Efficient CAM-based techniques to perform string searches in packet payloads
A payload and search string hash value technology, which is applied in digital transmission systems, instruments, data exchange networks, etc., can solve the problems of not supporting efficient string search function and maintaining line rate speed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
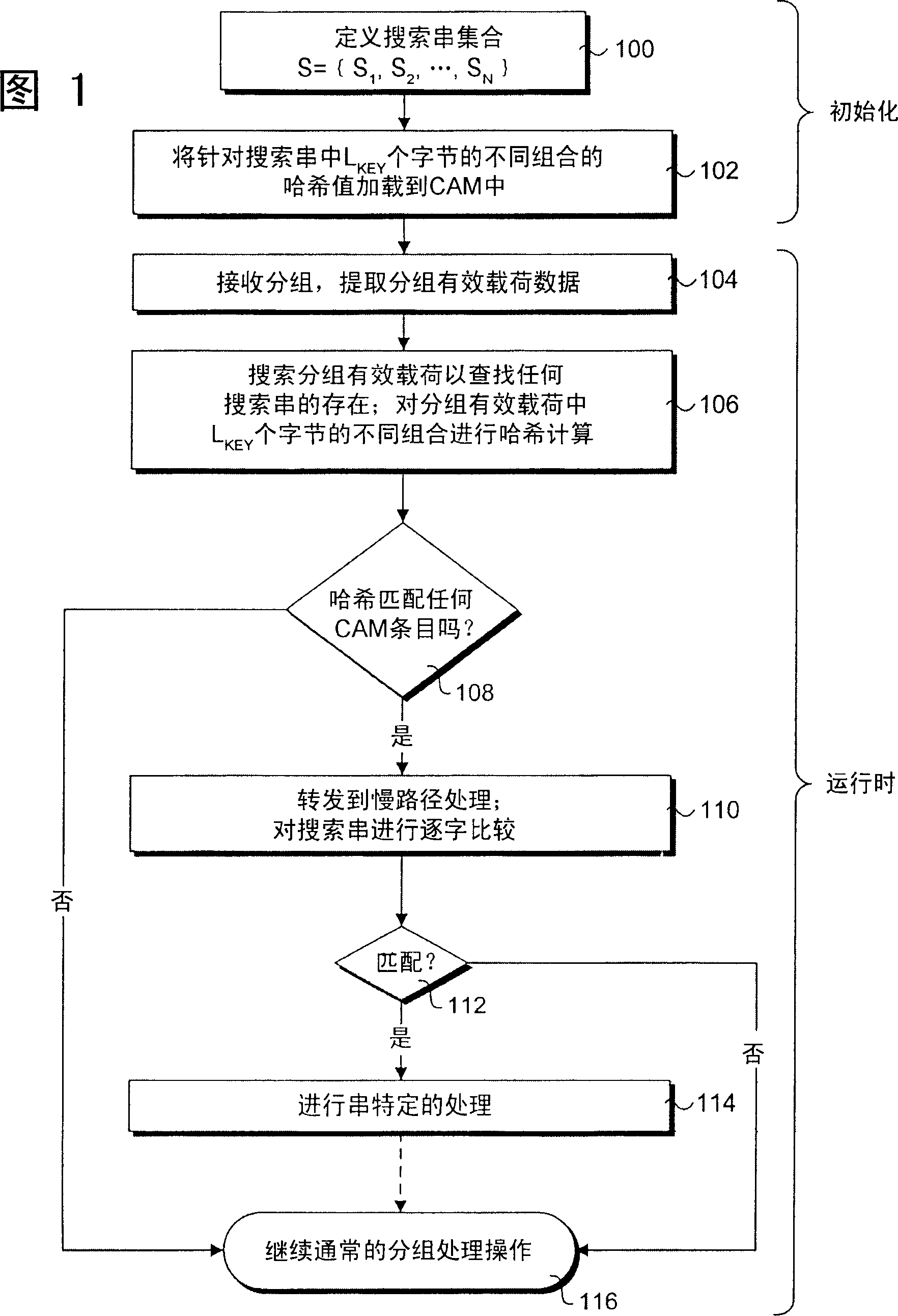
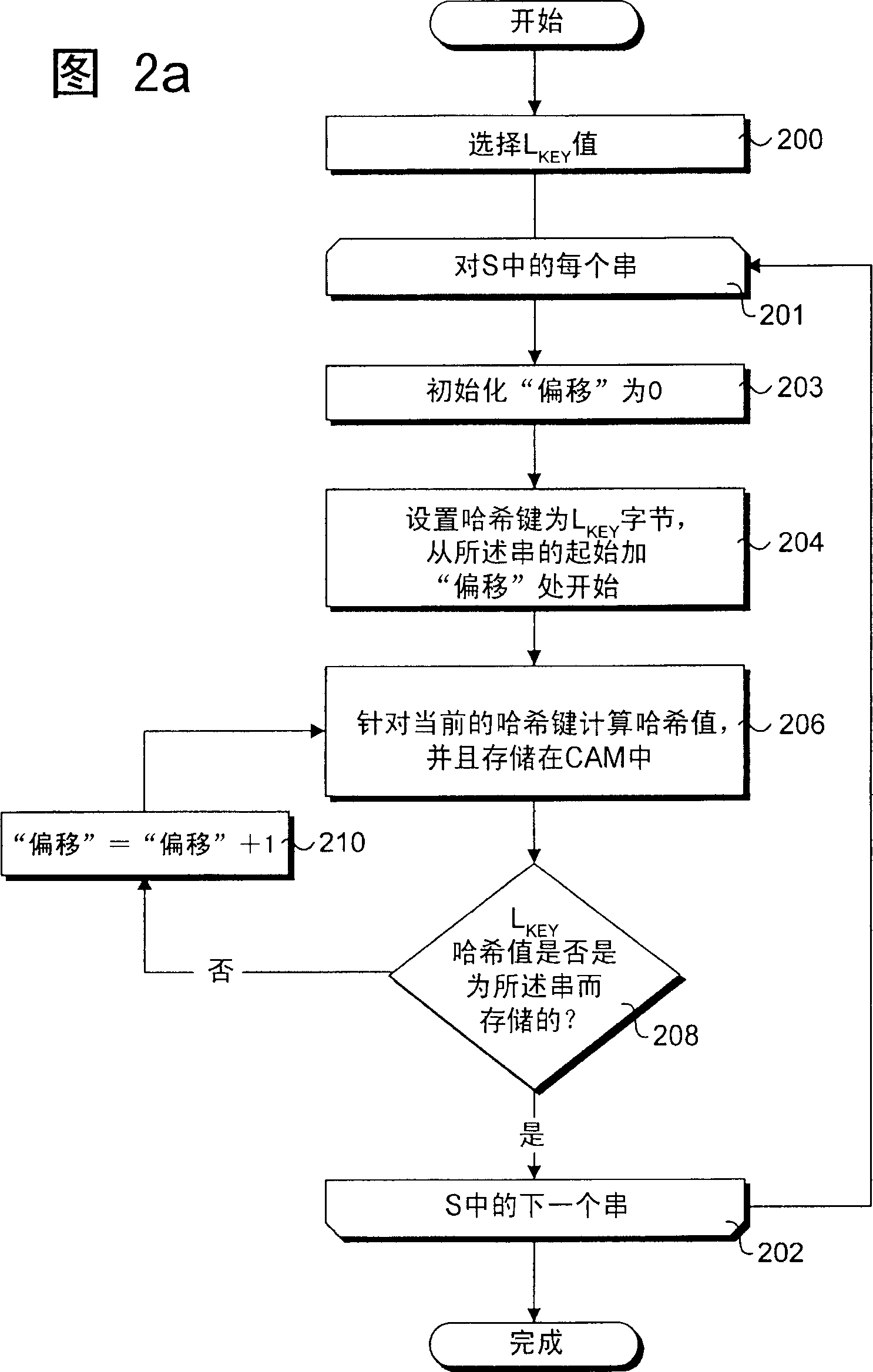
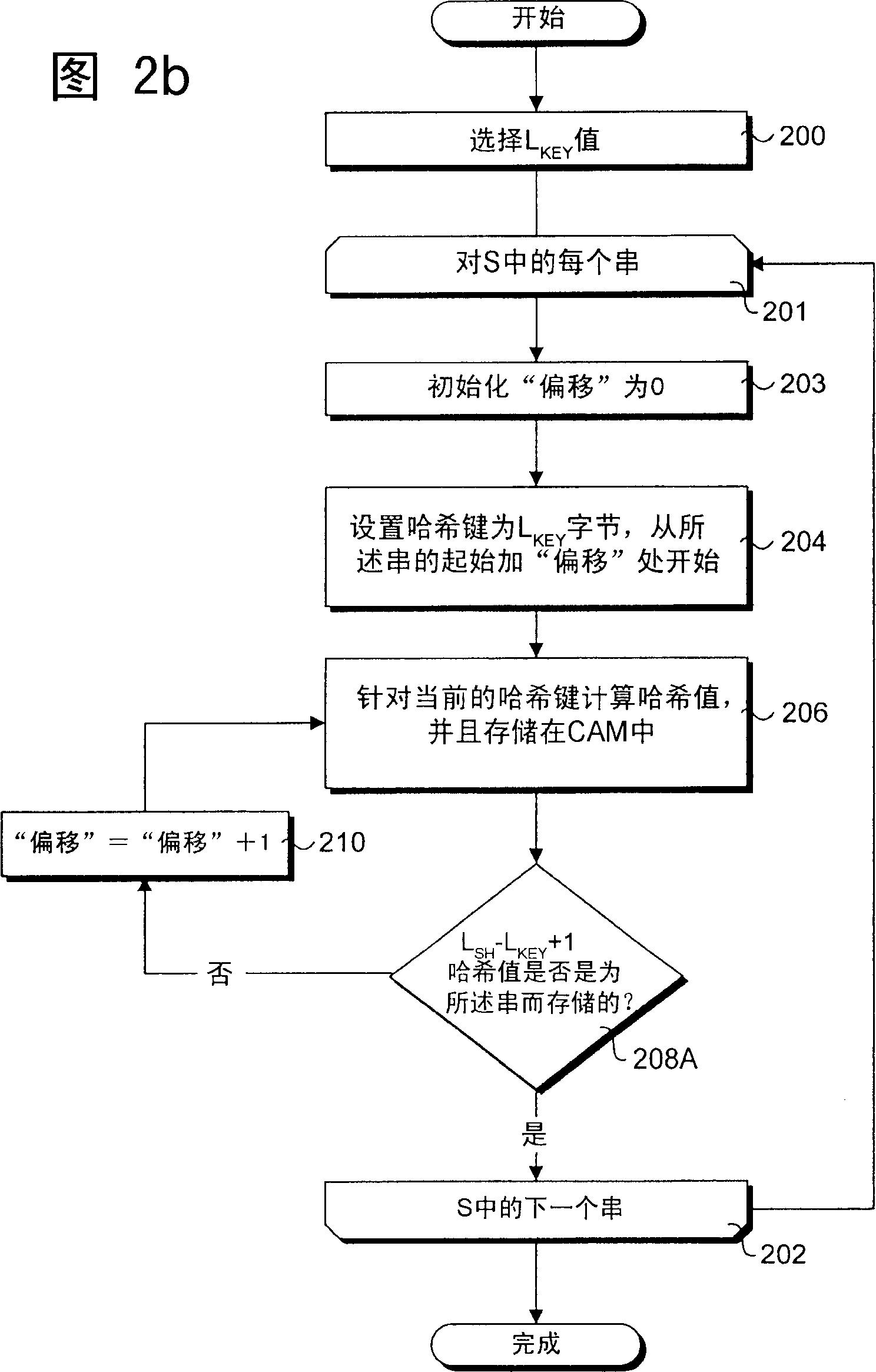
[0086] Under one embodiment, the remaining L of the string KEY A substring of bytes is compared to the hash key of an existing CAM entry. If there is a match, the CAM entry is offset by n(L HOP +L KEY )-L KEY bytes (the number of skipped bytes shown in Figure 8), where n is an integer greater than zero. In this instance, the term "offset" represents the distance (in bytes) between the end of a given hash key and the beginning of the matching hash key. For example, if n=1, one can remove the L offset from the matching hash key HOP The hash key of CAM entry C in Figure 8 33 shown. The reason it works is that if the packet payload search is to consider the hash key corresponding to the removed CAM entry, then the subsequent hops of the search one of the (e.g., the next hop when n=1, the next hop when n=2 The second hop at the time, etc.) will land on another CAM entry, yielding a CAM hit.
[0087] Another optimization involves the adjustment of the "effective" size of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com