A dual-network security synchronization system and method based on ssh
A synchronization system and secure technology, applied in the field of data transmission, to achieve the effect of reducing load dependence, safe and efficient file synchronization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
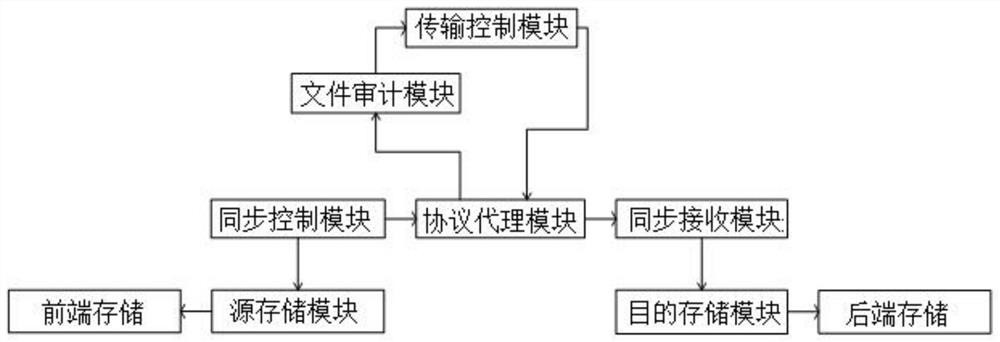
[0032] A dual-network security synchronization system based on SSH, such as figure 1 As shown, the following modules are included:
[0033] Source storage module: access to front-end storage, provide source storage type and storage directory range selection.
[0034] Synchronization control module: responsible for establishing a connection to the protocol proxy module through the SSH protocol, and checking the file changes of the synchronization source storage module through file increments.
[0035] Protocol agent module: responsible for establishing and maintaining the SSH two-way connection channel, and realizing the control and forwarding of the synchronously executed protocol content.
[0036] File audit module: analyze and restore the content synchronized in the protocol, load file attribute detection, sensitive content detection, anti-virus detection and other audit identification.
[0037] Transmission control module: Control the abnormal files detected by the file a...
Embodiment 2
[0041] An SSH-based double-network security synchronization method is carried out in the above-mentioned system, such as Figure 4 As shown, including the data synchronization phase:
[0042] 1. According to the data synchronization task, the synchronization control module uses the SSH exec channel to send the remote file copy command, opens a new data transmission channel and sends the traffic data including the file content to the protocol agent module.
[0043] 2. The protocol proxy module quickly detects the traffic data of the received file content by stream mode hash matching, and performs a shared cache. If the data that has been successfully matched in the hash table uses the SSH exec channel to open a new data transmission channel, it will The data is forwarded to the synchronous receiving module.
[0044] 3. If it is unmatched data in the hash table, send the file information that cannot be judged to the file audit module, and wait for the processing result.
[004...
Embodiment 3
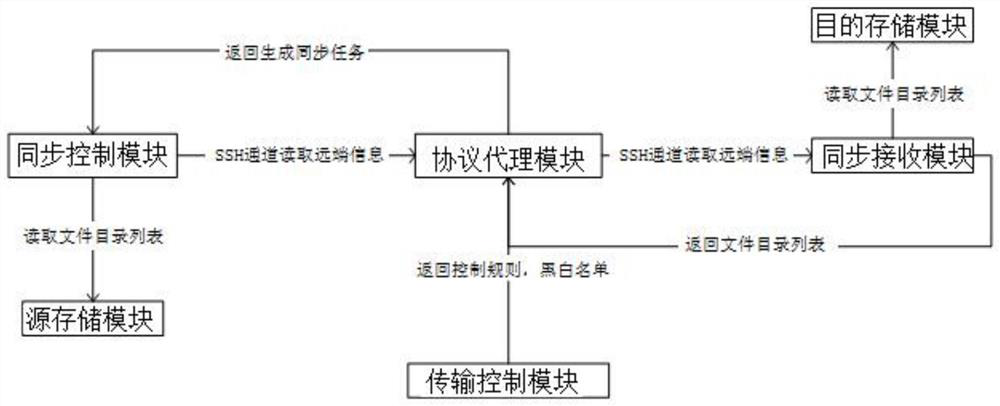
[0053] This embodiment is optimized on the basis of embodiment 1 or 2, as figure 2 As shown, the initialization phase is also included:
[0054] 1. Add and set front-end storage such as local file systems, remote file systems, and distributed storage object storage systems that need to be synchronized through the source storage module in the external network. The source storage module obtains files based on common file system formats for front-end storage and target list. The source storage module deploys multiple front-end storages connected to different locations at the same time to unify network access differences and realize unified adaptation of different heterogeneous environments.
[0055] 2. Set the connection address of the protocol agent module in the external network through the synchronization control module, authenticate and establish a connection with the protocol agent module through the SSH protocol.
[0056] 3. Add and set the target storage module in the i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com