Combined signature and verification signature method, system and storage medium
A technology for verifying signatures and signatures, applied in the field of blockchain, it can solve the problems of not involving assets custody to third-party institutions, low feasibility of private key shares, attacks, etc., to avoid security problems and credit risks, and to improve the feasibility of the scheme. sex, risk reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0080] The present invention will be described in detail below in conjunction with specific embodiments. The following examples will contribute to the skill in the art
[0085] The grouping method and the signature conditions set by each group are designed according to specific business scenarios, and there may be many forms.
[0090] The step 2 is characterized in that the shared public key combination includes at least two public key elements;
[0091] It is also characterized in that the public key element can be a single sub-public key or a sub-public key list;
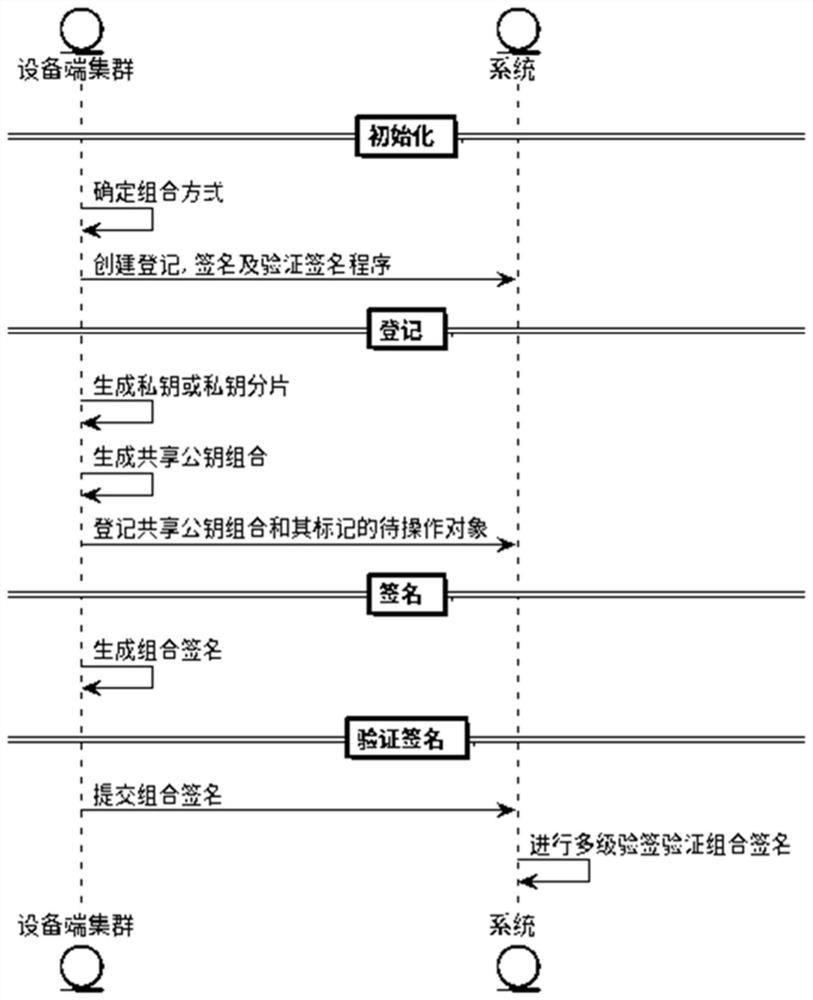
[0098] The device-side cluster may correspond to roles such as users or user groups, business parties, and supervisors.
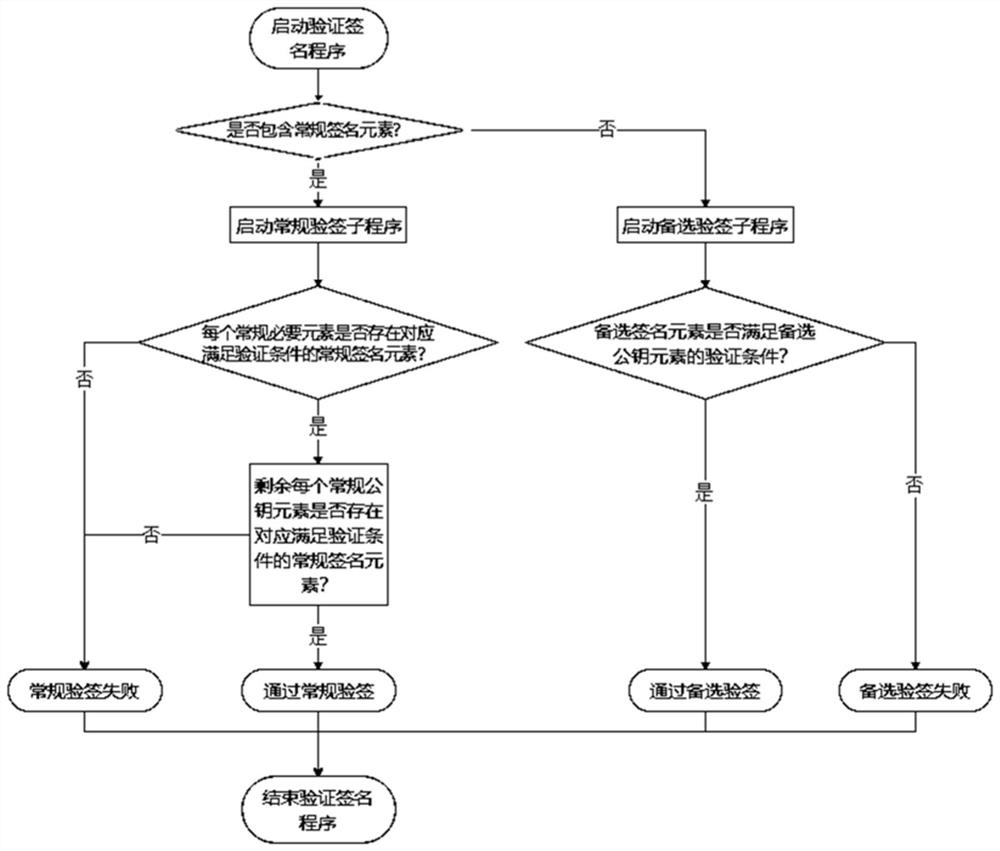
[0100] The routine signature verification subroutine judges whether each routine necessary public key element exists in the shared public key combination
[0102] Preferably, the system can set a device access mechanism, such as a consortium chain system, which consists of a plurality of independen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com