Trusted computer system and trusted boot method based on secure cryptographic chip
A computer system and cryptographic chip technology, applied in computer security devices, computing, instruments, etc., can solve problems such as being tampered with, not providing a protection mechanism for metric benchmark values, and CRTM residency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
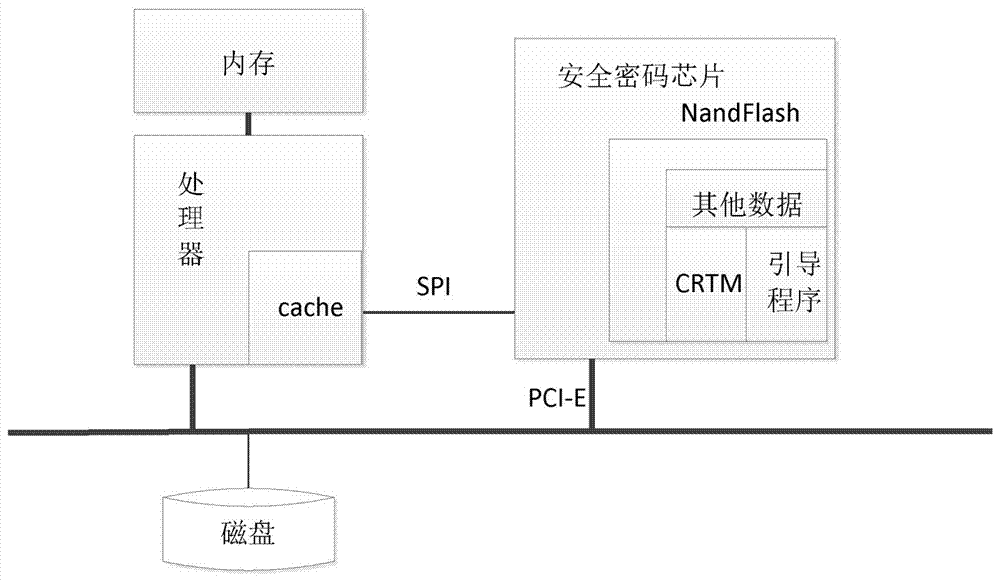
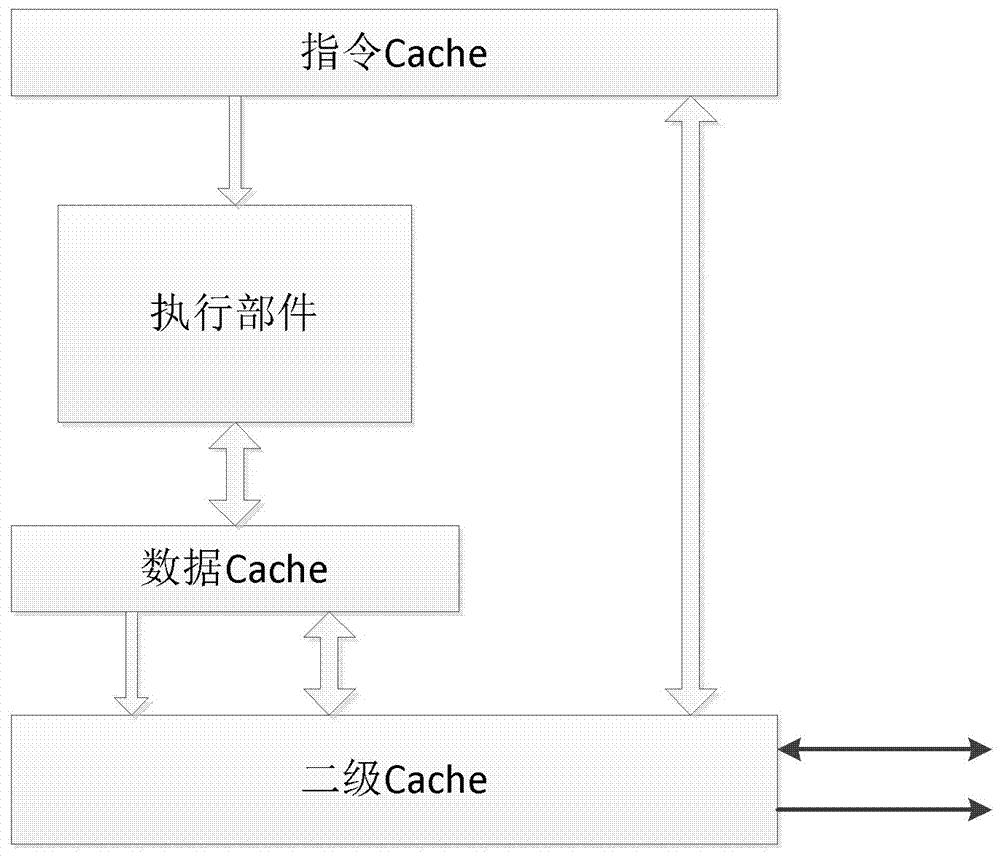
[0043] Embodiment one, see Figure 1~3 As shown, a trusted computer system based on a secure cryptographic chip, its hardware components include a main platform and a secure cryptographic chip, the secure cryptographic chip is responsible for the trusted guidance of the main platform and provides measurement services for the main platform, and the main platform is responsible for daily processing ;The main platform includes the main processor, internal memory, external memory, bus and external devices. The main processor includes an instruction cache unit and a data cache unit. It has an additional passive working state and abides by the startup agreement. The main processor in the passive working state receives Push data from the security cryptographic chip and store it in the instruction cache unit, and receive the wake-up signal from the security cryptographic chip to switch itself to the normal working state. After entering the normal working state, the main processor obeys...
Embodiment 2
[0045] Embodiment 2 is basically the same as Embodiment 1, except that the security cryptographic chip is connected to the main processor through a communication channel. Communication channels include dedicated channel SPI bus and high-speed channel PCI-E bus. The security encryption chip communicates with the main processor through the SPI bus, and pushes the trusted measurement core root CRTM of the main platform to the instruction cache unit of the main processor; the main processor communicates with the security encryption chip through the PCI-E bus to complete the communication between the two. Transmission of large amounts of data, such as bootloader loading, trusted measurement of files, and data encryption and decryption.
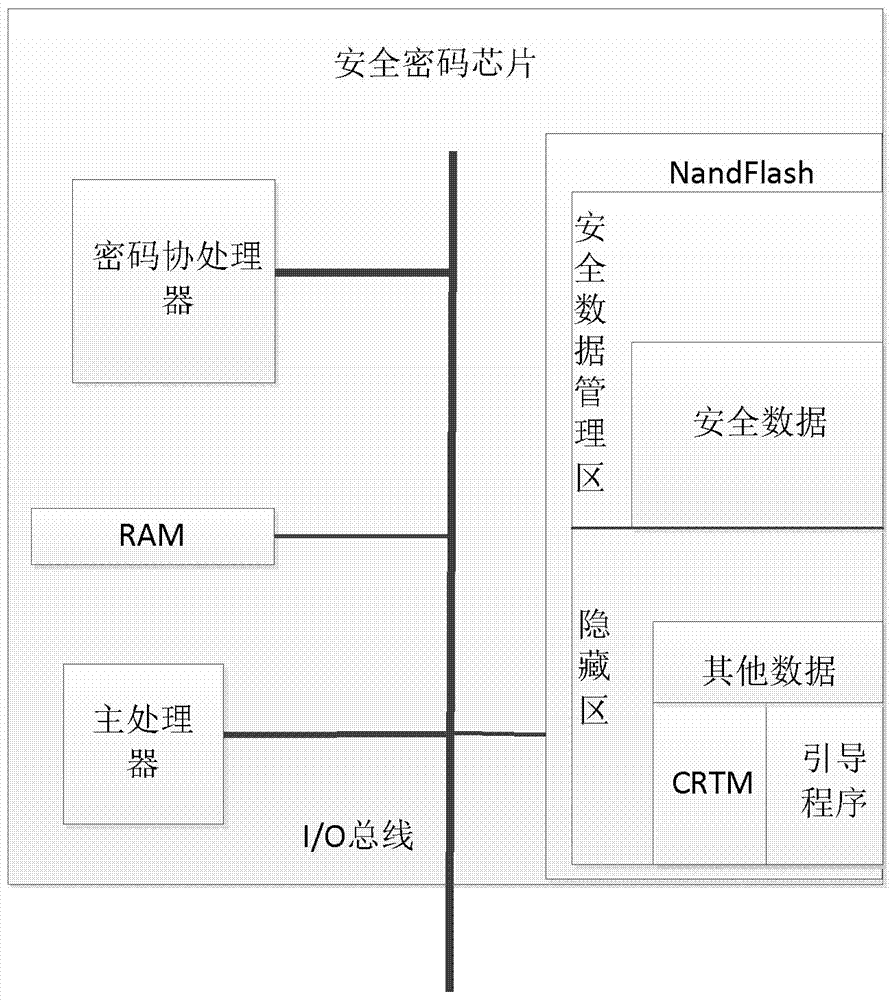
[0046] The security cryptographic chip includes on-chip processor, cryptographic coprocessor, RAM, NandFlash and I / O bus. The on-chip processor is responsible for interacting with the main processor and coordinating the internal work of the secure...
Embodiment 3
[0049] Embodiment three, see Figure 4 As shown, a trusted booting method of a trusted computer system based on a security cryptographic chip specifically includes the following steps:
[0050] Step 1. After the trusted computer system is powered on, the main processor enters a passive working state;
[0051] Step 2. The security cryptographic chip starts to run first, and enters the active working mode; the secure cryptographic chip processor loads the firmware system of the secure cryptographic chip from NandFlash into the built-in RAM of the secure cryptographic chip and executes it, and the security cryptographic chip and the SPI bus Initialize, after the initialization is complete, read the trusted measurement core root CRTM of the main platform from the NandFlash, and push the CRTM to the main processor through the SPI bus;
[0052] Step 3. The main processor receives the pushed CRTM and stores it in the instruction cache unit;
[0053] Step 4. After the security encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com