Anti-theft method and system for mobile phone game account, and server
An anti-theft method and mobile game technology, applied in the field of mobile games, can solve problems such as easy theft of game accounts, long dynamic verification time, etc., and achieve the effect of improving anti-theft and safety, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
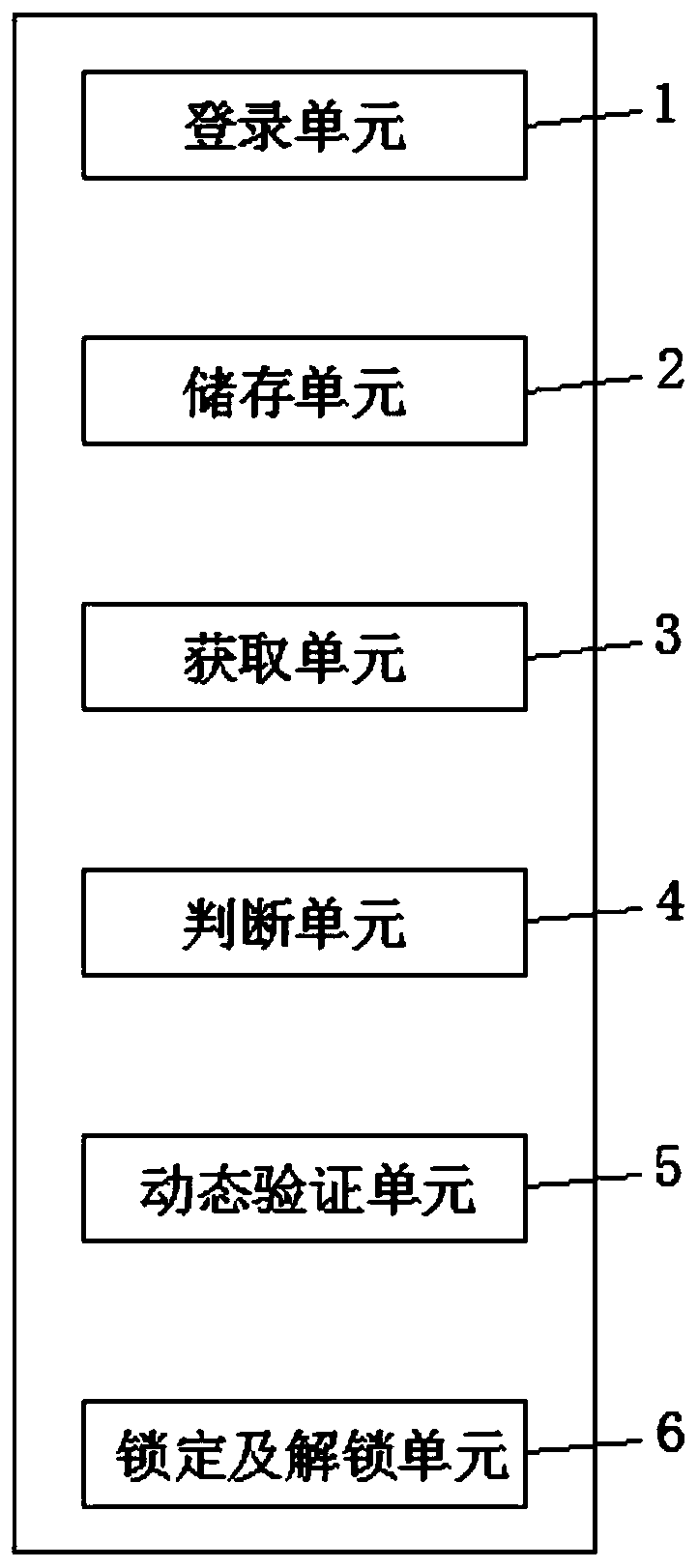
Image
Examples
Embodiment 1
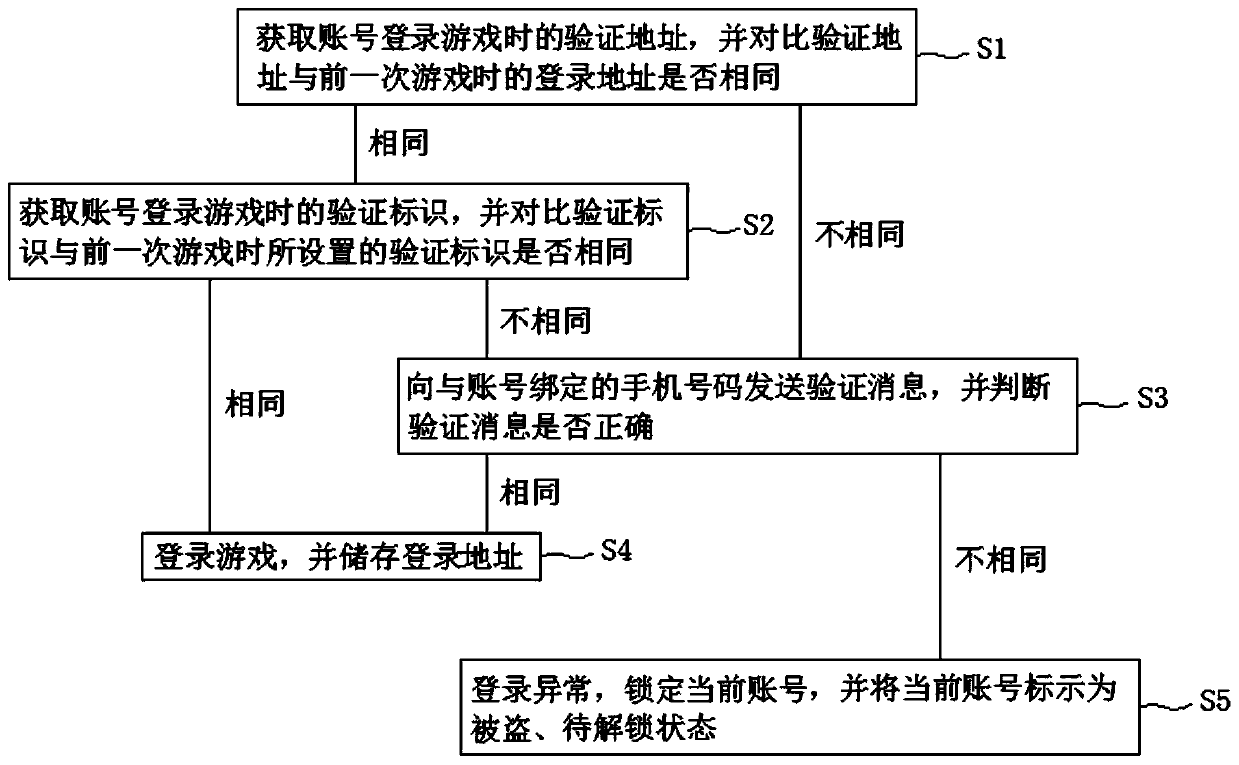
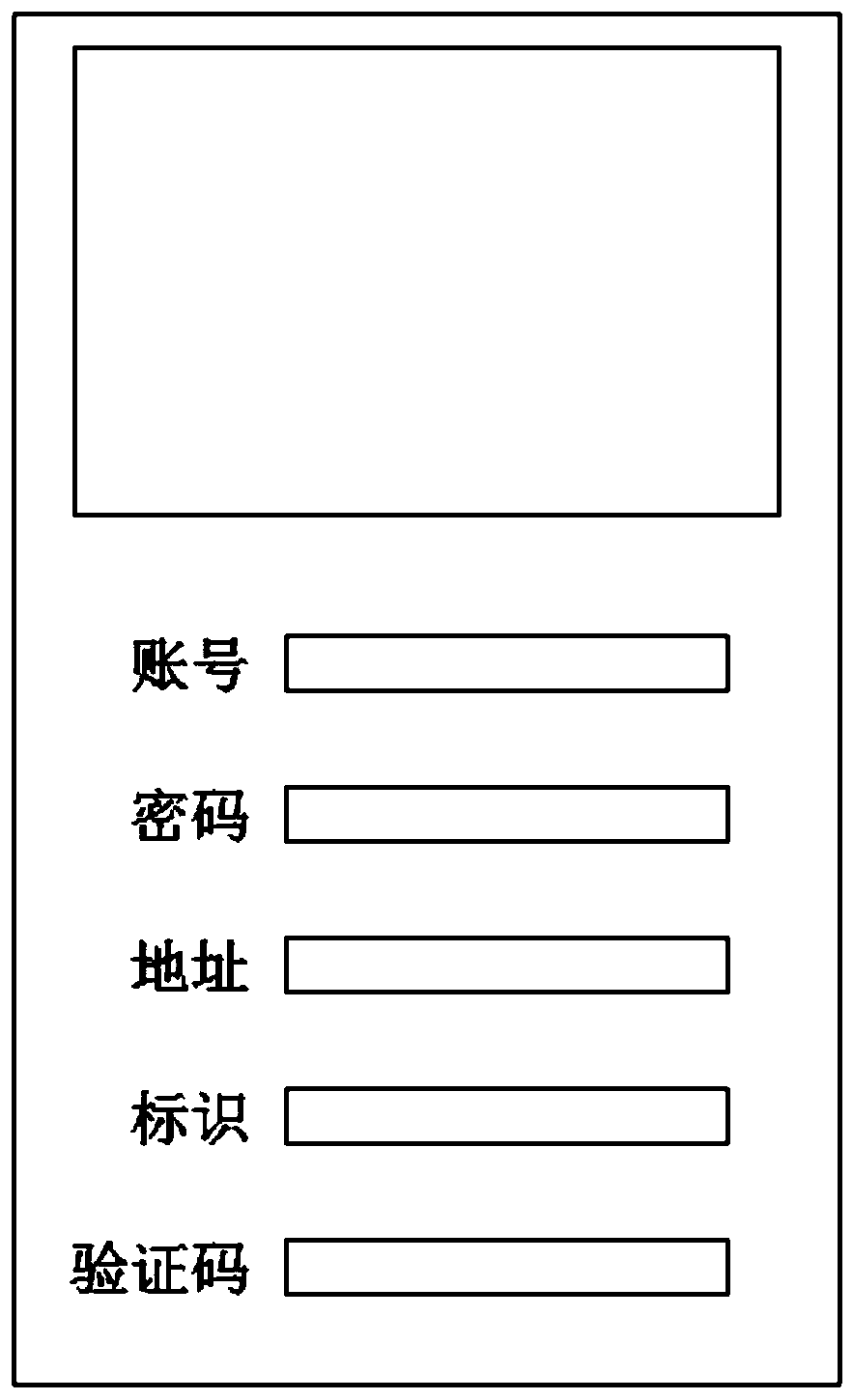
[0042] S1. Log in the game from a mobile terminal (mobile phone), and the login interface is as follows: image 3 As shown, the verification address when the server obtains an account based on wireless communication to log in to the game is a, and the previous login address of the same account stored in the server is also a; the addresses of the two games are the same;
[0043] S2. The verification identification b is input by the mobile terminal, and the server obtains the verification identification b when the account logs in to the game, and the identification b set by the same account in the previous game is stored in the server; the identifications of the two games are the same;
[0044] S3. Log in to the game, and record the login address as a'.
[0045] In addition, about exiting the game after the end of the game: when exiting the game, set the corresponding logo to be used as the login verification for the next game.
[0046] As mentioned above, based on the settings...
Embodiment 2
[0050] S1. The mobile terminal performs game login. The verification address when the server obtains an account based on wireless communication to log in to the game is a, and the previous login address of the same account stored in the server is also a1; the login addresses of the two games are different;
[0051] S2. Send a verification message c to the mobile phone number bound to the account, the mobile terminal inputs the verification message c, and the server determines that the input verification message is correct; specifically, the verification message here may preferably be a verification code;
[0052] S3. The verification identification b is input by the mobile terminal, and the server obtains the verification identification b when the account logs in to the game, and the identification b set by the same account in the previous game is stored in the server; the identifications of the two games are the same;
[0053] S4. Log in to the game, and record the login addre...
Embodiment 3
[0055] S1. The mobile terminal performs game login. The verification address when the server obtains an account based on wireless communication to log in to the game is a, and the previous login address of the same account stored in the server is also a1; the login addresses of the two games are different;
[0056]S2. Send a verification message f to the mobile phone number bound to the account, the mobile terminal inputs the verification message f1, and the server determines that the input verification message is incorrect;
[0057] S3. The login is abnormal, the current account is locked, and the current account is marked as stolen and to be unlocked.
[0058] In this embodiment, when the game account is locked, the operation of unlocking through real-name authentication is also included:
[0059] S4. The mobile terminal sends an unlock request to the server, and attaches the ID number for real-name authentication; for example, "iiiiii+unlock+ID number", where "iiiiii" refer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com