Magic square signature method for true or false identification
A magic square and identity technology, applied in the field of magic square signature, can solve the problems of unfavorable data format standardization, easy to be exchanged, public key complex authentication system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
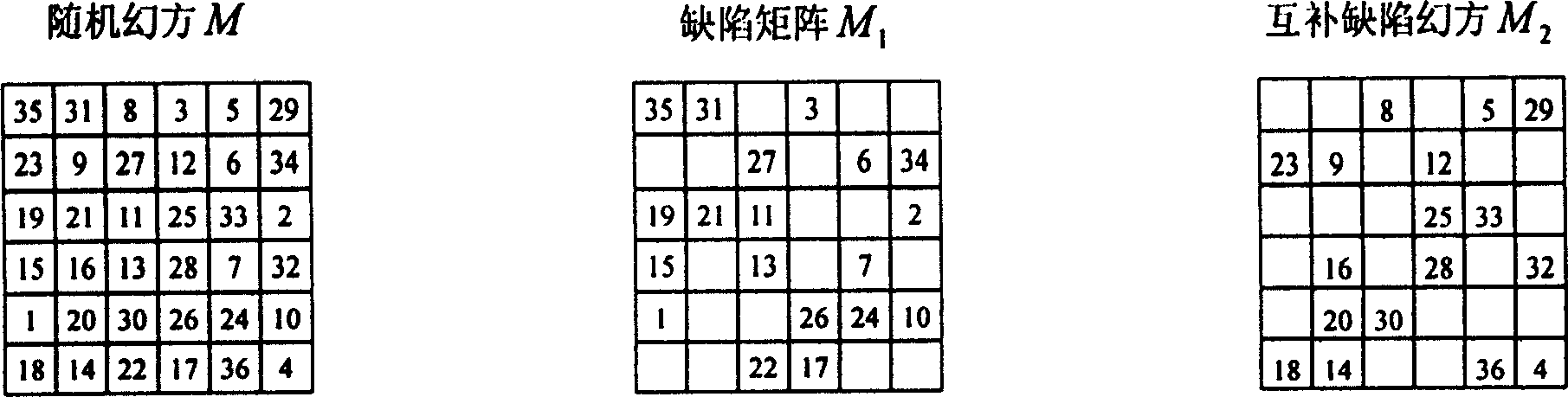
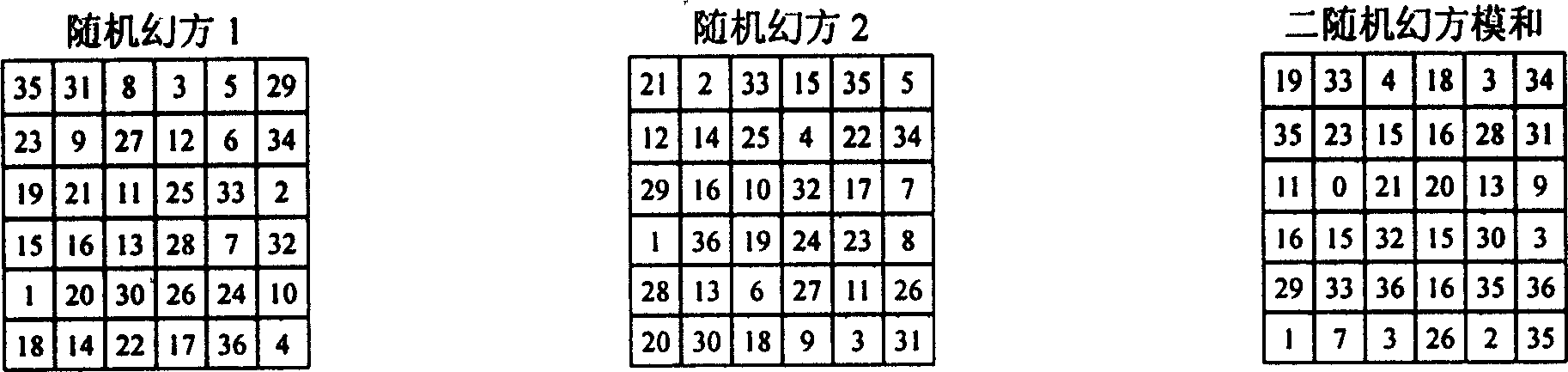
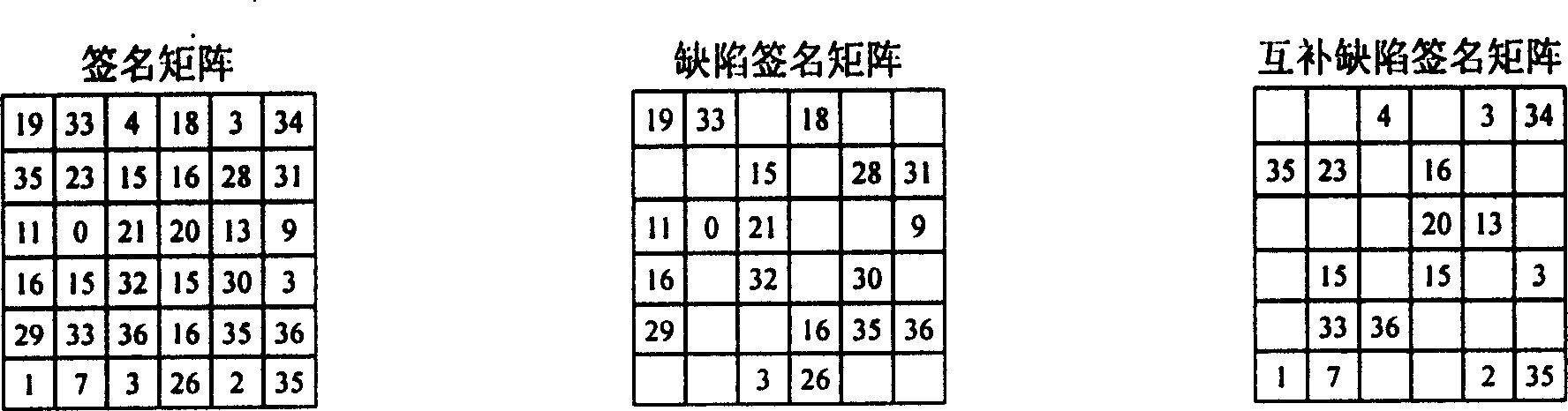
[0100] The principle of defect magic square filling: a randomly constructed magic square is evenly and randomly divided into two complementary defect magic squares. At present, there is no effective unified calculation method in theory, so that the other half can be restored from the defect magic square containing only half of the numbers. Position the numbers so that they still form a magic square, and vice versa. We call this problem the defect magic square filling problem, which is an open mathematical problem, such as figure 1 shown. Generally, if any one of the flawed magic squares is used as a lock, the other one can be used as the corresponding key, and the two are mutually a lock and a key. The corresponding "key" cannot be deduced from the "lock", and the corresponding "lock" cannot be deduced from the "key", and the "lock" can be made public. 7-order magic square can construct 10 34 Lock the magic square number, when the "lock" is known, the exhaustive times of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com