Two-way authentication and key agreement method under multi-server architecture
A key agreement, two-way authentication technology, applied in the field of multi-server architecture, can solve problems such as the difficulty of computing discrete logarithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
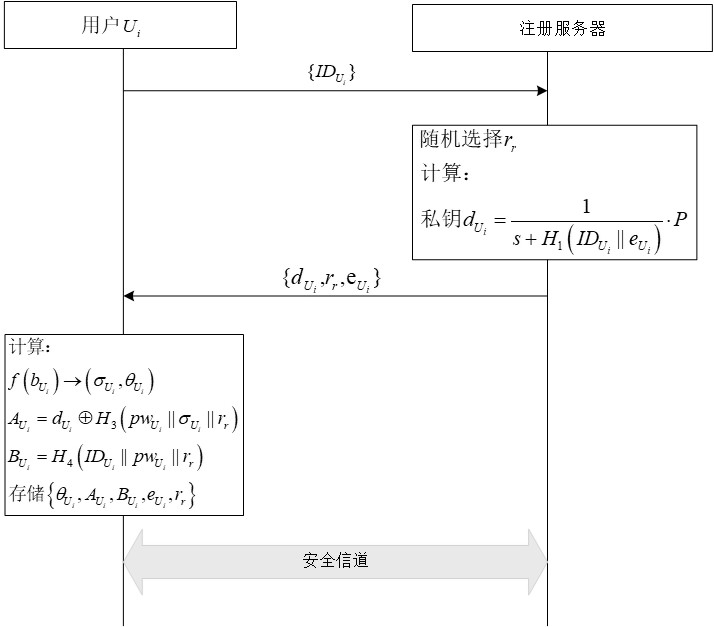
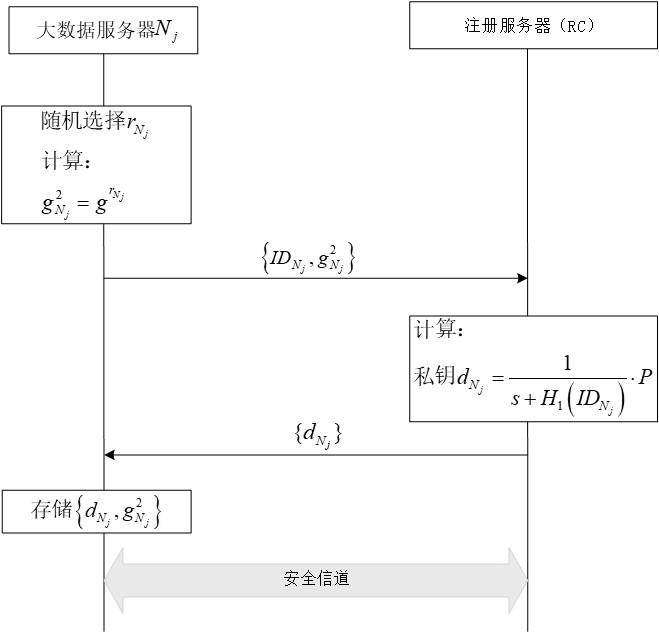
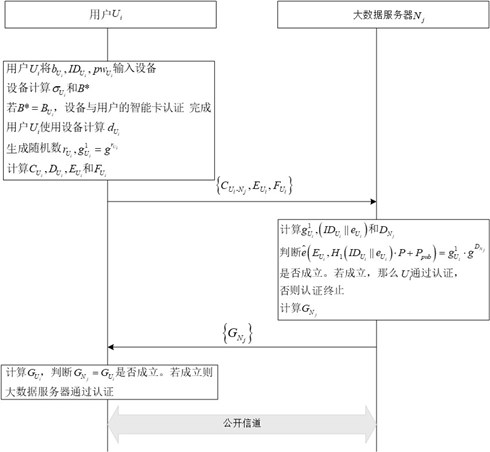
[0038] (1) System initialization
[0039] In the system initialization phase, the registration server generates initialization parameters for the registration phase, mutual authentication and key negotiation phases. The following table shows the symbols in the system and their meanings.
[0040] Table 1 Symbols and their meanings
[0041]
[0042]
[0043] The registration server runs the system parameter generation function Gen(1 n ), the input of the system parameter generation function is n∈Z + , the output parameters and the process are as follows:
[0044] (1.1) Select bilinear mapping group
[0045] The registrar selects the bilinear mapping group G 1 and G 2 , the order of both groups is q, and P is G 1generator of and P∈G 1 , is a bilinear mapping operation.
[0046] (1.2) Generate system master key and system public key
[0047] The registration server generates random numbers As the system master key, and calculate the system public key P pub =sP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com