A encryption U disk system with journal and audits
A log, encryption and decryption module technology, applied in the direction of computing, computer security devices, instruments, etc., can solve the problems that data confidentiality is difficult to be reliably guaranteed, the problem of U disk usage auditing cannot be well solved, and the user cannot be known, etc. , to achieve the effect of preventing viruses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] A kind of encrypted U disk system with log strong audit proposed by the present invention, combined with drawings and embodiments, is described in detail as follows:
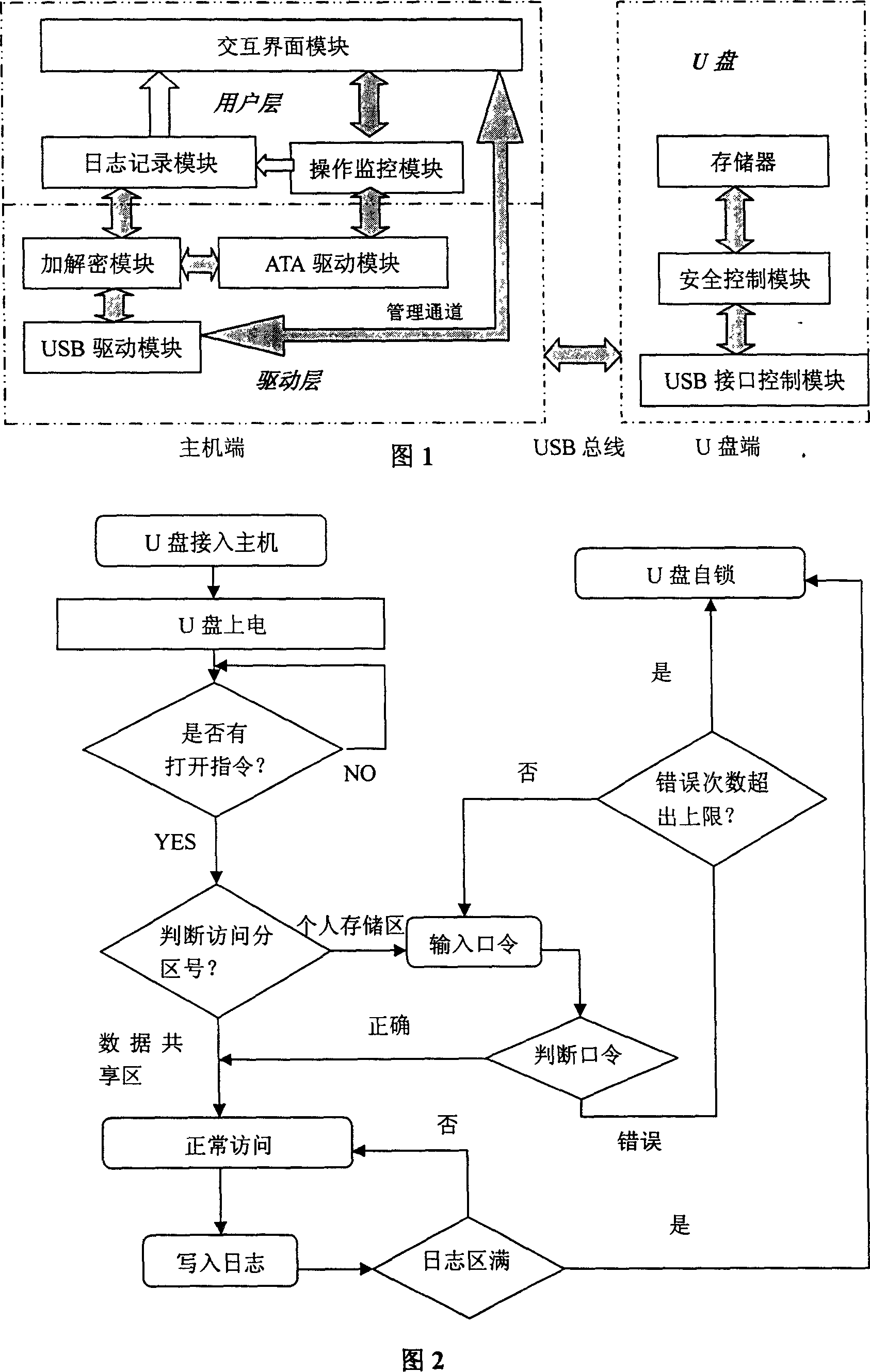
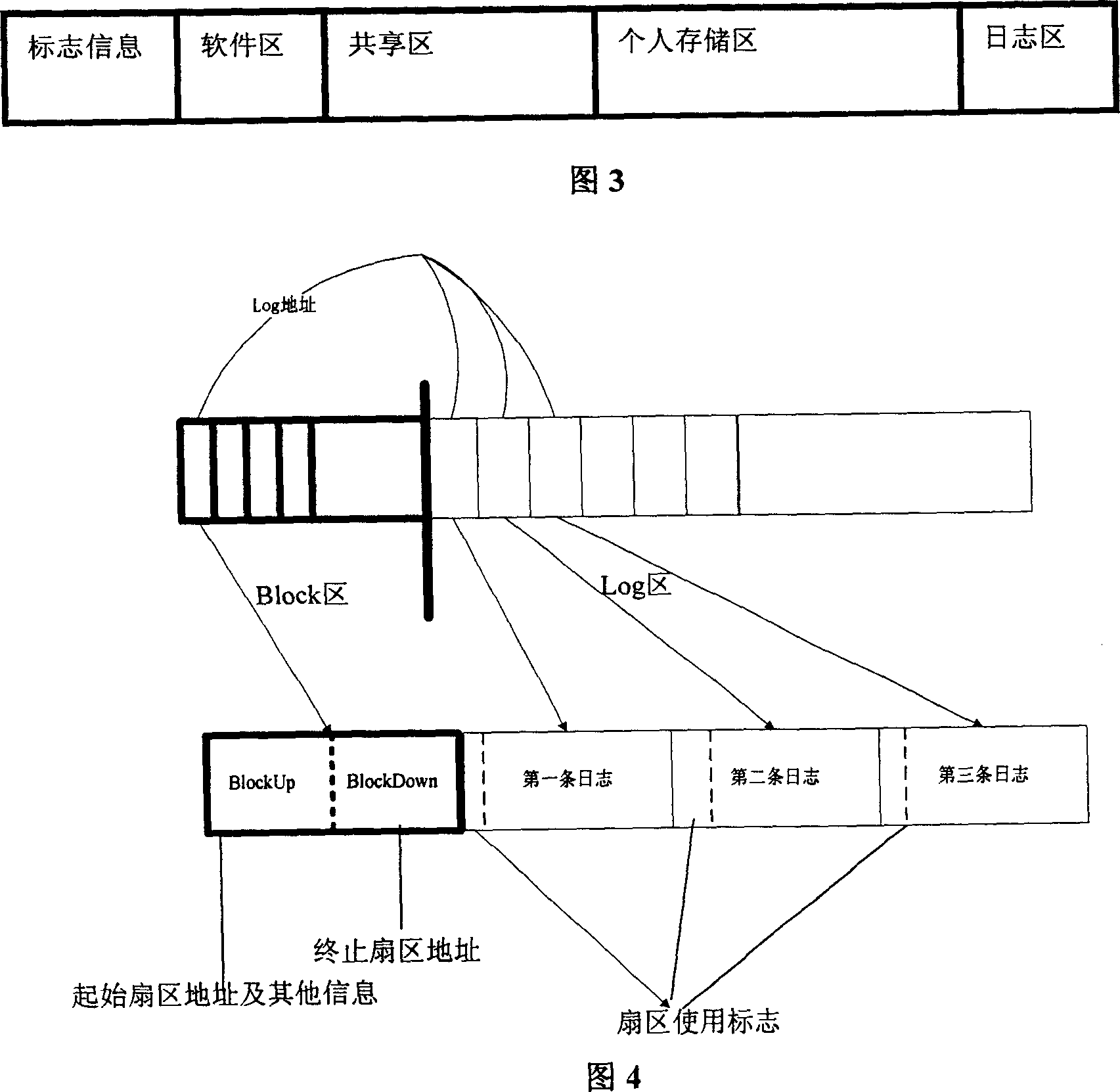
[0021] Overall composition structure of the present invention as shown in Figure 1, comprises the user layer and driver layer that are arranged on host computer (computer) end, and the U disk that is made of memory, safety control module and USB interface control module; U disk passes through standard USB interface Access to the host side, the user layer of the host side performs data and command interaction with the U disk through the USB bus (according to the USB protocol).
[0022] The composition of each component is described as follows:
[0023] user layer
[0024] The user layer provides an interactive interface for user operations, monitors user operations, generates log information and file read and write data to interact with the driver layer; the user layer includes an interactive interface mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com