Message processing method based on distributed network
A distributed network and message processing technology, applied in the field of message processing in distributed networks, can solve the problems of message processing time extension, waste of transmission bandwidth, high network resource overhead, etc., and achieve fast distribution and processing speed, good adaptability, The effect of transmission efficiency and strong environmental adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
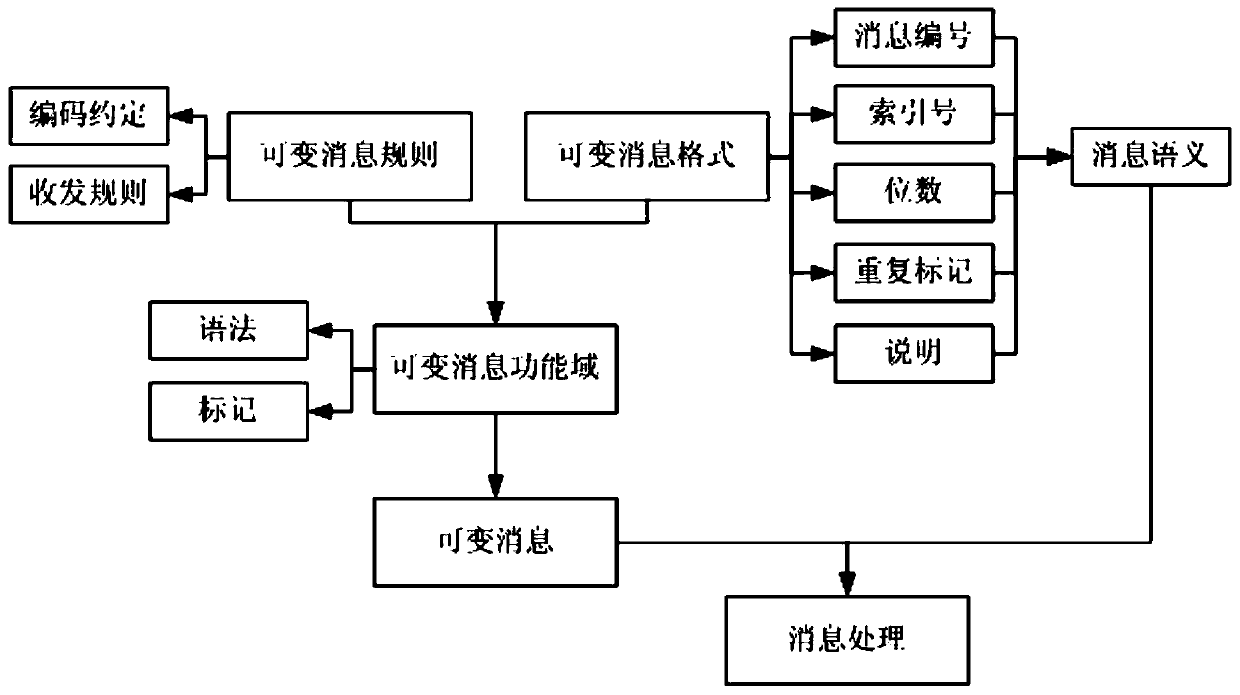
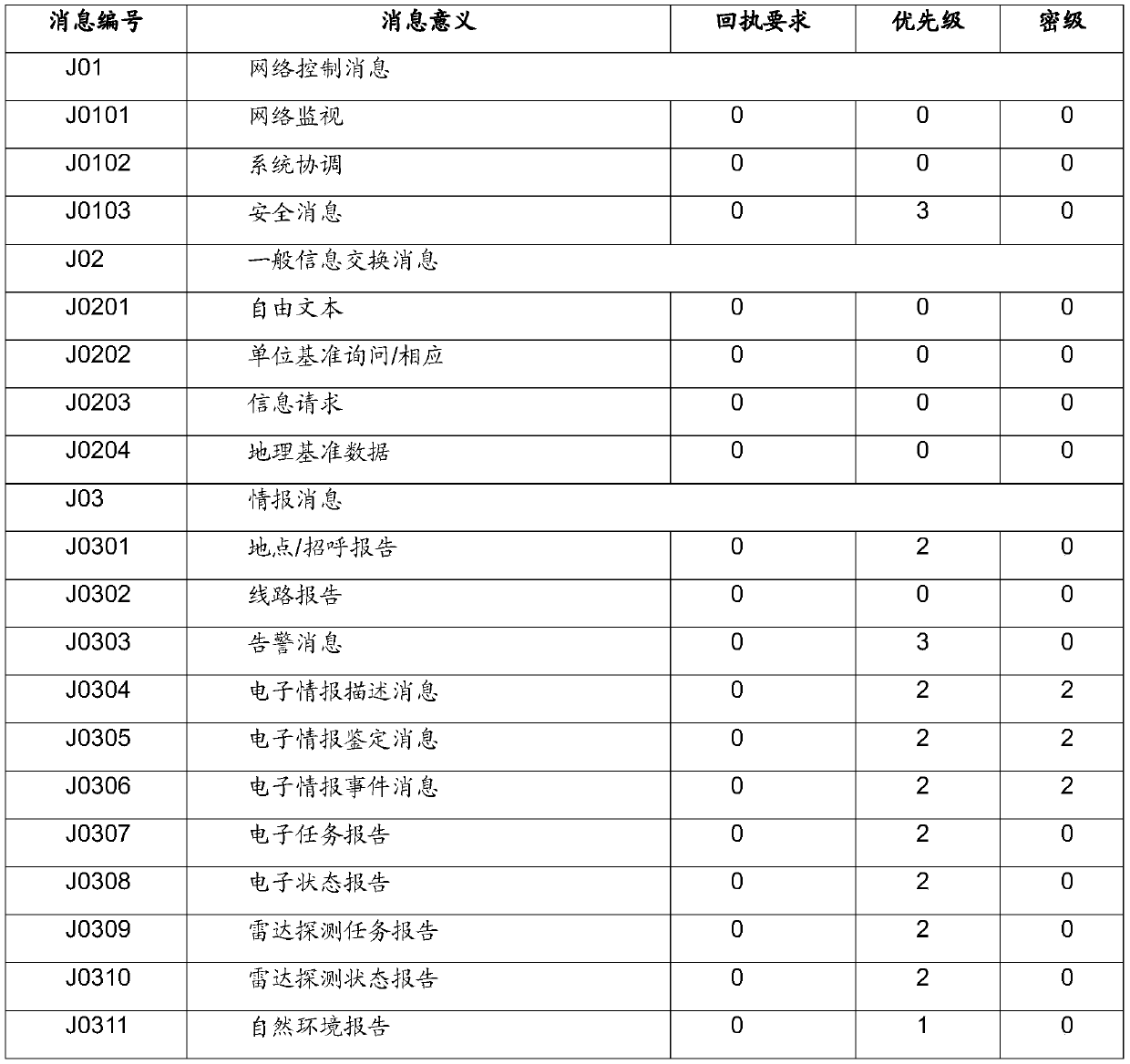
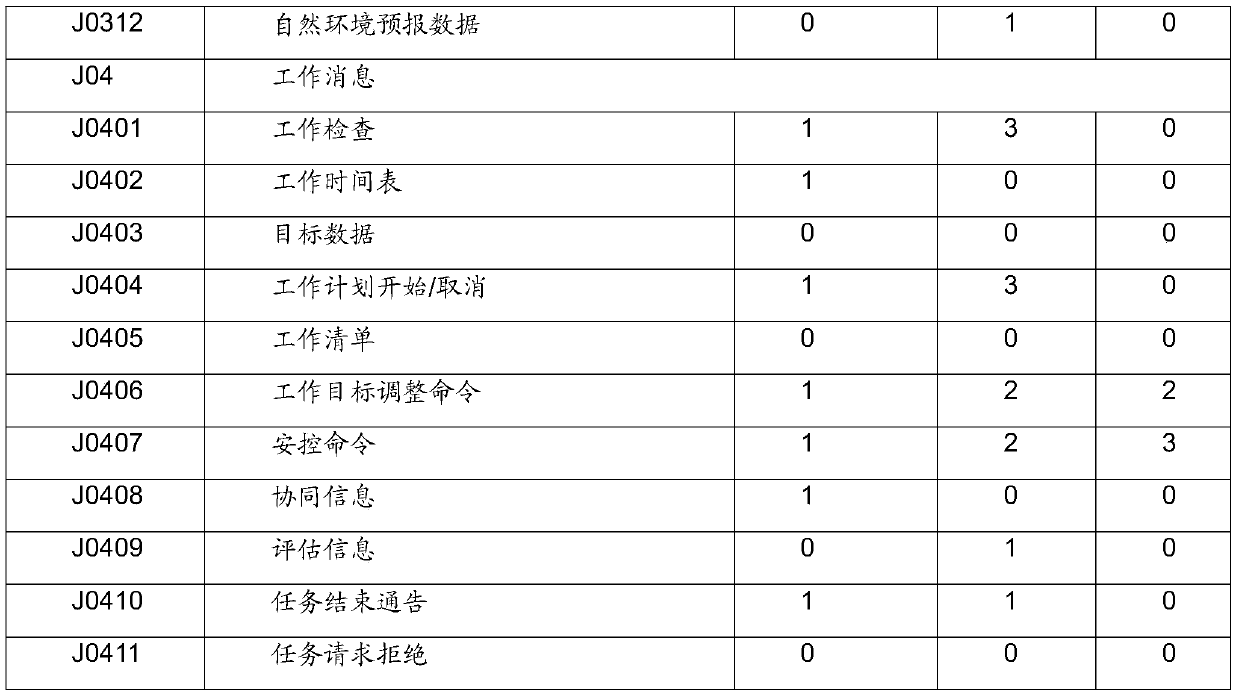
[0057] Table 1 is a definition table of message numbers in the variable message format of the present invention.
[0058] The message number uses a string to indicate the style, function and grouping information of the message, etc.: the first digit of the string indicates the message style, and the options are J / X / D / Q, where J is the drone room and X is the aircraft star , D is the machine address, Q is other message styles; the 2-3, 4-5 digits of the string represent the first-level and second-level indexes of the message function, and n and m are the first-level and second-level index characters of the message function respectively. From 00 to 99; the sixth digit is the message group number, s represents a different group, defined by variable message rules. Message semantics describes the message with keywords, representing the function, type, content, etc. of the entire message. As shown in Table 1, the first-level index character 01 is network control, the second-level c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com