Image anti-counterfeiting method and device, terminal and computer readable medium
A computer program and image technology, applied in the field of computer-readable media, can solve problems such as identification and misappropriation of bad merchants, loss of authentic merchants, etc., to achieve the effects of enriching product information content, ensuring authenticity, and increasing the difficulty of counterfeiting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
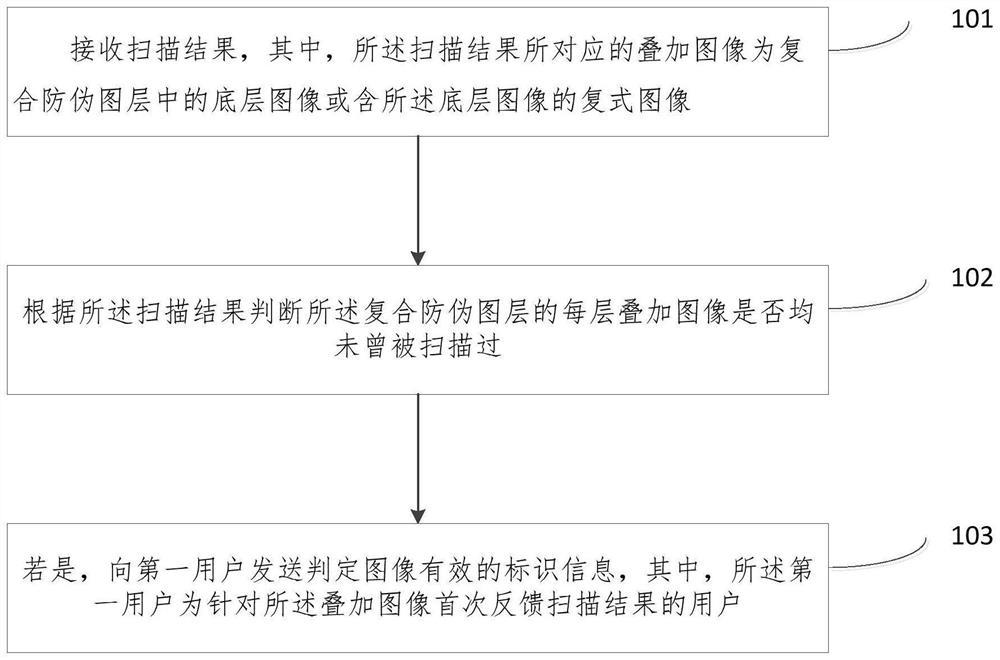
[0045] In Example 1, including the above figure 1 All the steps of the method shown, wherein step 101 is realized by the following processing methods:
[0046] The scanning result is received, wherein the superimposed image corresponding to the scanning result is an underlying image in the composite anti-counterfeiting layer or a composite image containing the underlying image. The composite anti-counterfeiting layer in this application document is a single-layer or multi-layer image, wherein, when the composite anti-counterfeiting layer is a single layer, the superimposed image is the bottom layer image, which is a single-layer image; when the composite anti-counterfeiting layer is multi-layer , the superimposed image is a composite image containing the bottom image, and the composite image is at least two layers of images containing the bottom image, wherein, for the composite anti-counterfeiting layer of N layers, there is one bottom image and (N-1) composite images. For e...
Embodiment 2
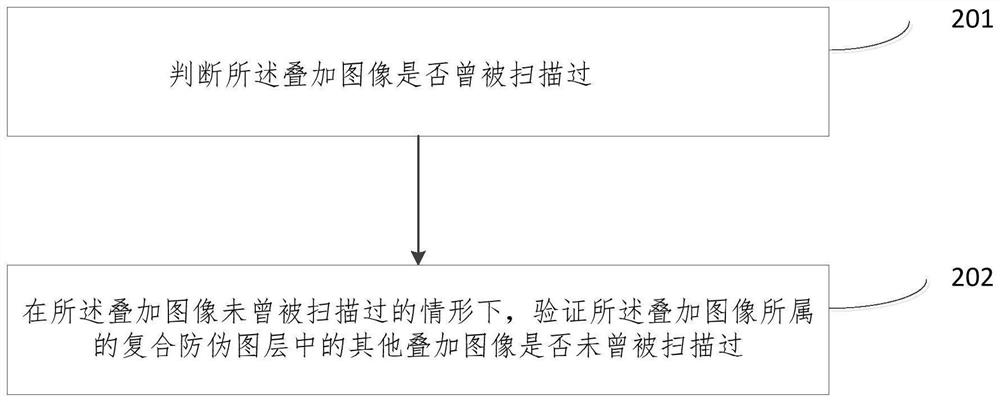
[0048] In Example 2, including the above figure 1 All the steps of the method shown, wherein, for step 102: judging according to the scanning result whether each layer of superimposed images of the composite anti-counterfeiting layer has never been scanned, through the following processing methods, such as figure 2 Shown:
[0049] Step 201: judging whether the superimposed image has been scanned;
[0050] Step 202: In the case that the superimposed image has never been scanned, verify whether other superimposed images in the composite anti-counterfeiting layer to which the superimposed image belongs have never been scanned.
[0051]According to the scanning result of the superimposed image, it is judged whether the superimposed image has been scanned by other users before this scan. Whether other superimposed images of the composite anti-counterfeiting layer have been scanned or not, wherein the determination of whether other superimposed images of the composite anti-counte...
Embodiment 3
[0056] In Example 3, including the above figure 1 All the steps of the method shown, wherein, in the case where the composite anti-counterfeiting layer has at least two layers, the identification information is sent to the first user and / or the second user respectively, so that the first user The user and / or the second user determine that the image is valid under the condition that at least two of the identification information are consistent, through the following processing methods:
[0057] In the case where the composite anti-counterfeiting layer has at least two layers, the identification information is sent to the first user and / or the second user respectively according to the number of scanning layers of the user, wherein the identification information corresponding to the different superimposed images of each layer is consistent, if If the user determines that at least two received identification information are consistent, the product with the superimposed image is de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com