A machine learning-based ssh protocol login status detection method
A login status and machine learning technology, applied in the field of network security, can solve problems such as missed reports and false positives of login status
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
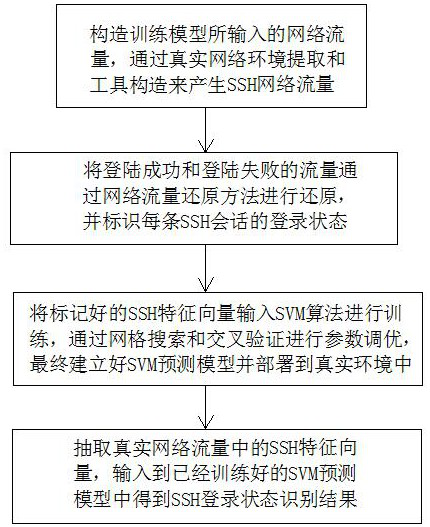
[0042] see figure 1 , a machine learning-based SSH protocol login status detection method, comprising the following steps:
[0043] a. Construct the network traffic input by the training model, generate SSH network traffic through real network environment extraction and tool construction, including SSH-based SCP protocol and SFTP network traffic, and configure password authentication, public key authentication and keyboard interaction respectively SSH network traffic in authentication mode, generate single-session and multi-session SSH brute-force cracking traffic through public SSH brute force tools, use SSH tools to generate normal network traffic and abnormal network traffic, and use SFTP and SCP tools to generate normal network traffic and abnormal network flow;
[0044] b. Restore the traffic of successful login and failed login through the network traffic restoration method, and identify the login status of each SSH session, extract the SSH feature vector used for model...
Embodiment 2
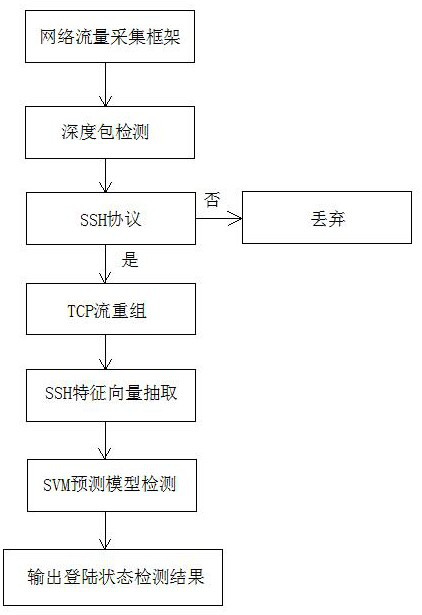
[0049] see figure 1 and figure 2 , a machine learning-based SSH protocol login status detection method, comprising the following steps:
[0050] a. Construct the network traffic input by the training model, generate SSH network traffic through real network environment extraction and tool construction, including SSH-based SCP protocol and SFTP network traffic, and configure password authentication, public key authentication and keyboard interaction respectively SSH network traffic in authentication mode, generate single-session and multi-session SSH brute-force cracking traffic through public SSH brute force tools, use SSH tools to generate normal network traffic and abnormal network traffic, and use SFTP and SCP tools to generate normal network traffic and abnormal network flow;
[0051] b. Restore the traffic of successful login and failed login through the network traffic restoration method, and identify the login status of each SSH session, extract the SSH feature vector...
Embodiment 3
[0065] see figure 1 and figure 2 , a machine learning-based SSH protocol login status detection method, comprising the following steps:
[0066] a. Construct the network traffic input by the training model, generate SSH network traffic through real network environment extraction and tool construction, including SSH-based SCP protocol and SFTP network traffic, and configure password authentication, public key authentication and keyboard interaction respectively SSH network traffic in authentication mode, generate single-session and multi-session SSH brute-force cracking traffic through public SSH brute force tools, use SSH tools to generate normal network traffic and abnormal network traffic, and use SFTP and SCP tools to generate normal network traffic and abnormal network flow;
[0067] b. Restore the traffic of successful login and failed login through the network traffic restoration method, and identify the login status of each SSH session, extract the SSH feature vector...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap