Methods, systems, and media for detecting two-dimensional videos placed on sphere in abusive spherical video content
A video content, spherical technology, applied in the direction of program/content distribution protection, graphic image conversion, character and pattern recognition, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
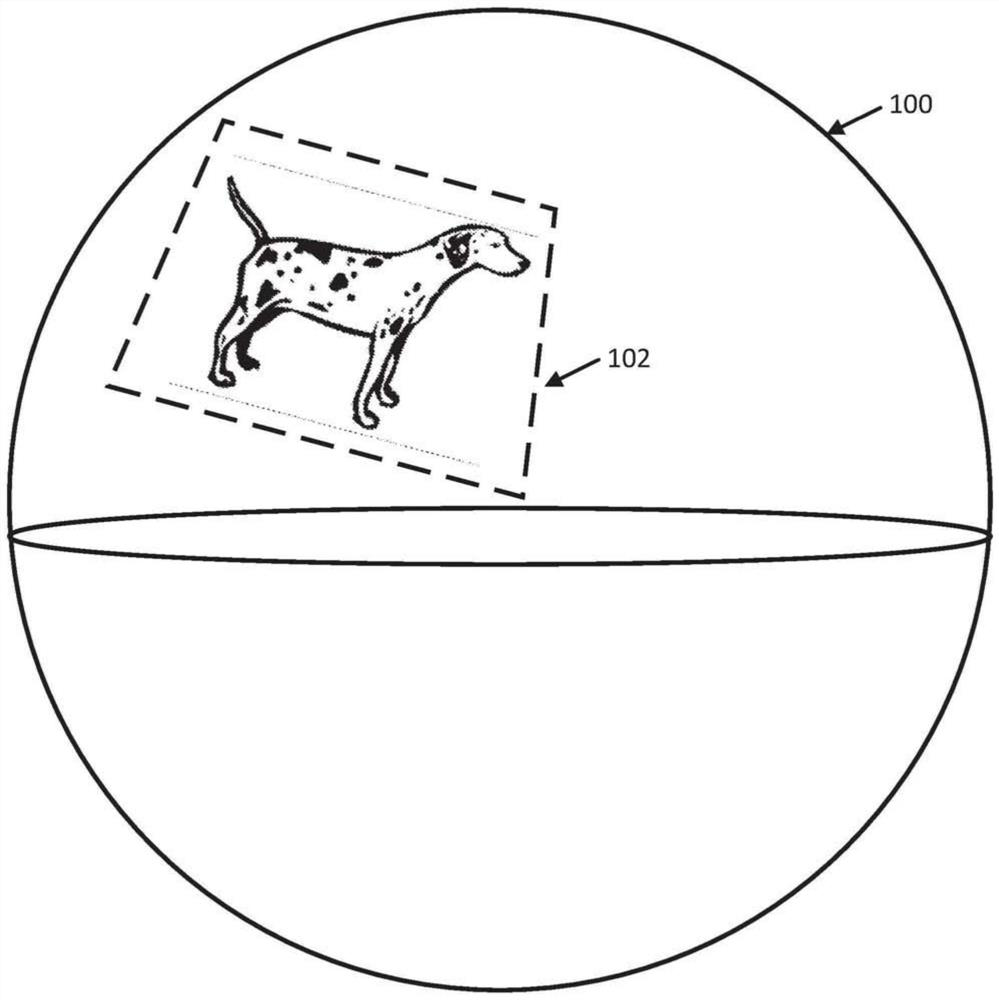
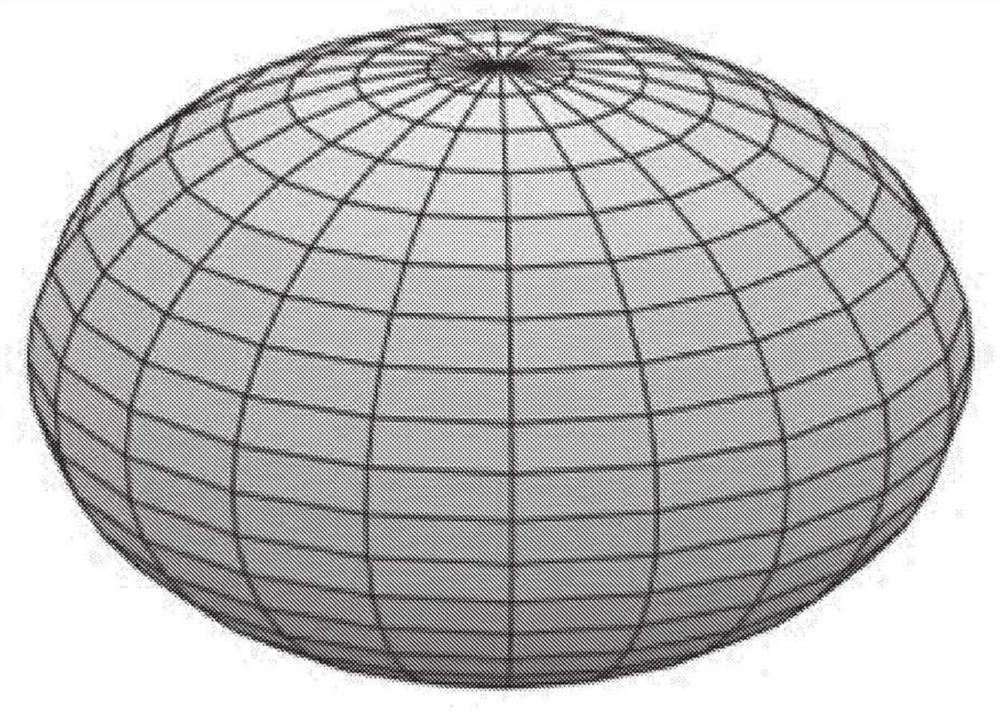
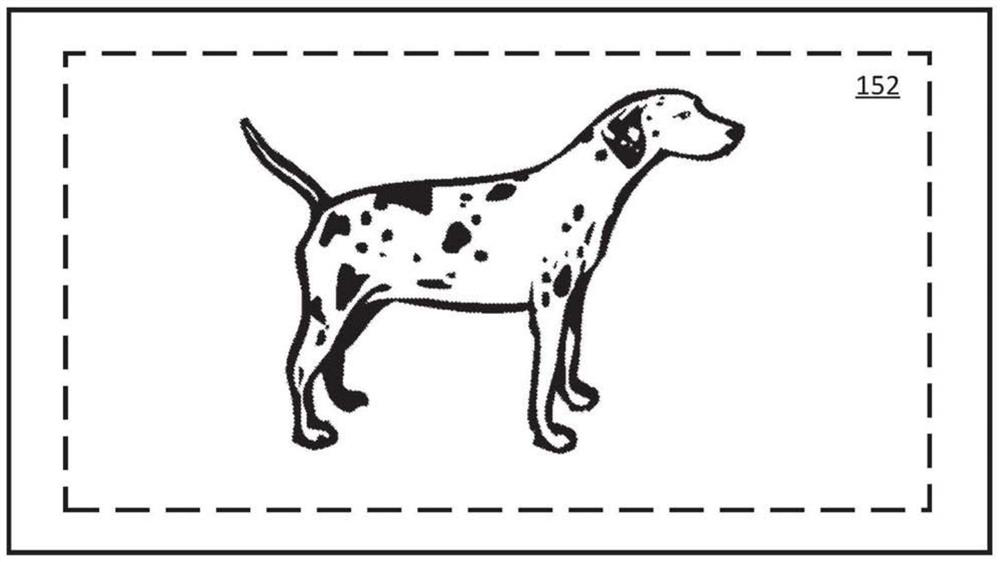
[0041] According to various embodiments, mechanisms (which may include methods, systems, and media) for detecting misuse of two-dimensional video placed on a sphere in spherical video content by tiling the sphere are provided.
[0042] In some embodiments, the mechanisms described herein may be used to detect certain types of video content superimposed on and / or stitched together with spherical video content. For example, in some embodiments, the mechanism may be used to detect potentially copyrighted video content or potentially copyrighted audio content that has been superimposed on or inserted into spherical video content. It should be noted that various fingerprinting techniques have been used to identify copyrighted content, for example by matching a portion of a content item with a reference content item in a database of reference content items. However, these fingerprinting techniques sometimes fail to identify copyrighted video content that has been inserted into spher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com