File encryption method based on two-dimension code scanning
A file encryption and two-dimensional code technology, which is applied in the field of file encryption, can solve problems such as easy theft and easy forgetting of passwords, and achieve the effects of improving security, improving reliability, and avoiding password leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
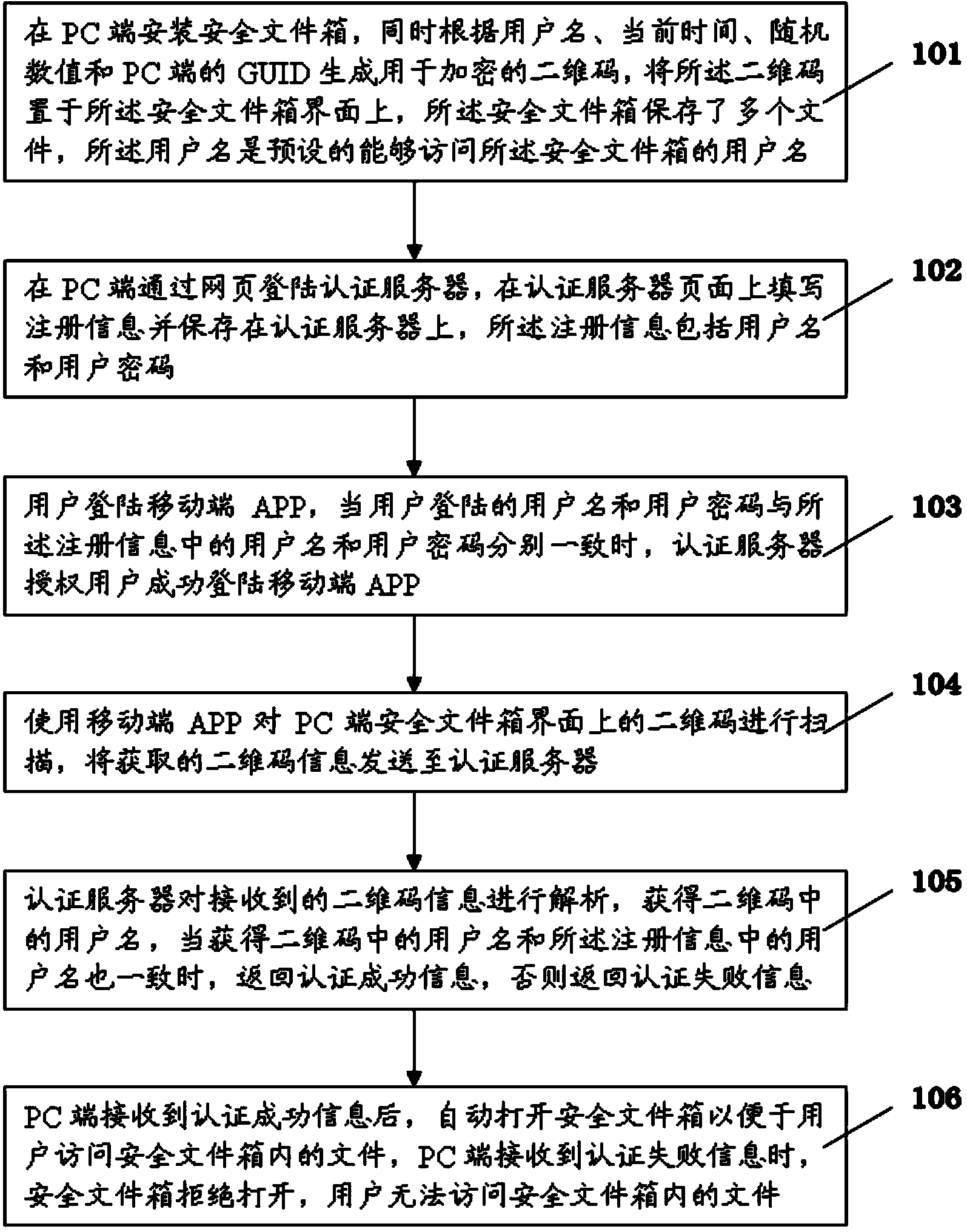
[0015] First of all, please refer to FIG. 1. FIG. 1 is a method flow chart of a file encryption method based on two-dimensional code scanning in the present invention, and the file encryption method includes the following steps:
[0016] Step 101: install the safe file box on the PC side, and generate a two-dimensional code for encryption according to the user name, current time, random value and GUID on the PC side, place the two-dimensional code on the interface of the safe file box, The safe file box stores a plurality of files, and the user name is a preset user name that can access the safe file box;
[0017] Step 102: log in to the authentication server through the webpage at the PC end, fill in the registration information on the authentication server page and save it on the authentication server, the registration information includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com