Method and system for machine learning secure aggregation prediction supporting bidirectional privacy protection
A machine learning and security aggregation technology, applied in the field of machine learning, can solve the problems of privacy leakage, inability to guarantee the privacy of teacher model training data, leakage of prediction results, etc., to achieve the effect of increasing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] This embodiment provides a machine learning security aggregation prediction method that supports bidirectional privacy protection;
[0040] Machine learning secure aggregate prediction methods that support bidirectional privacy protection, including:
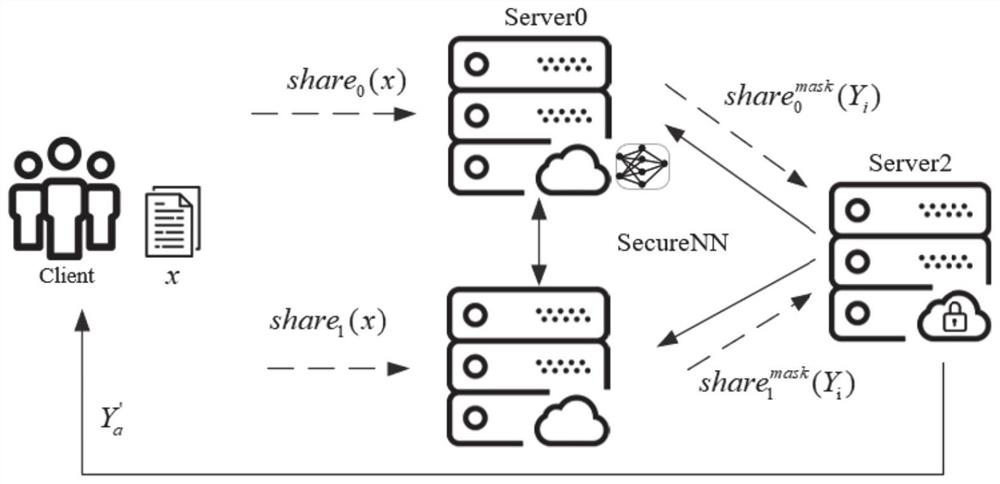
[0041] S101: The calculation server receives the data share of the data to be predicted sent by the client;
[0042] S102: the computing server processes the data share to obtain a predicted result share;
[0043] S103: The computing server performs blinding processing on the prediction result share to obtain a blinded prediction result share;
[0044] S104: The computing server sends the blinded prediction result share to the aggregation server;
[0045] S105: The aggregation server performs blind removal processing and noise addition processing on the shares of the blinded prediction results, and feeds back the results to the client.
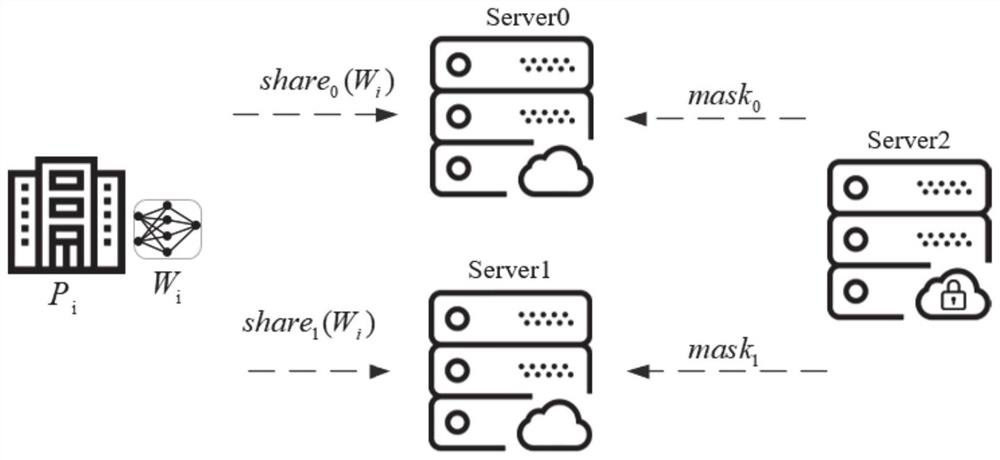
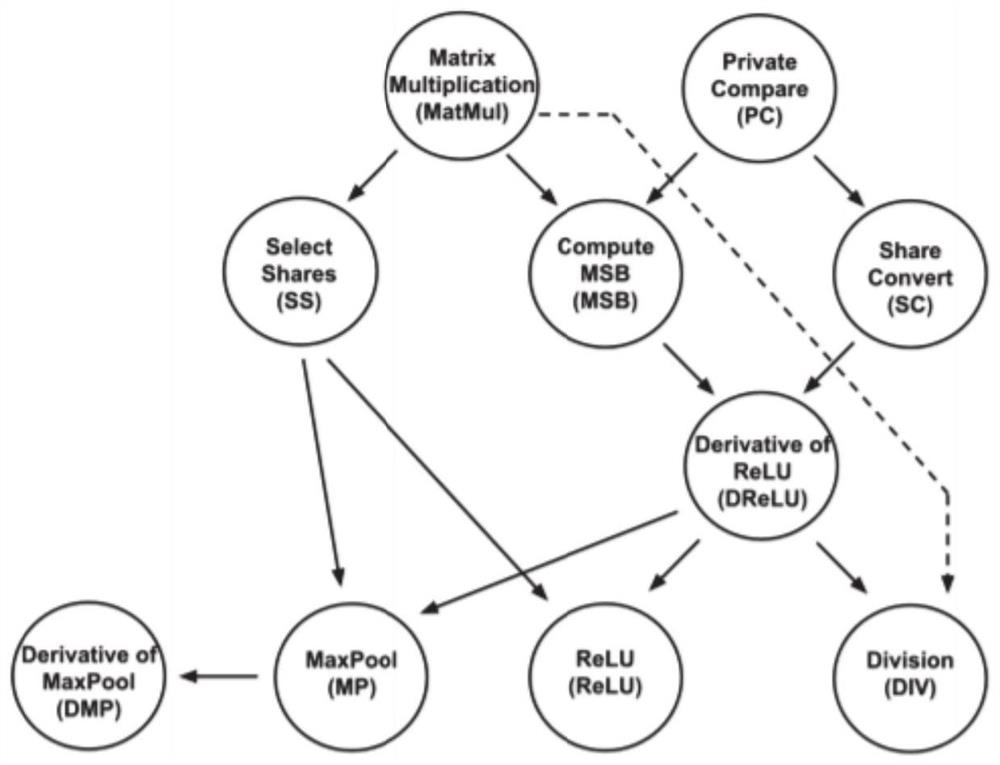
[0046] As one or more embodiments, before step S101, the method fu...
Embodiment 2
[0123] This embodiment provides a machine learning security aggregation prediction system that supports bidirectional privacy protection;
[0124] A machine learning security aggregation prediction system that supports bidirectional privacy protection, including: client, computing server and aggregation server;
[0125] The calculation server receives the data share of the data to be predicted sent by the client; the calculation server processes the data share to obtain the prediction result share; the calculation server performs blind processing on the prediction result share to obtain the blind prediction result share; The computing server sends the blind prediction result share to the aggregation server; the aggregation server performs blind removal processing and noise addition processing on the blind prediction result share, and feeds back the result to the client.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com