Method for constructing online personal identity database automatically
A technology for automatic construction and network identity identification, applied in the field of automatic construction of network personal identity database, can solve the problems of unable to support the input and arrangement of massive data of network users, difficulty in tracing, and the inability to realize real-time update and maintenance of network personal identity database, etc. Achieve the effect of real-time update and maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
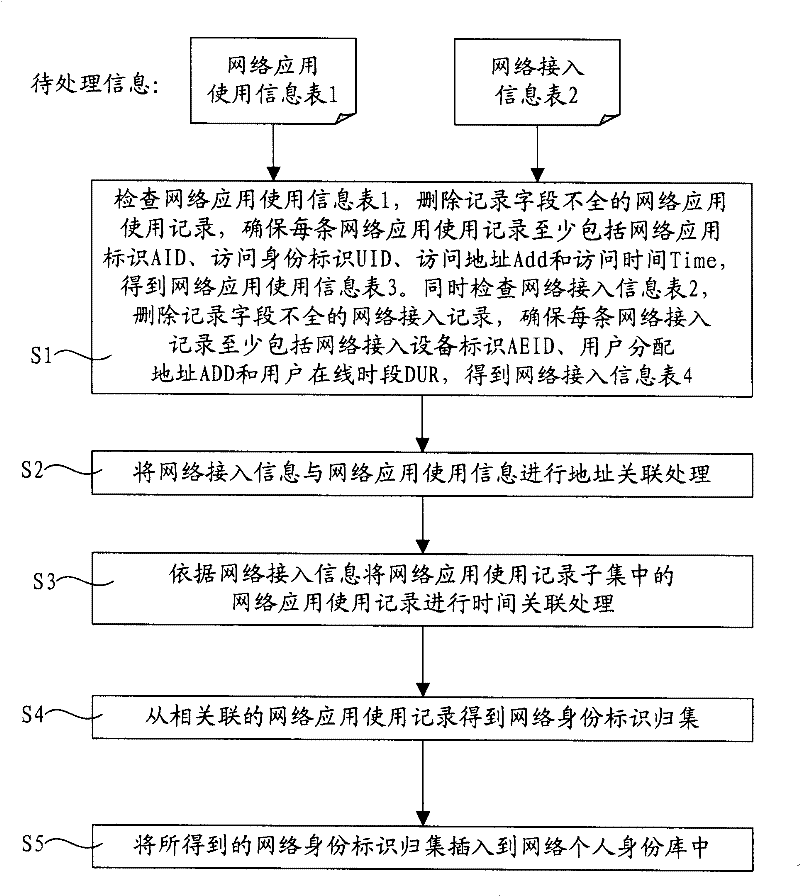
[0026] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0027] figure 1 It shows the flow of a preferred embodiment of the method for automatically constructing the network personal identity database of the present invention. See figure 1 Each step in the method flow will be described in detail below in conjunction with a specific example.
[0028] Data source description: the network application usage information and network access information used in the present invention can be collected by existing equipment and preprocessed by existing technologies.
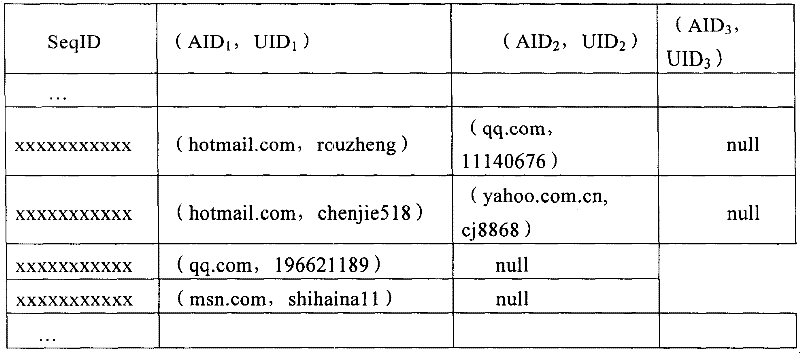
[0029] Assume that in this embodiment, the network application usage information used is as shown in Table 1 of the network application usage information:
[0030] UID
AID
add
Time
chenjie518
hotmail.com
210.221.85.121
2006-05-22
09:31:18
shihaina11
msn.c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com