A trusted startup method, device, electronic equipment and readable storage medium
A credible and block-storage technology, applied in secure communication devices, program control devices, computer security devices, etc., can solve problems such as not satisfying the reliability of equipment security, and achieve the effect of starting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
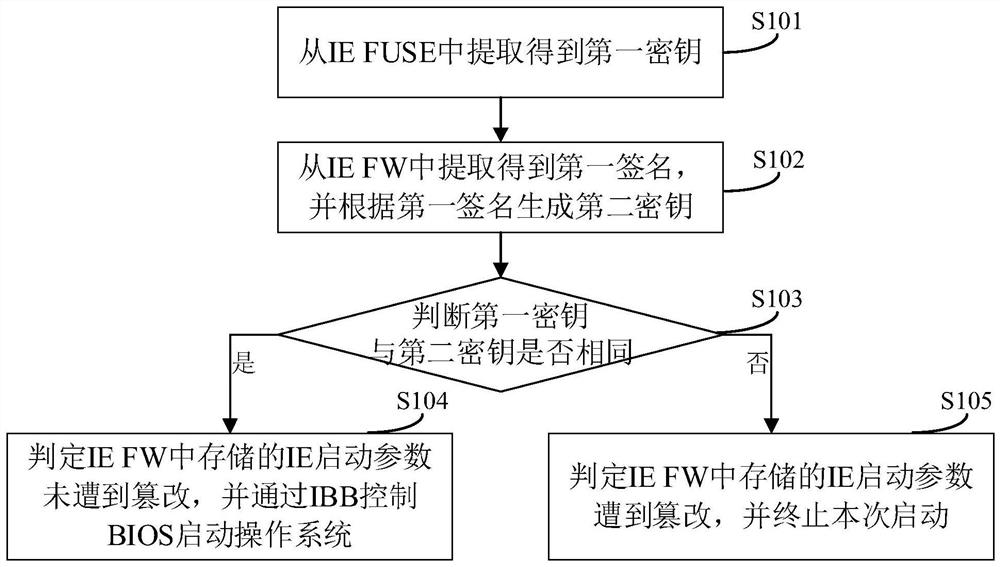
[0084] See figure 1 , figure 1 A flow chart of a trusted startup method provided in an embodiment of the present application includes the following steps:
[0085] S101: Extract the first key from IE FUSE;
[0086] Among them, IE FUSE only supports one-time data writing, the first key is generated based on the IE startup parameters stored in the original IE FW, IE FW supports multiple data writing, IE FUSE and IE FW are different on the same Flash. Data storage block.
[0087] Since the IE FUSE only supports one-time data writing, the first key cannot be changed after being written into the IE FUSE. This application uses this specific second key in the IE FW that actually stores the IE startup parameters. Consistency comparison is performed to determine whether the data stored in the IE FW has been tampered with.
[0088] S102: extract a first signature from the IE FW, and generate a second key according to the first signature;
[0089] The second key is generated based o...
Embodiment 2
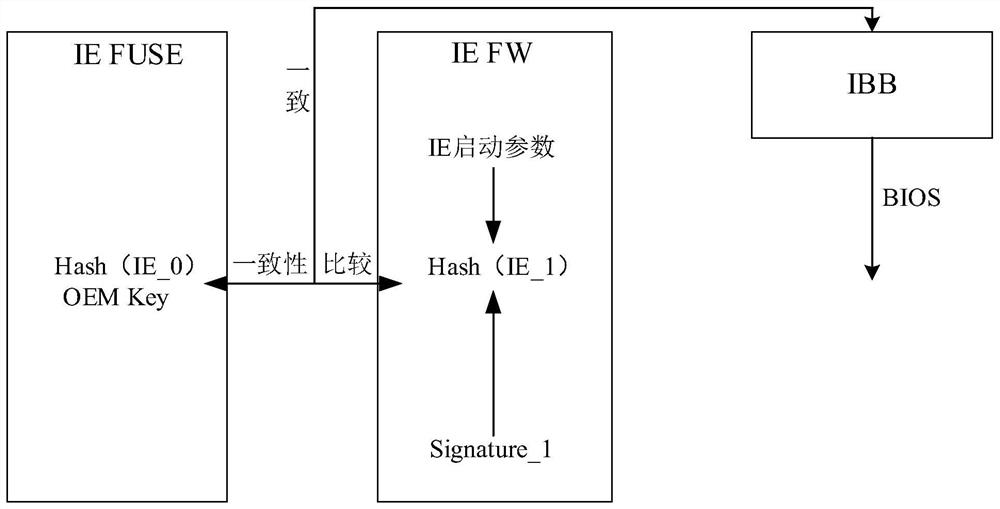
[0101] The above-mentioned embodiment provides a scheme of how to verify whether the current IE startup parameters are credible. According to the description of the IE application mode of the background technology of the present application, it can be seen that: IE, as a simplified BMC, is integrated with BIOS in a Flash, based on the characteristics of IE, In the complete startup process of the device, IE will start before the BIOS, that is, after the IE starts, it will transfer the control to the BIOS, and the BIOS will control the startup of the operating system. Therefore, although the BIOS boot parameters are not likely to be tampered with under the condition that the IE boot parameters are credible, in order to consider the possibility and precedent, this embodiment also adds a new feature to the BIOS on the basis of the first embodiment. Trusted verification of startup parameters to ensure that the startup is safe and reliable as much as possible.
[0102] See image 3...
Embodiment 3
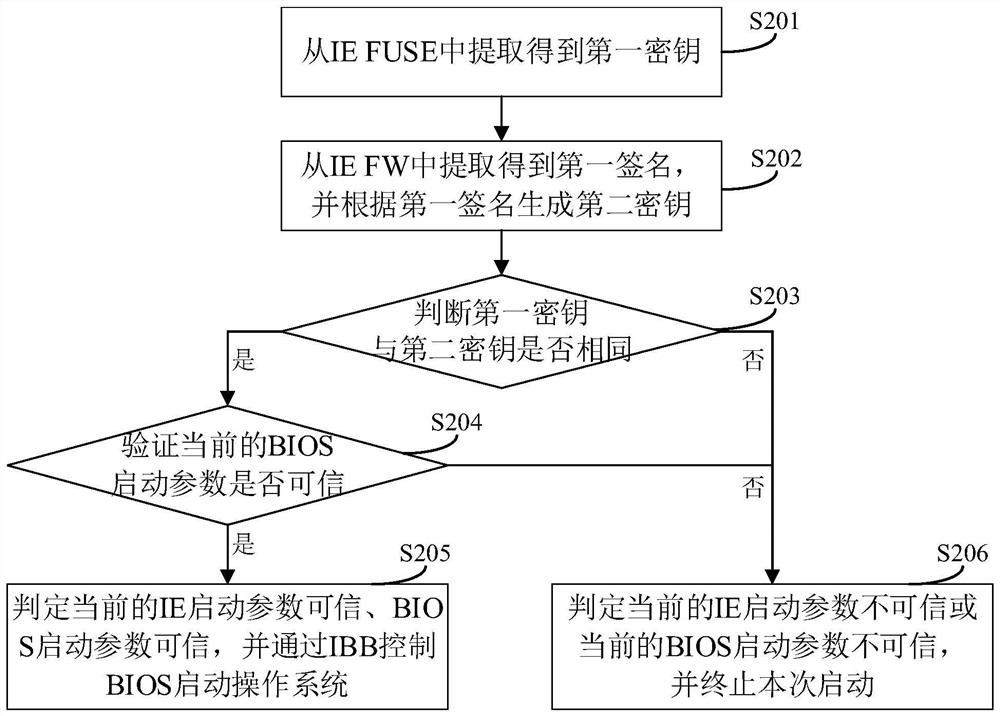
[0112] In this embodiment, the Figure 4 shown in the flow chart and as Figure 5 The flow chart shown in the figure provides two different ways to verify whether the current BIOS boot parameters are credible. They are distinguished by how the BIOS boot parameters are stored in the Flash, which will be introduced separately below:
[0113] See Figure 4 , Figure 4 A flowchart of a method for verifying whether a current BIOS boot parameter is credible in the trusted boot method provided by the embodiment of the present application includes the following steps:
[0114] S301: Extract the third key from IE FUSE;
[0115] The third key is generated based on the BIOS startup parameters stored in the initial BIOS startup parameter storage block, and the BIOS startup parameter storage block supports multiple data writing.
[0116] S302: Extract the second signature from the BIOS boot parameter storage block, and generate a fourth key according to the second signature;
[0117] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com