Method of securely accessing sqlite by multiple processes
A secure access, multi-process technology, applied in the field of multi-process secure access to sqlite, can solve problems such as high system overhead, long time consumption, and no database access type distinction, to avoid receiving confusion, high-performance access efficiency, and ensure orderliness. Effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
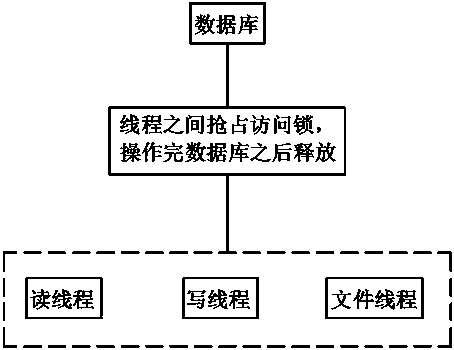
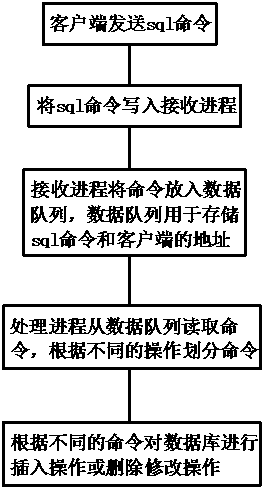
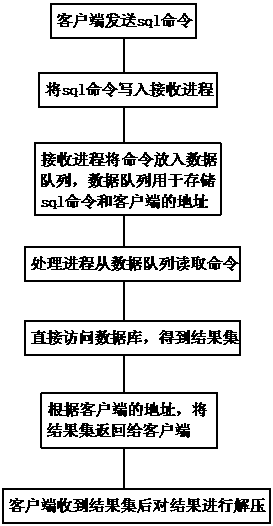
[0048] refer to Figure 1-4 , a specific embodiment of the present invention comprises the following steps:
[0049] A. The access to the database is divided into read thread, write thread and file thread;
[0050] Before accessing the database, the process described in B, step A queries the state of the database lock. If the database is locked, the thread preparing to access the database is in a waiting state. After the lock is released, the thread preparing to access the database acquires the control of the lock right to operate the database;
[0051] C. The above-mentioned threads adopt the first-come-first-served principle to acquire the lock. After the thread completes the operation on the database, the lock is released, and other threads acquire the lock state at this time and then operate on the database.
[0052] Add a random code before each database operation statement, and the server returns the result with this random code. If the random code corresponds, the ret...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com