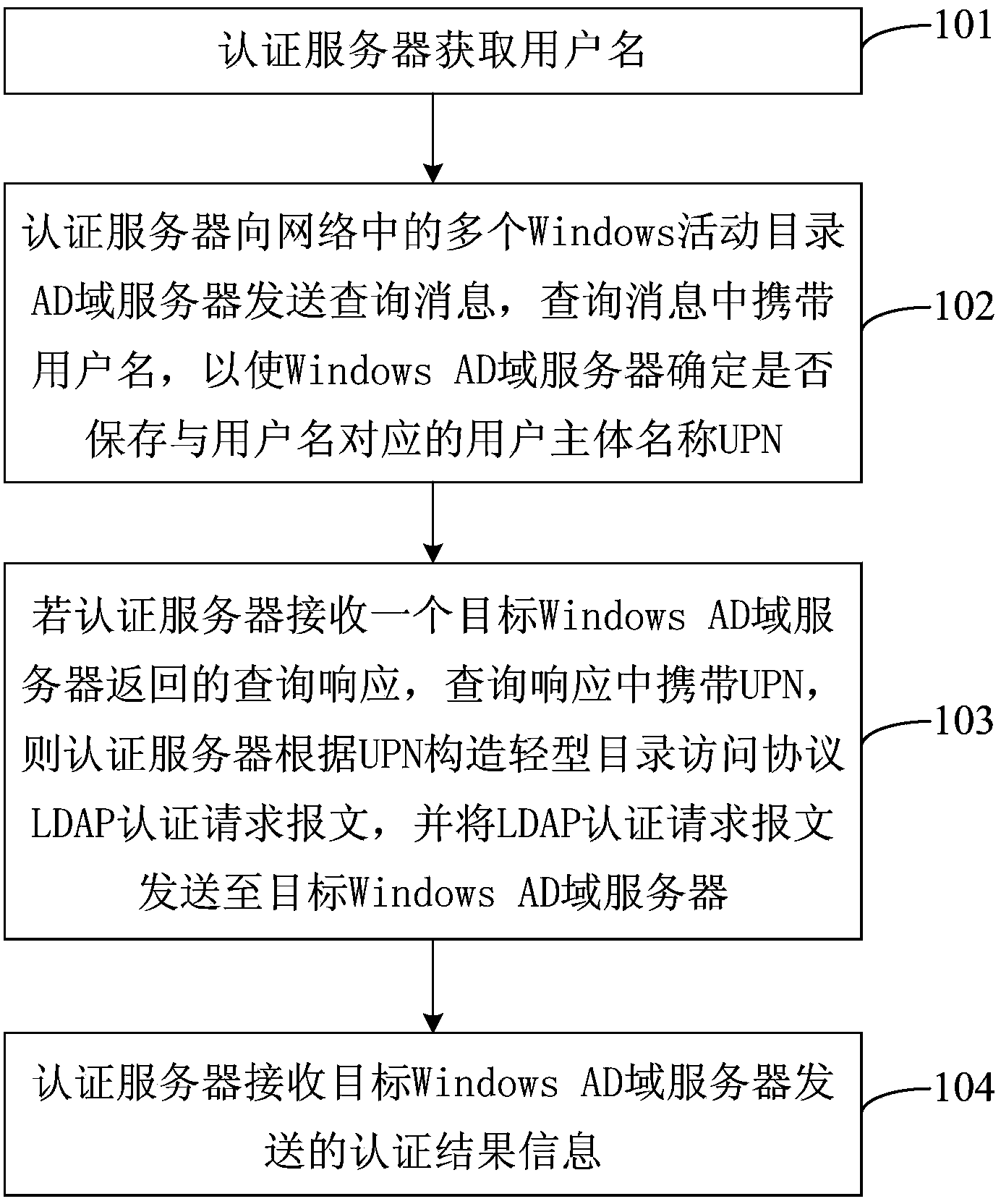
Authentication method, authentication server and authentication system
The invention provides an authentication method, an authentication server and an authentication system. The authentication server sends inquiry information with a user name to multiple Windows AD domain name servers in a network after obtaining the user name so that the Windows AD domain name servers can determine whether to store a user principal name UPN corresponding to the user name, if an inquiry response carrying the UPN and fed back by a target Windows AD domain server is received, a lightweight directory access protocol (LDAP) authentication request message is constructed according to the UPN and sent to the target Windows AD domain server, and authentication result information sent by the target Windows AD domain server is received. The authentication server constructs the LDAP authentication request message according to the UPN corresponding to the user name and sent by the Windows AD domain server, subdomain user authentication can be successfully carried out, and accordingly a computer corresponding to the user can normally have access to network communication.
Owner:RUIJIE NETWORKS CO LTD
Function extension method based on WEB browser and terminal device
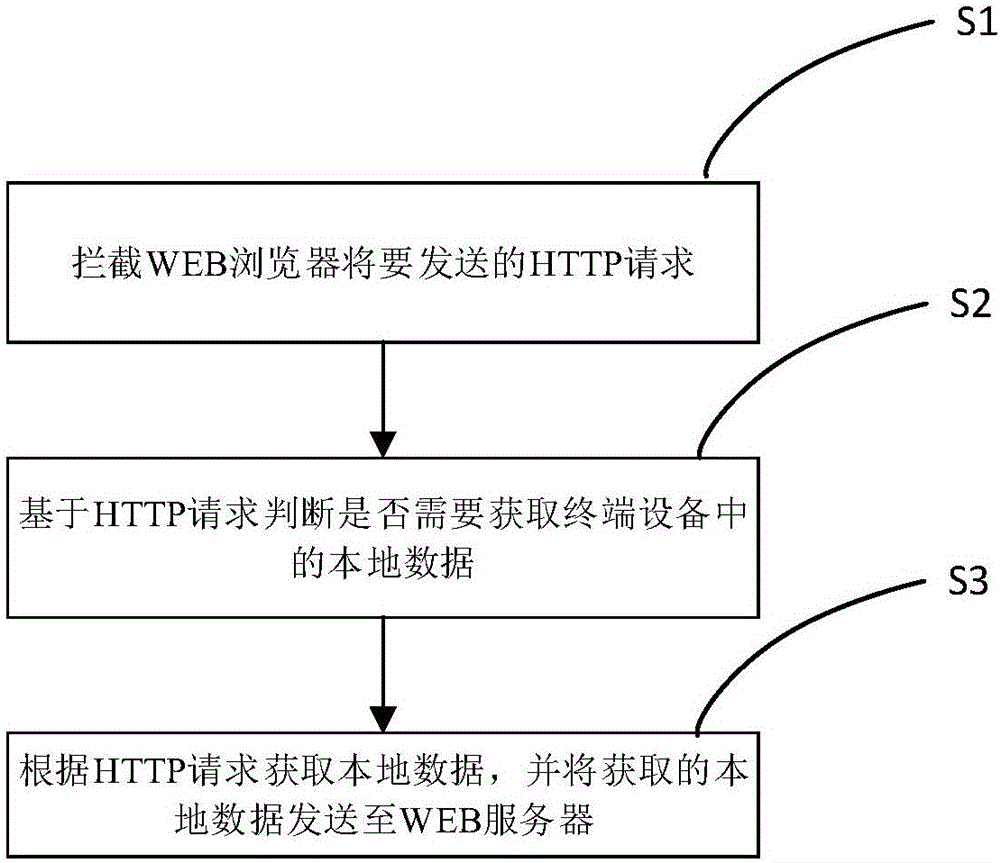
The invention discloses a function extension method based on a WEB browser. The WEB browser does not support a plug-in extension function. The method comprises the following steps: S1, intercepting an HTTP request to be sent by the WEB browser; S2, judging whether local data in a terminal device needs to be obtained based on the HTTP request, executing the step S3 if yes, and forwarding the HTTP request to a WEB server if no; and S3, obtaining the local data according to the HTTP request, and sending the obtained local data to the WEB server. According to the function extension method based on the WEB browser and the terminal device disclosed by the invention, the function extension can be carried out on the browser in a non-plug-in manner, so that an application system can carry out normal access on local system resources, local hardware peripherals and the like via the browser, and whether the browser supports a plug-in function does not need to be considered.
Owner:BEIJING SENSESHIELD TECH
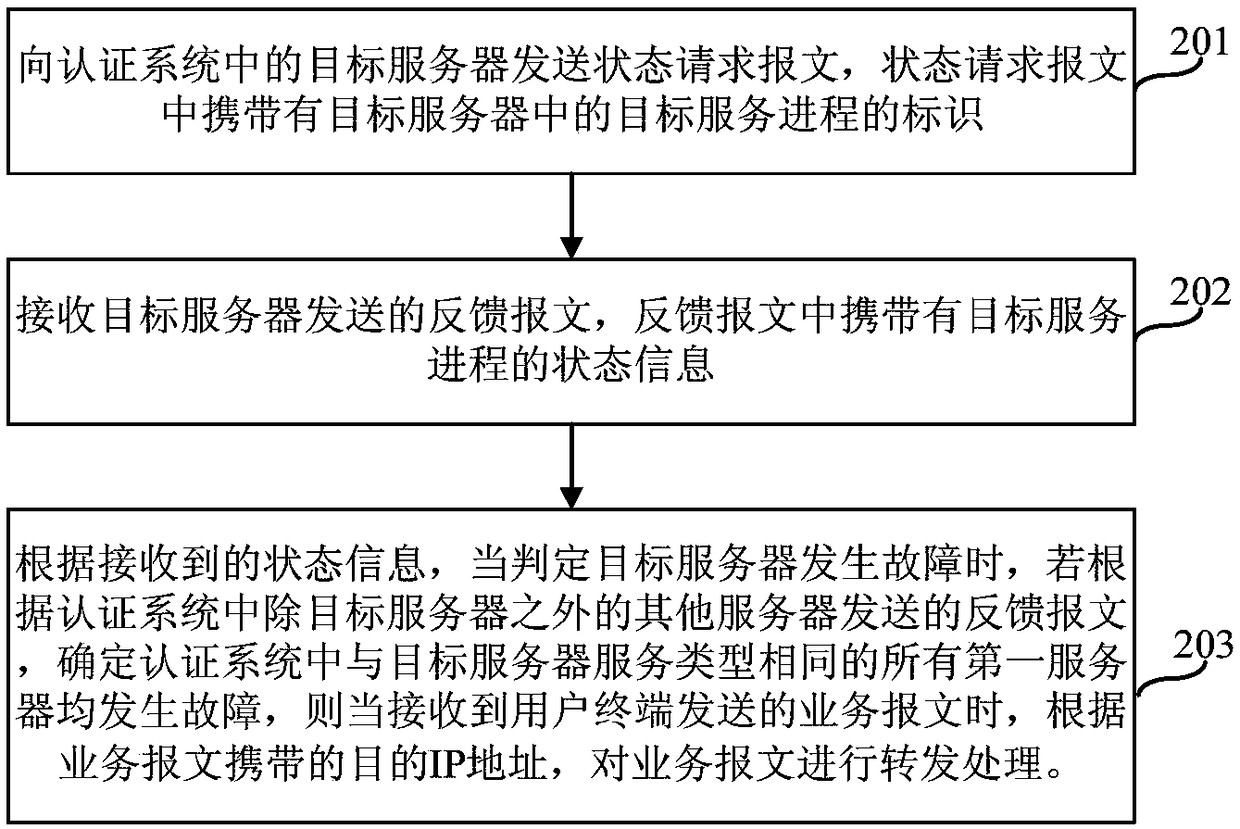
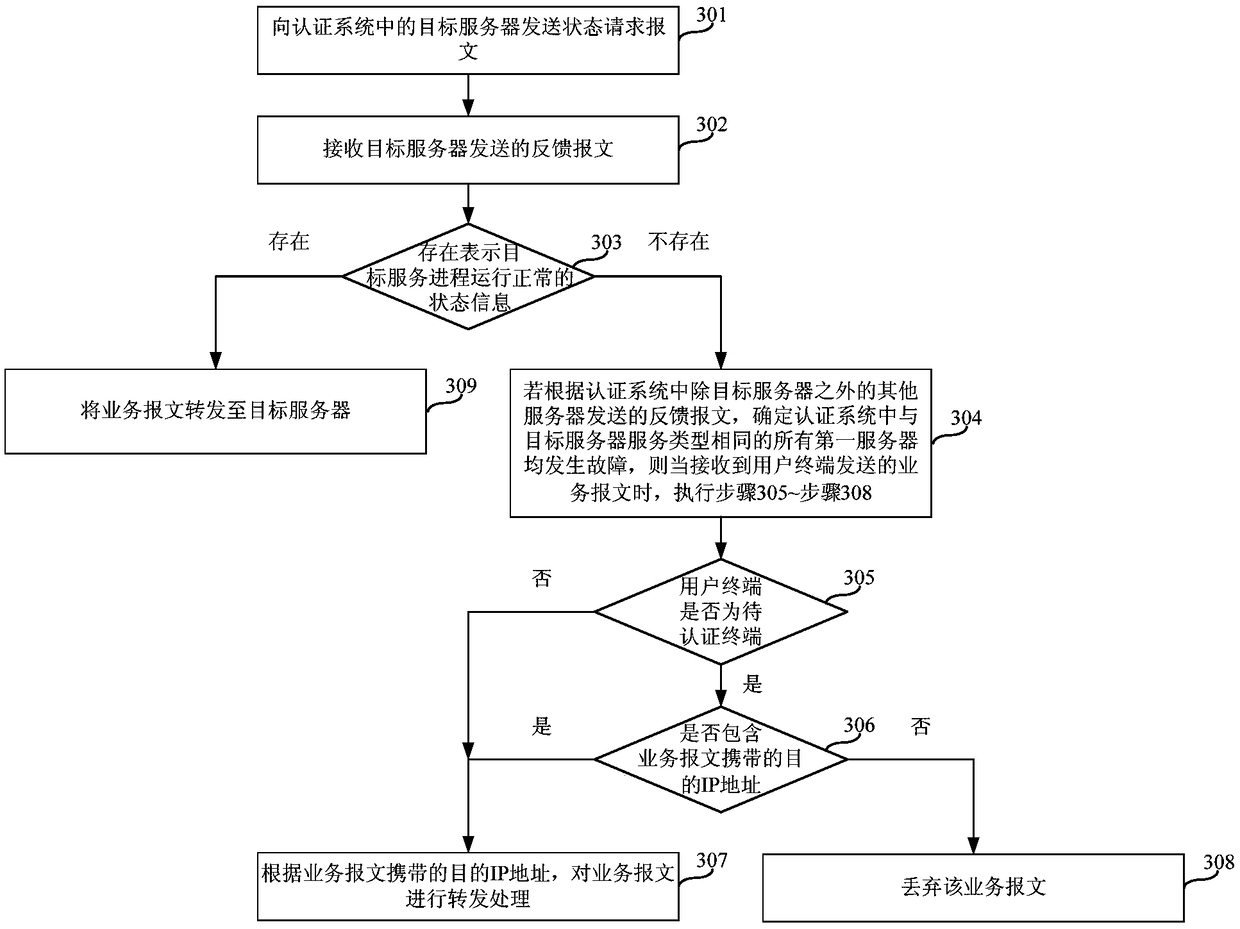
Service message processing method and apparatus
ActiveCN108769016ANormal accessTimely monitoring of faultsData switching networksIp addressMessage processing
The embodiment of the invention provides a service message processing method and apparatus, and relates to the technical field of communication. The method is applied to an access device, and the method comprises the following steps: sending a state request message to a target server in an authentication system; receiving a feedback message sent by the target server, wherein the feedback message carries the state information of a target service process; and according to the received state information, when it is judged that the target server is faulty, if it is determined that all first servers having the same service type as the target server in the authentication system are faulty according to the feedback messages sent by the other servers excluding the target server in the authentication system, then when a service message sent by a user terminal is received, performing forwarding processing on the service message according to a destination IP address carried in the service message. By adoption of the service message processing method and apparatus provided by the invention, it can be ensured that users access the network normally.
Owner:NEW H3C SECURITY TECH CO LTD
Video monitoring system based on cloud platform
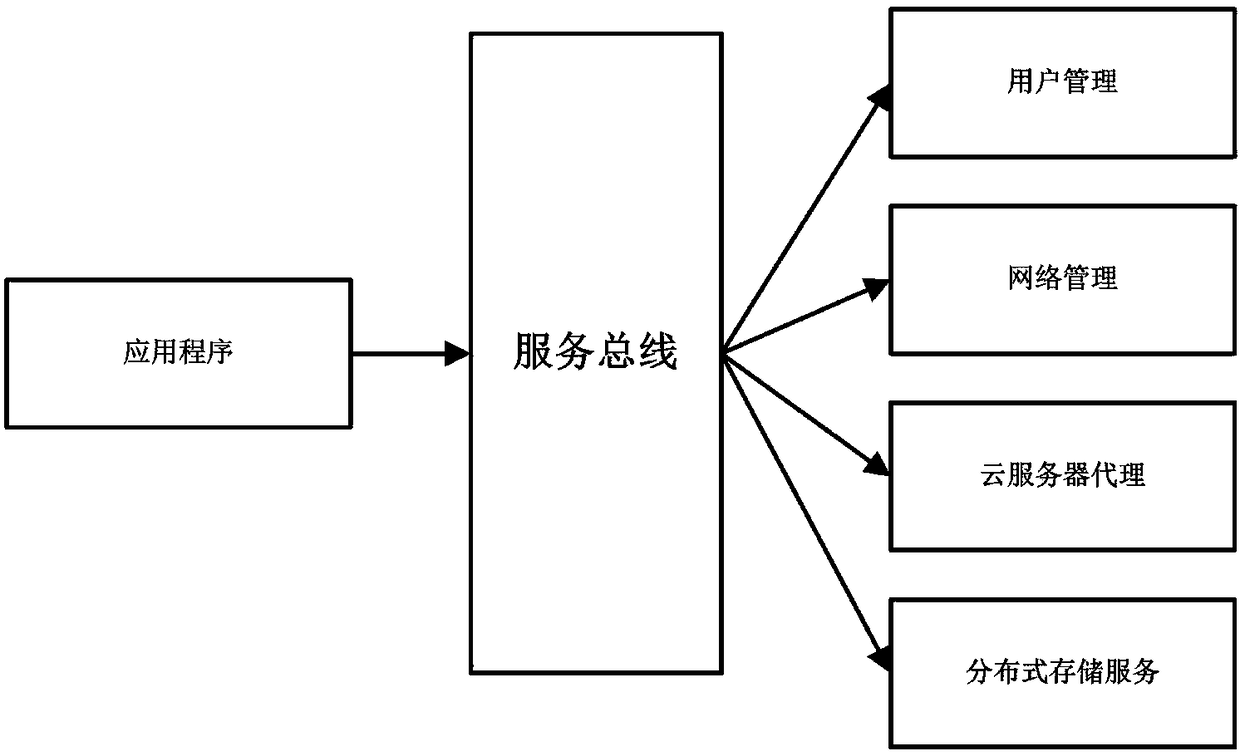
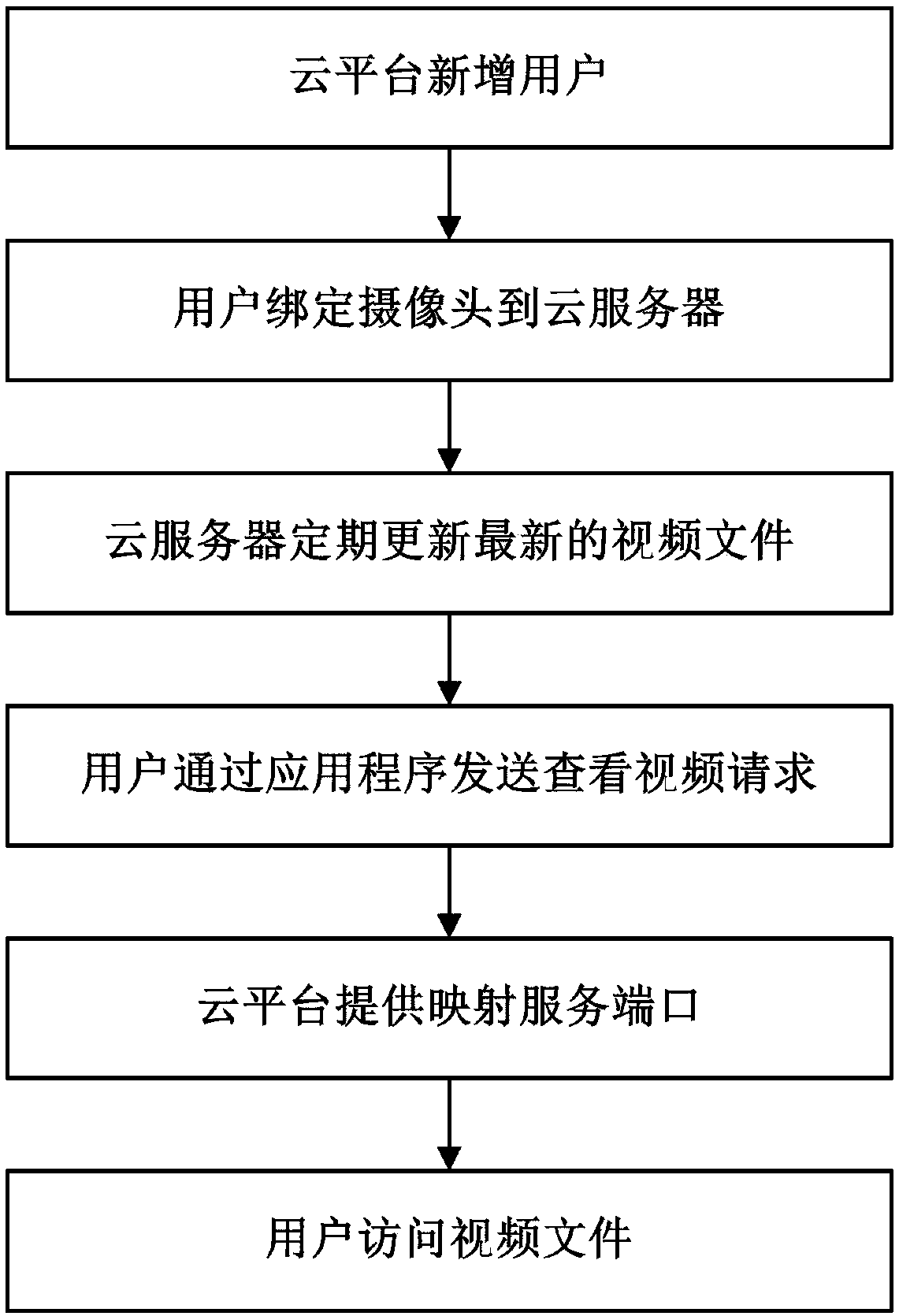
InactiveCN108495082AImprove securityPrevent breachClosed circuit television systemsTransmissionVideo monitoringVirtual firewall
The invention relates to the network monitoring technology field, especially relates to a video monitoring system based on a cloud platform. The video monitoring system comprises a service bus, a user management module, a cloud server proxy module, a network management module, distributed type storage service, and an application program. The service bus is used to provide a connection pivot for message interaction among the various modules. The user management module is used to create a cloud server automatically for a newly registered or added user, and a camera is bond with the cloud server. The distributed type storage service is used to provide block storage service. The cloud service proxy module is used to download latest video files, and store the downloaded video files in a clouddisk based on an internal network or a special network. The network management module is used to provide the service port mapping of the video files, and the ports are limited to be only open to the access of the IP address of the application program, and the access of other IP addresses is forbidden, and in addition a virtual firewall is provided. The application program is used for the query ofthe videos. The problems of the network video monitoring such as easy illegal attacks on the address, low safety performance, difficulty in expanding storage space are solved, and the video monitoringsystem can be used for the network video monitoring technology field.
Owner:G CLOUD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com