Simulated account login method and device, equipment and storage medium
A technology for simulating login and account, applied in computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0184] Example 1: Applied to the first application scenario above
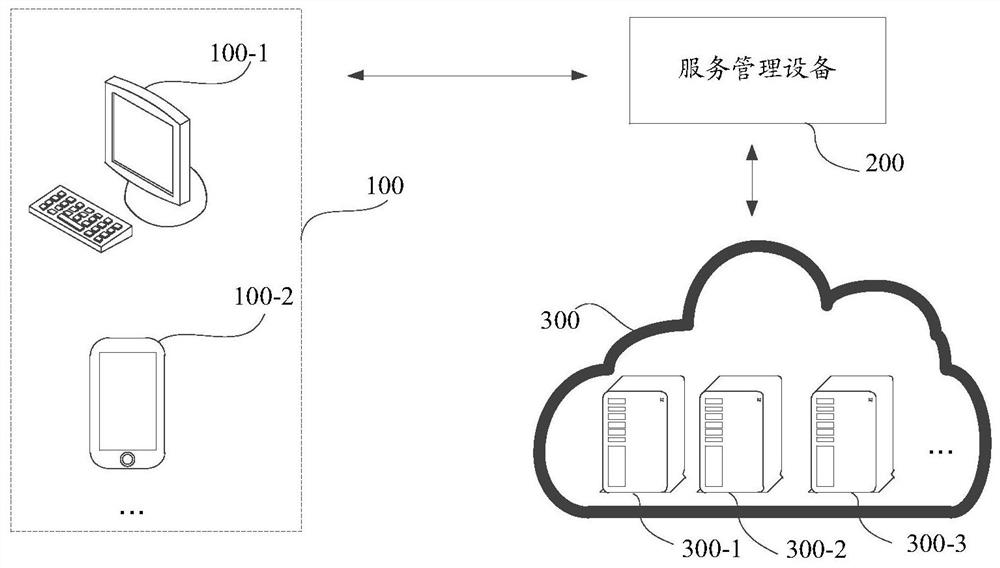
[0185] See Figure 9 , in this example, user B of the second account and user A of the first account can chat by telephone or online, and user B can obtain the account query information of the first account, and then user B can obtain the account query information of the second account through the identity information of the second account After logging in to the first website, query the target jump object of the first account based on the account query information of the first account, and trigger the login jump instruction by clicking the target jump object of the first account.
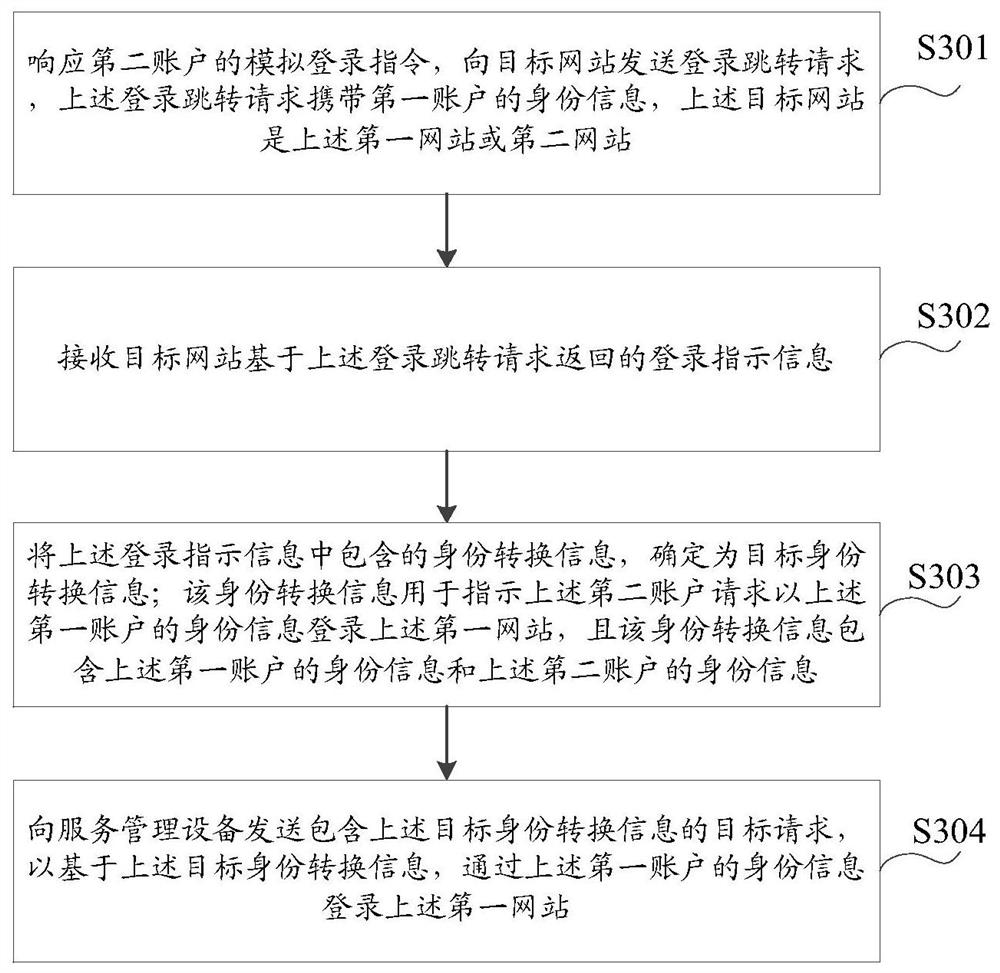
[0186] The process of obtaining target identity conversion information includes: after the browser on the terminal 100 detects the login redirection instruction, it sends a login redirection request to the API gateway; the API gateway forwards the login redirection request sent by the browser to the first server 300; The fi...
example 2
[0217] Example 2: Applied to the second application scenario above
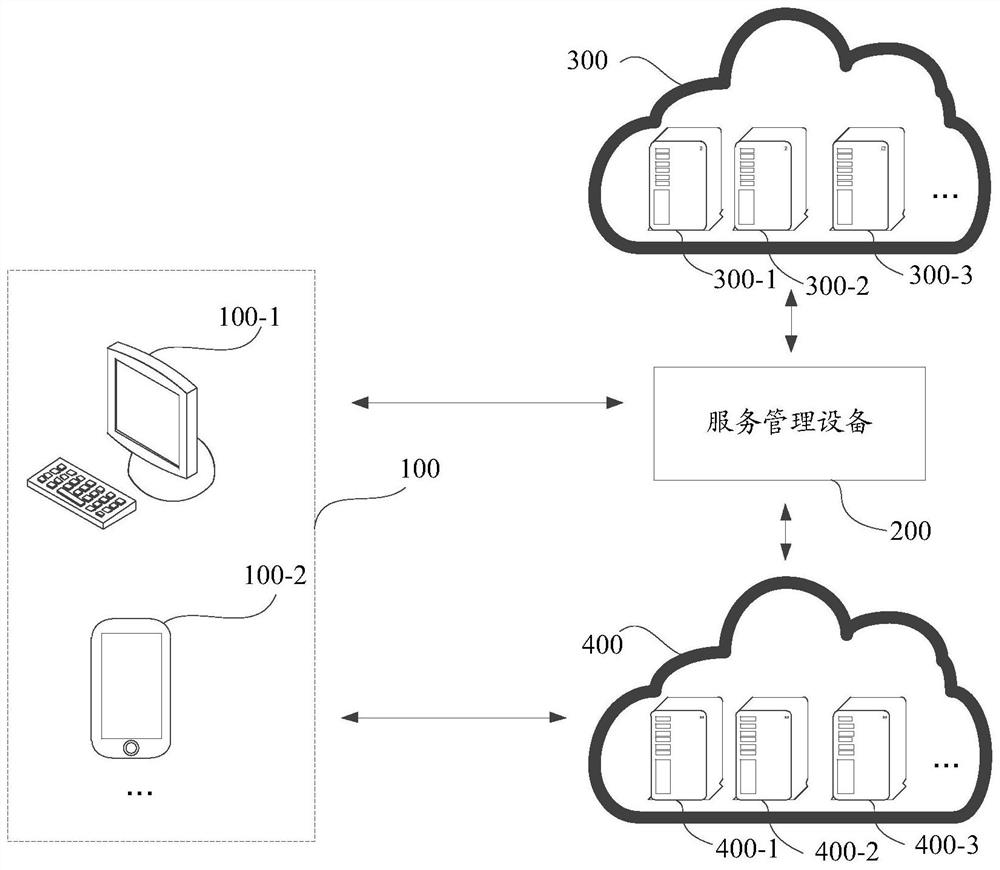
[0218] See Figure 12 , in this example, user B of the second account and user A of the first account can chat by telephone or online, and user B can obtain the account query information of the first account, and then user B can obtain the account query information of the second account through the identity information of the second account After logging in to the second website, query the target jump object of the first account based on the account query information of the first account, and trigger the login jump instruction by clicking the target jump object of the first account.
[0219] The process of obtaining target identity conversion information includes: after the browser on the terminal 100 detects a login redirection indication, it sends a login redirection request to the second server 400; and send the login instruction information including the identity conversion information to the brow...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap