System for real-time intrusion detection of SQL injection WEB attacks
An intrusion detection system and injection attack technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as high false alarm rate, special character filtering of input parameters, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
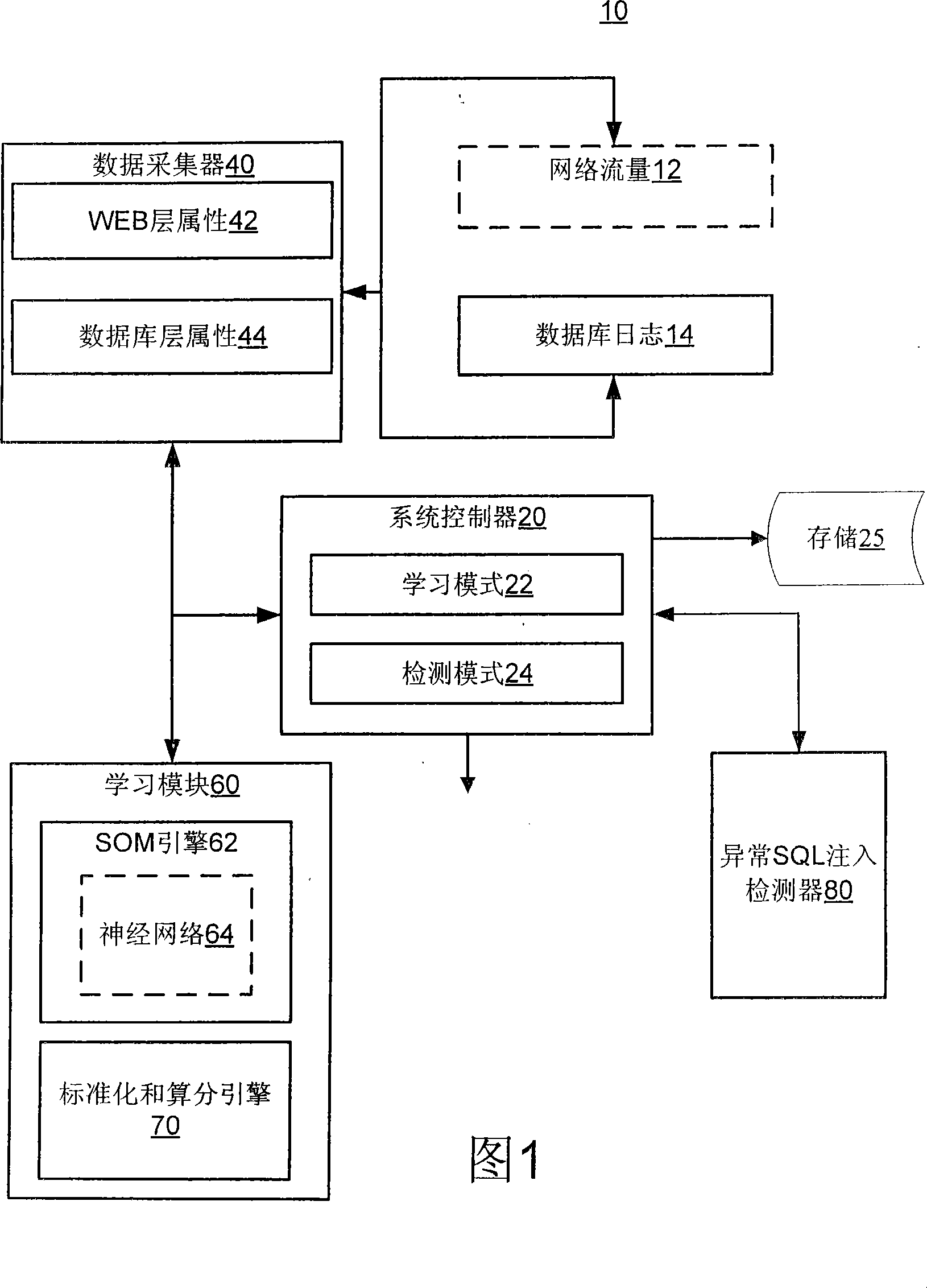
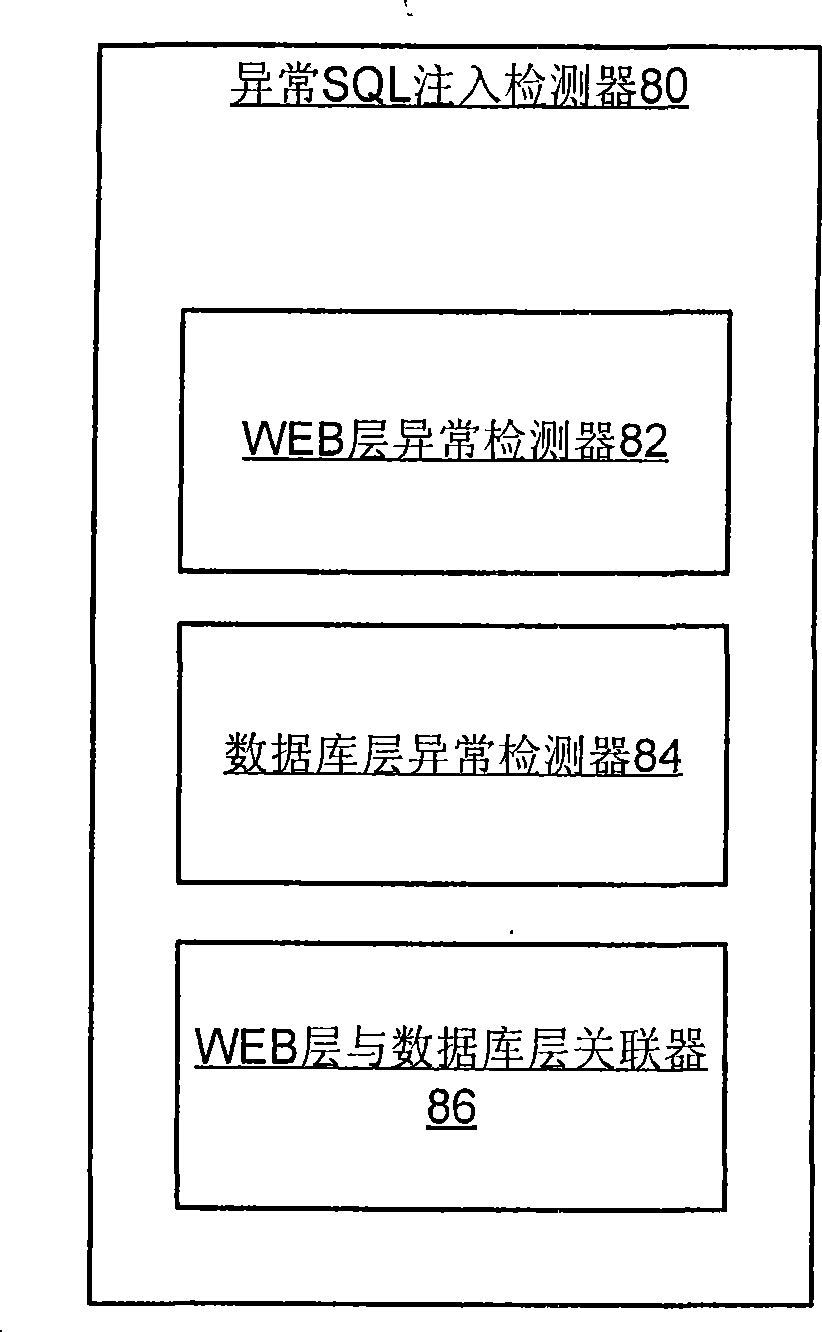
[0113] Embodiment 1: Referring to the chart, the real-time abnormal SQL injection detection system consistent with the present invention is represented by the number 10 in FIG. 1. The development goal of the system 10 is to detect abnormal SQL injection, and through such as Picture 10 The illustrated association between the database layer 520 and the web application layer 510 achieves high accuracy and low false alarms. The database layer 520 corresponds to figure 2 The background database 220 in the. The web application layer 510 corresponds to figure 2 Web server 210 or other computer equipment running WEB applications.
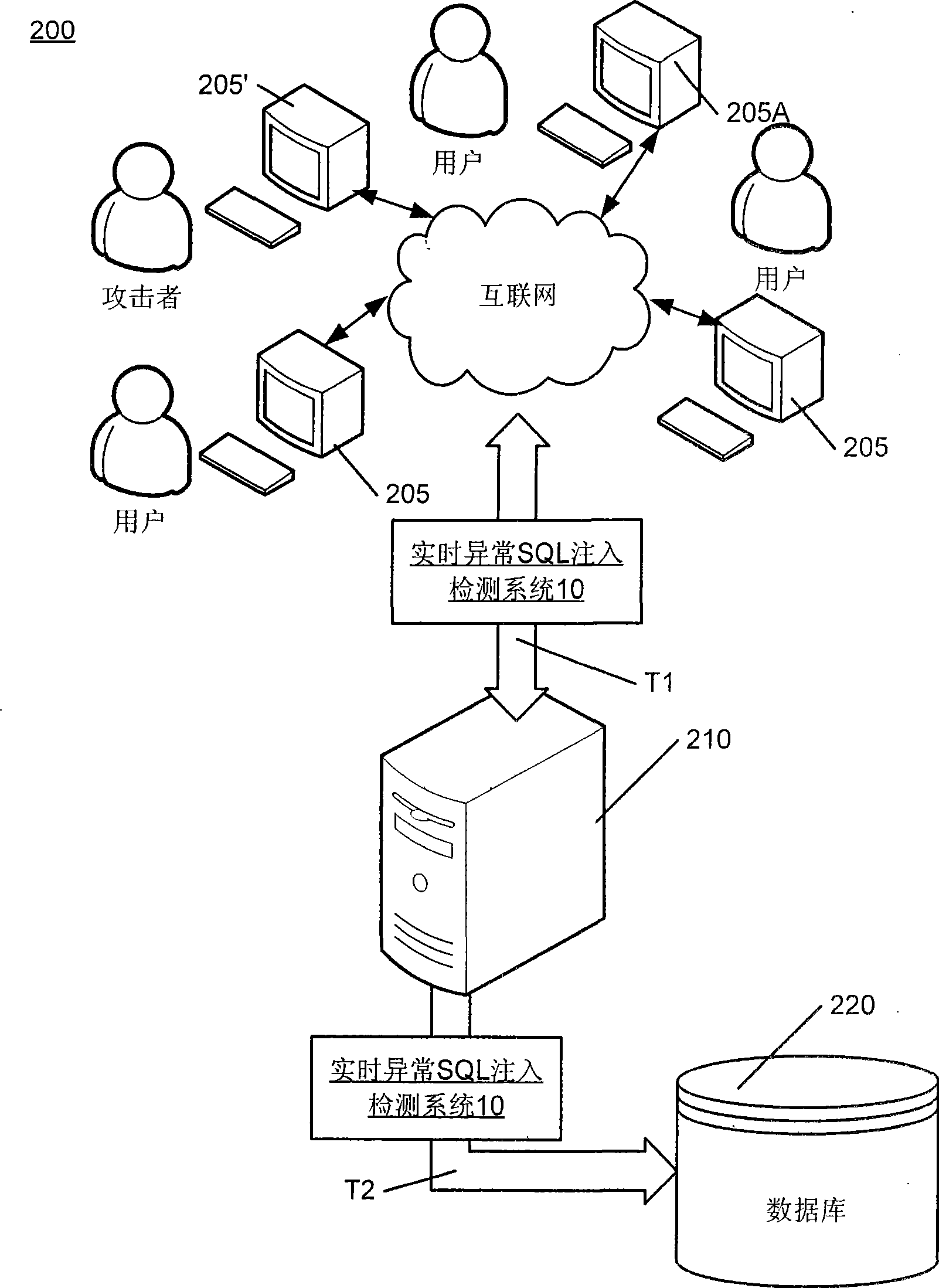
[0114] figure 2 It is a schematic diagram of the system 10 in FIG. 1 being applied to a website 200 for real-time abnormal SQL injection attack detection. The website 200 includes a WEB server 210 that provides WEB applications for end users 205. The end users 205 can be personal computers, laptops, notebook personal computers, notebooks, or other computer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com