Authorized rule for extending public group in presenting authorized strategy
A regular and public technology, applied in branch offices to provide special service devices, data exchange details, digital transmission systems, etc., can solve problems such as not supporting group public identification, not handling group public identification authorization, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
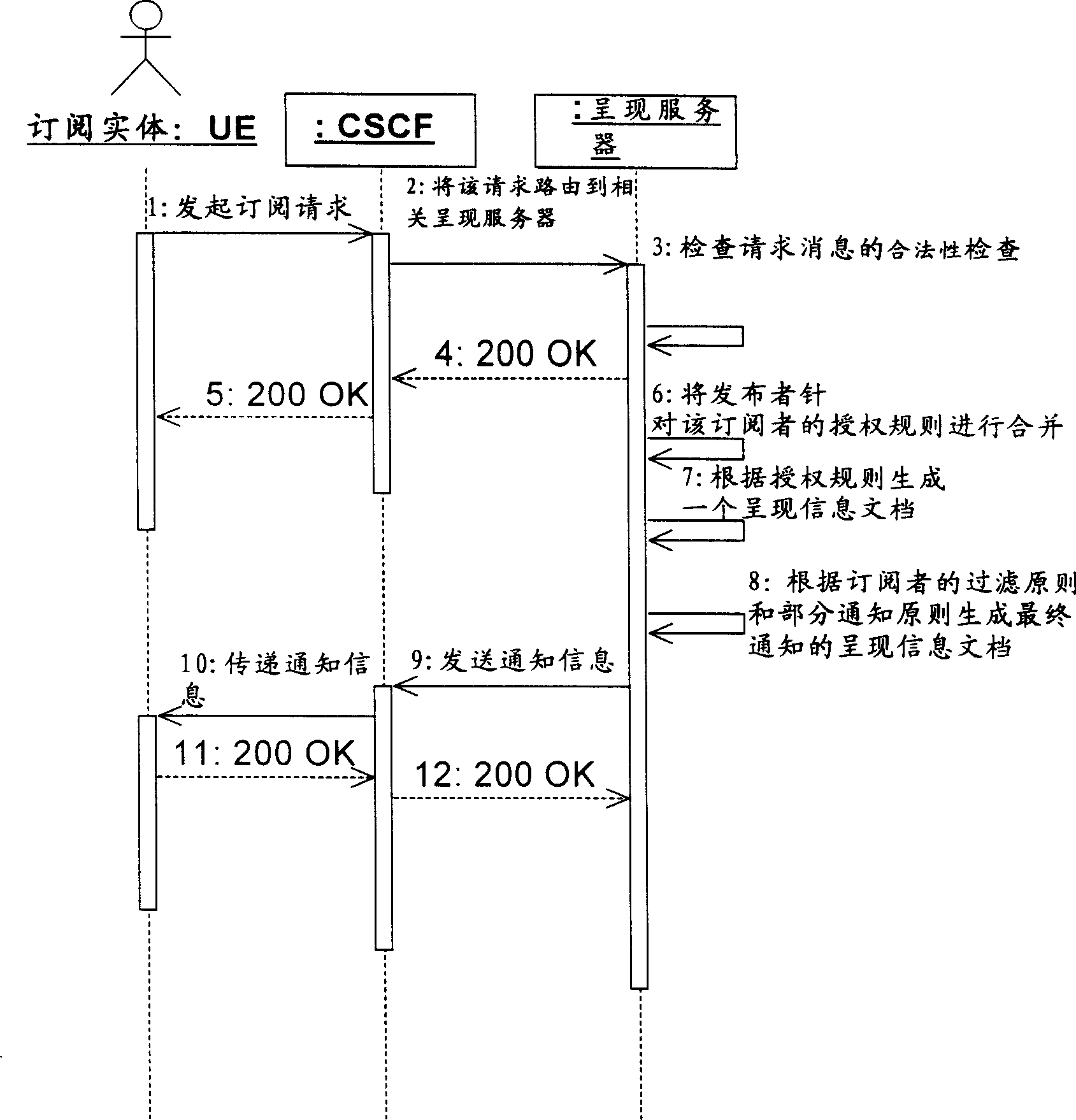
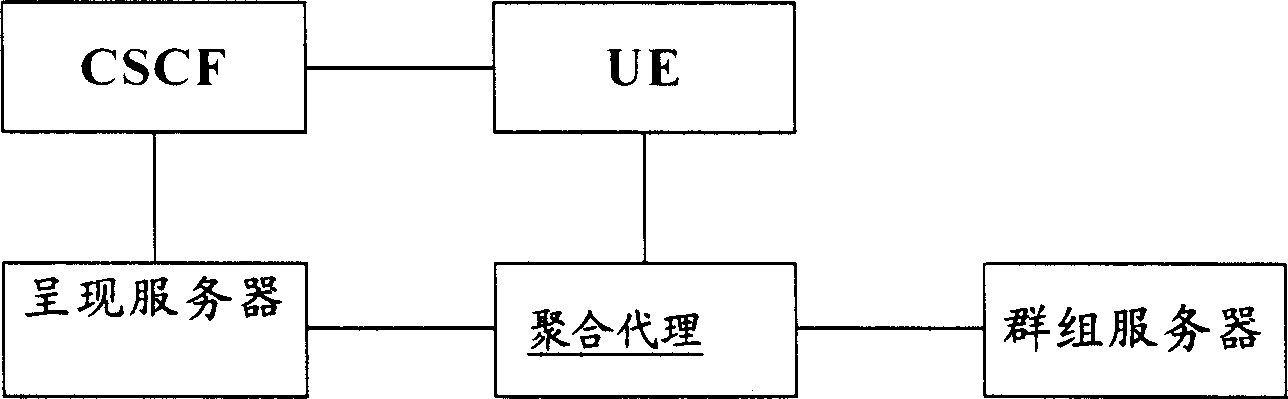
[0026] image 3 It is a network diagram of a system for implementing public group authorization and processing public group member subscriptions according to the present invention. Such as image 3 As shown, the user terminal equipment subscribes presence information to the presence server through core network equipment CSCF (call / session control function entity) (including P-CSCF, I-CSCF, S-CSCF, etc.). The user terminal device manages its own authorization policy through the aggregation proxy AP, which exists in the presence server; the user terminal device manages group information through the AP, and the group information exists in the group server; the presence server obtains group member information through the AP.
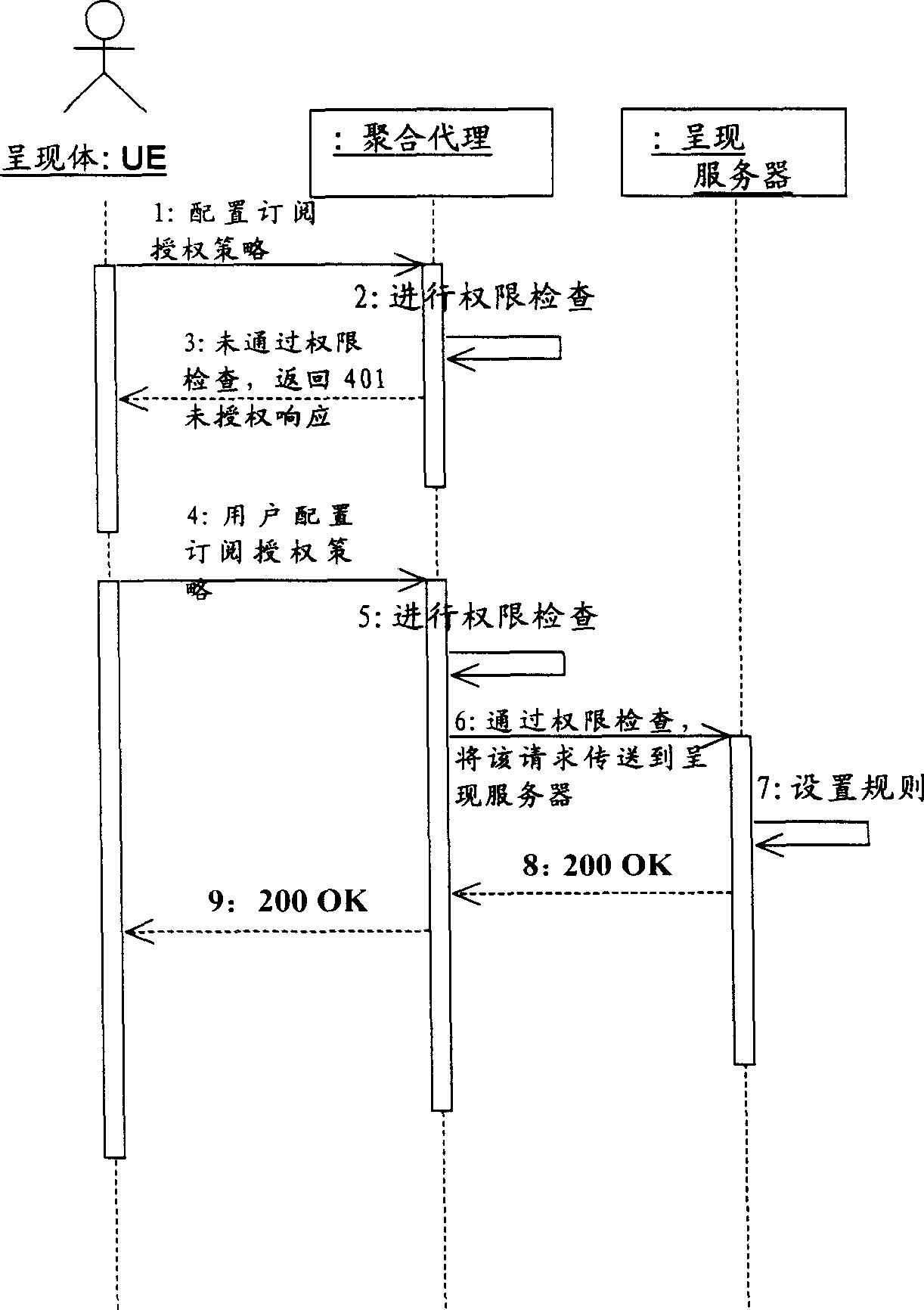
[0027] 1. Presentity configuration authorization rules
[0028] The technical solution of the present invention mainly relies on the existing mechanism for configuring authorization rules to realize the configuration of authorization rules for all members ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com