Class coalescence for obfuscation of object-oriented software
a technology of object-oriented software and coalescence, applied in the direction of program control, unauthorized memory use protection, instruments, etc., can solve the problems of software tampering with malicious intent, such as planting a trojan horse in the end user's system, being very undesirable, and being particularly susceptible to piracy and other forms of malicious condu
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
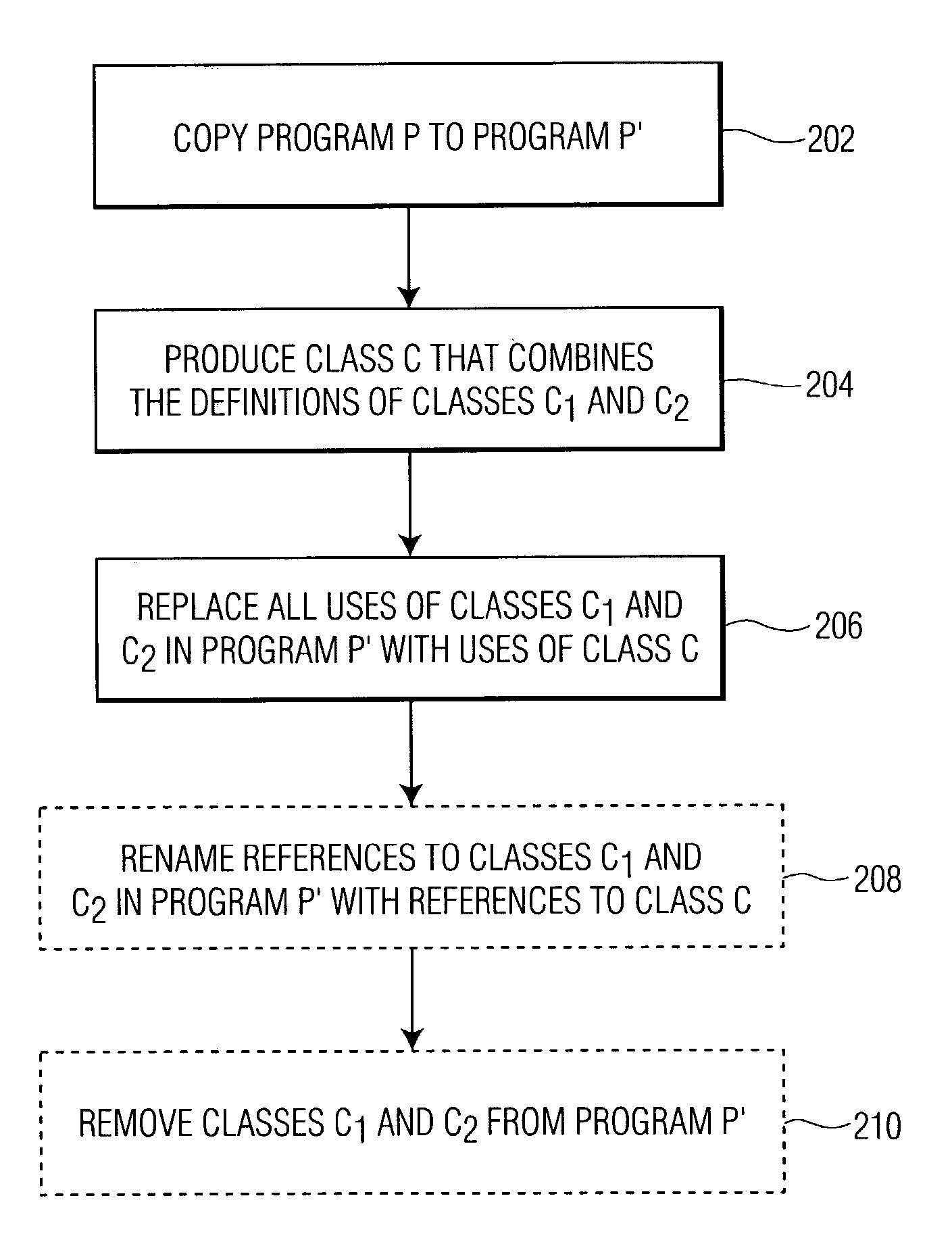
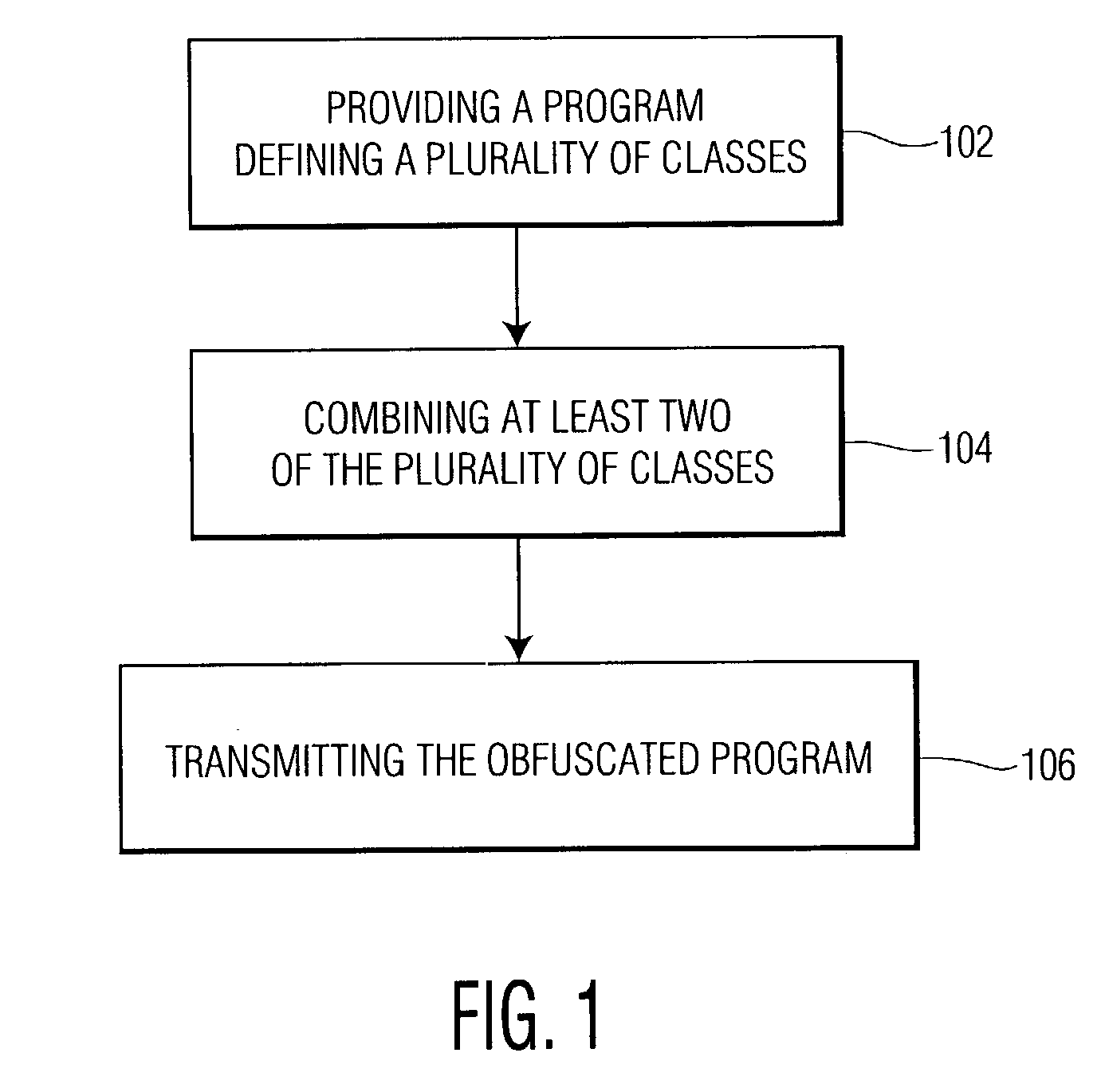
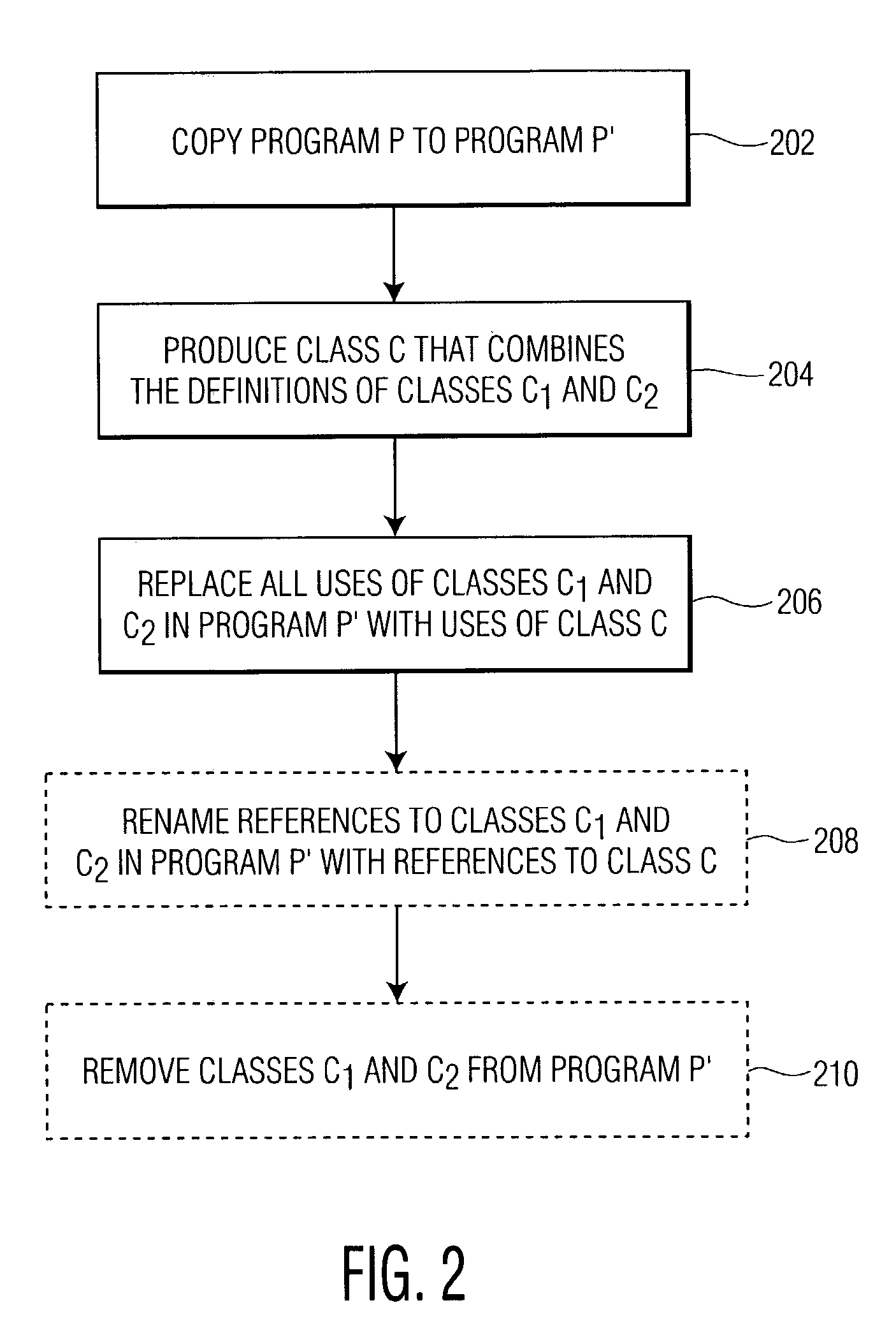
[0015]In an exemplary embodiment, the present invention relates to an obfuscation technique for programs written in an object-oriented language based on combining (coalescing) classes in a way that preserves the functional behavior of the program. In such an embodiment, if several classes are coalesced, the number of classes used by the program is reduced. The resulting obfuscation breaks abstractions represented by the coalesced classes, thereby making reverse engineering of the program more difficult. In some situations, it should be noted that class coalescence by itself may not provide sufficient obfuscation to prevent re-engineering and / or tampering. As such, it is anticipated that class coalescence may be used in conjunction with other obfuscation techniques such as variable renaming and splitting, to produce powerful and efficient obfuscation transformations.
[0016]Although the present application concentrates heavily on coalescing classes in Java programs, the invention is ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com