A secure smartphone and control method based on a split-core virtual machine
A technology of smart phones and virtual machines, applied in computer security devices, branch equipment, telephone communications, etc., can solve the problems of sensitive data theft, easy to steal users, etc., and achieve the effect of eliminating security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
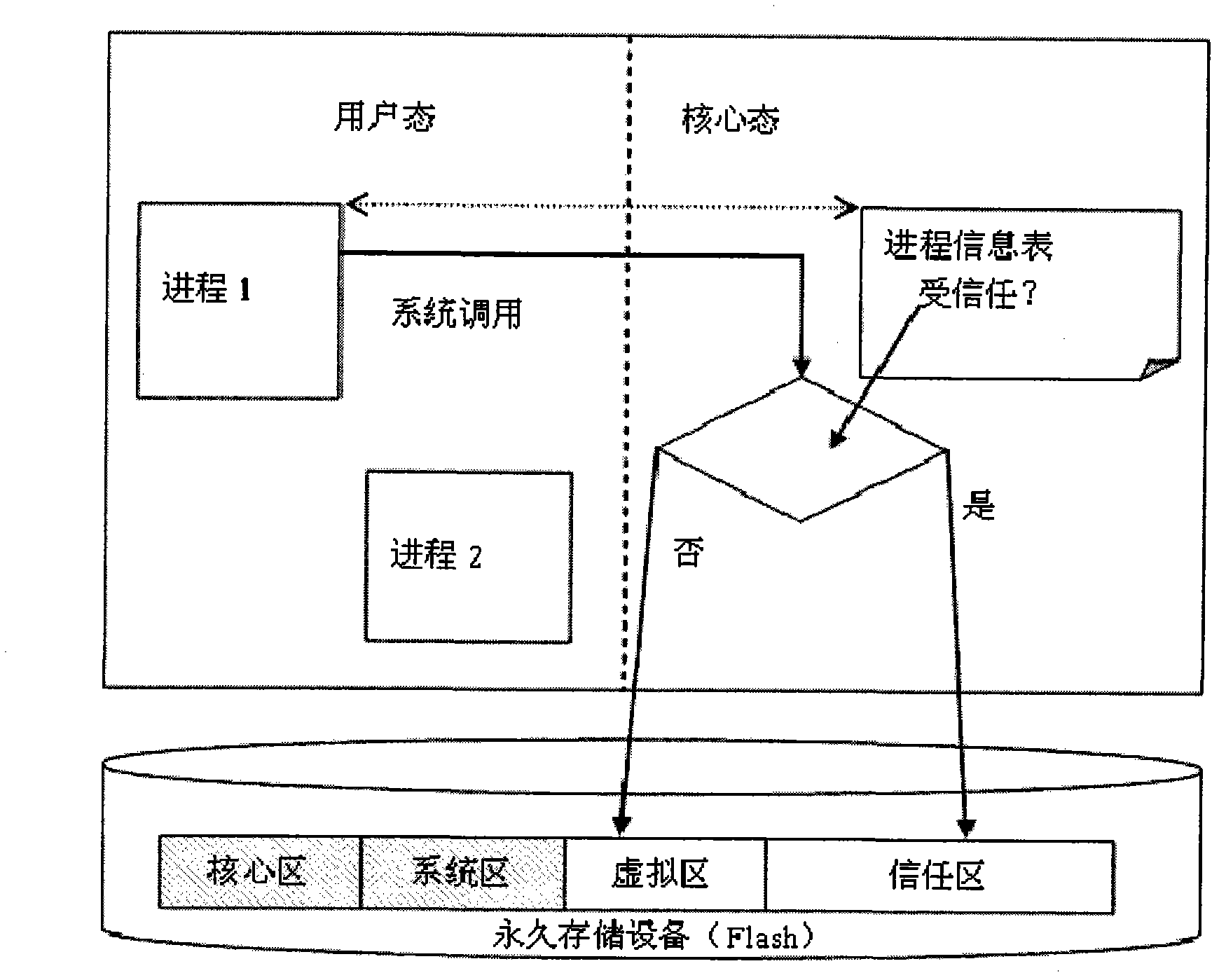
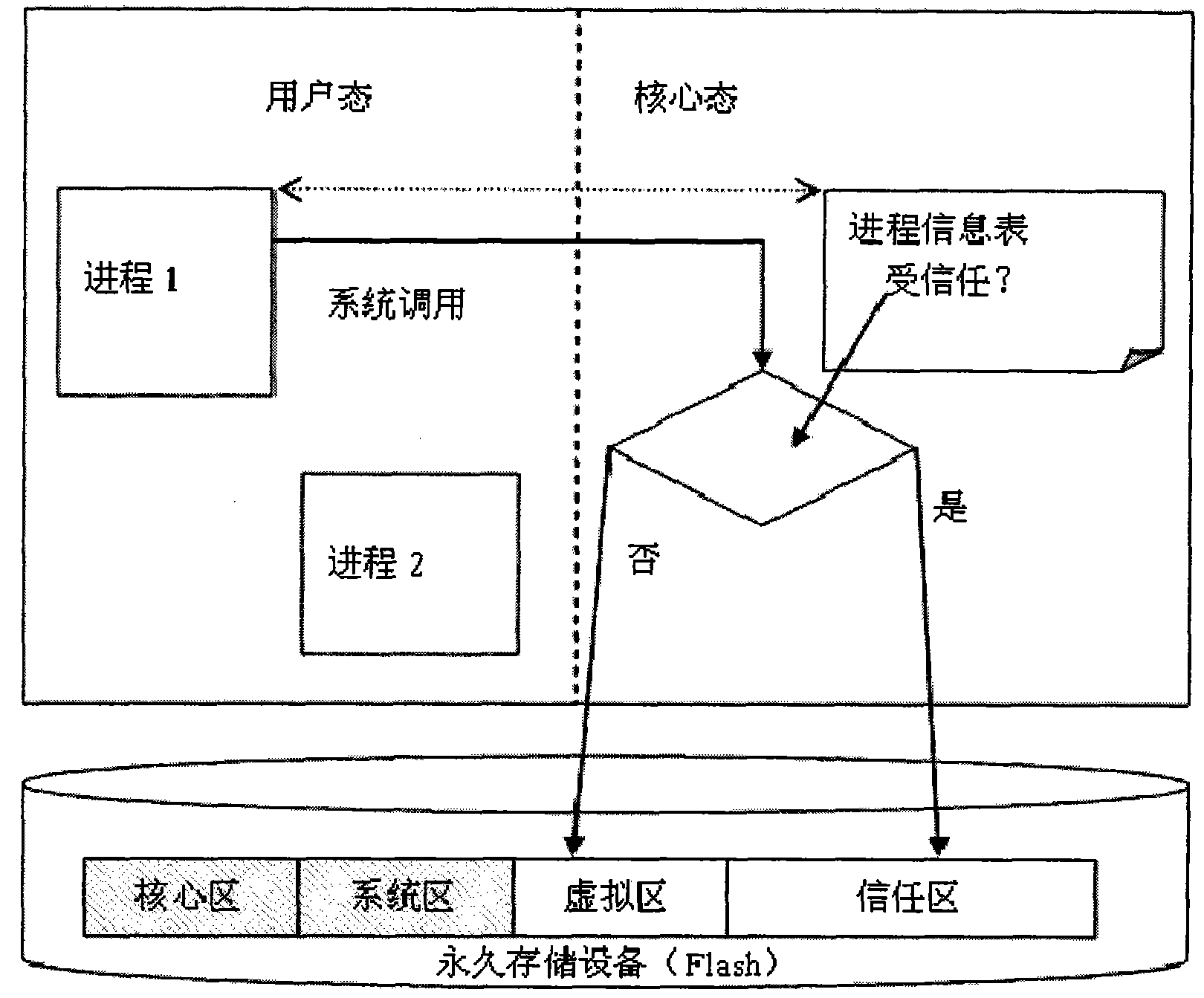
[0035] Aiming at the security smart phone and control method based on split core virtualization of the present invention, a preferred embodiment will be described in detail in conjunction with the drawings, refer to figure 1 ,in:
[0036]The Android (android) operating system of Google adopted by the operating system of the safe smart phone of the present invention. The operating system is a privilege-separated operating system. In this operating system, each application runs under a unique system identity. Each part of the system also uses its own independent identification method. This isolates applications from applications and applications from the system. More security functions of the system are provided through the authority mechanism. Permissions can restrict specific operations of a specific process, and can also restrict access to specific data segments per URI permission. Therefore, the operating system has the property of completely isolating processes. It ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com