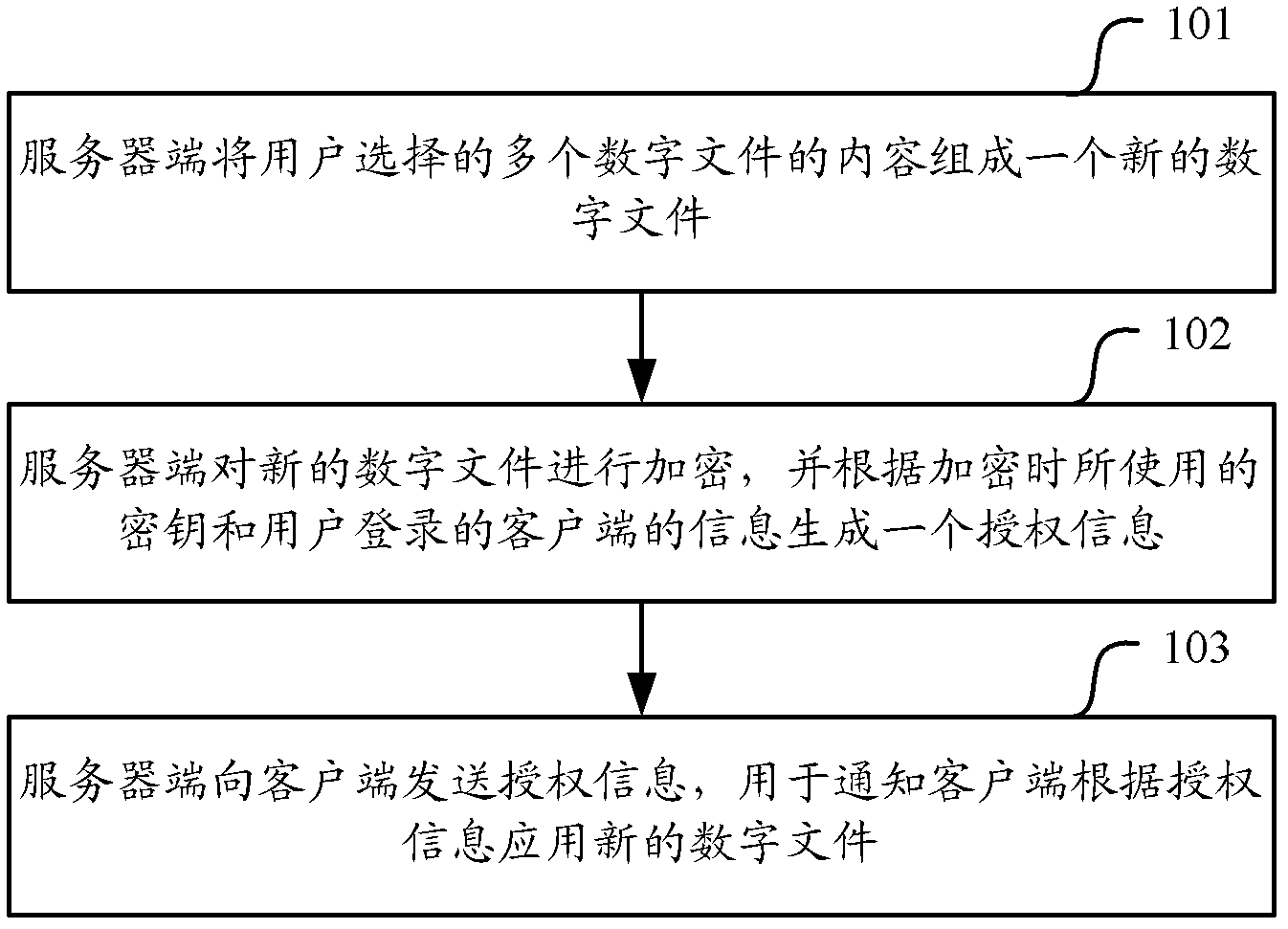
Patents
Literature
33results about How to "Authorization implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and system for providing authorization through mobile terminal
ActiveCN104063790AAuthorization implementationDigital data authenticationProtocols using social networksAuthorizationMobile phone
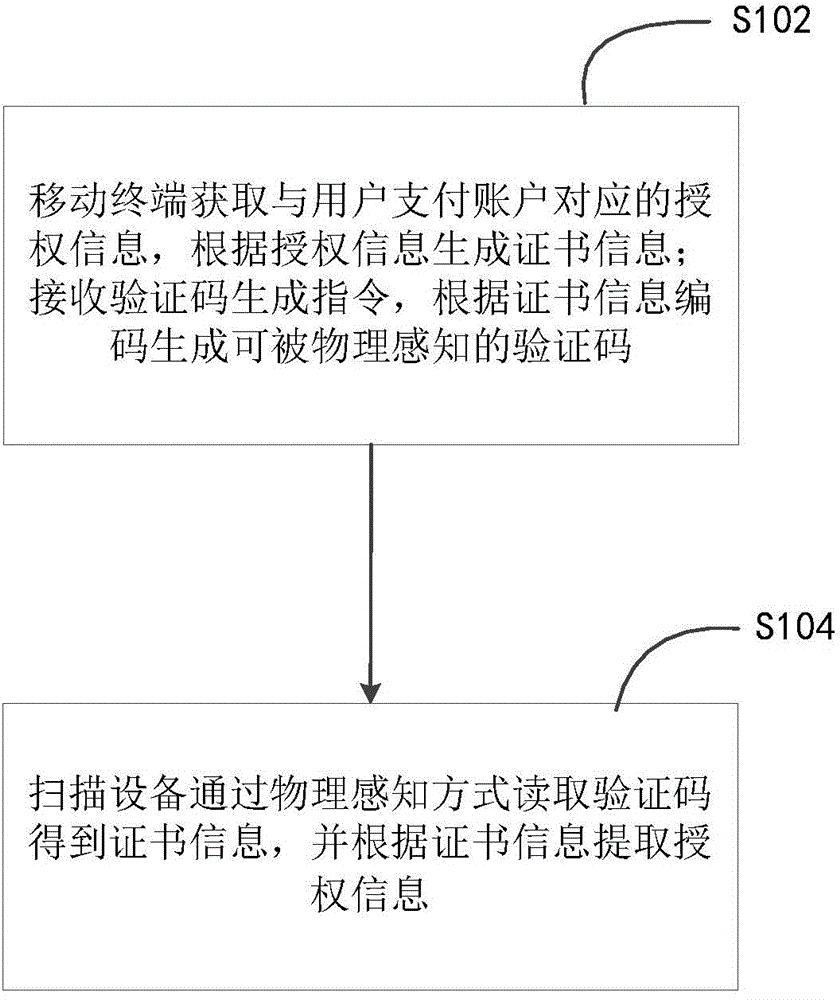
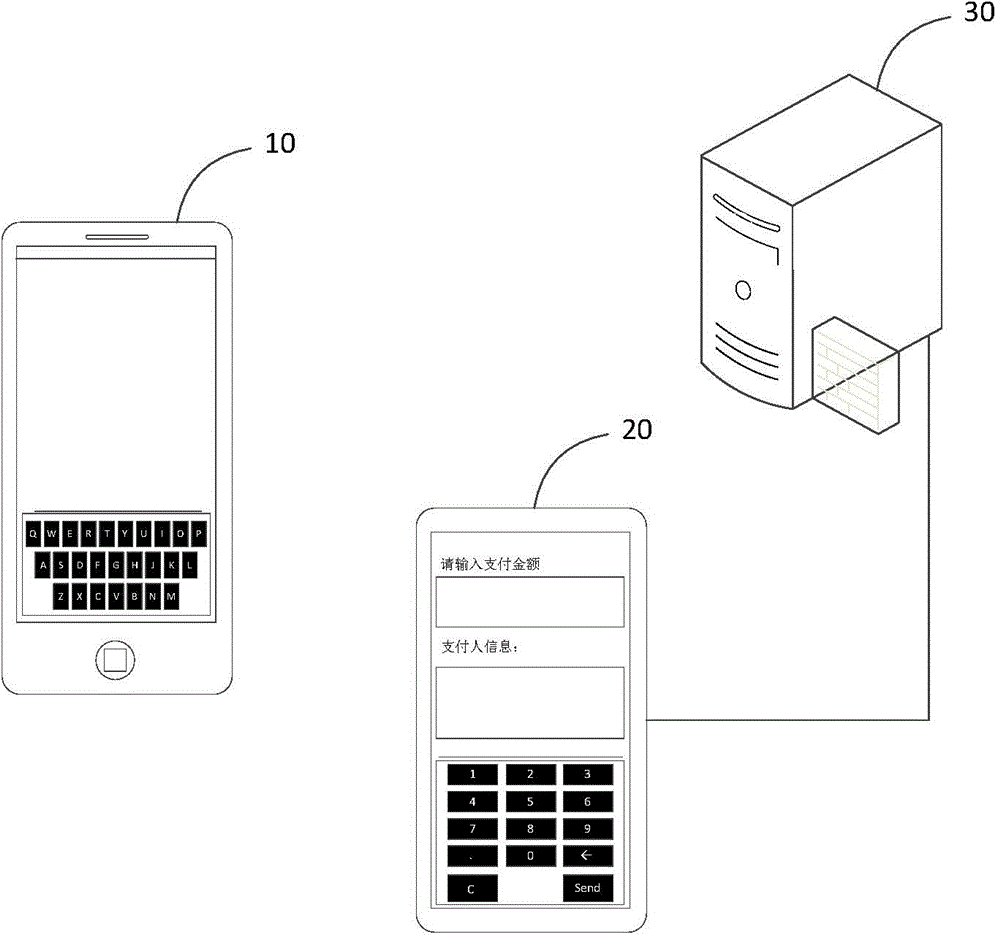
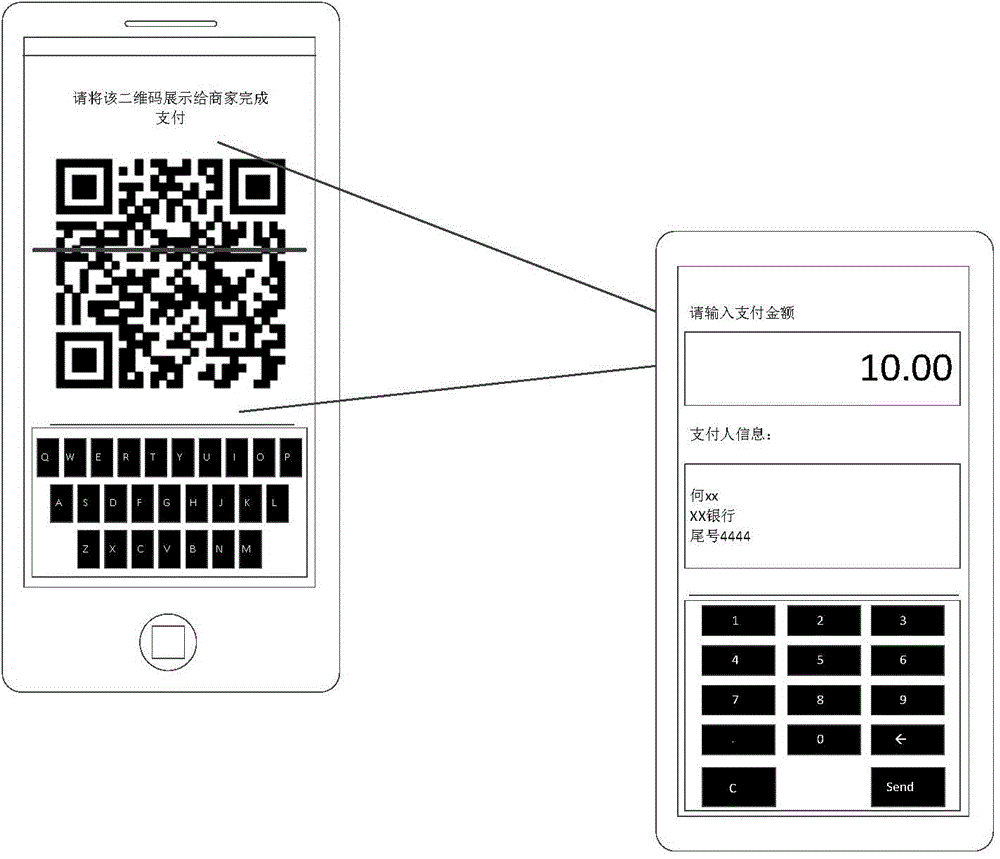
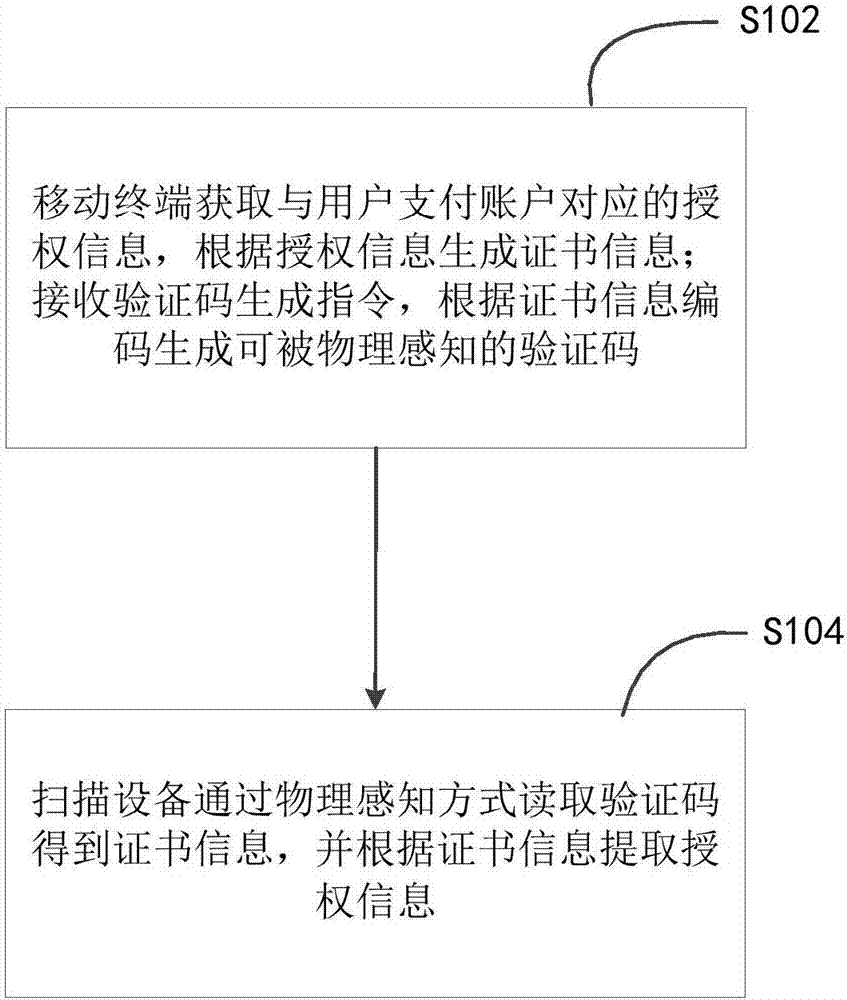
The invention discloses a method and system for providing authorization through a mobile terminal. The method for providing the authorization through the mobile terminal includes that enabling the mobile terminal to acquire authorization information corresponding to a user payment account and generate certificate information according to the authorization information; receiving a verification code generation command and generating a physically sensed verification code according to a certificate information code; enabling a scanning device to read the verification code through a physical sensing way to obtain the certificate information, and extracting the authorization information according to the certificate information. By means of the method and system for providing the authorization through the mobile terminal, a user does not need to depend on a network to provide the authorization through the mobile phone, and accordingly the method and the system can provide the authorization service when the mobile terminal is located in an offline state.
Owner:TENCENT TECH (SHENZHEN) CO LTD
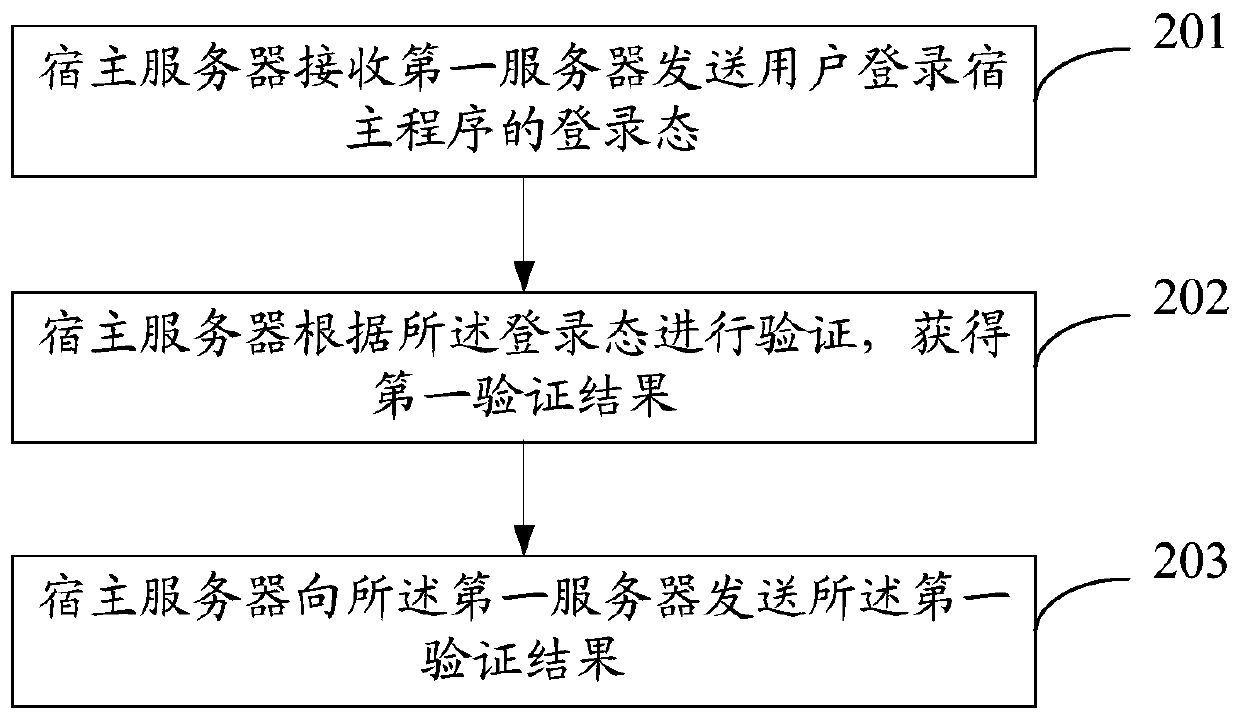
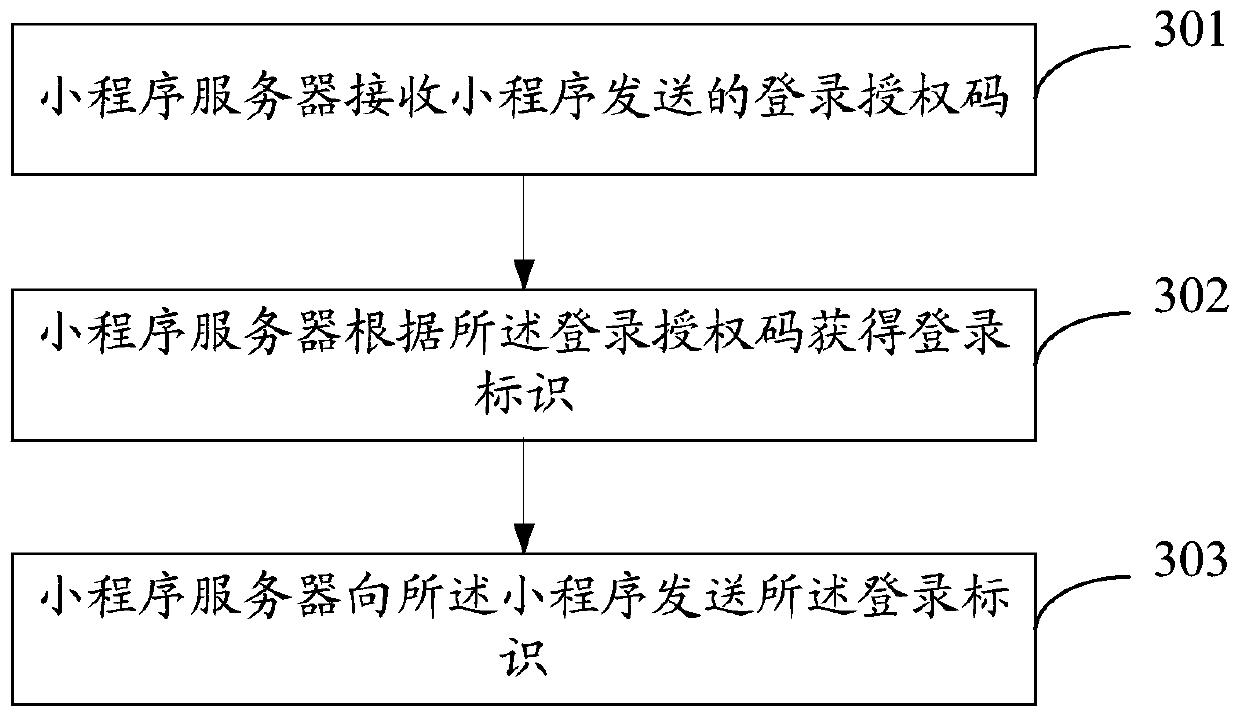
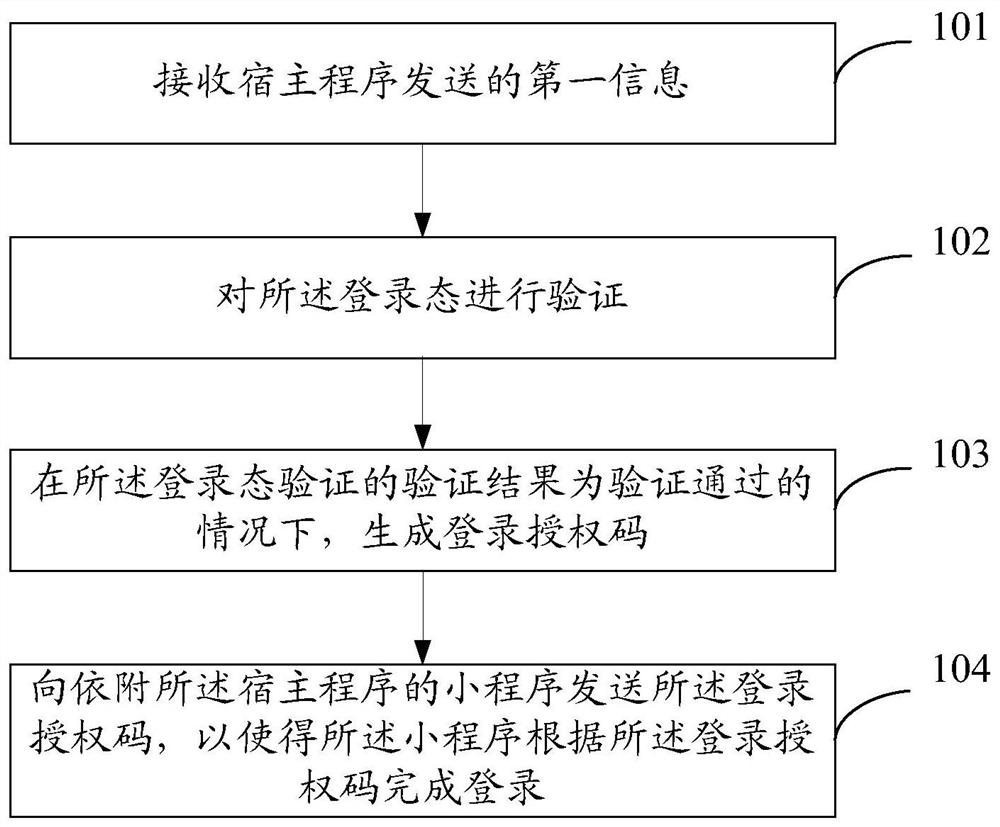
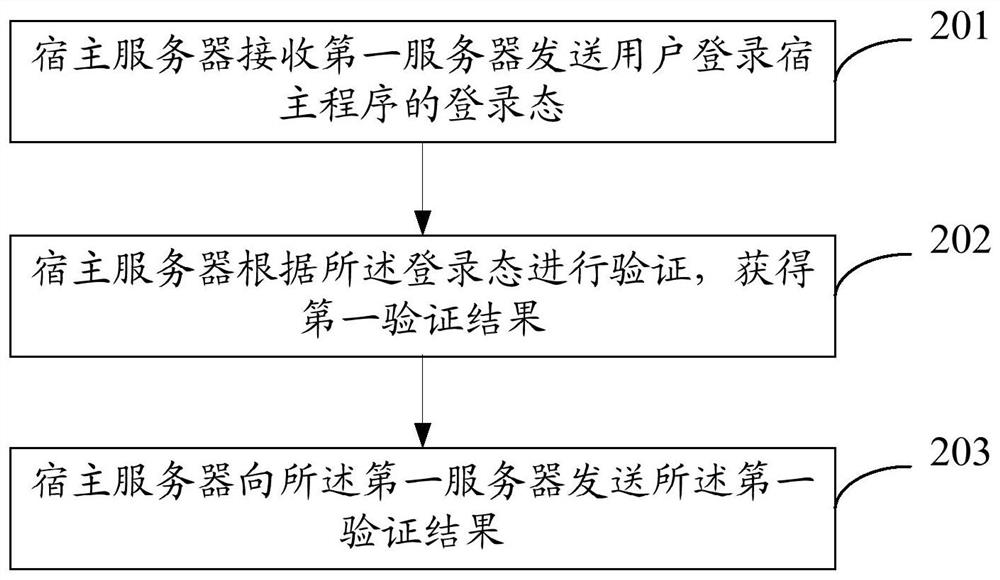
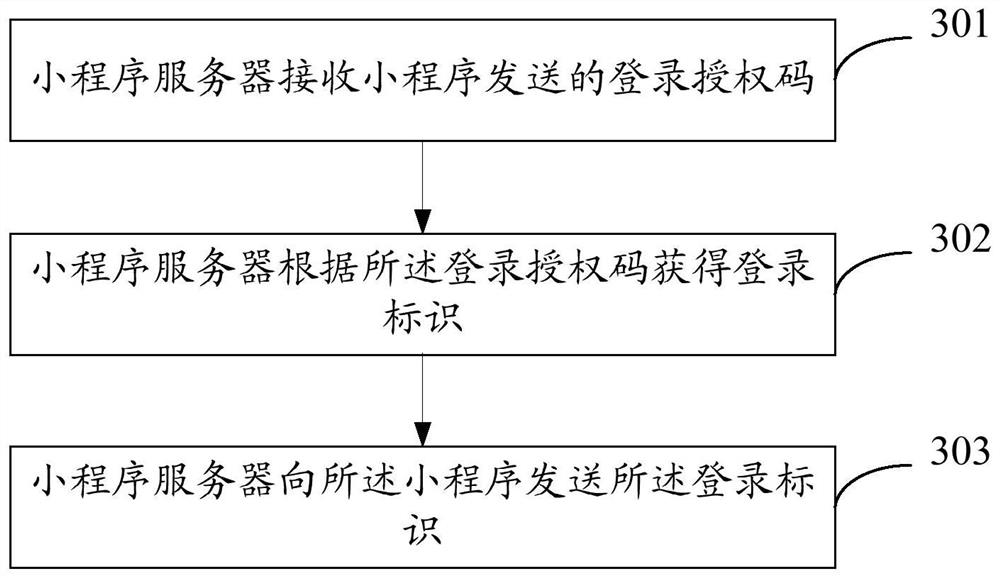
Small program login method, server and electronic equipment
ActiveCN111245825AImprove login efficiencyPromote generationUser identity/authority verificationSoftware engineeringAuthorization
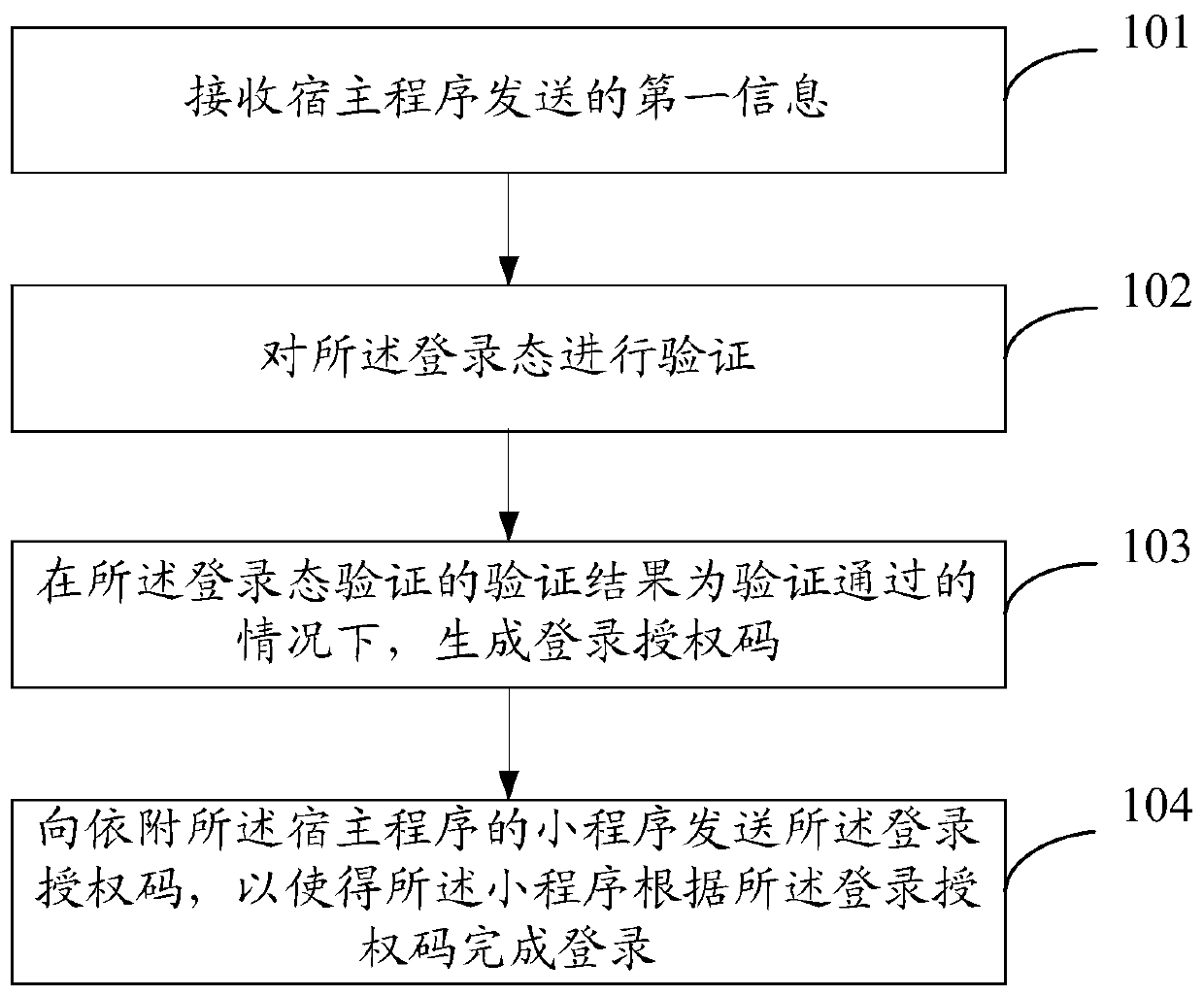
The invention discloses an applet login method, a server and electronic equipment, and relates to the field of applets. The method comprises the steps: enabling a first server to receive first information sent by a host program, wherein the first information comprises a login state of the host program; requesting the host server to verify the login state; generating a login authorization code under the condition that the verification result of the login state verification is that the verification is passed; and sending the login authorization code to the applet attached to the host program, sothe applet completes login. Since the whole login process of the applet does not need to use a specified account for login, login can be completed through the user information of logging in the hostprogram by the user, and the login efficiency of the applet is improved. Since the first server can receive the login state information of the plurality of host clients and perform login state verification through the host servers corresponding to the host clients, the same set of login authorization service provided by the first server can be docked with different account systems of different host programs, and the development cost is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
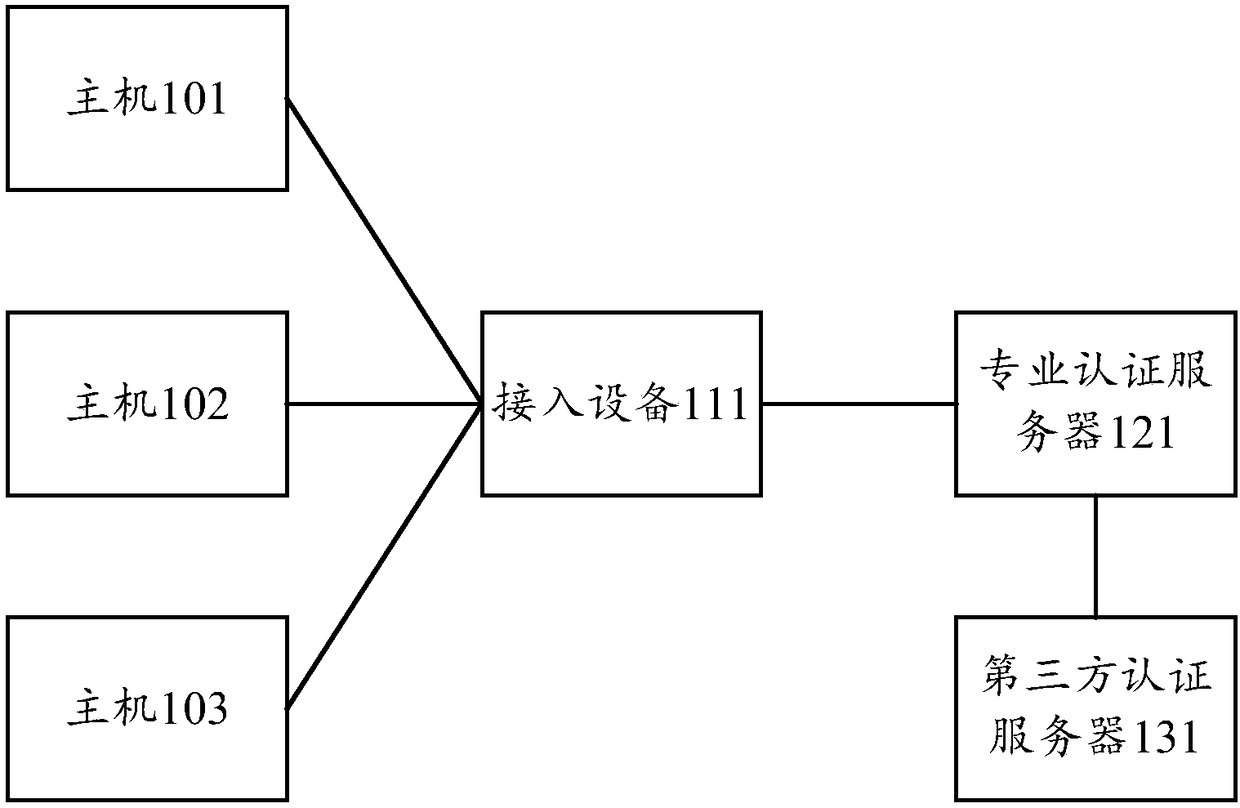
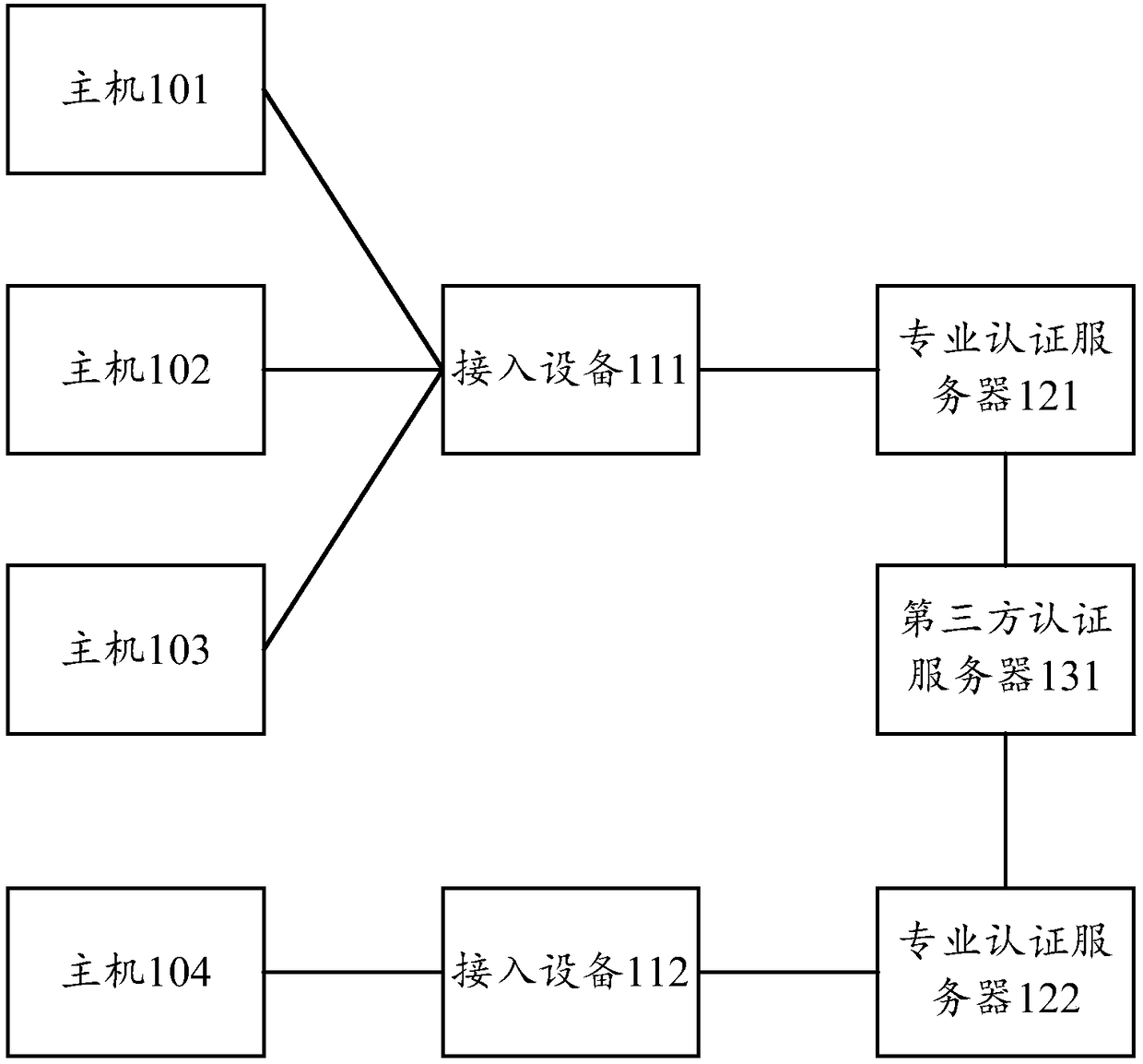
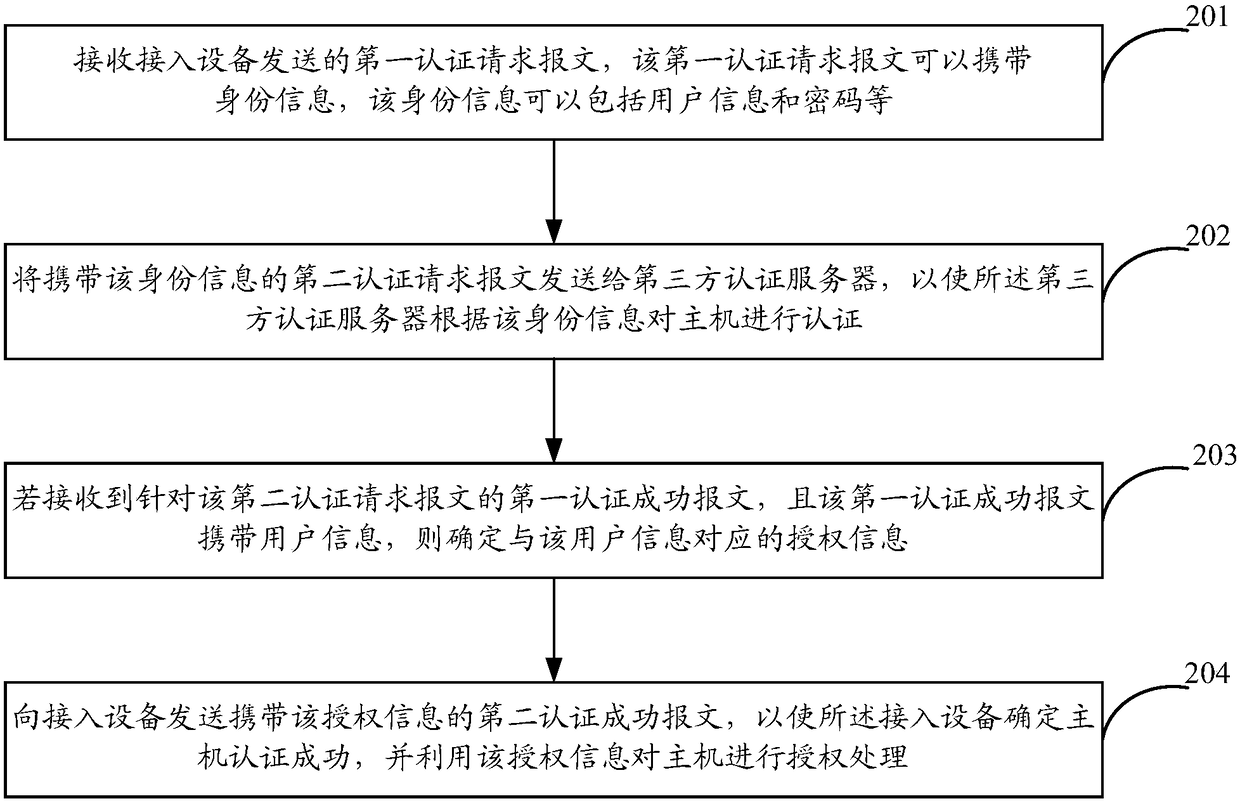
Authentication and authorization method and apparatus, authentication server, and machine-readable storage medium
The invention provides an authentication and authorization method and apparatus, an authentication server, and a machine-readable storage medium. The method comprises the following steps: receiving afirst authentication request message carrying identity information sent by an access device, and transmitting a second authentication message carrying the identity information to a third party authentication server, so that the third party authentication server authenticates a host according to the identity information; if a first authentication success message is received, and the first authentication success message carries user information, determining authorization information corresponding to the user information; and sending a second authentication success message carrying the authorization information to the access device, so that the access device determines that the authentication of the host is successful, and performs authorization processing on the host by using the authorization information. By adoption of the technical scheme of the invention, the docking of the third party authentication server and a professional authentication server is achieved, the third party authentication server performs authentication processing, and the professional authentication server performs authorization processing, thereby implementing authentication, authorization and other operationson the host.
Owner:NEW H3C TECH CO LTD
Method, system and server for digital rights management (DRM)
InactiveCN103139143AAuthorization implementationImprove usabilityTransmissionProgram/content distribution protectionDigital rights managementClient-side
Owner:NEW FOUNDER HLDG DEV LLC +1
Method, device and system for authorizing permission to account
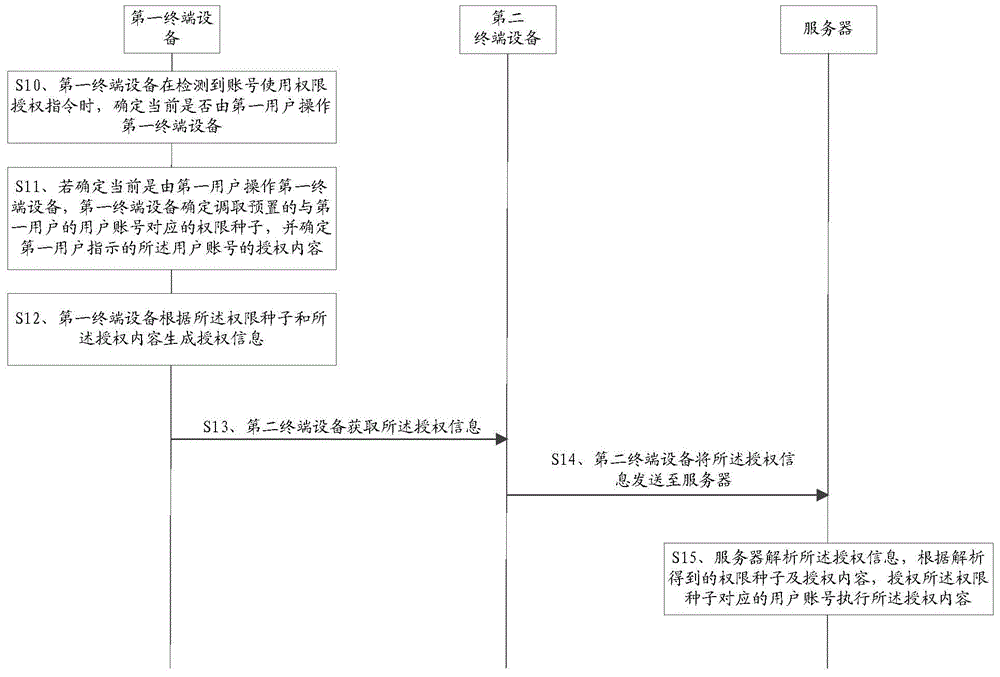
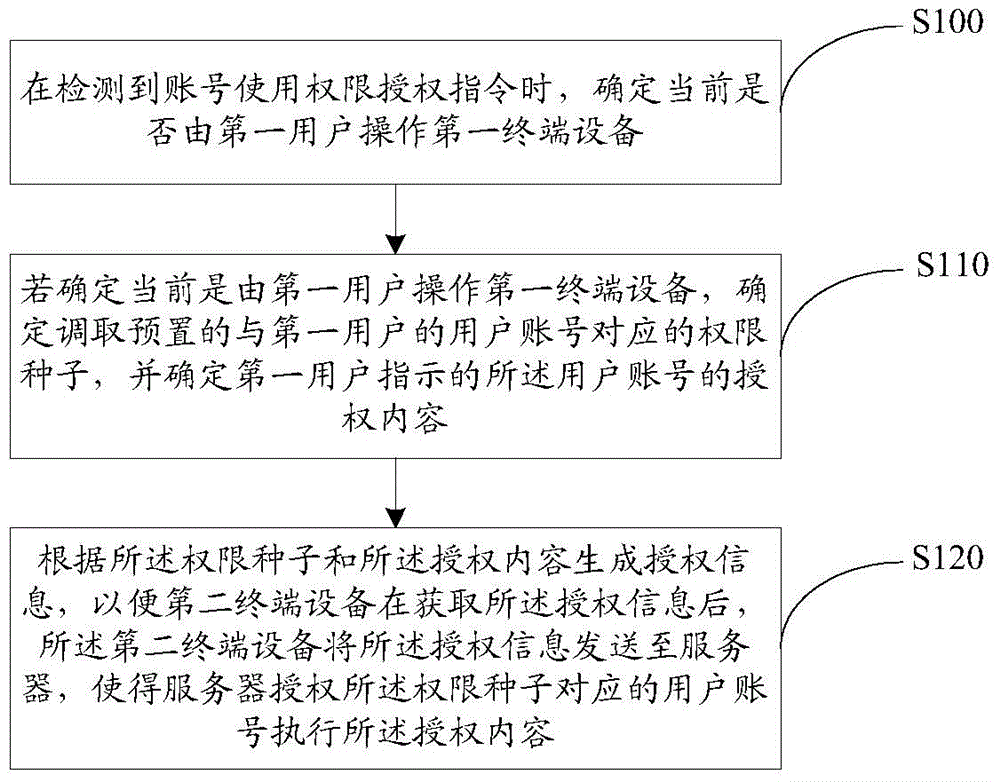
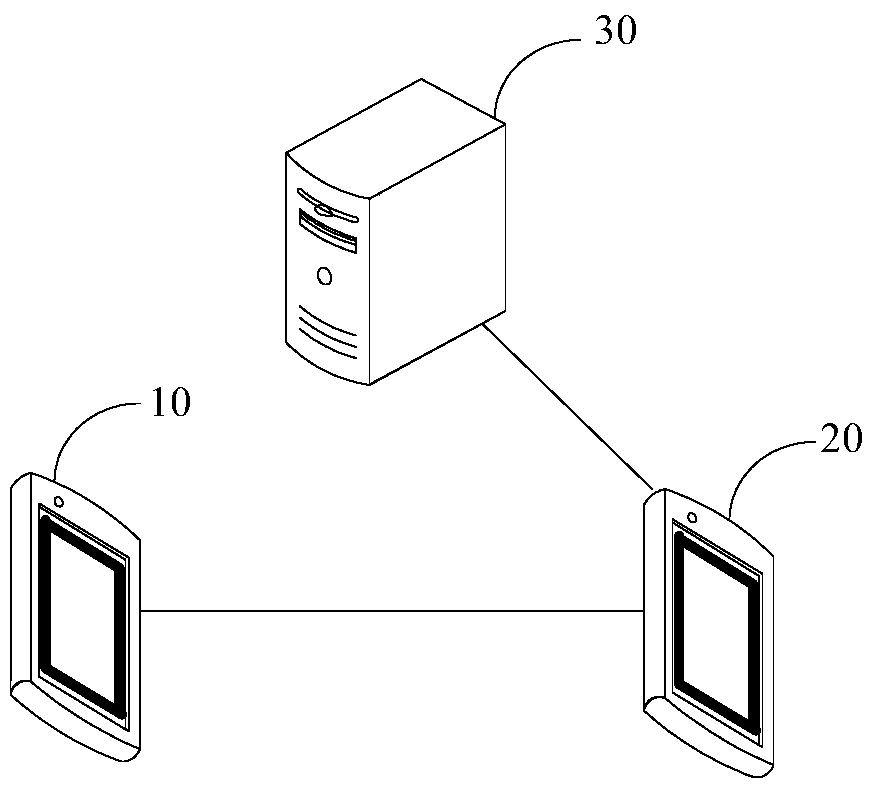
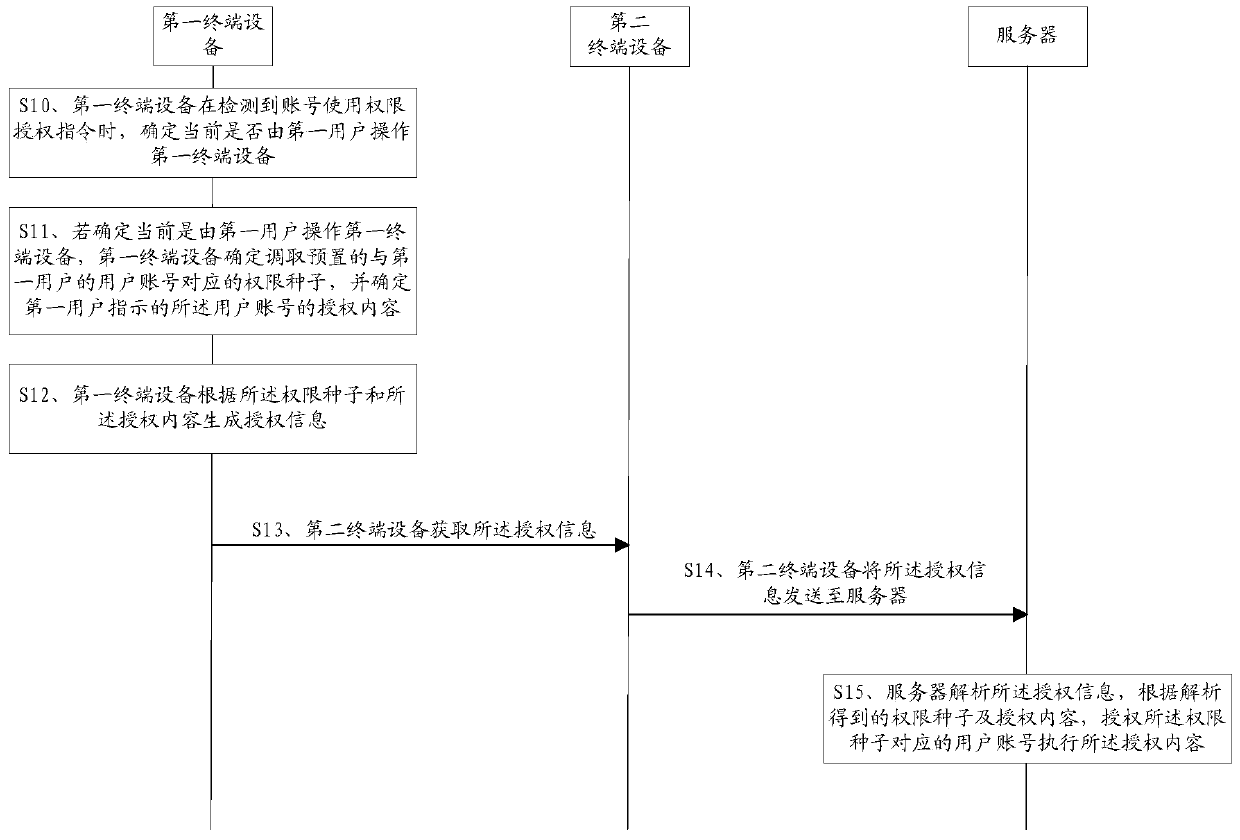
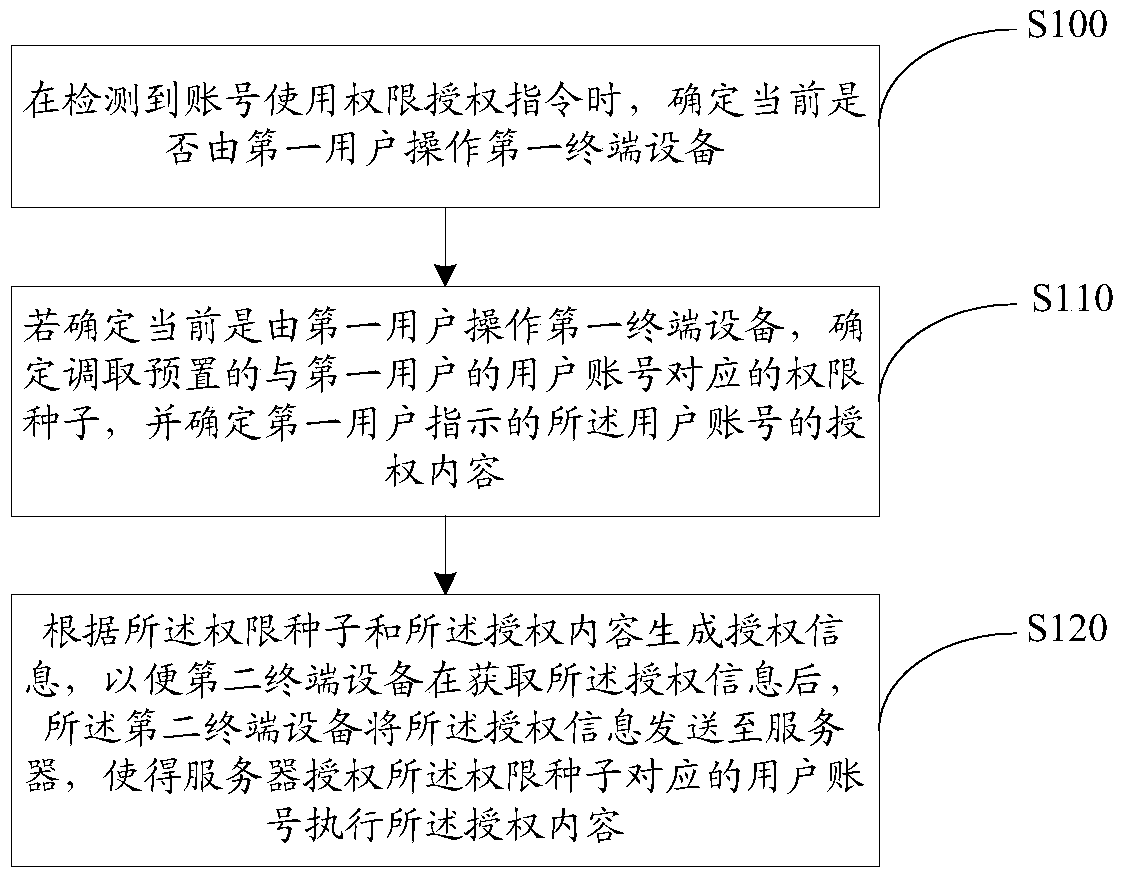
ActiveCN106549926AImprove securityRealize personalizationTransmissionTerminal equipmentComputer terminal
The embodiment of the invention provides a method, a device and a system for authorizing permission to an account. The method comprises the steps of determining whether first terminal equipment is operated by a first user when an account permission authorization command is detected; if the first terminal equipment is operated by the first user is determined, determining to call a preset permission seed corresponding to the user account of the first user, and determining authorization content of the user account indicated by the first user; generating authorization information according to the permission seed and the authorization content, thus allowing second terminal equipment to send the authorization information to a server after acquiring the authorization information, and allowing the server to authorize the user account corresponding to the permission seed to execute the authorization content. According to the method, the device and the system provided by the embodiment of the invention, security of the account is improved during a process of authorizing the permission to the account.
Owner:TENCENT TECH (SHENZHEN) CO LTD
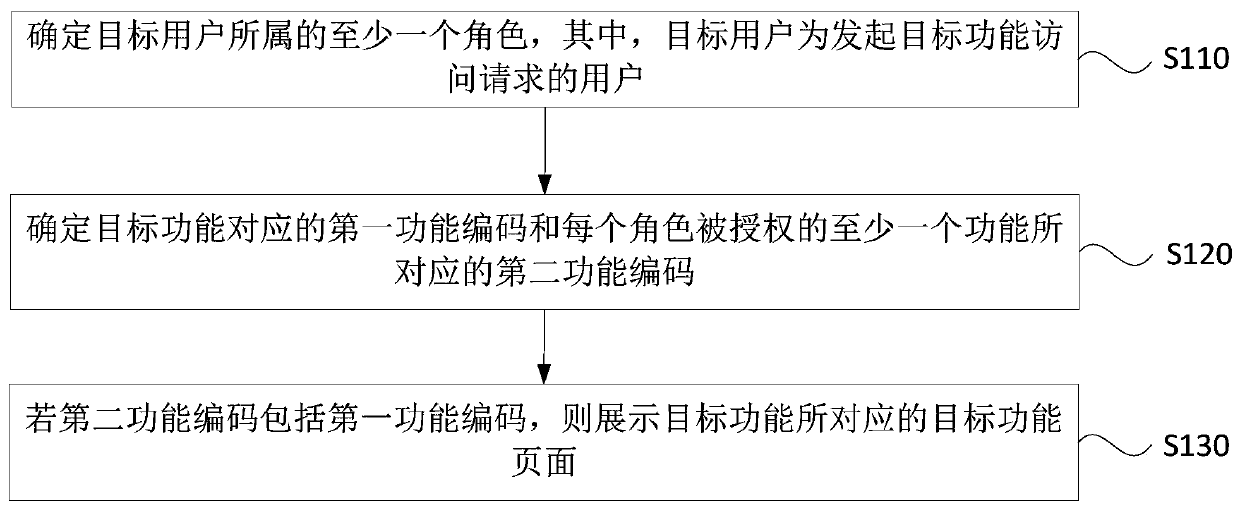
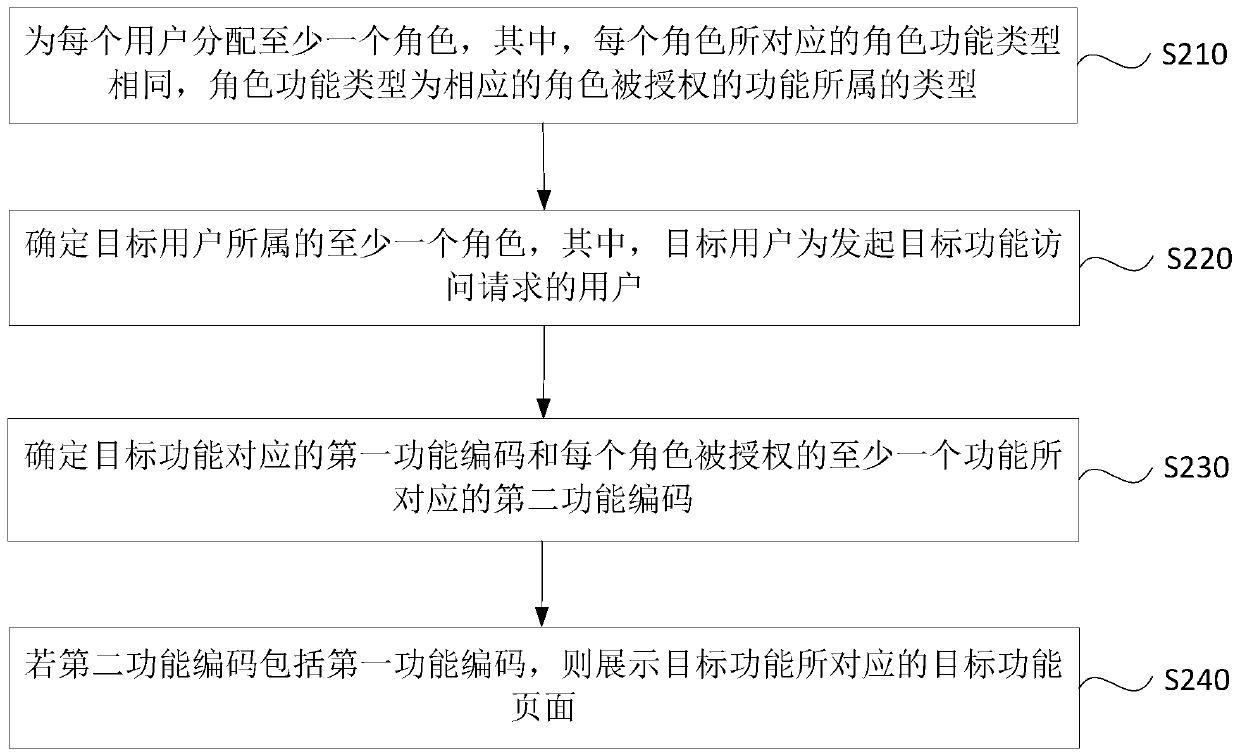
Access control method and device, computer device and storage medium
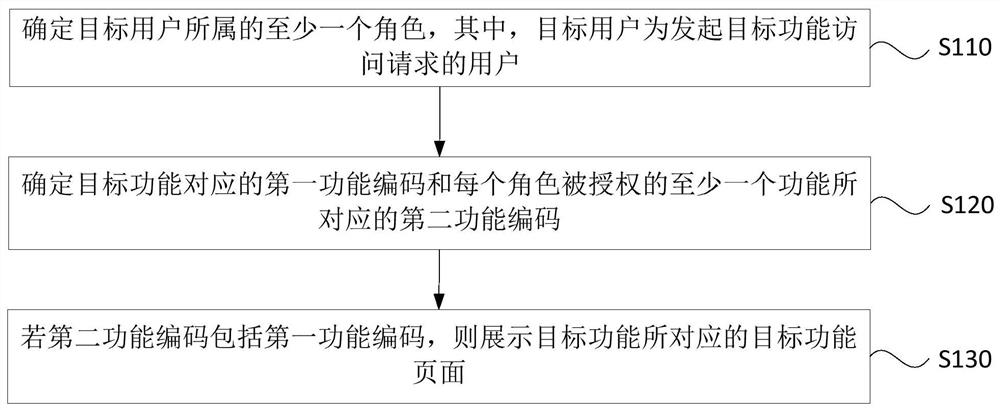
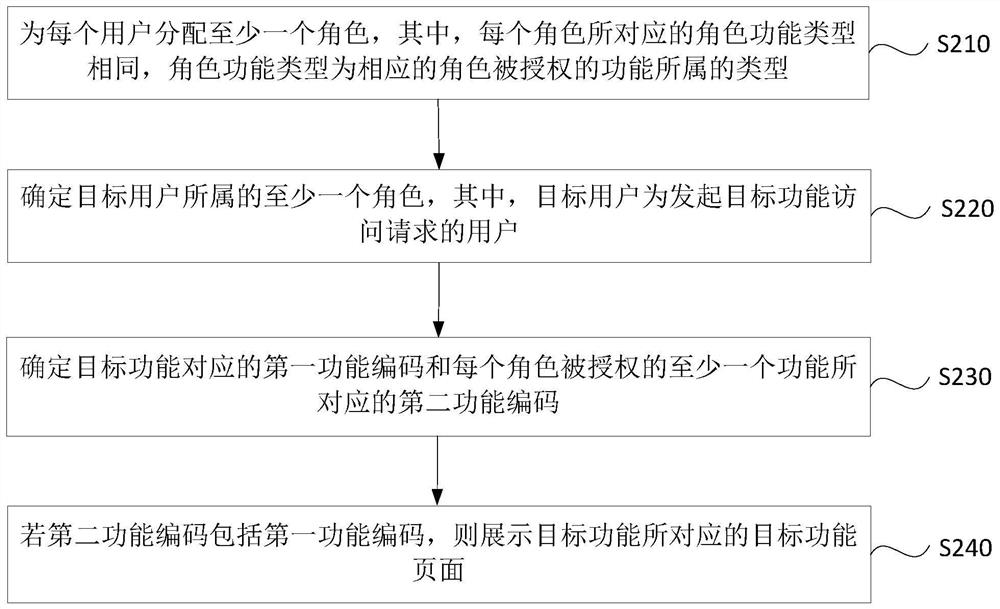
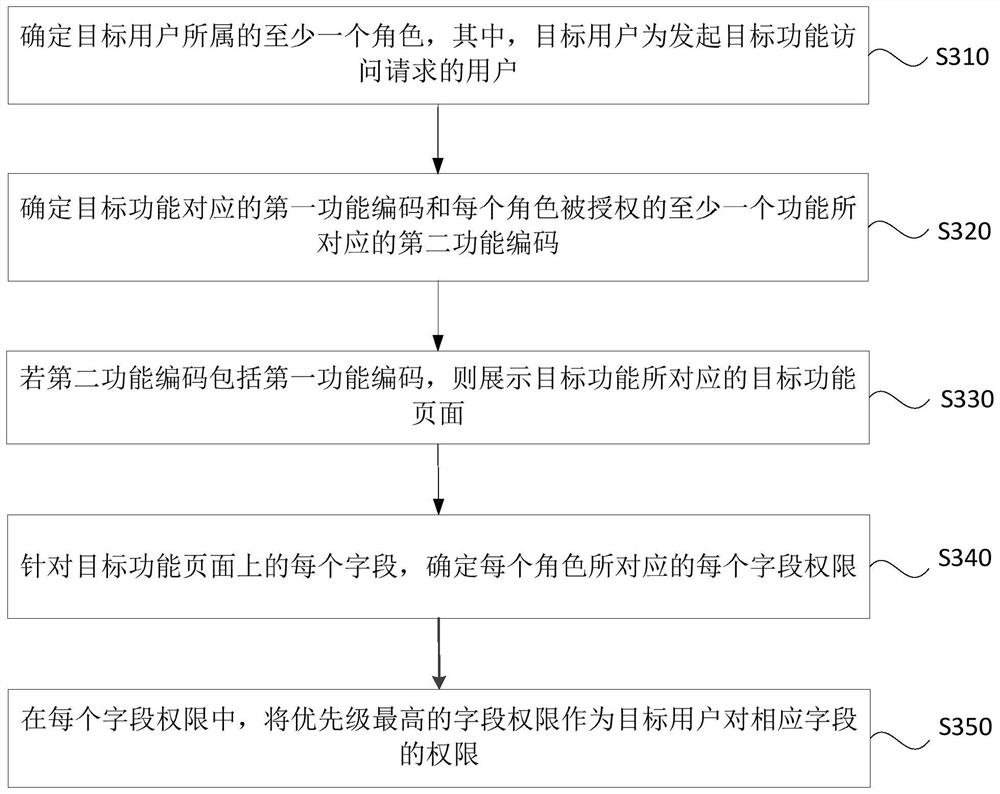
ActiveCN110569667AAuthorization implementationDigital data protectionComplex information systemAuthorization
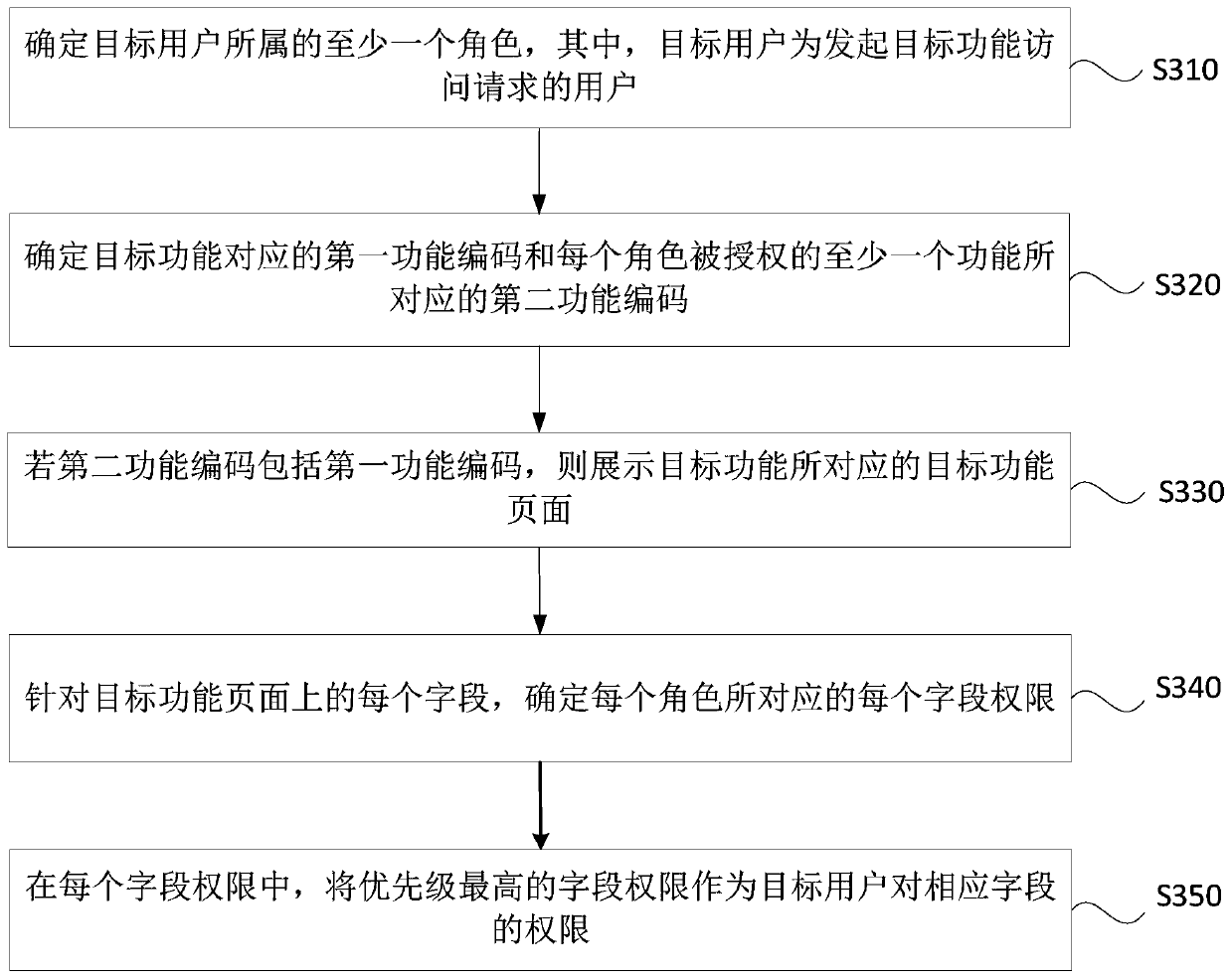
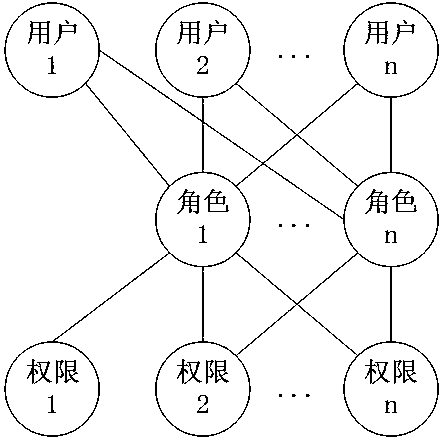
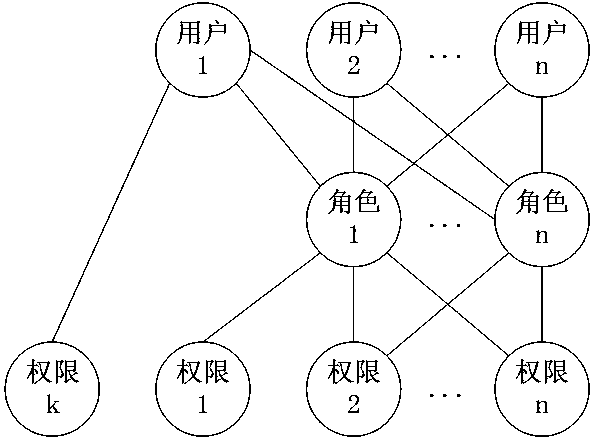
The embodiment of the invention discloses an access control method and device, a computer device and a storage medium. The access control method comprises: determining at least one role to which a target user belongs, and the target user being a user initiating a target function access request; determining a first function code corresponding to the target function and a second function code corresponding to at least one function authorized for each role; and if the second function code comprises the first function code, displaying a target function page corresponding to the target function. According to the technical scheme provided by the embodiment of the invention, the problems that system resources cannot be authorized in detail when an existing role-based permission access control model authorizes the role by utilizing URI, and authorization chaos is easily caused are overcome, and the effect that in the complex information system, authorization of the system resources can be achieved more carefully on the premise that authorization chaos is not caused is achieved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method and device for authorizing wireless equipment and sending control command for authorization of electric appliances
InactiveCN105827589AAuthorization implementationData switching by path configurationAuthorizationEquipment use
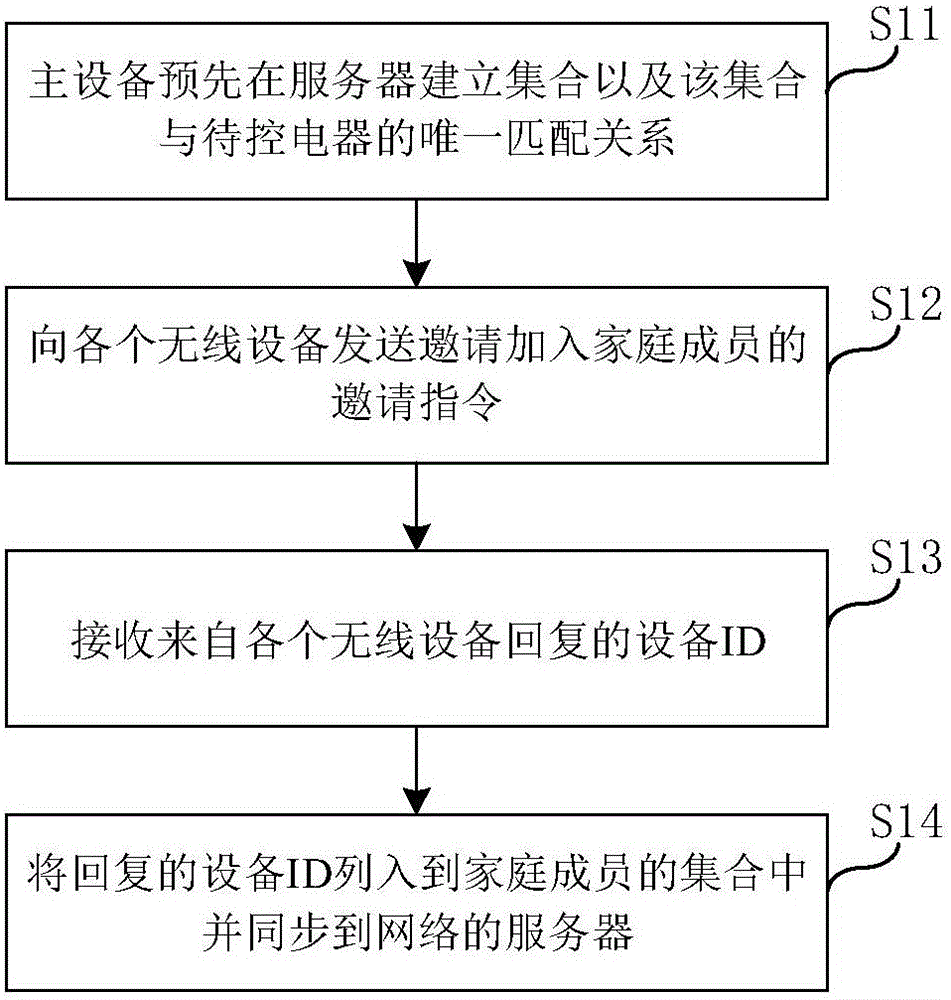
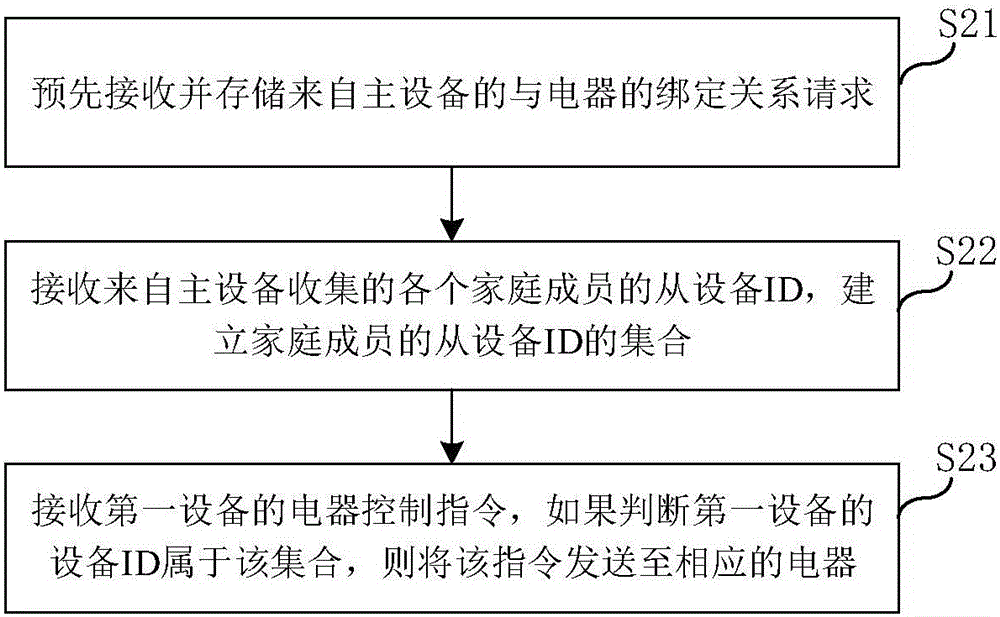
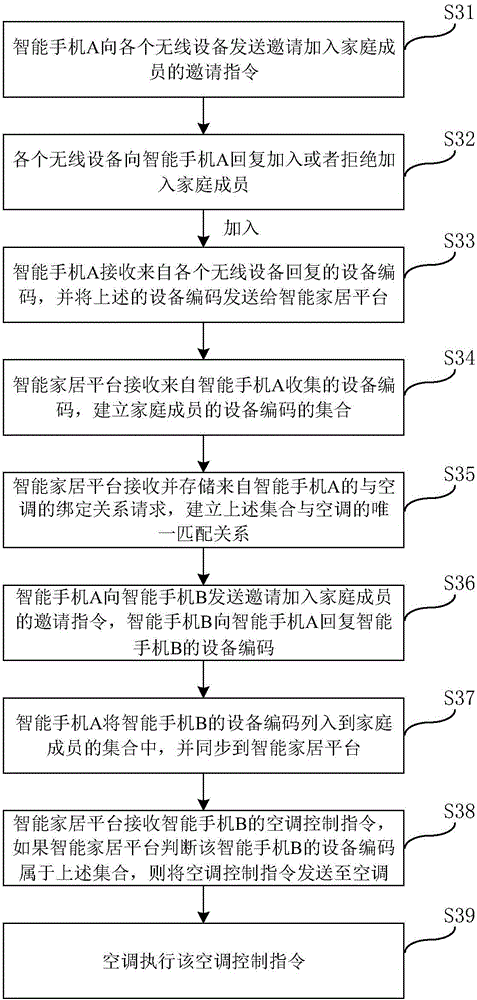
The invention provides a method for authorizing wireless equipment used for controlling electric appliances. The method comprises the steps of sending an invitation instruction to each wireless equipment to invite the wireless equipment to join as a family member; receiving the ID of each equipment that is returned from the wireless equipment; listing the returned ID into the set of family members, and synchronizing the ID in a network server. The invention also discloses a device for authorizing the wireless equipment used for controlling electric appliances, a method and a device for sending a control command for the authorization of electric appliances. Based on the method and the device for authorizing the wireless equipment used for controlling electric appliances, and the method and the device for sending the control command for the authorization of electric appliances, master equipment and slave equipment are free from being registered through the APP, and only the ID of the slave equipment needs to be listed in the set of family members established by the master equipment. Therefore, the slave equipment in the set can be authorized.
Owner:QINGDAO HAIER AIR CONDITIONER GENERAL CORP LTD
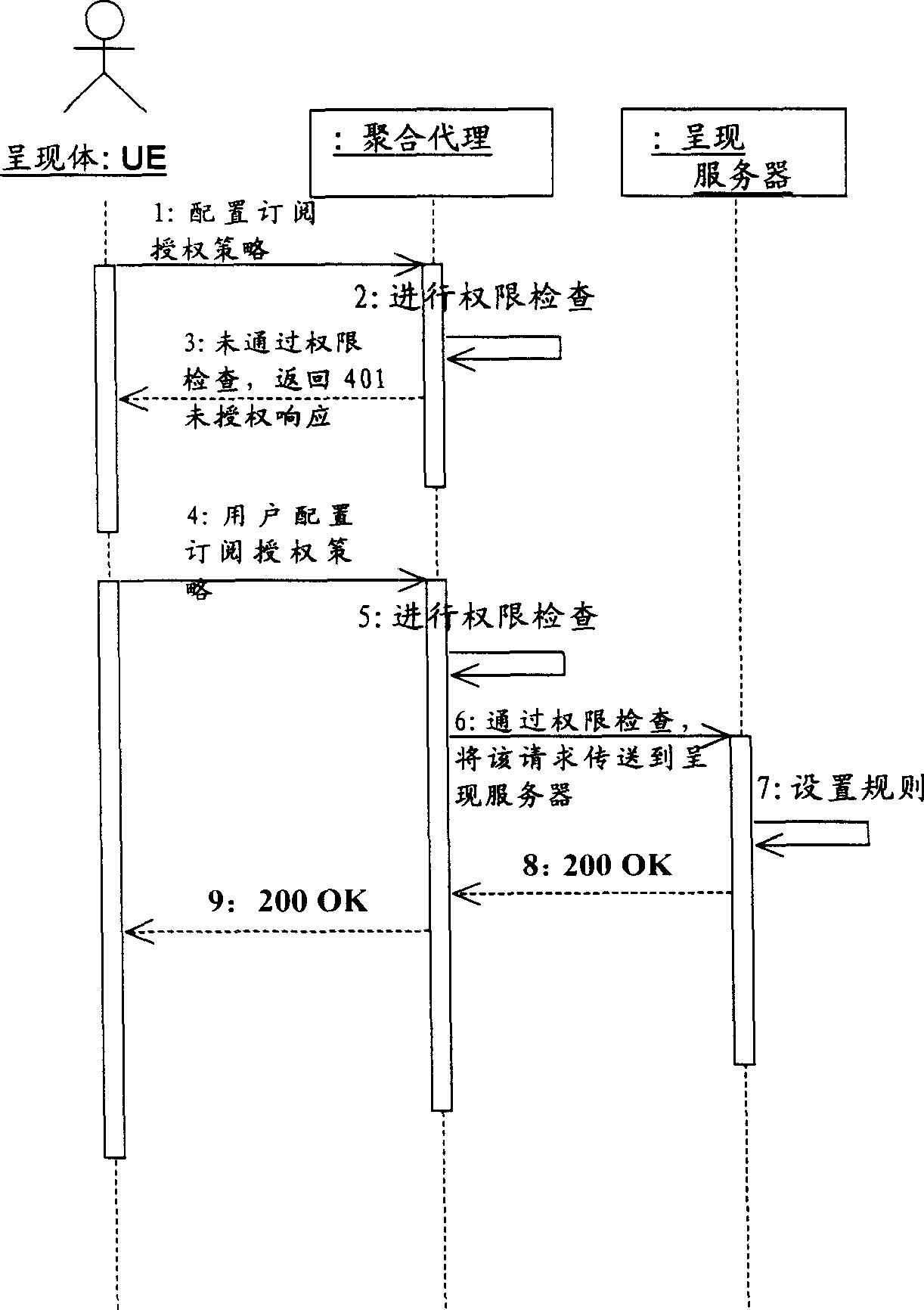
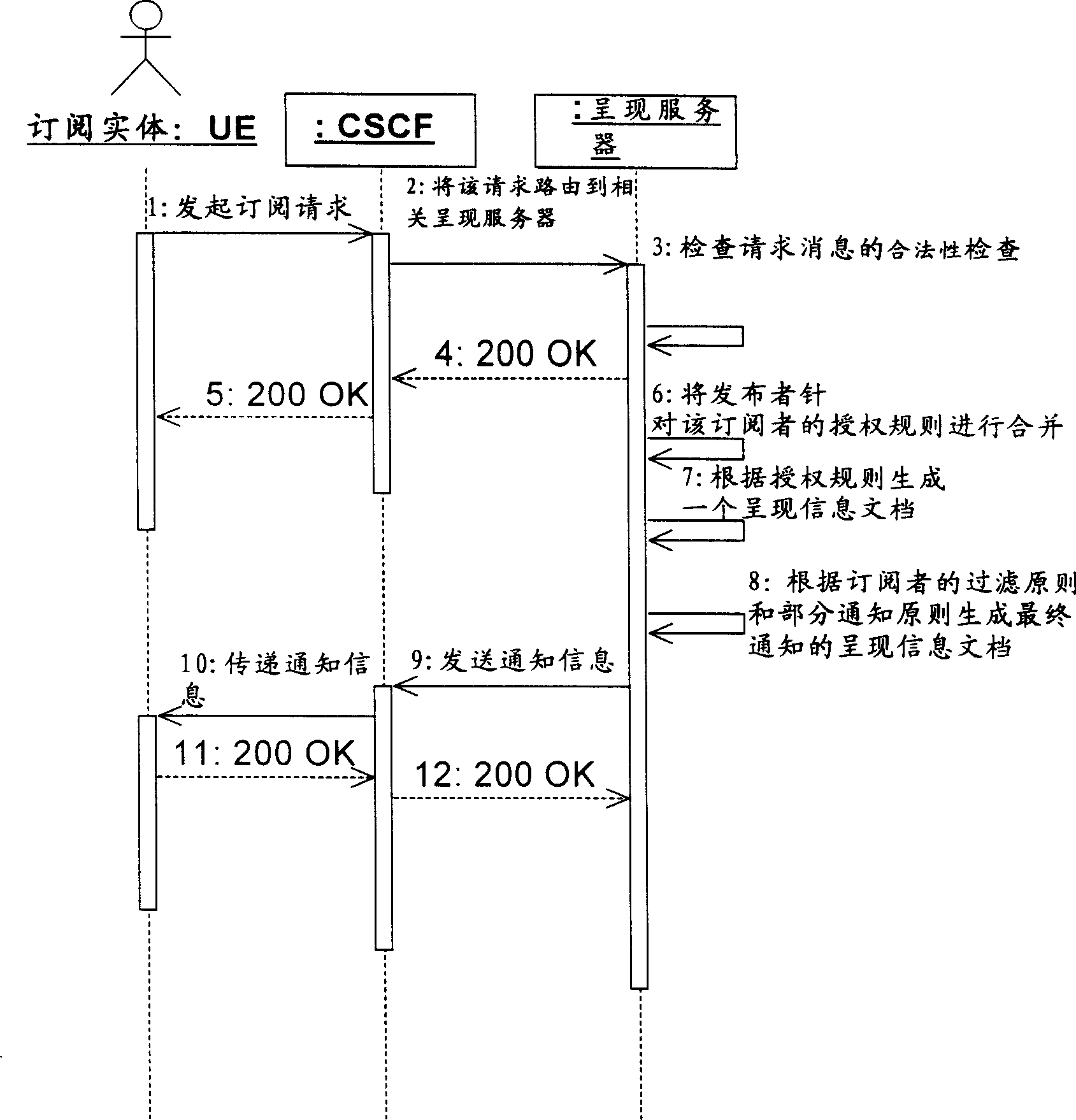
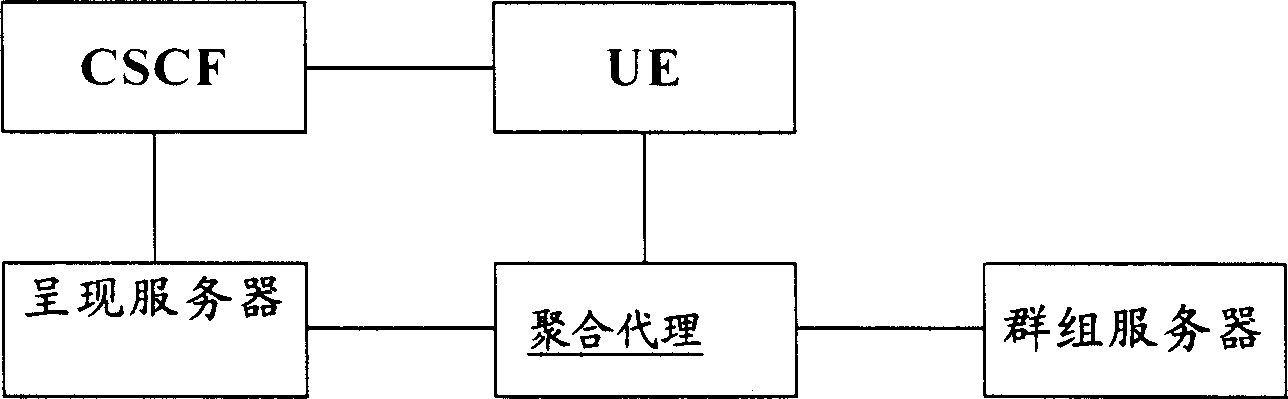
Authorized rule for extending public group in presenting authorized strategy
InactiveCN1859141AAuthorization implementationSpecial service provision for substationRunning timeDocumentation
The present invention provides a subscribing presentment information method, server and system. Said method includes receiving subscribing presentment information request from registered reader; obtaining allowed subscribing public groups from said presentment information promulgator authorized rule; obtaining said public groups member list; if registered reader is public groups member then according to authorized rule generating presentment information document, transmitting presentment information document to registered reader. Adopting present invention user can once configure authorized rule to all member in whole public groups instead of one by one configuring, saving operation steps and running time.
Owner:HUAWEI TECH CO LTD
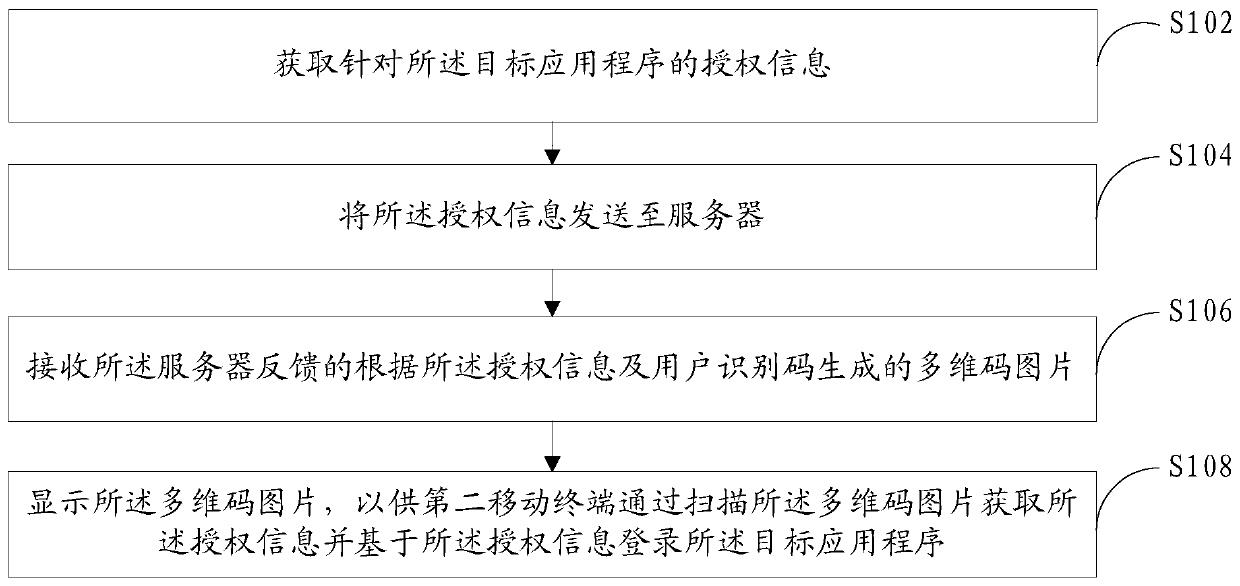
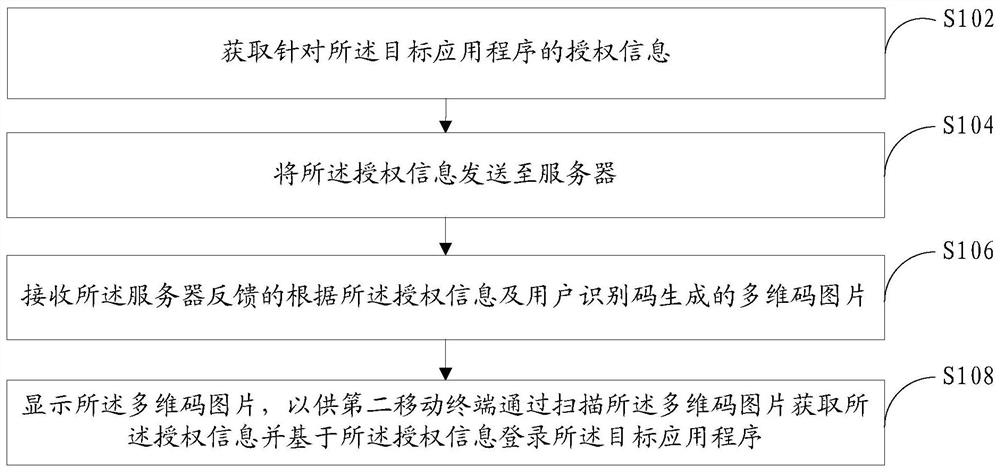
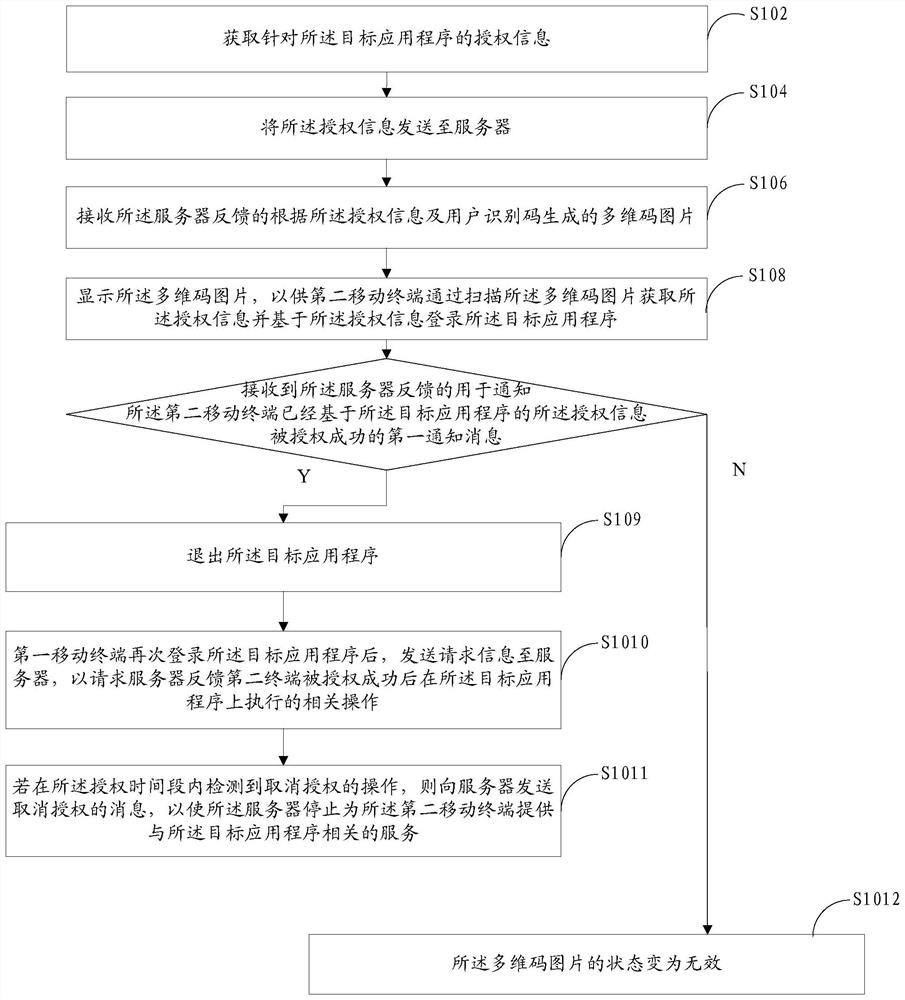
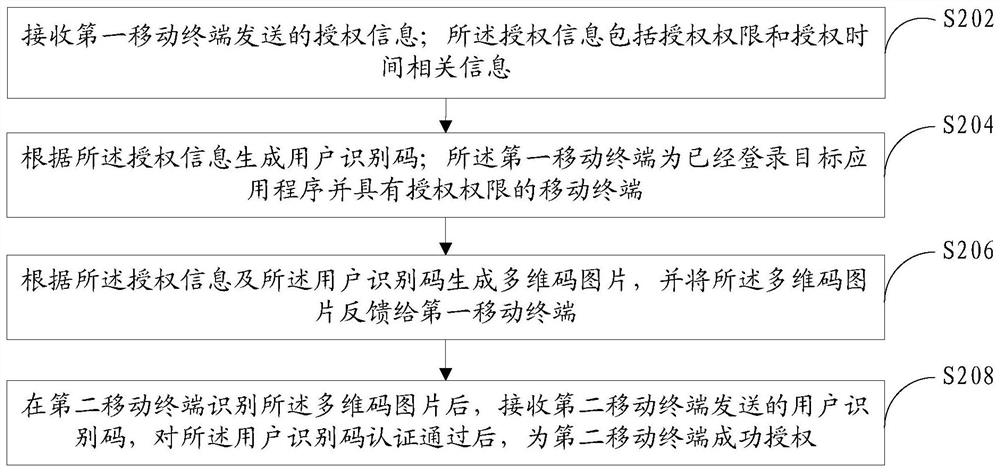
Authorization method based on multidimensional code, mobile terminal and server
ActiveCN109753784AAuthorization implementationDigital data authenticationTransmissionRelevant informationComputer terminal
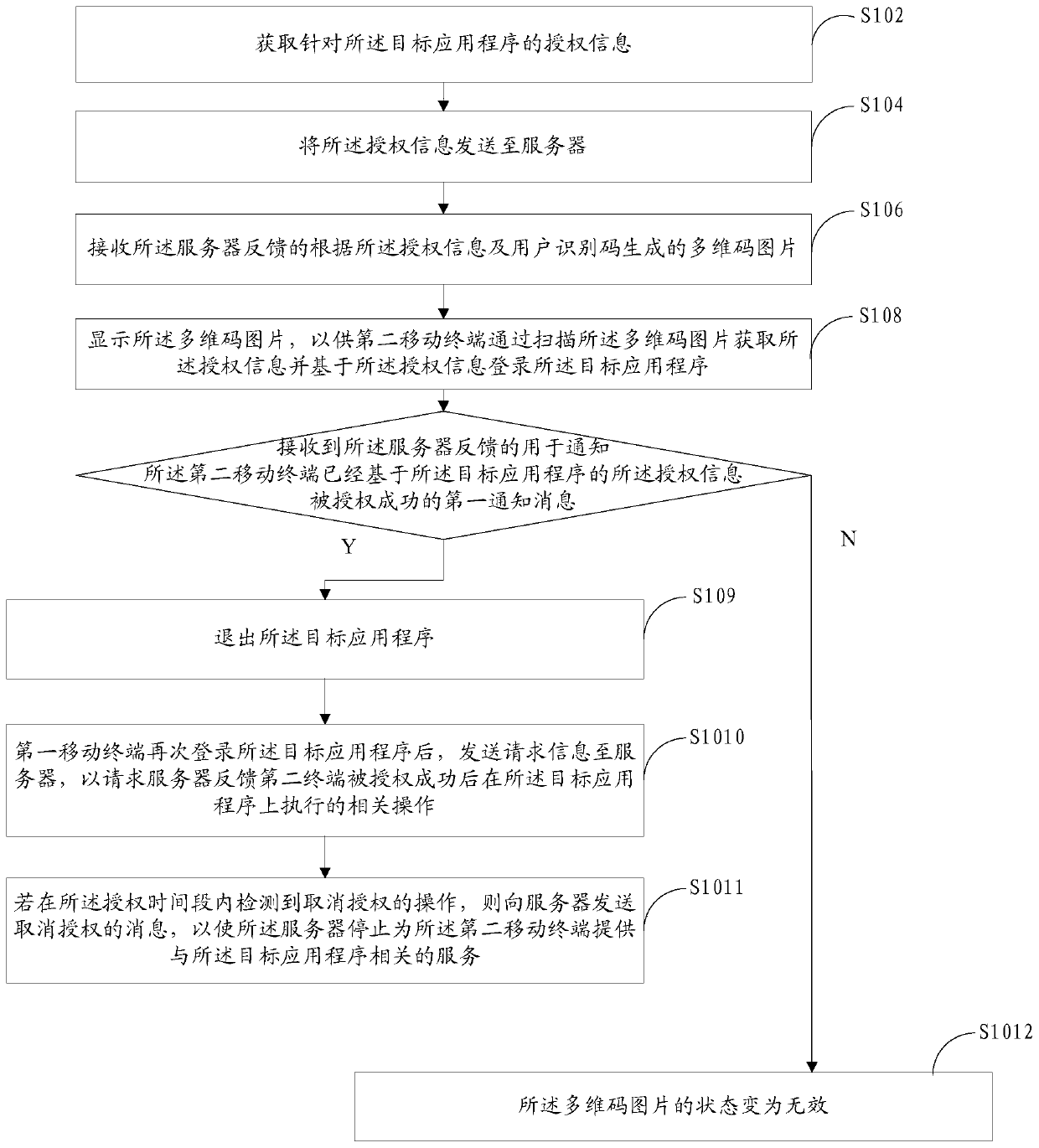
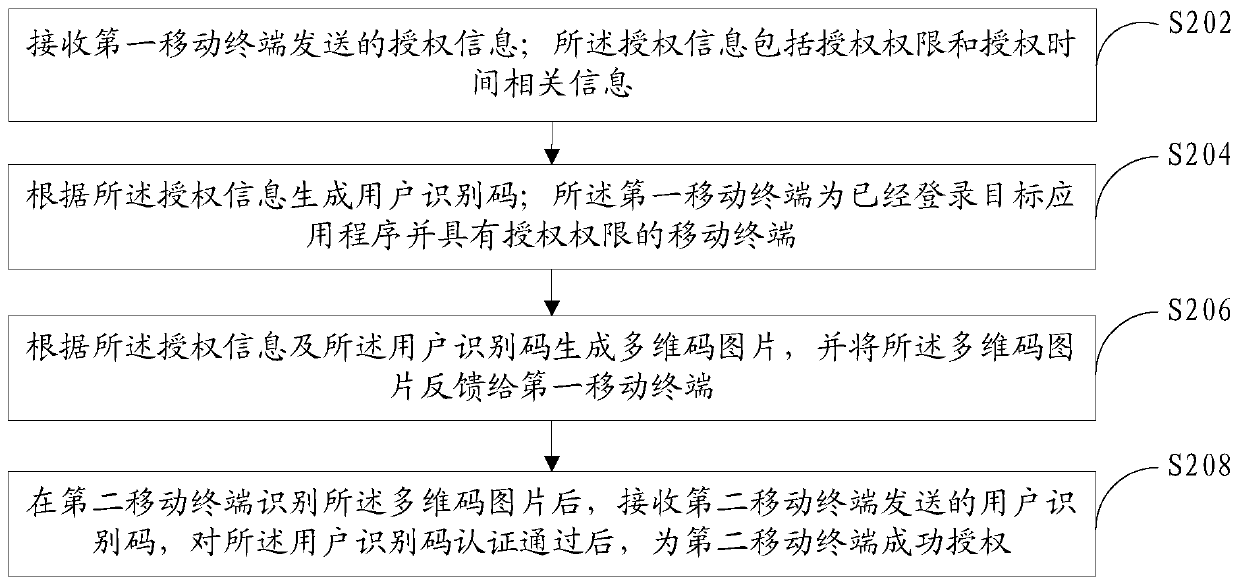
The invention discloses an authorization method based on a multi-dimensional code, a mobile terminal, and a server. The method applied to the first mobile terminal comprises: authorization informationfor a target application program is obtained, the authorization information comprises at least one of authorization permission and authorization time related information, and the first mobile terminal has logged in the target application program and has the authorization permission; sending the authorization information to a server; receiving a multi-dimensional code picture which is fed back bythe server and generated according to the authorization information and the user identification code; and displaying the multi-dimensional code picture, so that a second mobile terminal obtains the authorization information by scanning the multi-dimensional code picture and is successfully authorized based on the authorization information. According to the scheme, the mobile terminals can be authorized through the multi-dimensional codes, and the blank that authorization can only be carried out between the mobile terminals and a computer in the prior art is filled.
Owner:VIVO MOBILE COMM CO LTD
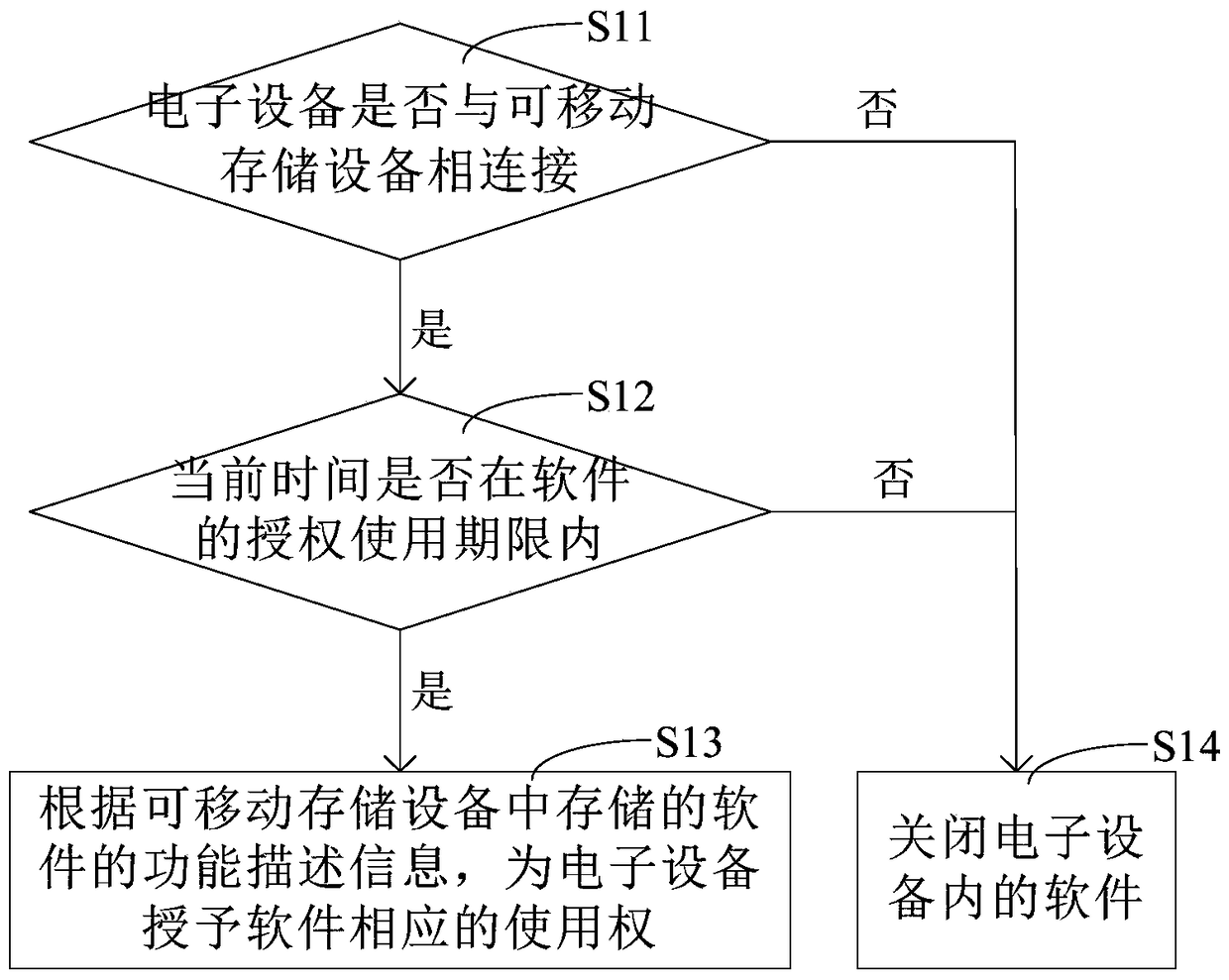
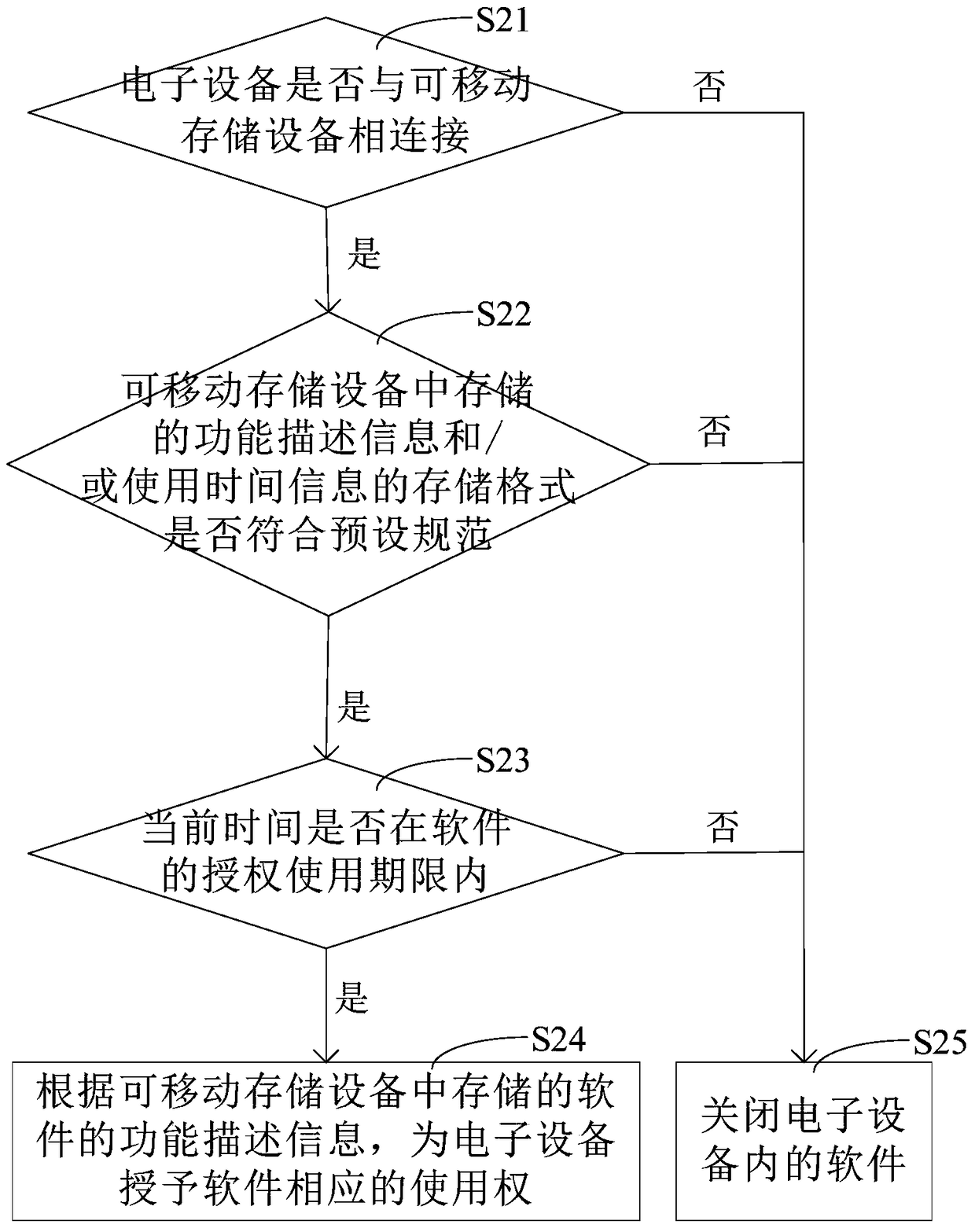
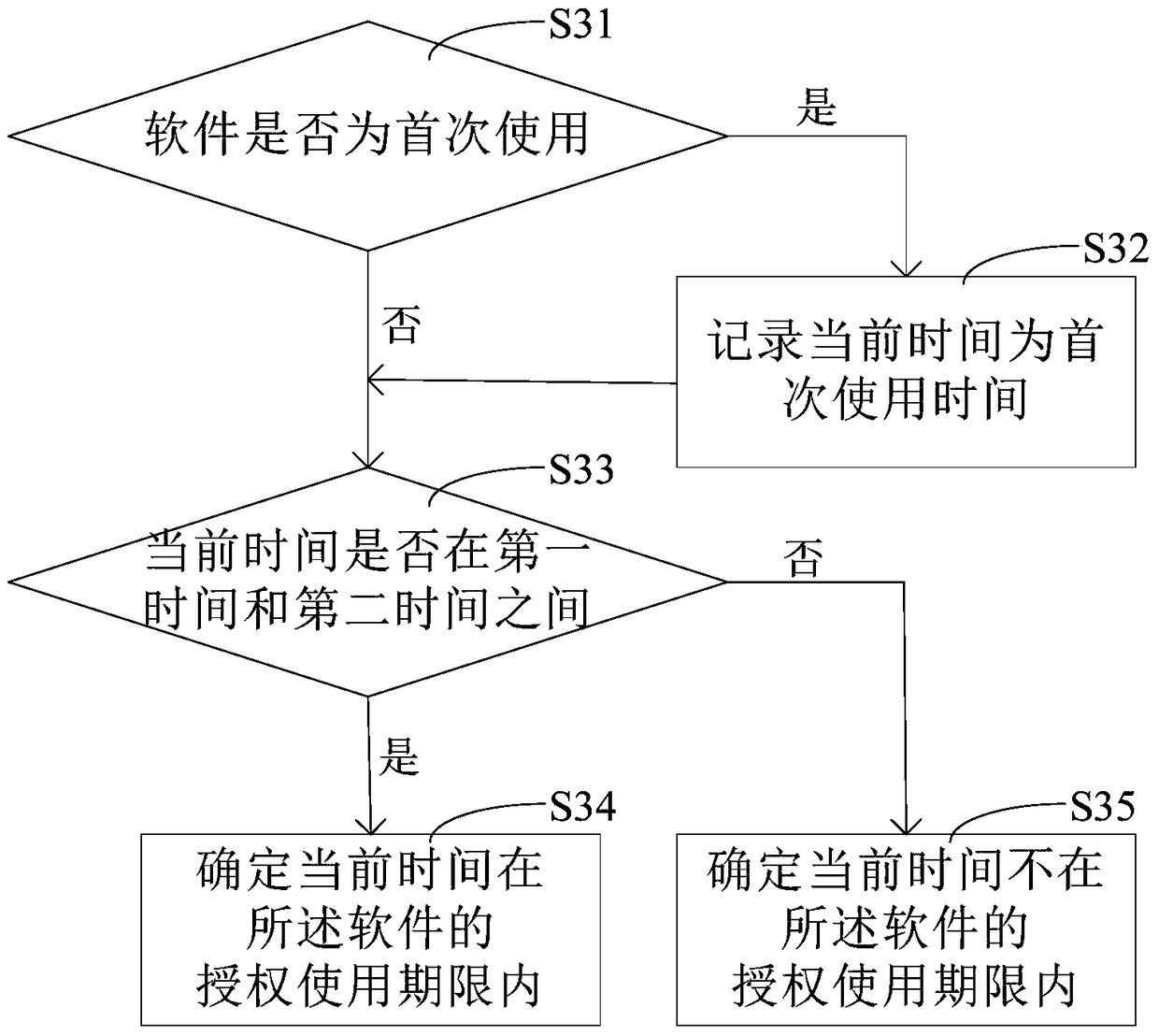
Method and device for authorizing software based on removable storage equipment
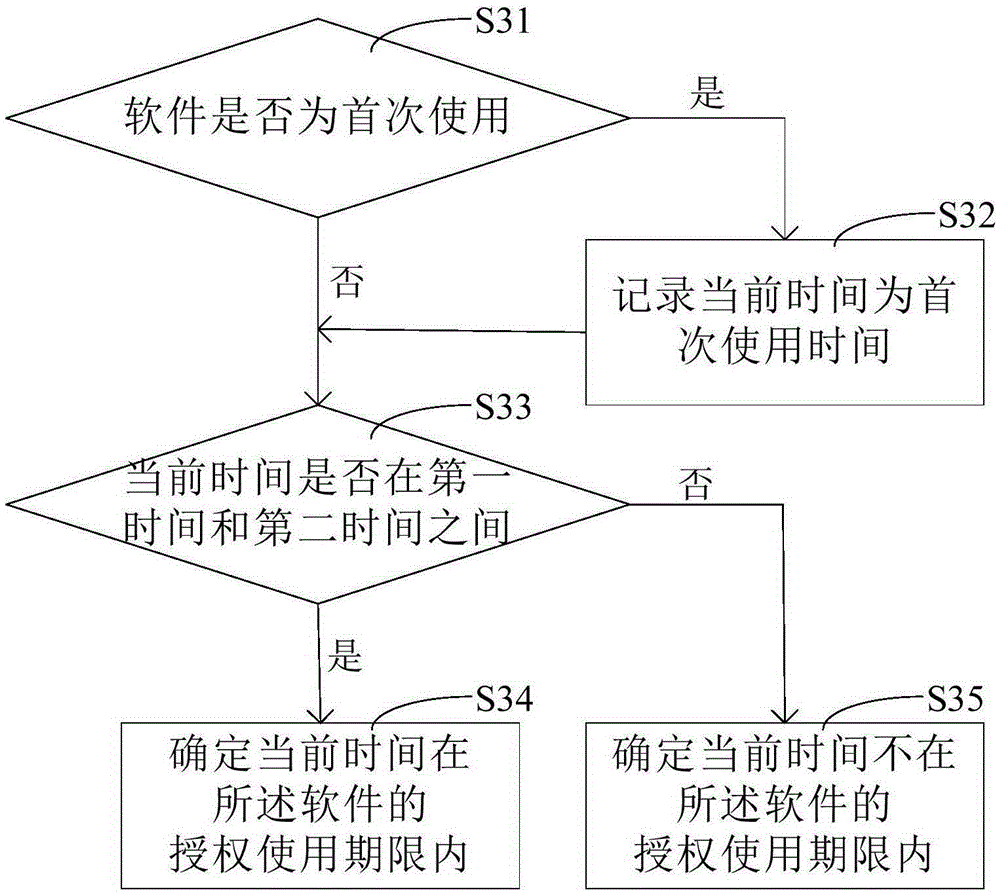
ActiveCN105335628AAuthorization implementationWarranty periodProgram/content distribution protectionTime informationState of art
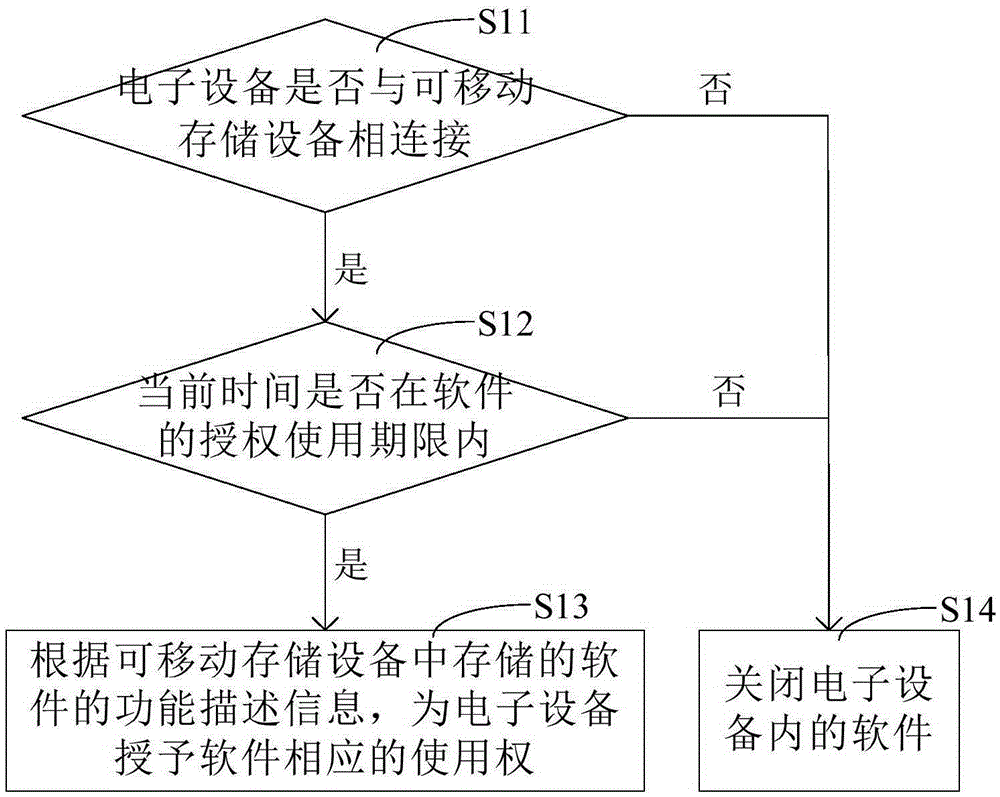
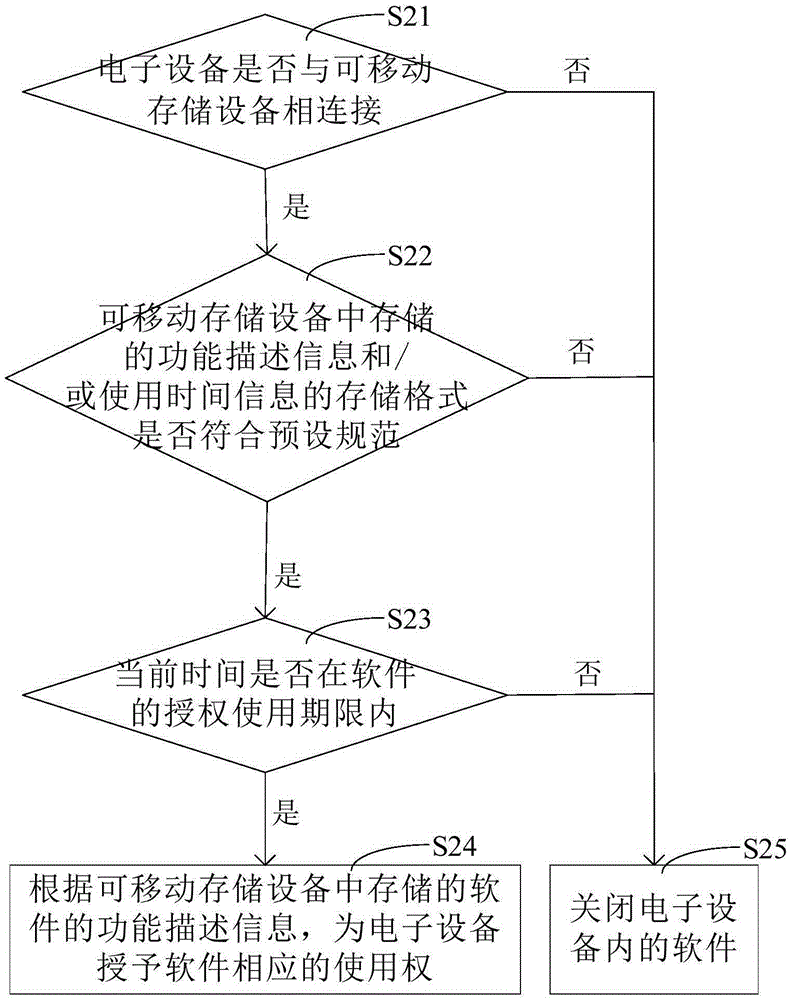
The invention discloses a method and a device for authorizing software based on removable storage equipment. Through a scheme disclosed by the invention, software authorization of electronic equipment can be realized; since the electronic equipment in the scheme is authorized through functional description information and using time information which are stored in the removable storage equipment, and the removable storage equipment can be connected with different electronic equipment, the removable storage equipment in which the functional description information and the using time information are stored is enabled to be connected with each electronic equipment needing to run the software when the scheme disclosed by the application is adopted for obtaining the software authorization; compared with the prior art which just can be used for carrying out the software authorization on stationary electronic equipment, through the scheme, the electronic equipment can be replaced; in addition, the software authorization of the electronic equipment can be obtained only when the current time is within an authorized service life of the software, so that the service life of the software is ensured.
Owner:LUSTER TERABAND PHOTONICS TECHNOLOGY CO LTD
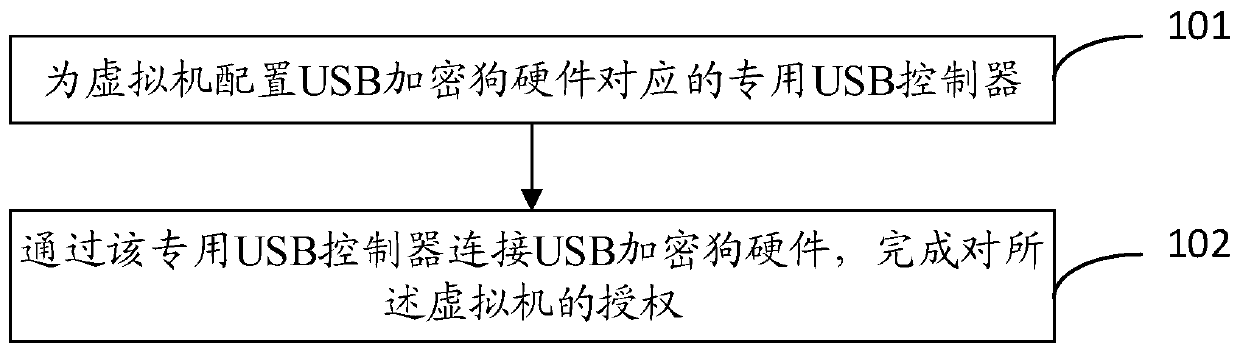
Method and apparatus for authorizing virtual machine software
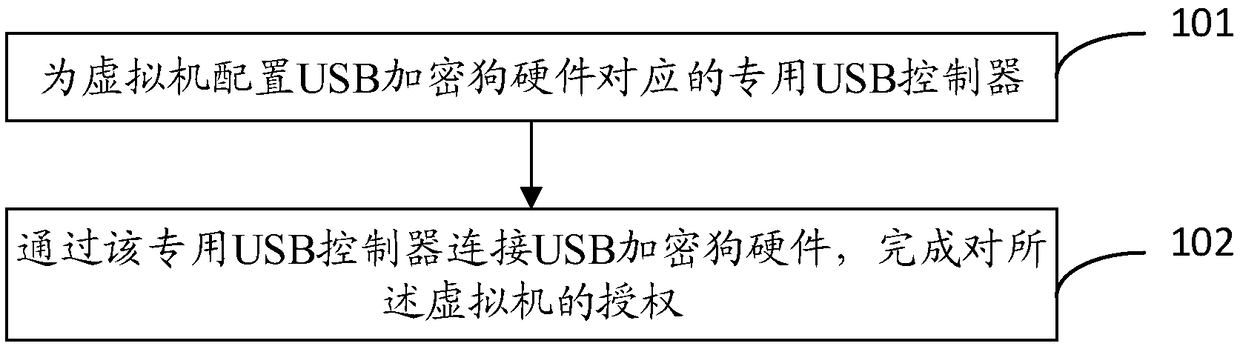
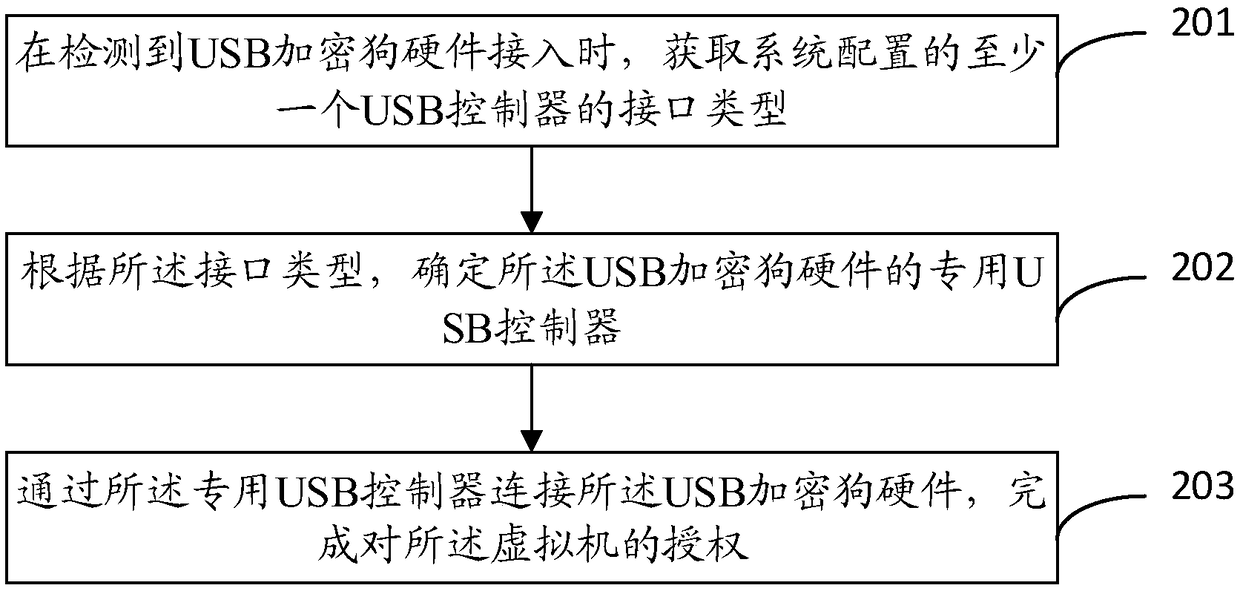
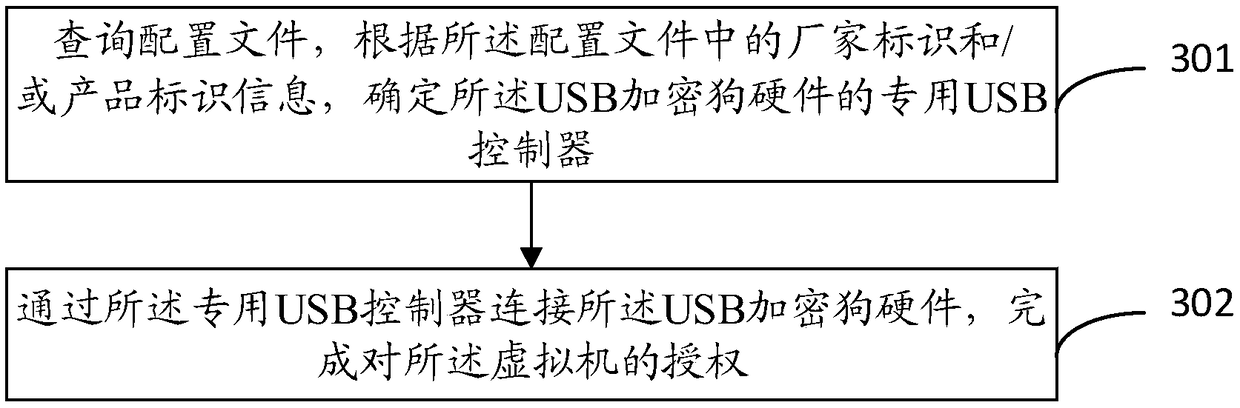
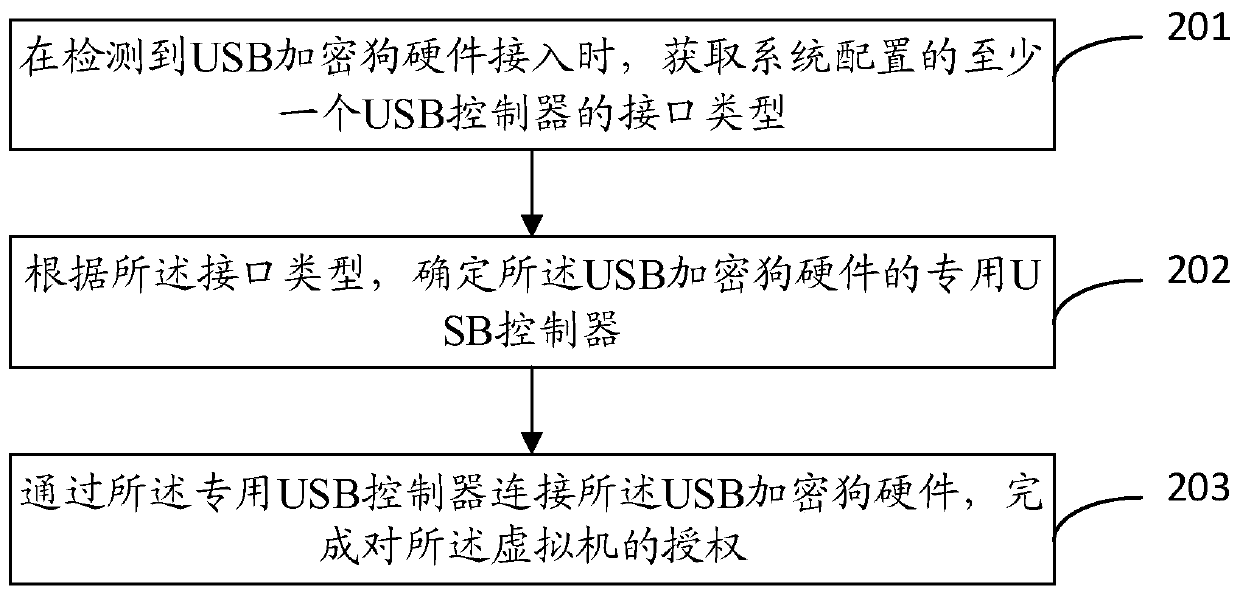
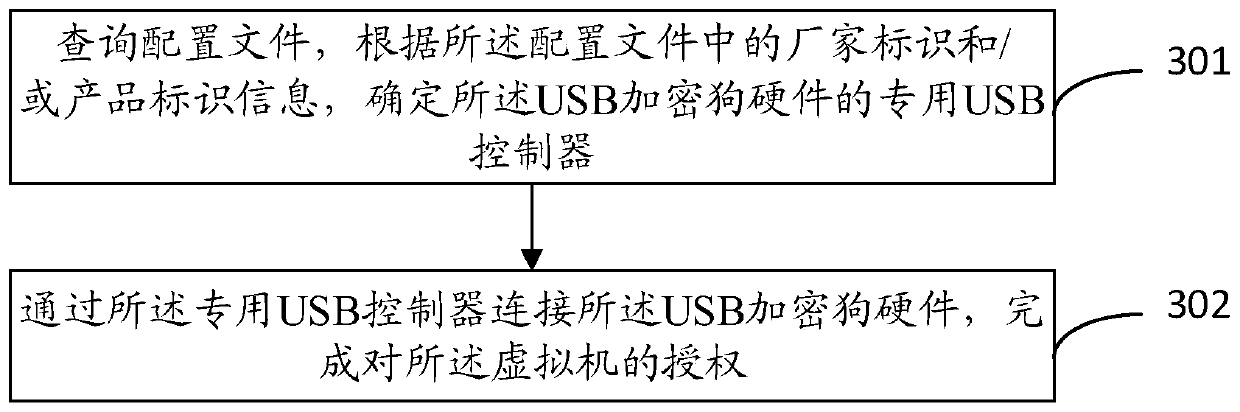
ActiveCN109033804AAuthorization implementationDigital data authenticationSoftware simulation/interpretation/emulationCanis lupus familiarisUSB
The invention discloses a virtual machine software authorization method and a device. The invention relates to a virtual machine security technology, which solves the problem of lacking a USB encryption dog mechanism of a virtual platform. The method comprises the following steps: configuring a special USB controller corresponding to the USB encryption dog hardware for the virtual machine; the USBencryption dog hardware being connected with the dedicated USB controller to complete the authorization of the virtual machine. The technical proposal provided by the invention is suitable for software management of a virtual platform, and software authorization based on USB encryption dog hardware in a virtual machine system is realized.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Elevator destination floor registration system, elevator control method and building authority management system
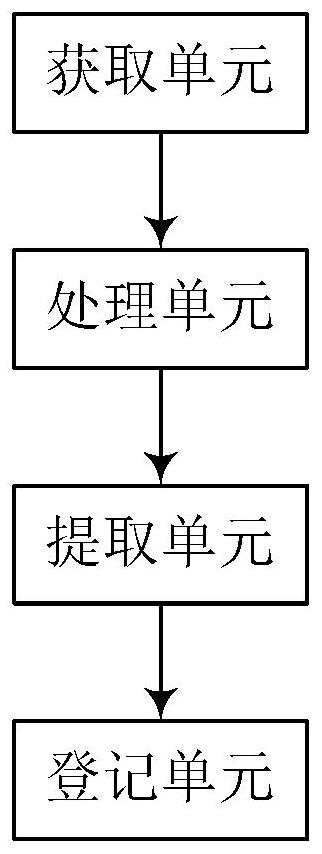
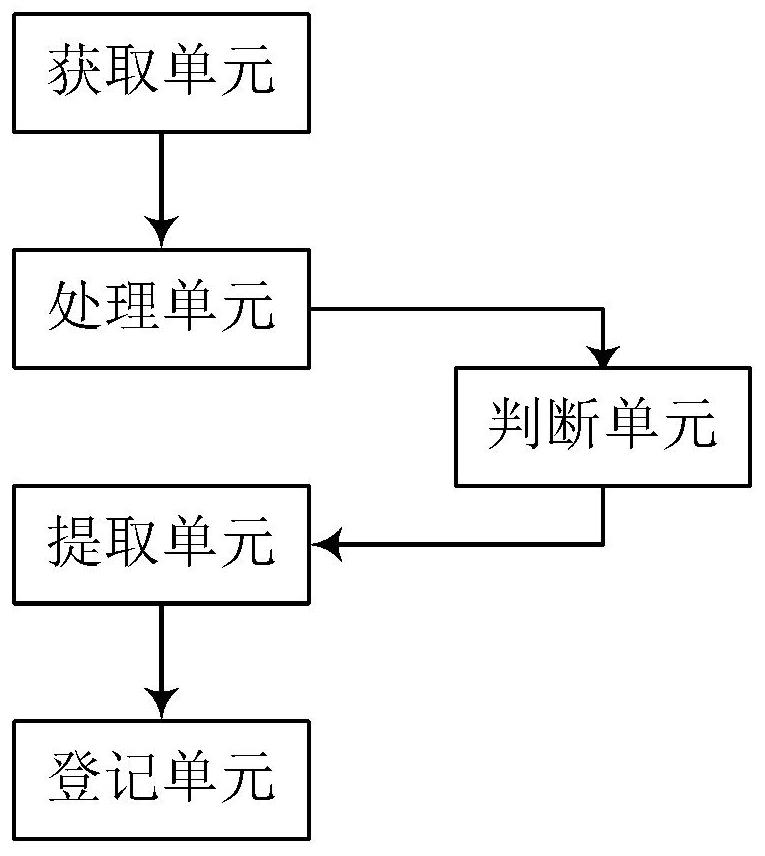
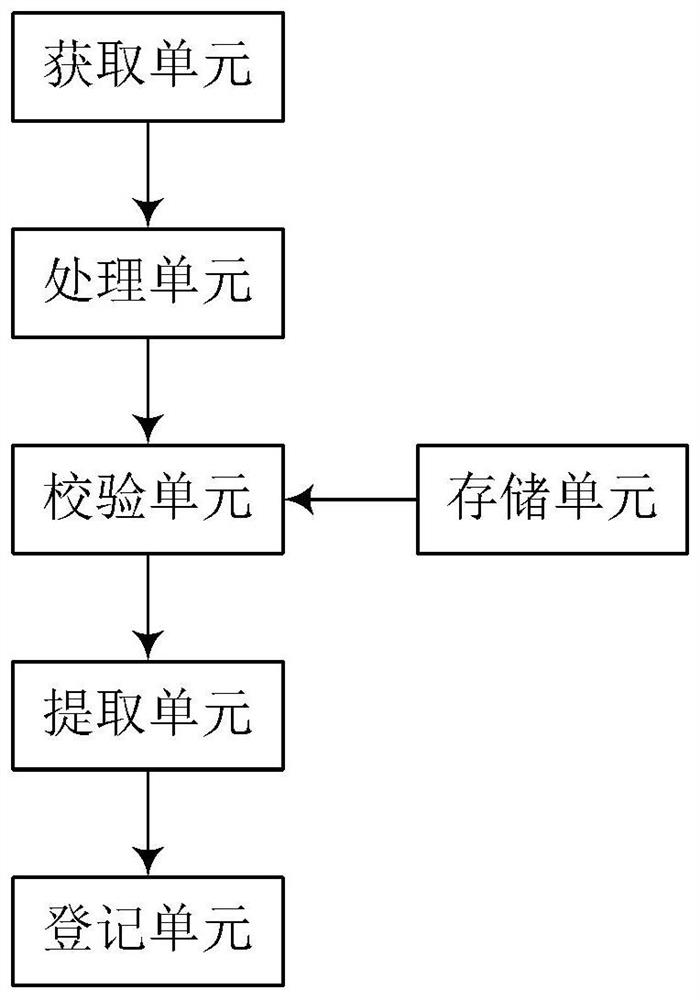
ActiveCN114291667AAuthorization implementationAvoid defects that affect shipping efficiencyElevatorsSustainable buildingsProcessing elementElevator control
The invention discloses an elevator destination floor registration system which comprises an acquisition unit used for acquiring a delivery bill image which comprises an image of consignee address information; the processing unit is used for processing the delivery bill image acquired by the acquisition unit and outputting delivery bill information containing the address information of the consignee; the extraction unit is used for extracting the floor where the consignee is located from the consignee address information contained in the delivery list information output by the processing unit; and the registration unit is used for registering the floor where the consignee is located, which is extracted by the extraction unit, as a target floor. The invention further discloses an elevator control method and a building authority management system. According to the method, the target floor can be quickly and conveniently obtained, the delivery personnel can be authorized, and the defect that the delivery personnel need to apply for obtaining authorization in advance every time when entering and exiting multiple buildings and multiple floors, and the delivery efficiency of the delivery personnel is affected is overcome.
Owner:SHANGHAI MITSUBISHI ELEVATOR CO LTD
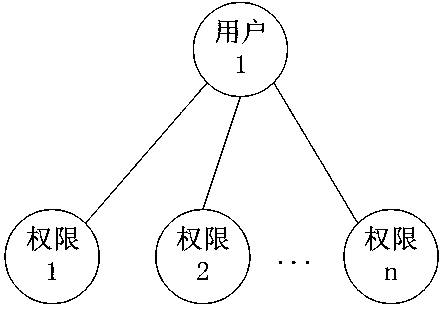
Authorization method capable of displaying current authority states of all system users
InactiveCN107480557AEasy to modifyAuthorization implementationDigital data protectionDigital data authenticationSoftware engineeringAuthorization
The invention discloses an authorization method capable of displaying the current authority states of all system users. The authorization method includes the steps that a form is selected; one element item of one element of the form is selected; all the system users in the system are displayed after the element item is selected, and the current authority state of the element item selected by each system user is displayed; the element items of one or more system users are authorized. After all the system users in the system are displayed, the current authority state of the element item selected by each system user is displayed, so that an authorization operator conducts modification on the basis conveniently to authorize the element items selected by the system users, and the authorization efficiency is improved.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
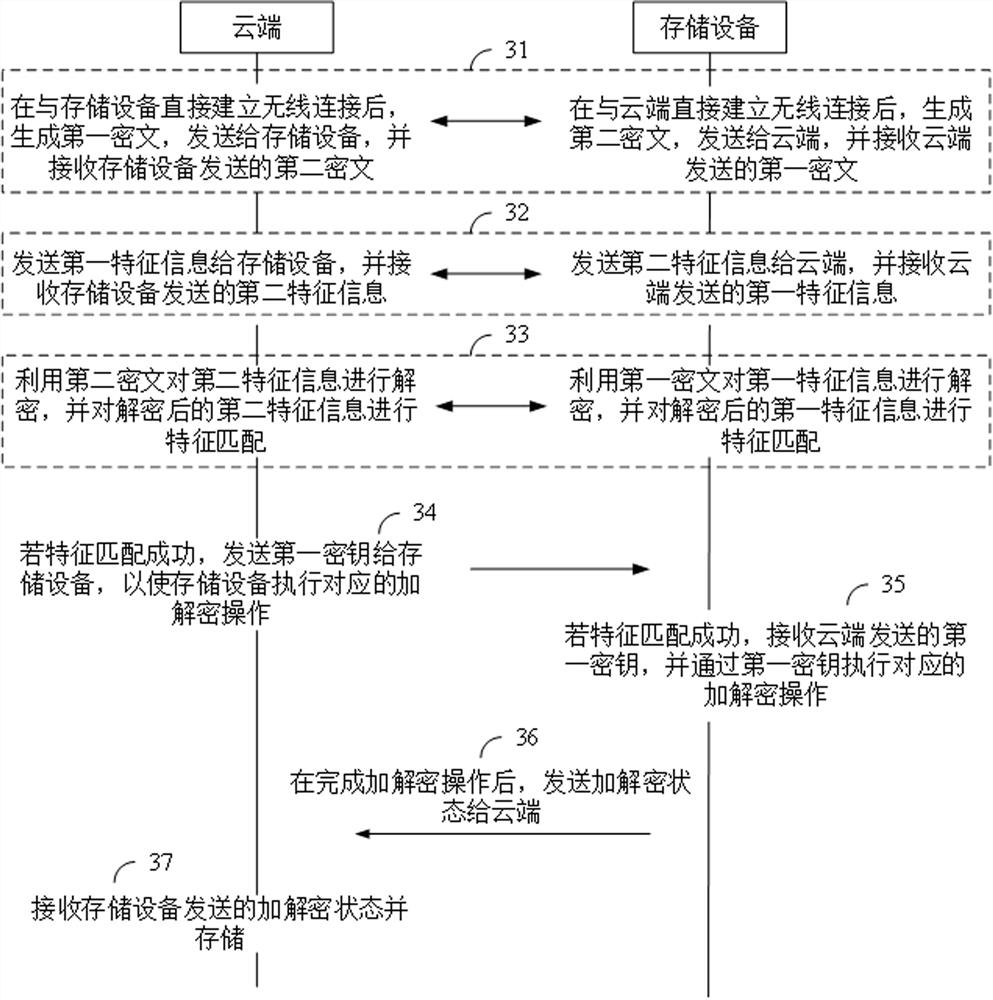
Data encryption and decryption method and system, server, storage device and mobile device
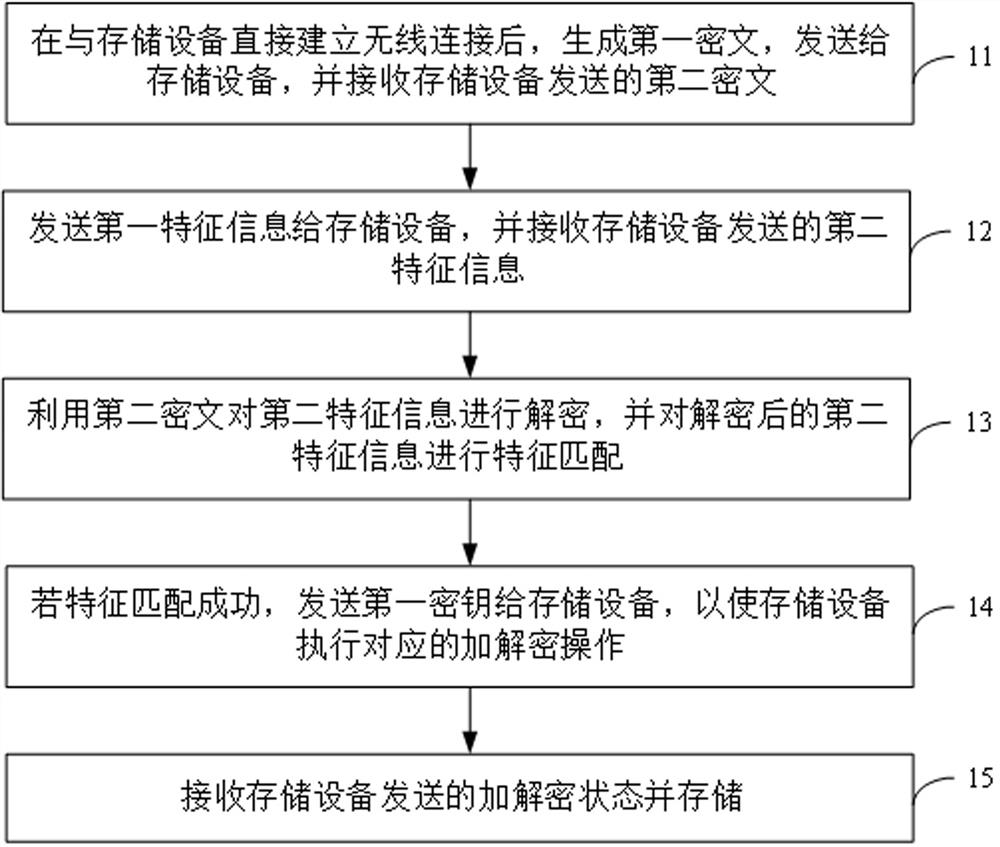
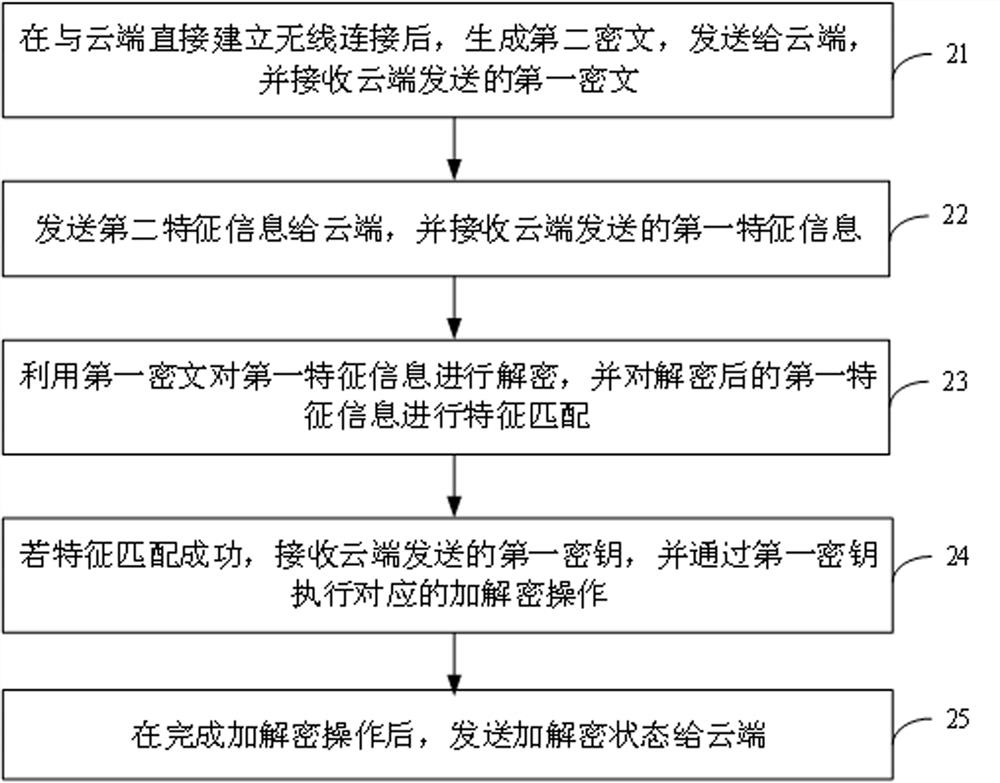
InactiveCN112601219AImplement two-way authenticationEnsure safetySecurity arrangementComputer hardwareCiphertext
The invention relates to a data encryption and decryption method and system, a server, a storage device and a mobile device. The data encryption and decryption method comprises the steps: generating afirst ciphertext after directly building wireless connection with the storage device, transmitting the first ciphertext to the storage device, and receiving a second ciphertext transmitted by the storage device; sending the first feature information to a storage device, and receiving second feature information sent by the storage device; decrypting the second feature information by using the second ciphertext, and performing feature matching on the decrypted second feature information; if the feature matching succeeds, sending a key to the storage device to enable the storage device to execute corresponding encryption and decryption operations; and receiving and storing the encryption and decryption state sent by the storage device. Thus, bidirectional authentication before data transmission is realized, the security of data transmission is further guaranteed, an authorizer does not need to independently provide a key, the key does not need to be worried about being forgotten and lost, and the implementation is convenient and rapid.
Owner:四川微巨芯科技有限公司
Method and system for providing authorization through mobile terminal
ActiveCN104063790BAuthorization implementationDigital data authenticationProtocols using social networksPayment transactionComputer terminal
A computing device receives an authentication code from a mobile terminal while the mobile terminal is in an offline state. The mobile terminal generates the authentication code based on payment authorization information it receives from a remote payment server while the mobile terminal is in an online state. The computing device extracts the payment authorization information from the authentication code and then generates a payment request using the payment authorization information, a payment amount and an authorized payment receiving account. Next, the computing device sends the payment request to the remote payment server. The remote payment server determines the validity of the payment request based on the payment authorization information, the payment amount and the authorized payment receiving account and returns a payment acknowledgment message to the remote computer. The computing device forwards the payment acknowledgment message to the mobile terminal, which then completes the payment transaction.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Authorization system and method based on set-top box cardless CA
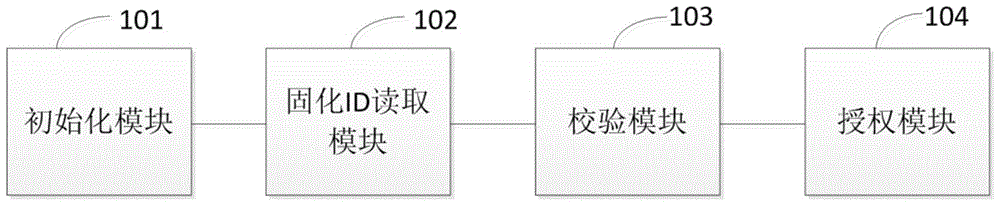
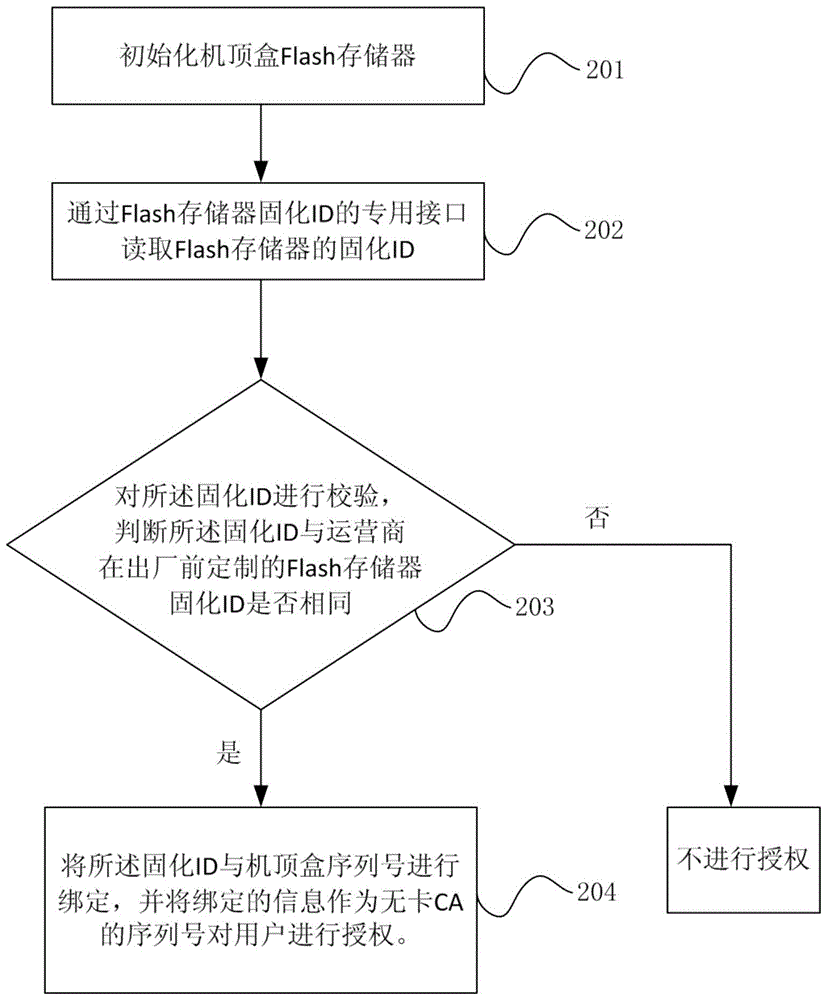
InactiveCN104079994BAuthorization implementationSelective content distributionAuthorization certificateSoftware engineering
The invention relates to the field of digital set top boxes, and provides an authorization system and method based on set top box card-free CA. The authorization system and method based on set top box card-free CA are used for solving the problem that a user cannot be authorized in the set top box card-free CA process. The authorization system comprises an initialization module, a cured ID reading module, a verification module and an authorization module. The initialization module is used for initialization of a set top box Flash memory. The cured ID reading module is used for reading the cured ID of the Flash memory. The verification module is used for verifying the cured ID. Whether the cured ID is the same as the cured ID, customized before delivery by an operator, of the Flash memory is judged according to the verification result, and if yes, the user is authorized. The chip ID of a master chip of a set top box is not used as an authorization certificate, so that the authorization system and method have the wider application range.
Owner:SICHUAN JINWANGTONG ELECTRONICS SCI & TECH
Small program login method, server and electronic device
ActiveCN111245825BImprove login efficiencyPromote generationUser identity/authority verificationSoftware engineeringAuthorization
The application discloses a small program login method, a server and an electronic device, and relates to the field of small programs. The first server receives the first information sent by the host program, and the first information includes the login state of the host program; requests the host server to verify the login state; and generates a login authorization code when the verification result of the login state verification is verified; Send the login authorization code to the applet attached to the host program, so that the applet can complete the login. Since the entire login process of the applet does not need to use a specified account to log in, the login can be completed through the user information of the user logging in to the host program, which improves the login efficiency of the applet. Since the first server can receive login status information of multiple host clients, and perform login status verification through the host server corresponding to the host client, the same set of login authorization services provided by the first server can be connected to different account systems of different host programs, Reduced development costs.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Authorization method, mobile terminal and server based on multidimensional code
ActiveCN109753784BAuthorization implementationDigital data authenticationTransmissionEngineeringAuthorization
Owner:VIVO MOBILE COMM CO LTD
Method, device and system for authorizing account use rights
ActiveCN106549926BImprove securityRealize personalizationTransmissionTerminal equipmentComputer terminal
The embodiment of the invention provides a method, a device and a system for authorizing permission to an account. The method comprises the steps of determining whether first terminal equipment is operated by a first user when an account permission authorization command is detected; if the first terminal equipment is operated by the first user is determined, determining to call a preset permission seed corresponding to the user account of the first user, and determining authorization content of the user account indicated by the first user; generating authorization information according to the permission seed and the authorization content, thus allowing second terminal equipment to send the authorization information to a server after acquiring the authorization information, and allowing the server to authorize the user account corresponding to the permission seed to execute the authorization content. According to the method, the device and the system provided by the embodiment of the invention, security of the account is improved during a process of authorizing the permission to the account.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Authorization method that displays the current permission status of all system users
ActiveCN109064138AEasy to modifyAuthorization implementationDigital data authenticationOffice automationSystem usageAuthorization
The invention discloses an authorization method for displaying the current authorization status of all system users. Selecting an element item of a form element of the form; After the element item isselected, all system users in the system are displayed, and the current permission status of each system user on the selected element item is displayed. Authorization of that selecte element items isperform on one or more users of the system. After displaying all system users in the system, the invention displays the current authorization status of each system user to the selected element item, which is convenient for authorized operator to modify on the basis, realizes authorization of the selected element item for the system user, and improves authorization efficiency.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
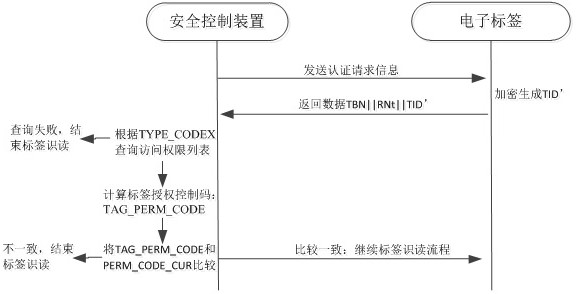
Security control device, authority authorization method and electronic tag reading method
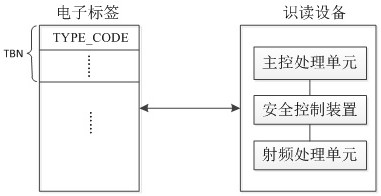
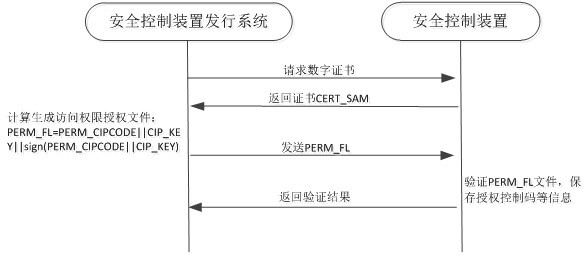
ActiveCN112364330AReduce R&D and operating costsAuthorized data is safe and reliableDigital data protectionInternal/peripheral component protectionRadio frequencyInternet privacy
The invention designs a security control device, an authority authorization method and an electronic tag reading method, which can apply a single reading device to multiple industry fields to realizecompatible reading, thereby reducing the research and operation cost of reading equipment, including a national password security chip. A security control device is saved in the national password security chip. An issuing system is composed of a certificate CERT_SAM, a root certificate CERT_ISSUE of the issuing system of the security control device, a private key SAM_PRIKEY of the security controldevice and an electronic tag access permission list, all of which are stored in the national secret security chip, and the certificate CERT_SAM comprises a serial number SAM_SN of the security control device; the security control device is provided with an interface connected with a main control processing unit and used for sending an access permission authorization file to the security control device through the main control processing unit, and the security control device is further provided with an interface connected with the radio frequency processing unit and used for achieving the specific reading process of an electronic tag.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
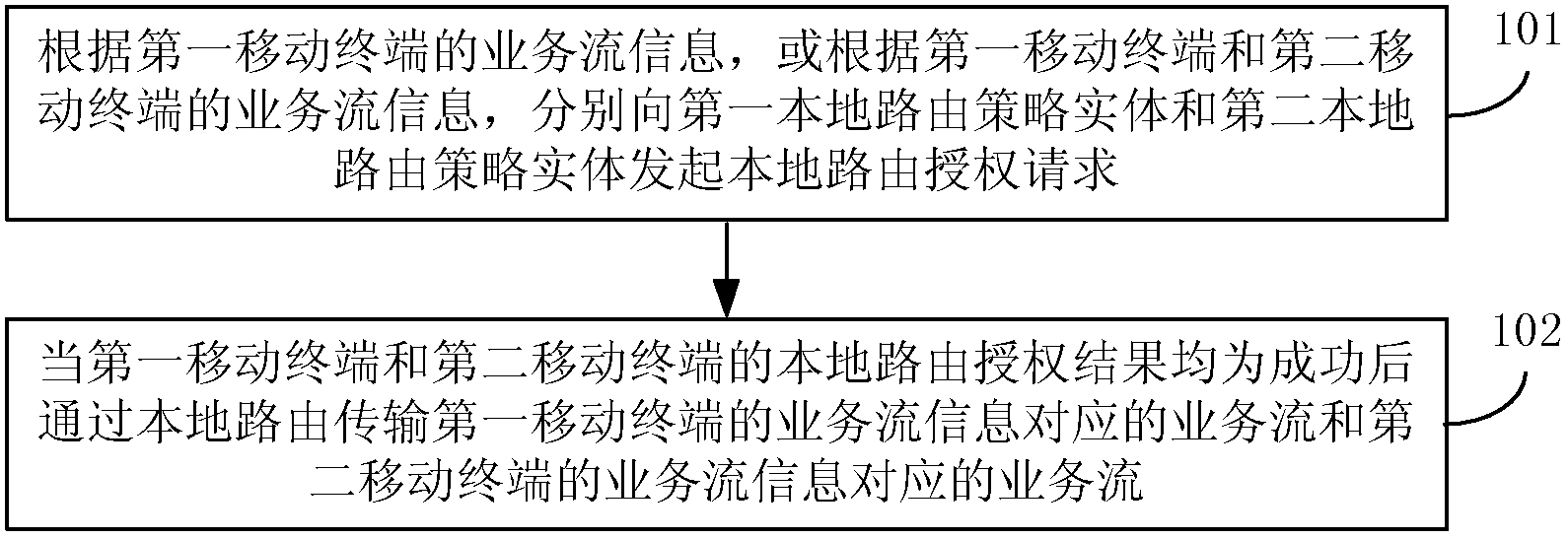
Method, device and system for local route authorization
ActiveCN102369699BAuthorization implementationSatisfy authorization requirementsMetering/charging/biilling arrangementsSecurity arrangementService flowTelecommunications
A method includes: respectively initiating a local routing authorization request to a first local routing policy entity and a second local routing policy entity according to service flow information of a first mobile station, so as to enable the first local routing policy entity to perform local routing authorization for the first mobile station and enable the second local routing policy entity to perform local routing authorization for the second mobile station; and when a local routing authorization result of the first mobile station and a local routing authorization result of the second mobile station are both success, transmitting, through local routing, a service flow corresponding to the service flow information of the first mobile station and a service flow corresponding to the service flow information of the second mobile station.
Owner:HUAWEI TECH CO LTD
A virtual machine software authorization method and device
ActiveCN109033804BAuthorization implementationDigital data authenticationSoftware simulation/interpretation/emulationDongleAuthorization
The invention discloses a virtual machine software authorization method and a device. The invention relates to a virtual machine security technology, which solves the problem of lacking a USB encryption dog mechanism of a virtual platform. The method comprises the following steps: configuring a special USB controller corresponding to the USB encryption dog hardware for the virtual machine; the USBencryption dog hardware being connected with the dedicated USB controller to complete the authorization of the virtual machine. The technical proposal provided by the invention is suitable for software management of a virtual platform, and software authorization based on USB encryption dog hardware in a virtual machine system is realized.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Payment terminal offline authorization method and system based on IC card
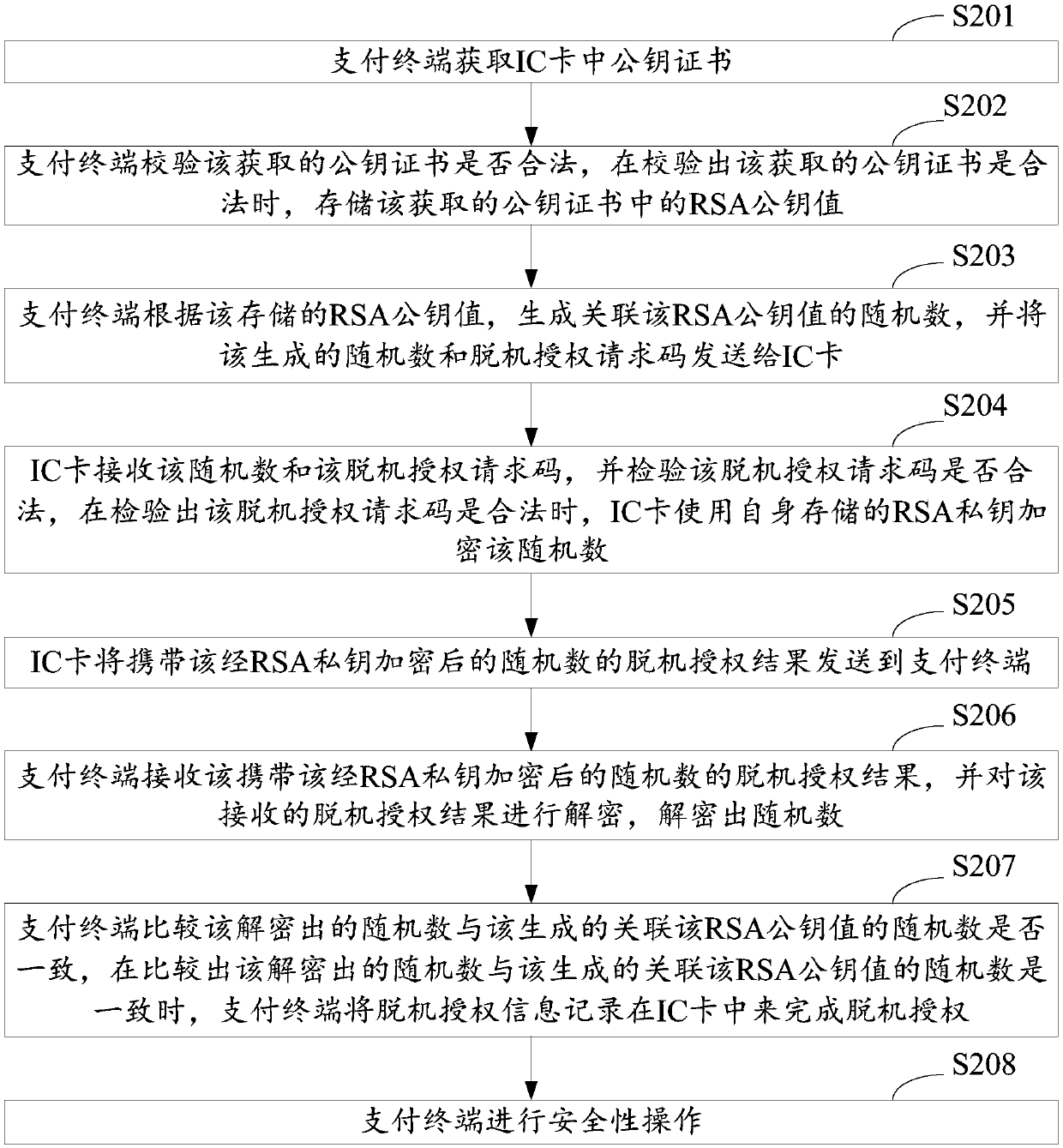
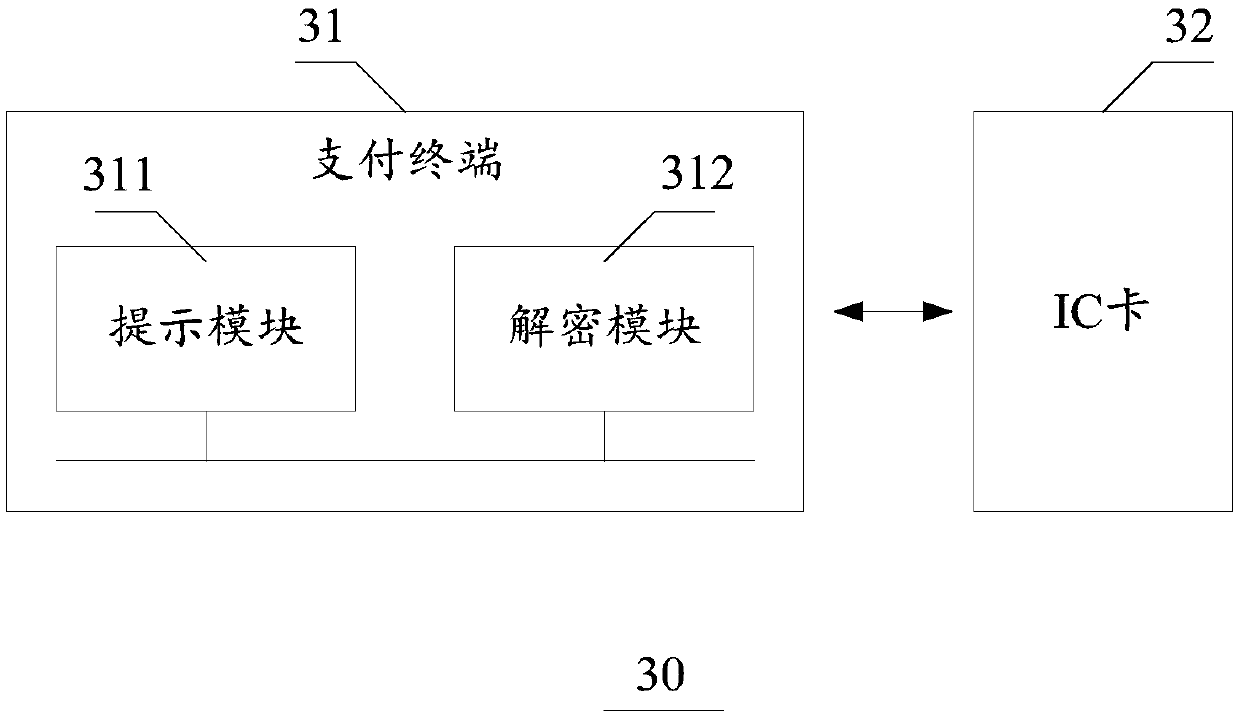
InactiveCN109636381AAchieve securityEnsure safetyProtocol authorisationAuthorizationPayment terminal
The invention discloses a payment terminal offline authorization method and system based on an IC card. The method comprises the following steps of: obtaining a target object, the payment terminal cancompare whether the decrypted random number is consistent with the generated random number of the associated RSA public key value or not, and when it is compared that the decrypted random number is consistent with the generated random number of the associated RSA public key value, the payment terminal can record offline authorization information in an IC card to complete offline authorization. Through the above mode, the safety operation of the payment terminal can be authorized in an offline mode.
Owner:FUJIAN NEWLAND PAYMENT TECH
Method, device and system for obtaining data authorization
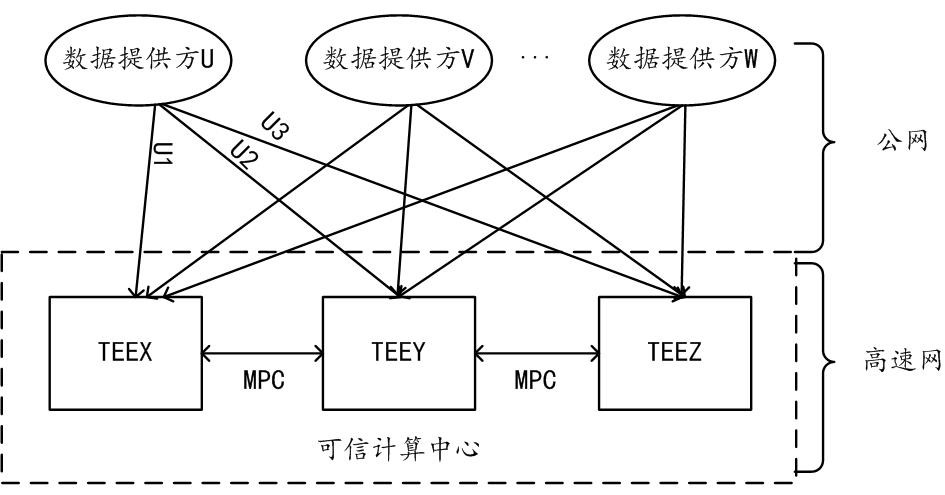
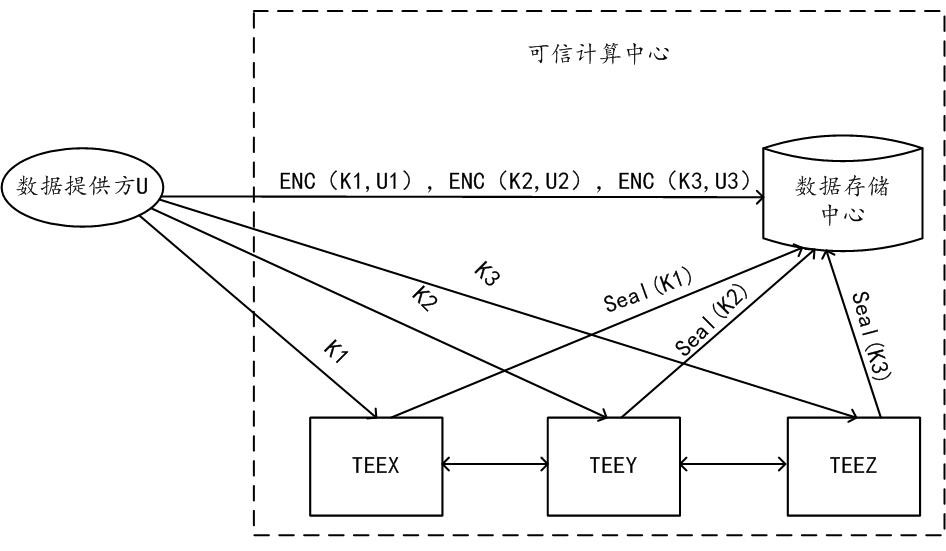
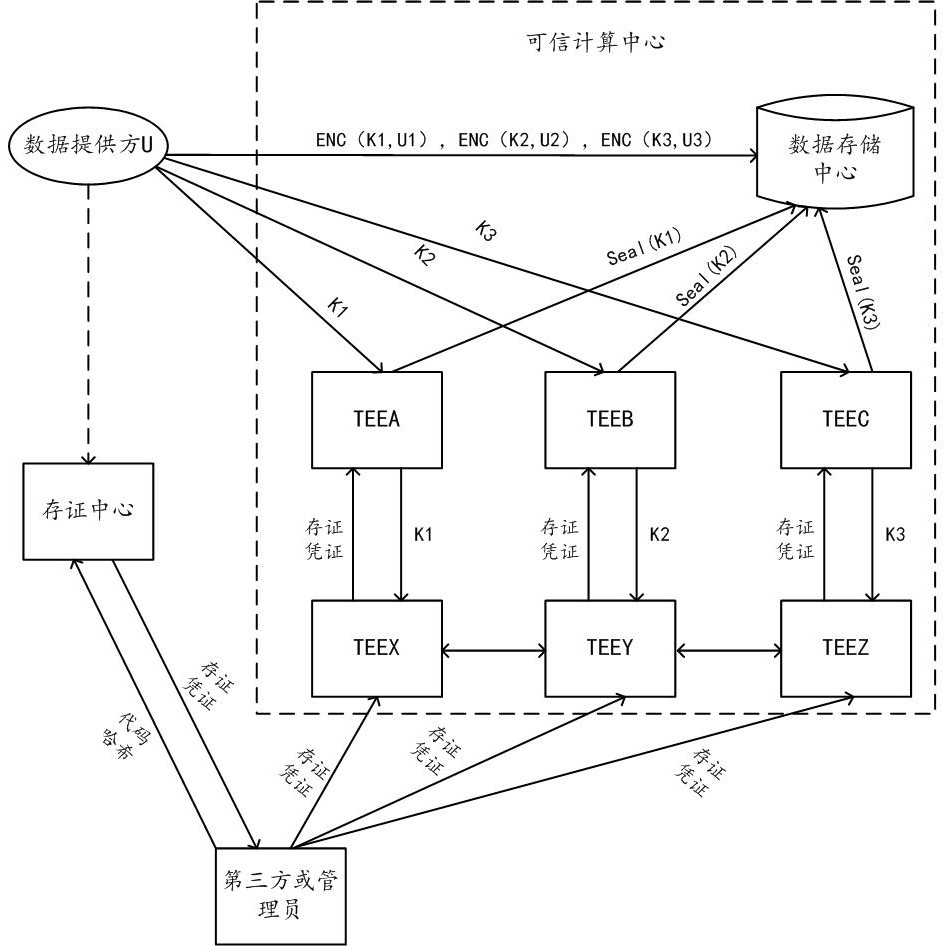
ActiveCN113987554BAuthorization implementationDigital data protectionDigital data authenticationShardComputational logic
The embodiments of this specification provide a method, device and system for obtaining data authorization. In the method for obtaining data authorization, any first computing node in the trusted computing center receives an authentication request from the first provider. Authentication information is returned to the first provider, including at least a first code hash of the first computing logic running in the first computing node. Receive the channel establishment request sent by the first provider after determining that the first computing node has passed the trusted authentication and the first code hash has passed the correctness verification. Establish a first trusted channel with the first provider according to the channel establishment request. Through the first trusted channel, the target encryption key among the encryption keys of several encrypted slices obtained based on the privacy data of the data provider is received, so as to obtain the target encryption key corresponding to the target encryption key based on the first calculation logic. Permission to perform calculations on shards. Thus, the security of the private data of the data provider can be ensured.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A Distributed Trusted Organization Identity Access Control System and Method
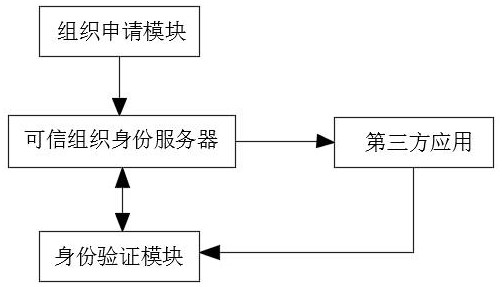
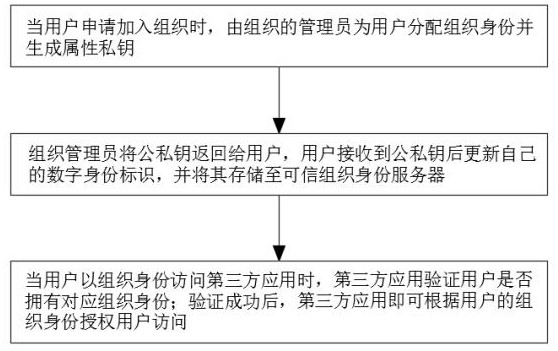
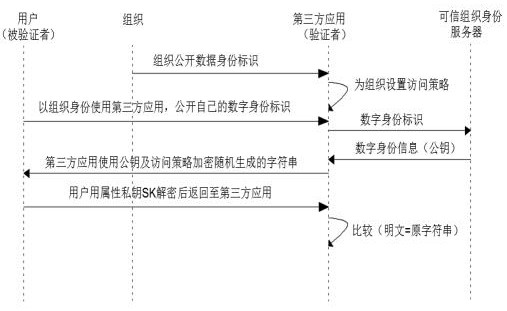
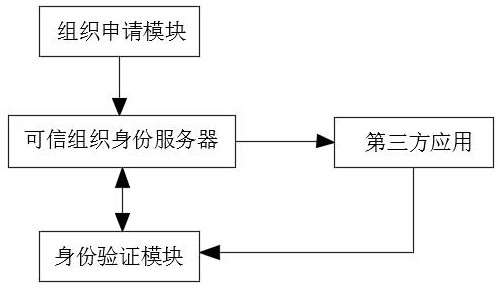
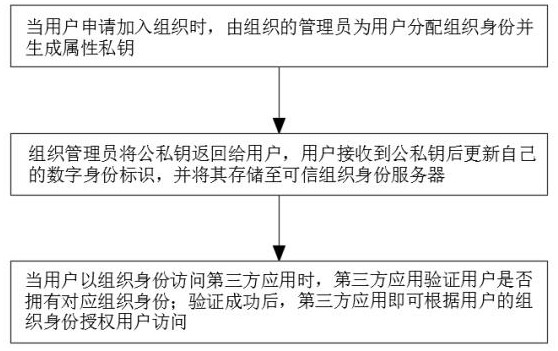
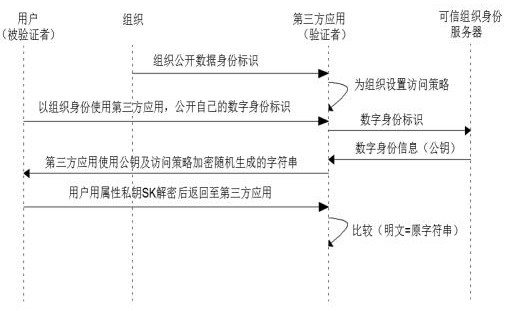
ActiveCN113641985BImprove securityAuthorization implementationDigital data authenticationThird partyAccess structure
The invention discloses a distributed trusted organization identity access control system and method, relates to the technical field of information security, and solves the technical problem of organization identity verification in the business scenario of multi-organization cooperation without leaking privacy; including Organization application module, trusted organization identity server and identity verification module. The organization application module is used for users to apply for organization identity. The administrator of the organization assigns the organization identity to the user and generates the attribute private key based on the CP‑ABE cryptographic algorithm; when the user uses When an organization identity accesses a third-party application, the identity verification module is used by the third-party application to verify whether the user has the corresponding organization identity. The present invention verifies the individual organization identity through the user's private key SK. "Zero-knowledge" proof, and the third-party application system authorizes and controls access according to the access structure, which greatly improves information security.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
Distributed trusted organization identity access control system and method
ActiveCN113641985AImprove securityAuthorization implementationDigital data authenticationAccess structureThird party
The invention discloses a distributed trusted organization identity access control system and method, which relate to the technical field of information security, and solve the technical problem of organization identity verification in a business scene of multi-organization cooperation under the condition of not leaking privacy. The system comprises an organization application module, a trusted organization identity server and an identity verification module, wherein the organization application module is used for a user to apply for an organization identity, and an organization administrator allocates the organization identity to the user and generates an attribute private key based on a CP-ABE cryptography algorithm; when the user accesses the third-party application with the organization identity, the identity verification module is used for the third-party application to verify whether the user has the corresponding organization identity, the individual organization identity is verified through the user private key SK, the user does not need to provide any privacy data in the whole verification process, namely, so-called 'zero-knowledge' proof is achieved, And meanwhile, the third-party application system performs authorization and access control according to the access structure, so that the information security is greatly improved.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
An access control method, device, computer equipment and storage medium
ActiveCN110569667BAuthorization implementationDigital data protectionSoftware engineeringAuthorization
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
A software authorization method and device based on a removable storage device
ActiveCN105335628BAuthorization implementationWarranty periodProgram/content distribution protectionTime informationSoftware engineering
The invention discloses a method and a device for authorizing software based on removable storage equipment. Through a scheme disclosed by the invention, software authorization of electronic equipment can be realized; since the electronic equipment in the scheme is authorized through functional description information and using time information which are stored in the removable storage equipment, and the removable storage equipment can be connected with different electronic equipment, the removable storage equipment in which the functional description information and the using time information are stored is enabled to be connected with each electronic equipment needing to run the software when the scheme disclosed by the application is adopted for obtaining the software authorization; compared with the prior art which just can be used for carrying out the software authorization on stationary electronic equipment, through the scheme, the electronic equipment can be replaced; in addition, the software authorization of the electronic equipment can be obtained only when the current time is within an authorized service life of the software, so that the service life of the software is ensured.
Owner:LUSTER TERABAND PHOTONICS TECHNOLOGY CO LTD
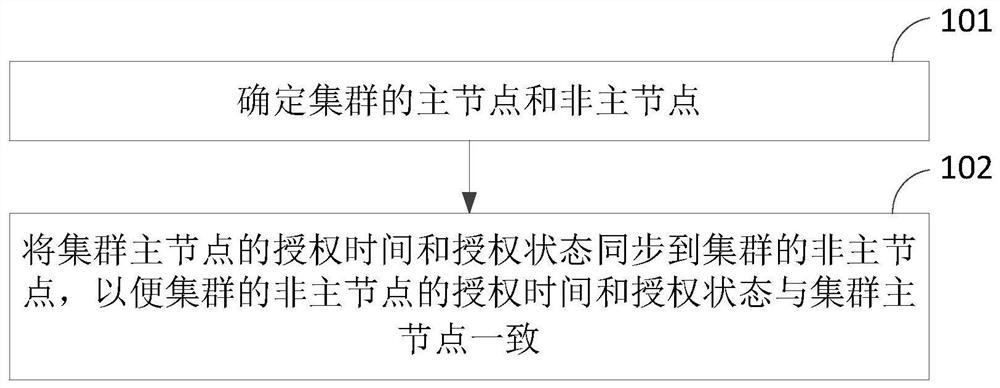
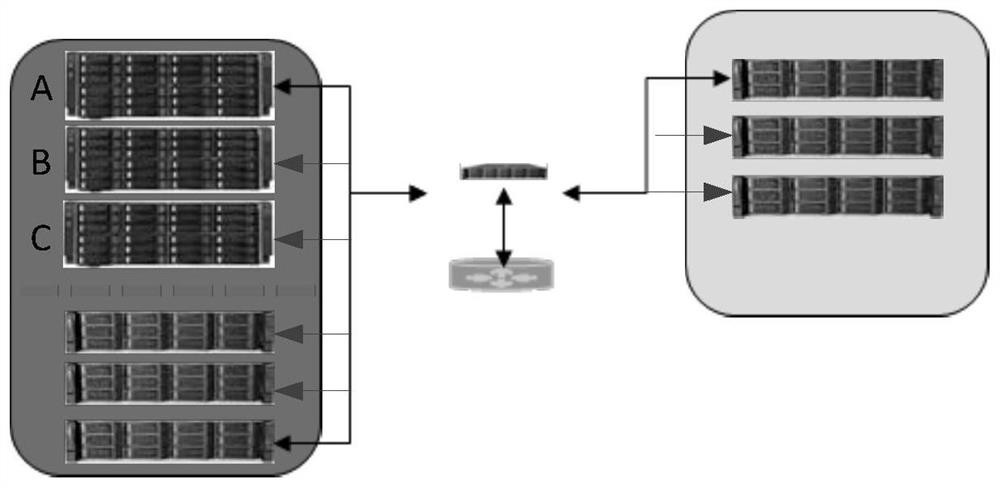
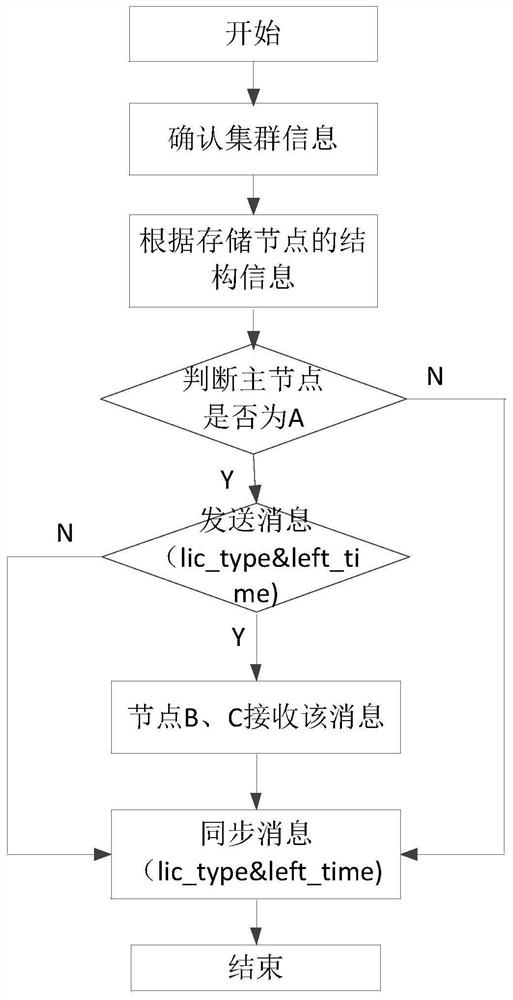
A cluster authorization method and device based on unified management
ActiveCN109088937BNormal serviceConsistent authorization timeTime-division multiplexTransmissionEngineeringAuthorization
The present application discloses a cluster authorization method and device based on unified management. The method includes: after determining the master node and the non-master node in the cluster, synchronizing the authorization time and authorization status of the master node of the cluster to other nodes in the cluster All non-master nodes, so that the authorization time and authorization status of all other non-master nodes in the cluster are consistent with the cluster master node. In this way, the authorization time and authorization status of all nodes in the cluster are guaranteed to be consistent, and unified management is realized. Cluster authorization. It can be seen that this application no longer uses the method of independently calculating the authorization time for each node, but after determining the master node and non-master nodes in the cluster, the authorization time and authorization status of the cluster master node are synchronized to all other nodes in the cluster. Non-master nodes, so as to realize the unified management of the authorization time and authorization state of each node in the cluster, thereby ensuring that the authorization time of all nodes in the cluster is consistent, and ensuring that the cluster can provide services normally.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com