Login validation method for network system database
A technology for network system and login verification, which is applied in the direction of user identity/authority verification, etc., and can solve problems such as hidden safety hazards and hidden dangers of online game databases
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0010] Specific embodiments of the present invention will be described below with reference to the accompanying drawings.
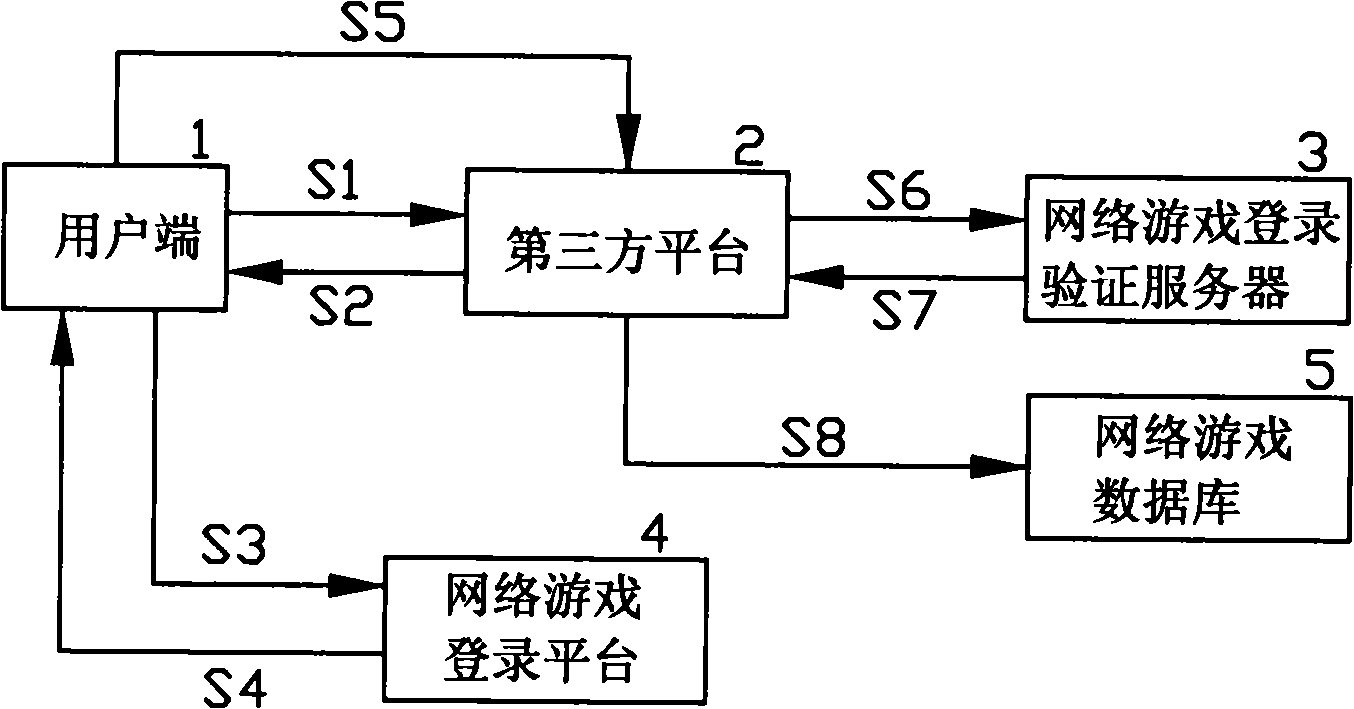
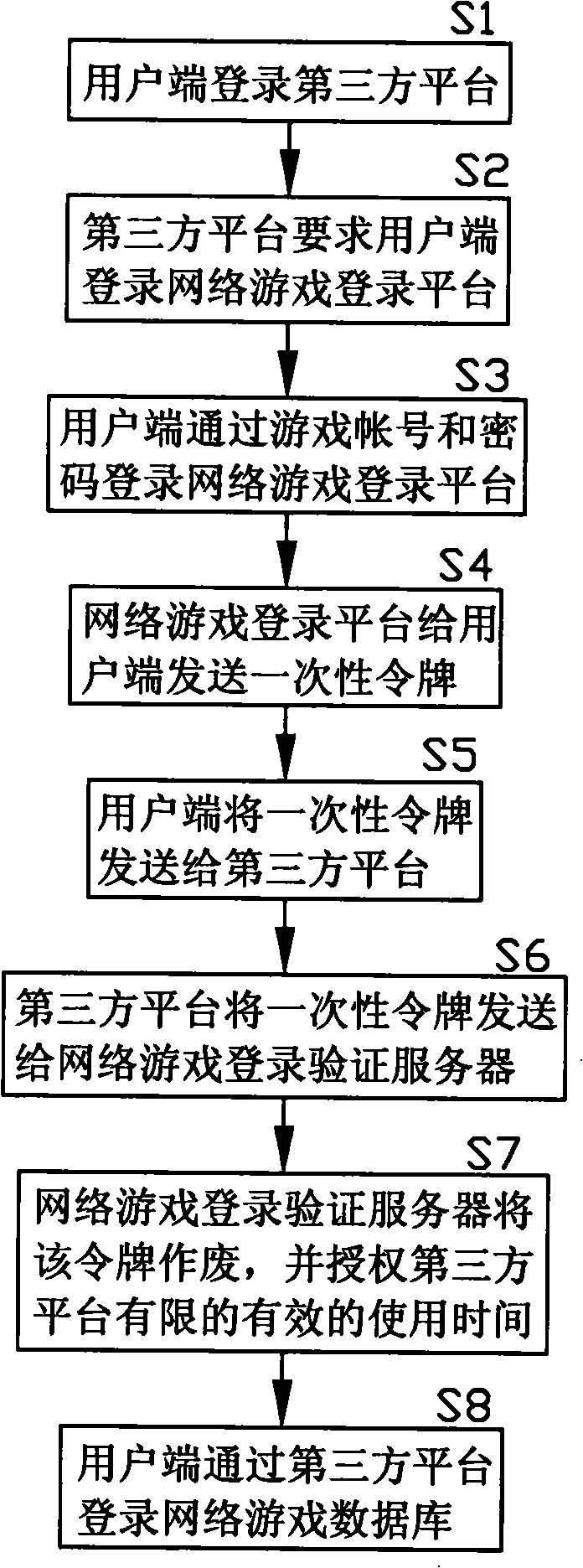
[0011] This embodiment is mainly to provide a safe login verification method for logging into the game database for the online game virtual property online transaction management system, that is, to provide a safe login verification method for logging into the online game database through a third-party platform. The above-mentioned online game virtual property online management system mainly establishes a management platform that supports many client terminals with functions such as online storage, transfer, transaction and payment, and establishes an adapter between the management platform and the network game operator system. A series of standardized definitions made by the adapter enable data exchange between the management platform and the game database of the online game operator system, so as to realize the online storage, transfer, transaction and p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com