Method for implementing continuous authentication joint intrusion detection by mobile equipment in wireless network
A mobile device, wireless network technology, applied in wireless communication, user identity/authority verification, security devices, etc., can solve the problems of information cannot be shared with each other, cannot be combined and applied wireless terminal equipment, cannot be united, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] In order to understand the technical content of the present invention more clearly, the following examples are given in detail.
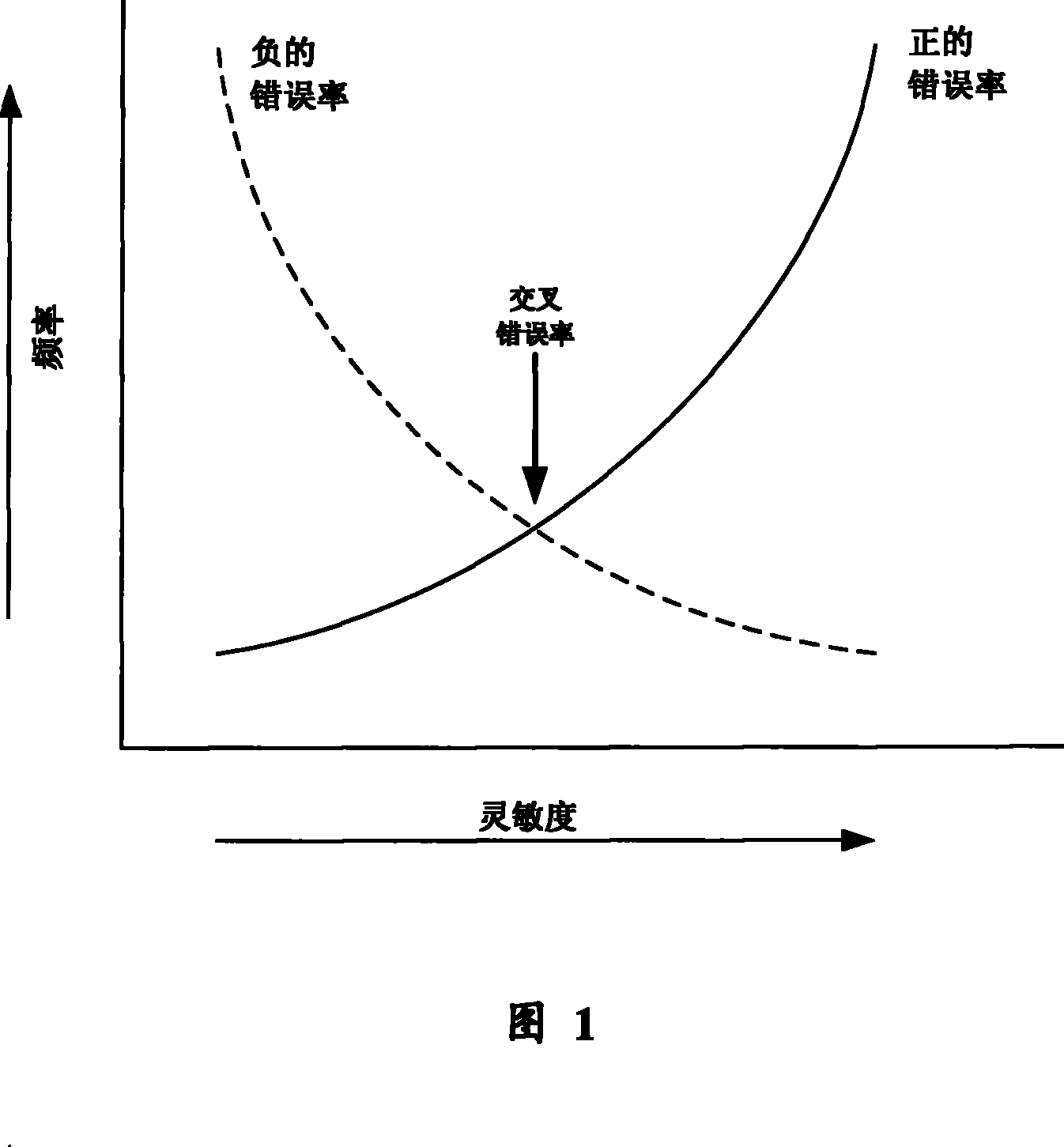
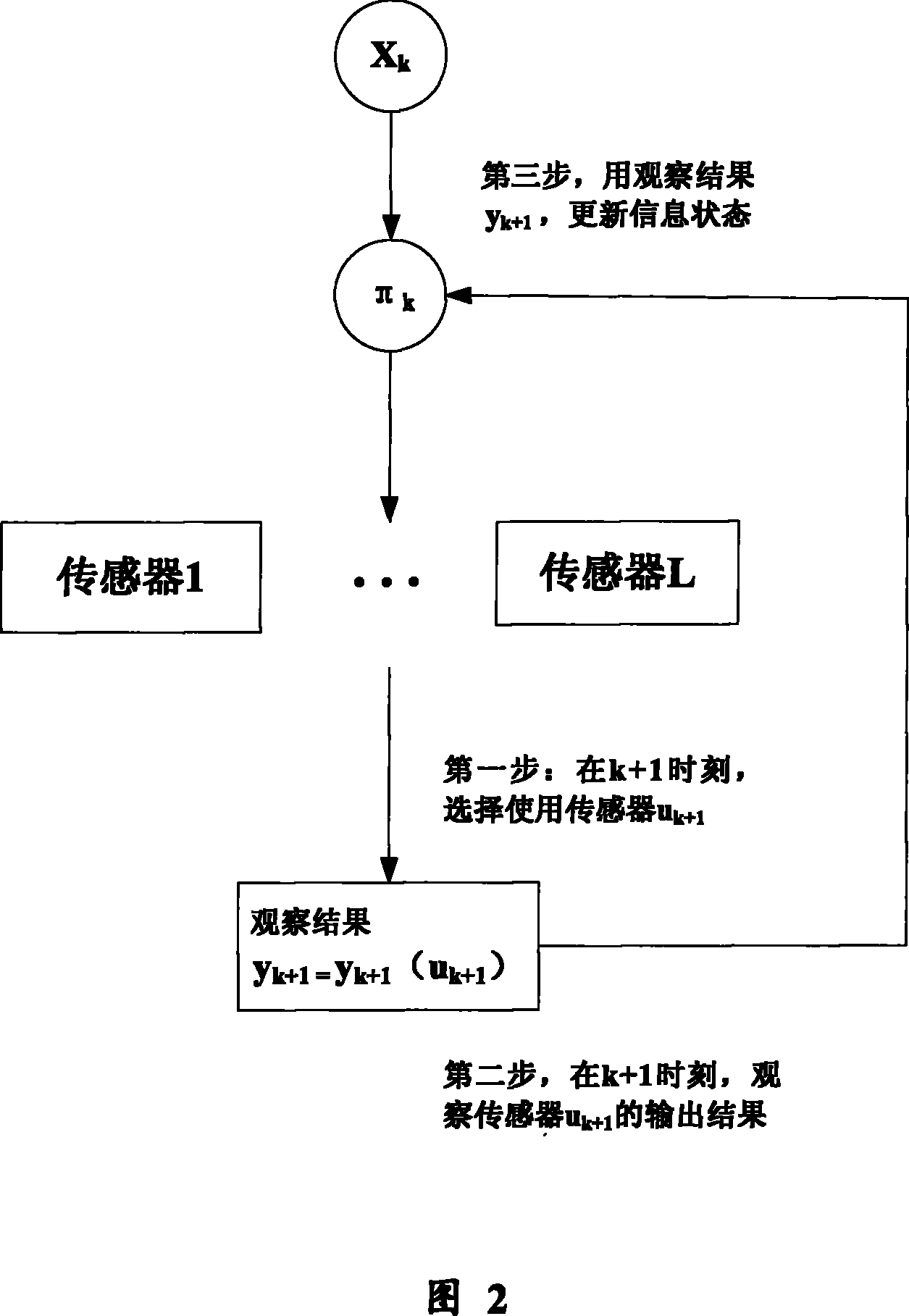
[0063] Please refer to Fig. 2, the method for implementing continuous authentication and joint intrusion detection by mobile devices in the wireless network includes several biometric authentication function modules arranged on the mobile device, the biometric authentication function modules can be biosensors, Of course, other devices with biometric feature collection and authentication functions can also be used, wherein the method includes the following steps:
[0064] (1) Establish a part of the observable Markov decision process system model according to the continuous authentication process, and determine the information state space of the system model and the information state of the system at each discrete time point, including the following steps:
[0065] (a) Determine the information state π of the system model according to the foll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com