VPN login authentication method and apparatus
A login authentication and login account technology, applied in the field of communication, can solve problems such as different hardware identifications, failure to access VPN normally, etc., and achieve the effect of security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
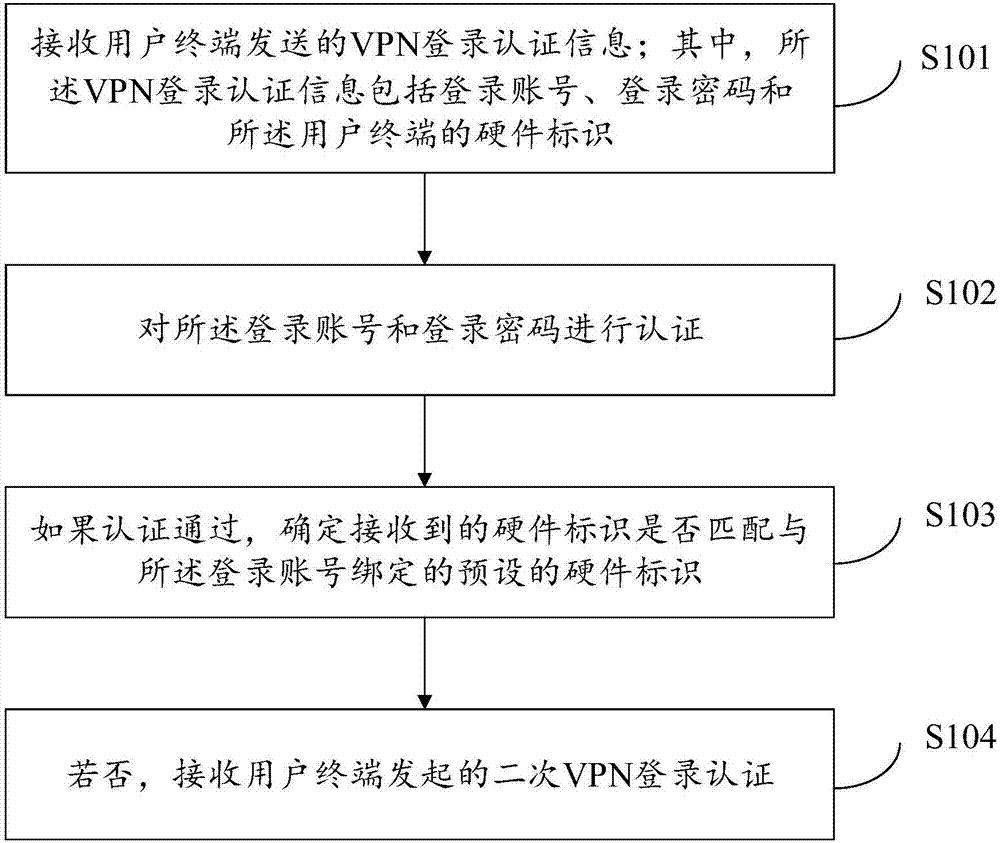
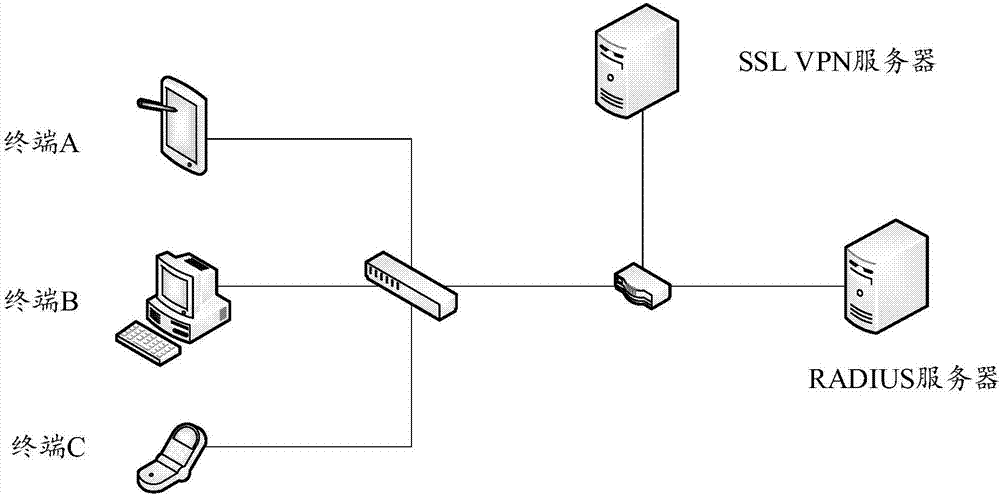
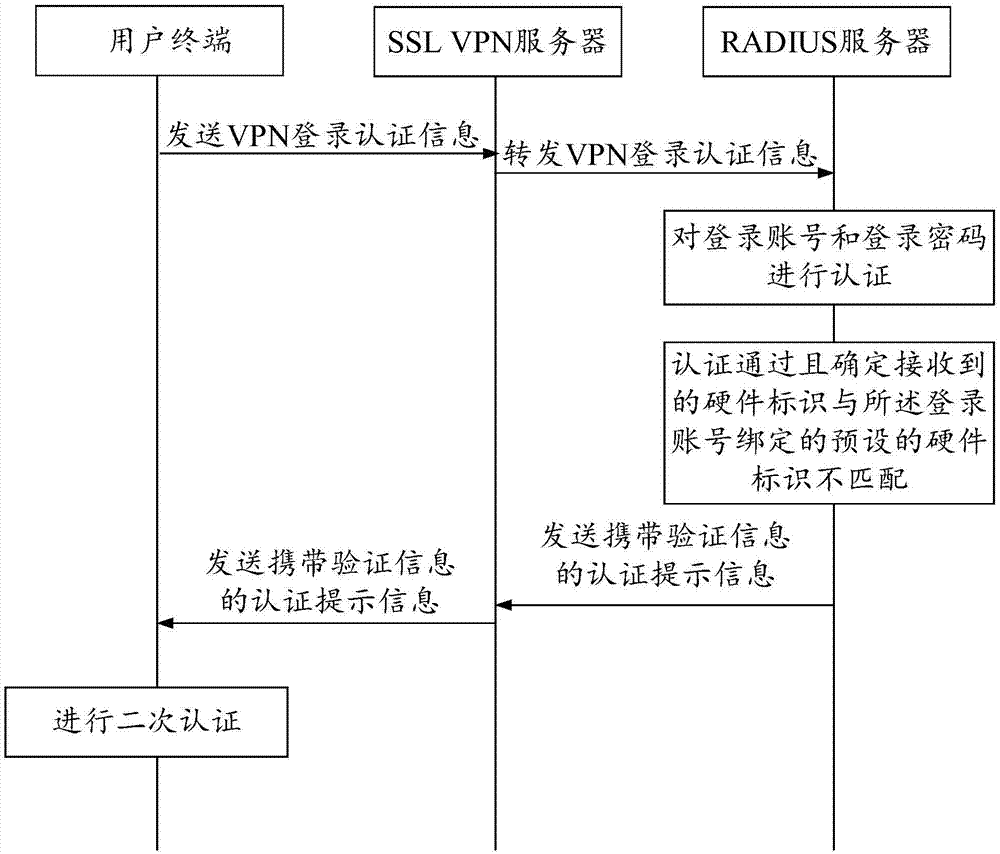
[0044] In the prior art, in order to ensure the data security of VPN users, multiple login authentication methods are commonly used for authentication. The mainstream VPN login authentication method usually uses the login account, login password and the hardware identification of the user terminal for authentication.
[0045] Before VPN login, the user can first complete the registration on the VPN client carried on the user terminal. During the registration process, the user can fill in the login account and login password, and at the same time, the VPN client can obtain the hardware identification of the user terminal. At this time, the login account filled in by the user can be bound with the hardware identification obtained by the VPN client.
[0046] During the VPN login process, the user can enter a login account and a login password, and the VPN client can obtain the hardware identification of the user terminal at this time.
[0047] When the authentication server dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com