Apparatus and method for generating verification specification of verification target program
A target program and specification technology, applied in the direction of program control design, instrumentation, error detection/correction, etc., can solve problems such as difficult to describe verification specifications without errors, difficult to judge, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
---- example 1
[0039] -----Example 1: Verification object-----
[0040] file f; / / file
[0041] mutex m; / / Mutual exclusion lock
[0042] int x;
[0043] f.fopen("text.txt");
[0044] m.init();
[0045] while(*){
[0046] m. lock();
[0047] if(*){
[0048] x = f.read(...);
[0049] }
[0050] else {
[0051] x = f.write(...);
[0052] if(x<0)break;
[0053]}
[0054] m. unlock()
[0055]}
[0056] f. fclose();
[0057] m. destroy();
[0058] Example 2 shows the validation specification (Validation Specification 1). Verification specification 1 defines a finite state machine (finite state machine) that provides a usage method of a mutex. The structure of the finite state machine is shown in Figure 16. This specification (name: mutex_check1) uses the symbol "v" to refer to the abstract state of the program variable type "{mutex}". A state variable "v" is an occurrence of a variable in a program whose initial state is "start" and transitions from "s...
---- example 2
[0059] -----Example 2: Verification Specification 1-----
[0060] sm mutex_check1{
[0061] state decl{mutex}v;
[0062] decl any_fn_call call;
[0063] decl any_args args;
[0064] start:
[0065] {v}==>v.undef;
[0066] v. undef:
[0067] {v.init()}==>v.valid
[0068] |{v.call(args)}==>{err("1")};
[0069] v. valid:
[0070] {v.lock()}==>v.valid
[0071] |{v.unlock()}==>v.valid
[0072] |{v.destroy()}==>v.undef
[0073] |{v.call(args)}==>{err("2")};
[0074]}
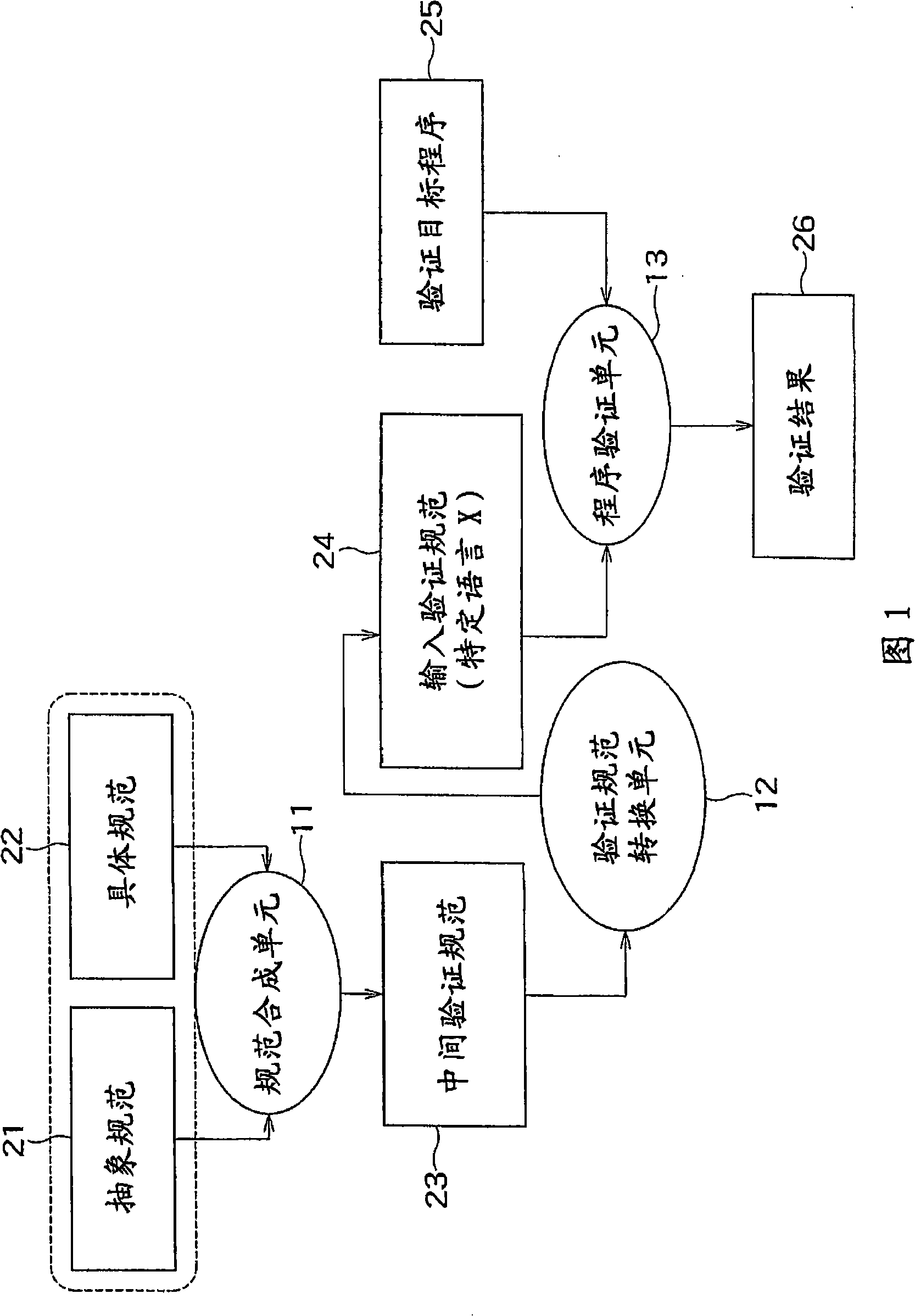
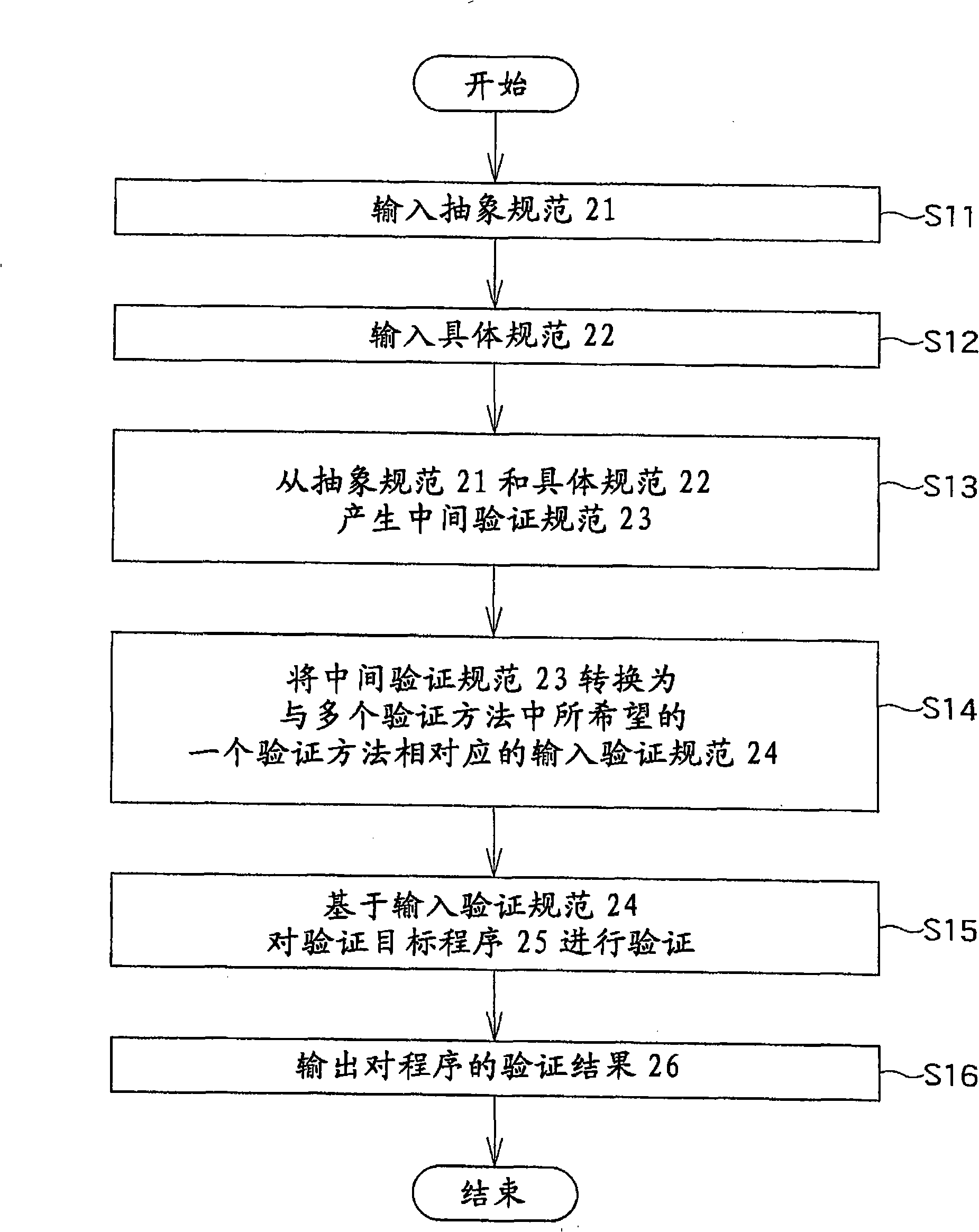
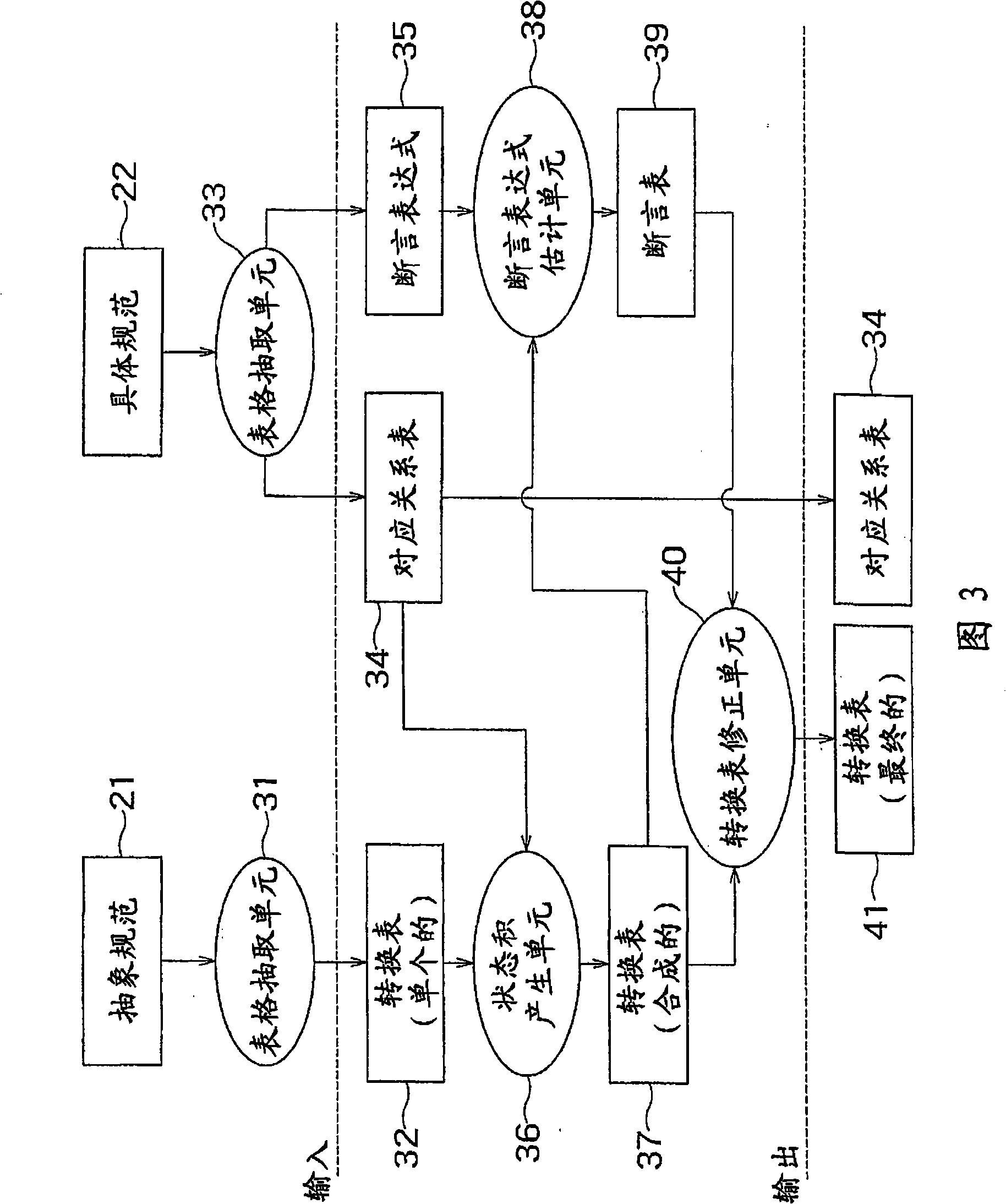
[0075] In the program verification apparatus X of FIG. 12, the verification target program shown in Example 1 is converted into the control flow graph shown in FIG. 13 according to well-known steps. Each basic box in the control flow graph is the maximum code (maximum code), excluding branching and merging of the program. The basic boxes are connected by directed edges indicating branch targets. The program verification device X searches the control flow graph in an ...
----- example 3
[0078] -----Example 3: Verification Specification 2-----
[0079] sm mutex_check2{
[0080] state decl{mutex}v;
[0081] decl any_fn_call call;
[0082] decl any_args args;
[0083] start:
[0084] {v}==>v.undef;
[0085] v. undef:
[0086] {v.init()}==>v.valid
[0087] |{v.call(args)}==>{err("error1")};
[0088] v. valid:
[0089] {v.lock()}==>v.locked
[0090] |{v.destroy()}==>v.undef
[0091] |{v.call(args)}==>{err("error2")};
[0092] v. locked:
[0093] {v.unlock()}==>v.valid
[0094] |{v.call(args)}==>{err("error3")};
[0095]}
[0096] If you want to check the entry of the file before starting the operation, then, by substituting "{file}" for "{mutex}" and "v.open()" for "v.init()" in validation specification 1 of Example 2 " to generate validation specifications.
[0097] In this way, in conventional verification specifications 1 and 2, the definition of the finite state machine and the definition correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com