Method for realizing safety communication between user equipment and network service application entity
A technology for network services and application entities, which is applied in the direction of public keys for secure communication, and can solve problems such as not providing a key selection mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
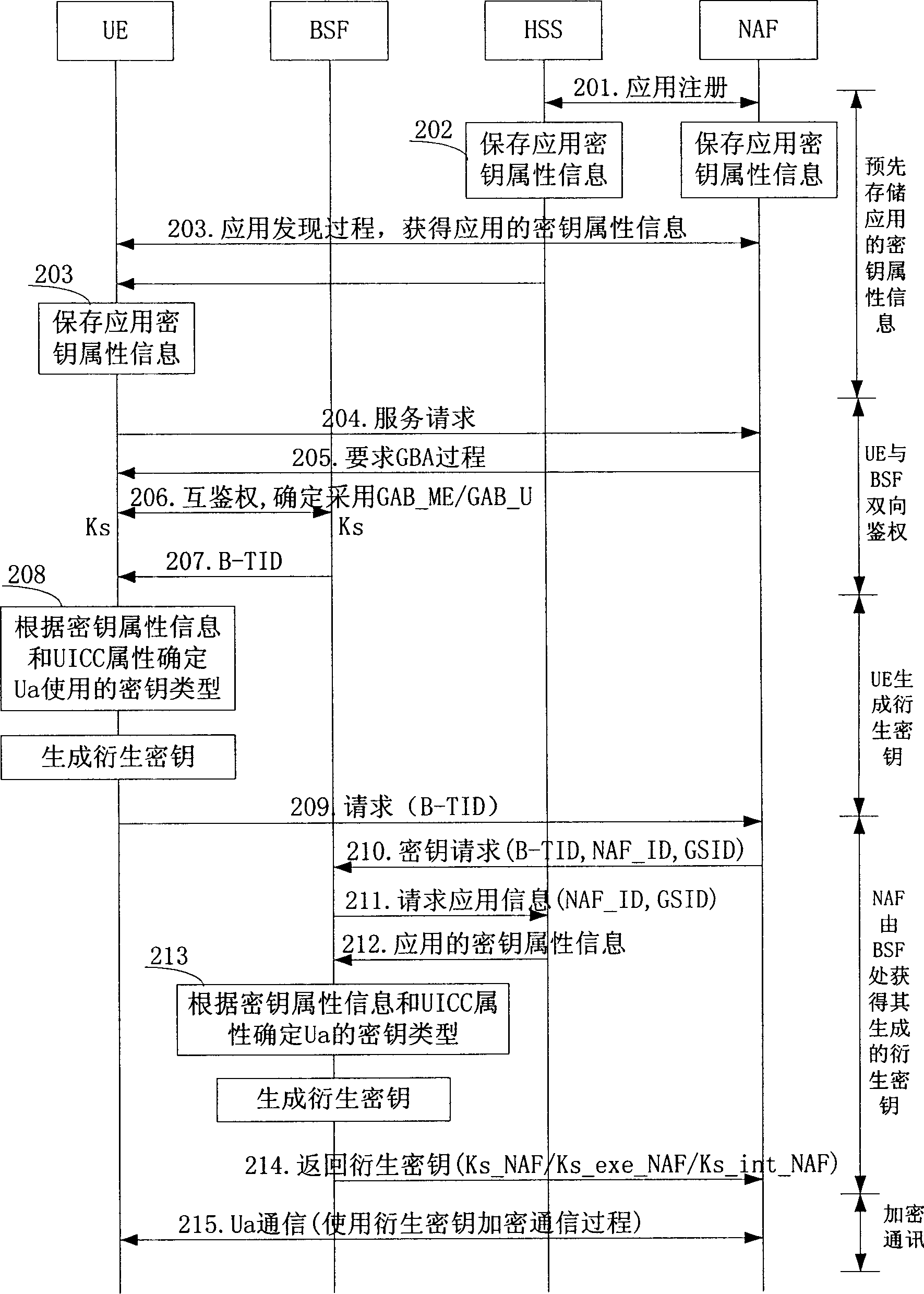
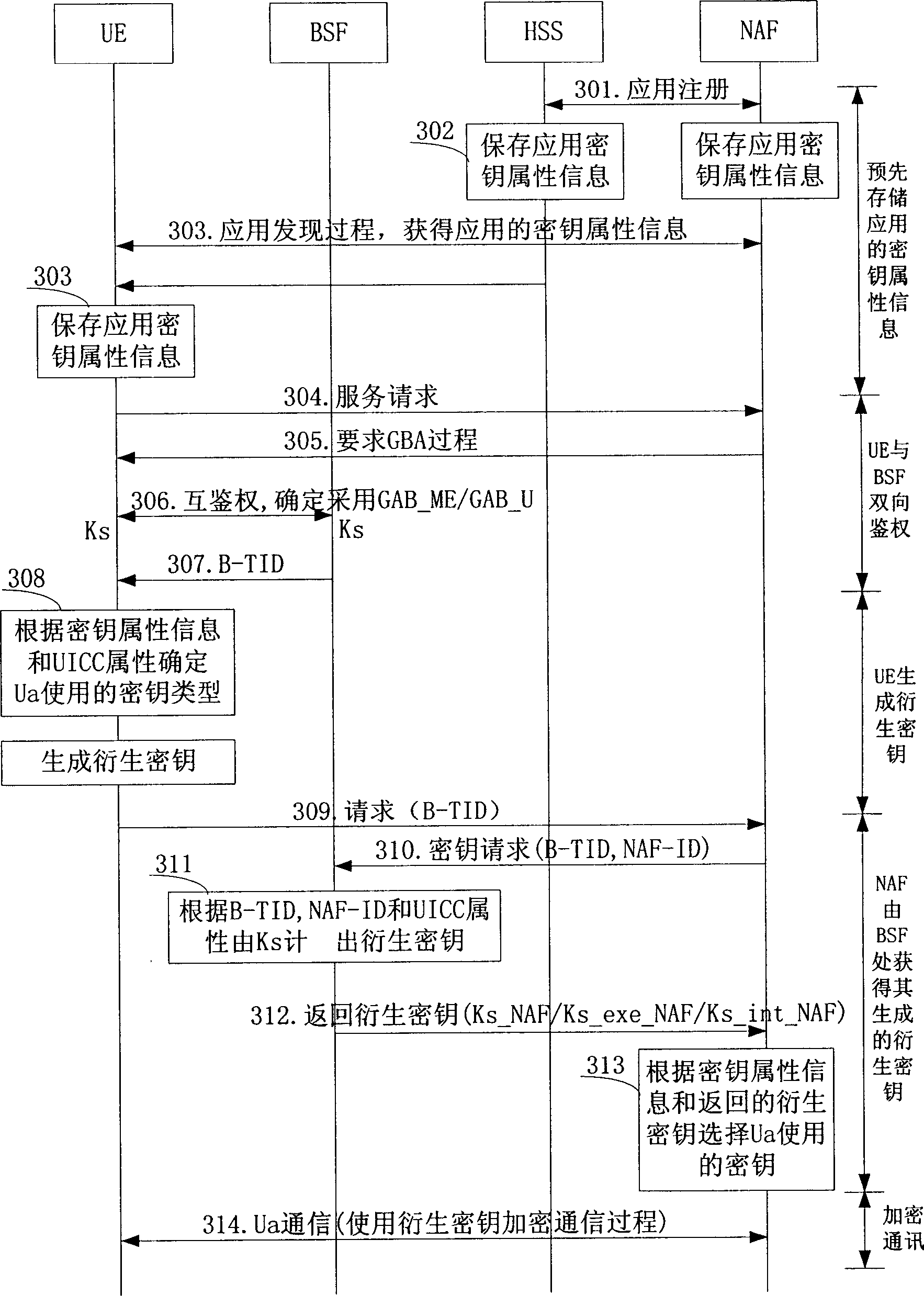
[0043] The invention specifies different protection key types used by different applications, and when a user wants to use a certain application to communicate with NAF, a corresponding key is generated according to the protection key type specified by the user.
[0044] When the UE needs to use a certain application, the process of realizing the communication between the UE and the NAF is divided into the following stages:
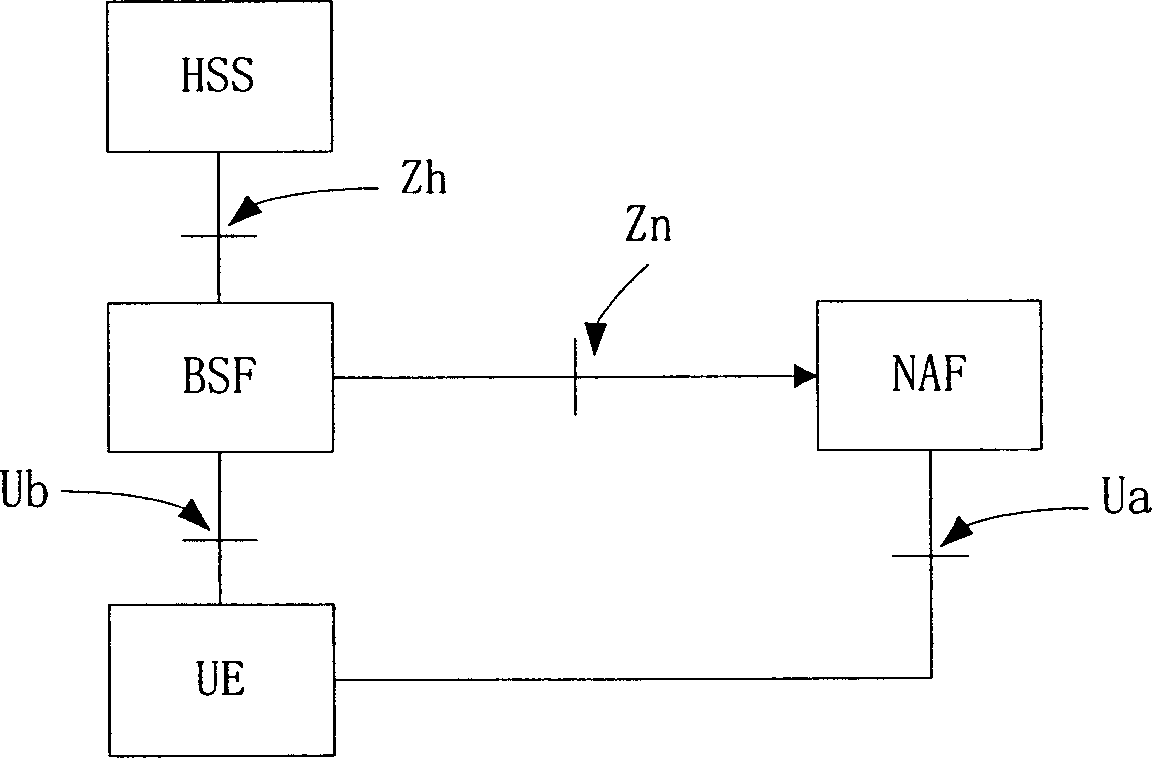
[0045] The first part: in advance, both the network and the UE store the information of different protection key types used at the Ua interface specified by different applications. This information can be called the key attribute information of the application;
[0046] The second part: before the communication, the UE and the BSF perform a two-way authentication process to generate a shared key Ks;
[0047] The third part: UE uses Ks to generate a derived key and selects which derived key to use according to the key management function of UICC and the ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com