Anti-inference attack privacy protection information matching method and device
An information matching and privacy protection technology, applied in the field of information security, can solve problems such as the inability to adapt to the dynamic changes of user needs and the inability to resist inference attacks, so as to reduce the risk of leakage, do not lose matching accuracy, and resist inference attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
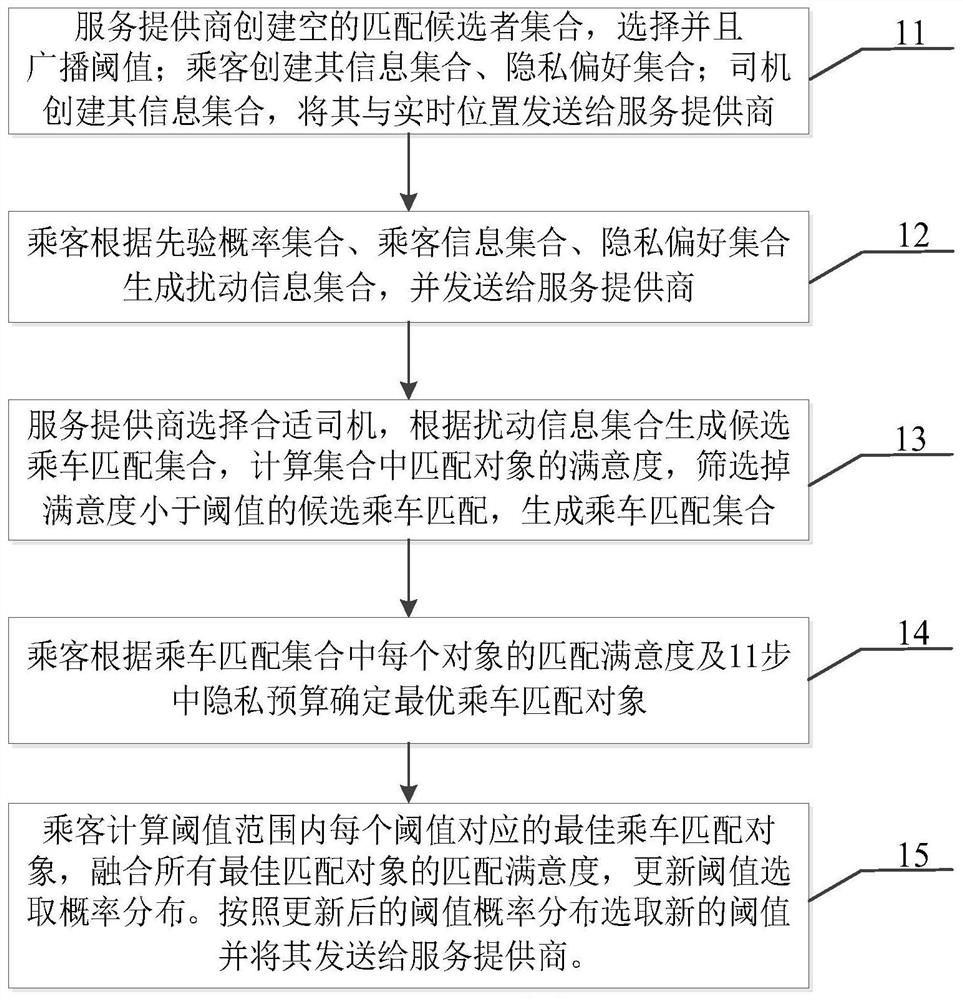
Examples
Embodiment 1
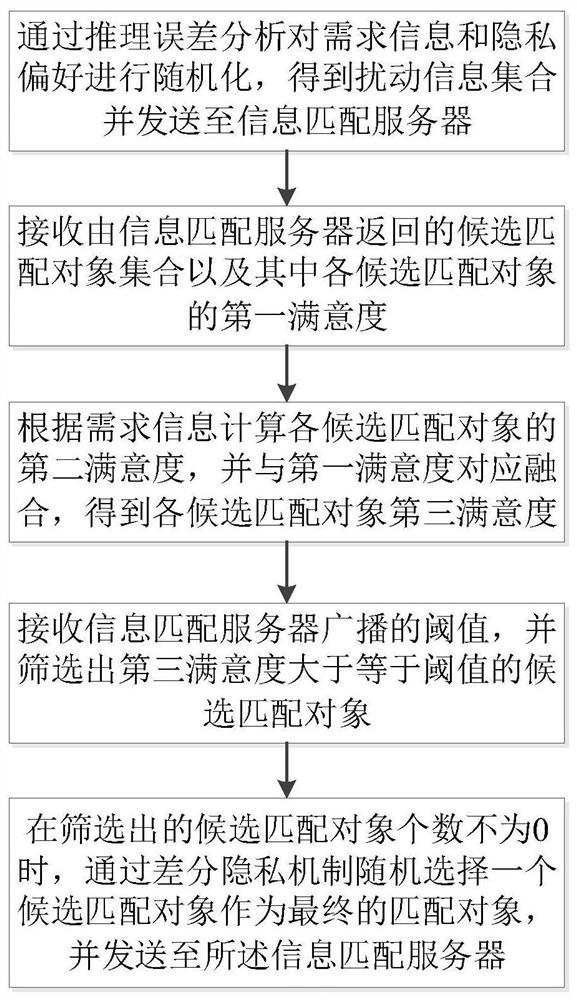
[0065] A privacy-preserving information matching method against inference attacks, such as figure 1 shown, including:
[0066] The demand information and privacy preference are randomized through reasoning error analysis, and the disturbance information set is obtained and sent to the information matching server; each disturbance information point in the disturbance information set is the data point obtained after randomization of the matching scheme that satisfies the demand information ;Demand information includes the basic information needed to obtain the shared service and the user's basic needs for the shared service. For different shared services, there may be different expressions. For example, in the shared vehicle service, the required information may Including the starting point and end point of the itinerary, the time when the ride request is initiated, the longest acceptable walking time from the starting point (drop-off point) to the pick-up point (destination), a...
Embodiment 2
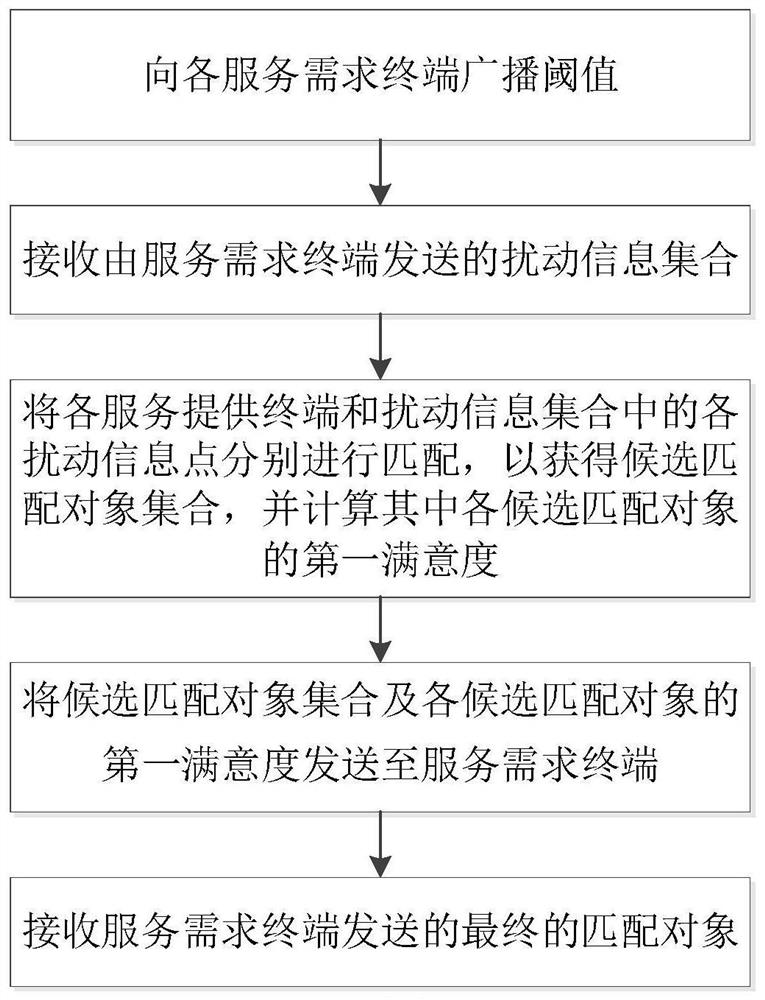
[0088] A privacy-preserving information matching method against inference attacks, such as figure 2 shown, including:
[0089] Broadcast the threshold to each service demand terminal;
[0090] Receive the disturbance information set sent by the service demand terminal; the disturbance information set is obtained by randomizing the demand information and privacy preference of the service demand terminal through reasoning error analysis, and each disturbance information point is the matching scheme that satisfies the demand information. Data points obtained after randomization;
[0091] Match each service provider terminal with each disturbance information point in the disturbance information set to obtain a set of candidate matching objects, and calculate the first satisfaction degree of each candidate matching object; candidate matching objects include disturbance information points and corresponding Matched service provider terminal information, the first degree of satisfa...
Embodiment 3
[0104] A service demand terminal, including a processor and a computer-readable storage medium, where a computer program is stored in the computer-readable storage medium;
[0105] The processor is configured to read the computer program in the computer-readable storage medium, and execute the privacy-preserving information matching method against inference attack provided in Embodiment 1 above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com