Offline authorization method for distributed software product
A software product, distributed technology, applied in the direction of program/content distribution protection, instruments, electrical digital data processing, etc., can solve problems such as inability to achieve, and achieve the effect of preventing tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
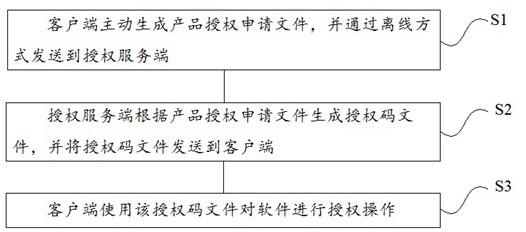
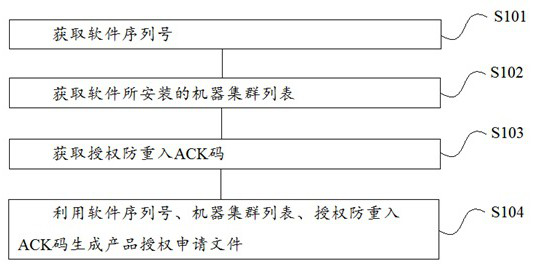
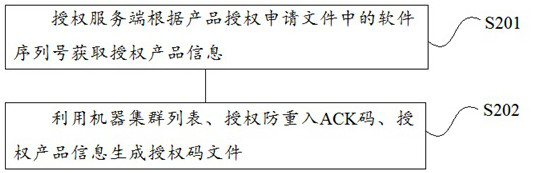
Examples
Embodiment 2
[0083] Embodiment 2 adds the verification steps of the authorization result on the basis of Embodiment 1, such as Figure 5 As shown, the inspection steps include:
[0084] S601: Obtain an authorization code file corresponding to the product;
[0085] S602: Obtain the software serial number;
[0086] S603: Verify the authorization result by using the authorization code file and the software serial number.
[0087] Such as Figure 6 As shown, the verification of the authorization result by using the authorization code file and the software serial number includes:
[0088] S6031: Judging whether the authorized product information in the authorization code file is the same as the authorized product information of the current software running, if the authorized product information is different, the authorization result check is failed;
[0089] S6032: If the authorized product information is the same, determine whether the machine cluster list in the authorization code file ov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com