Method for constructing network inbreak scene based on hidden Mrakov model
A hidden Markov and network intrusion technology, applied to digital transmission systems, electrical components, transmission systems, etc., can solve problems such as unrecognizable attack intentions and complicated processing processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
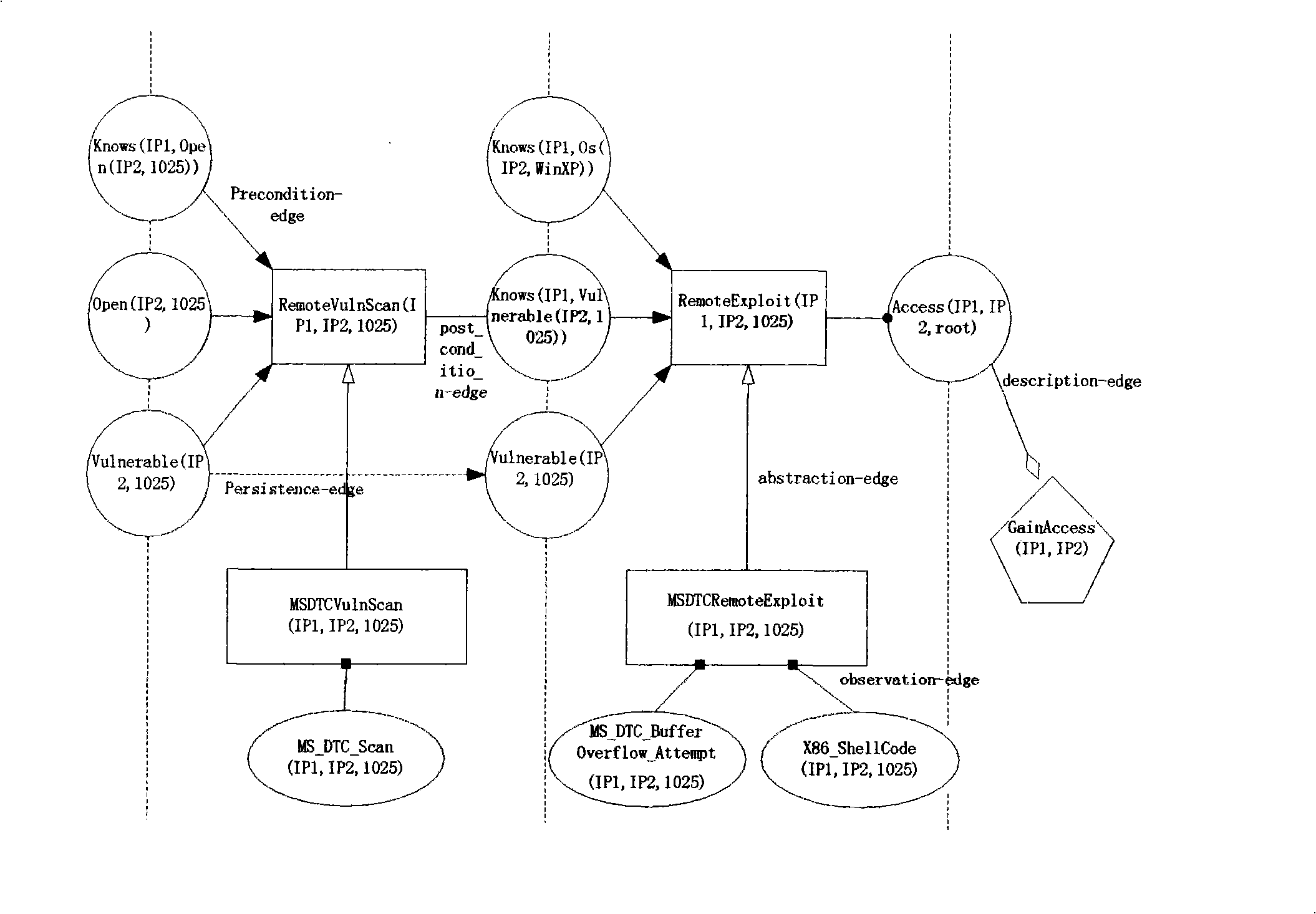
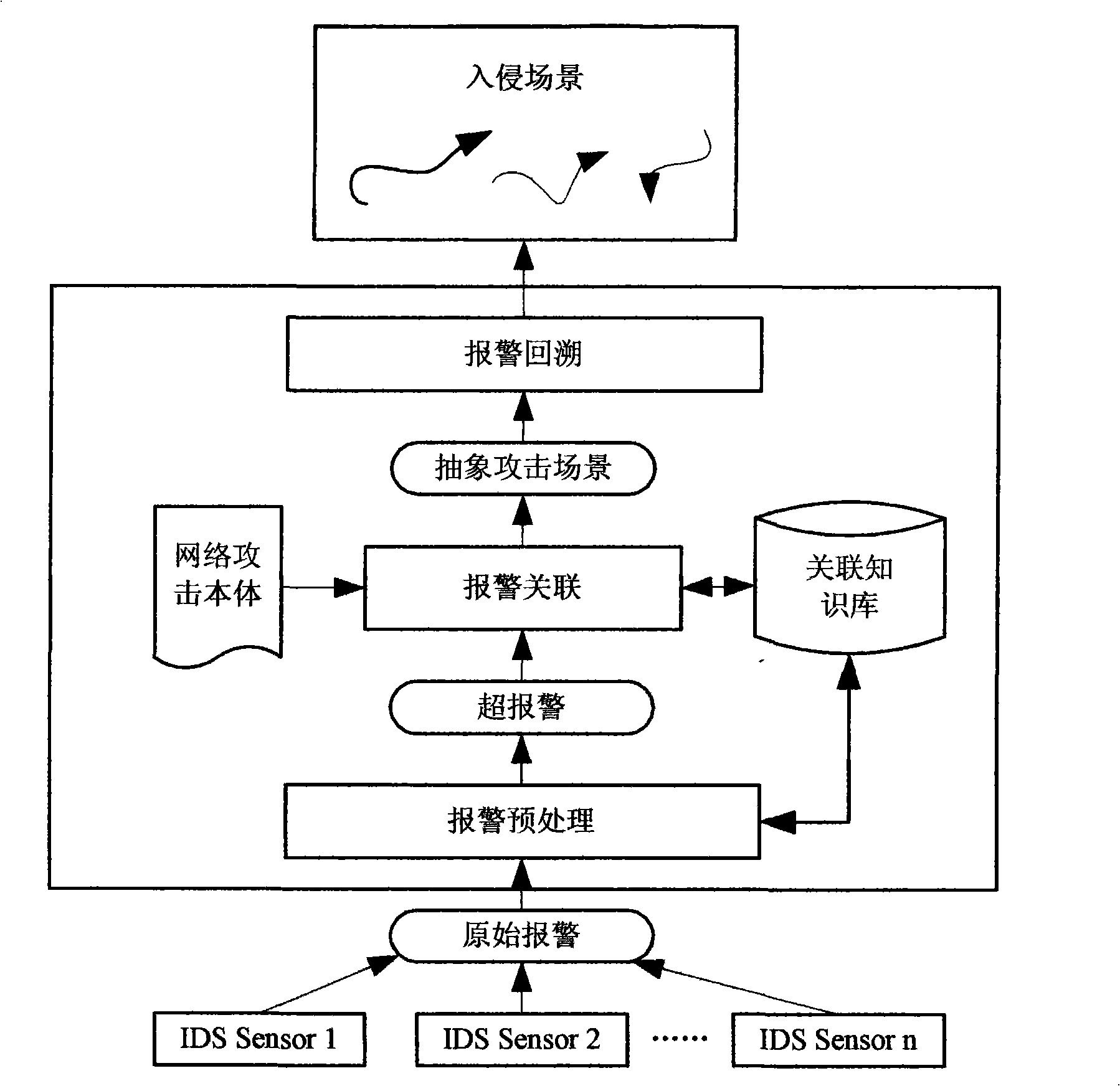
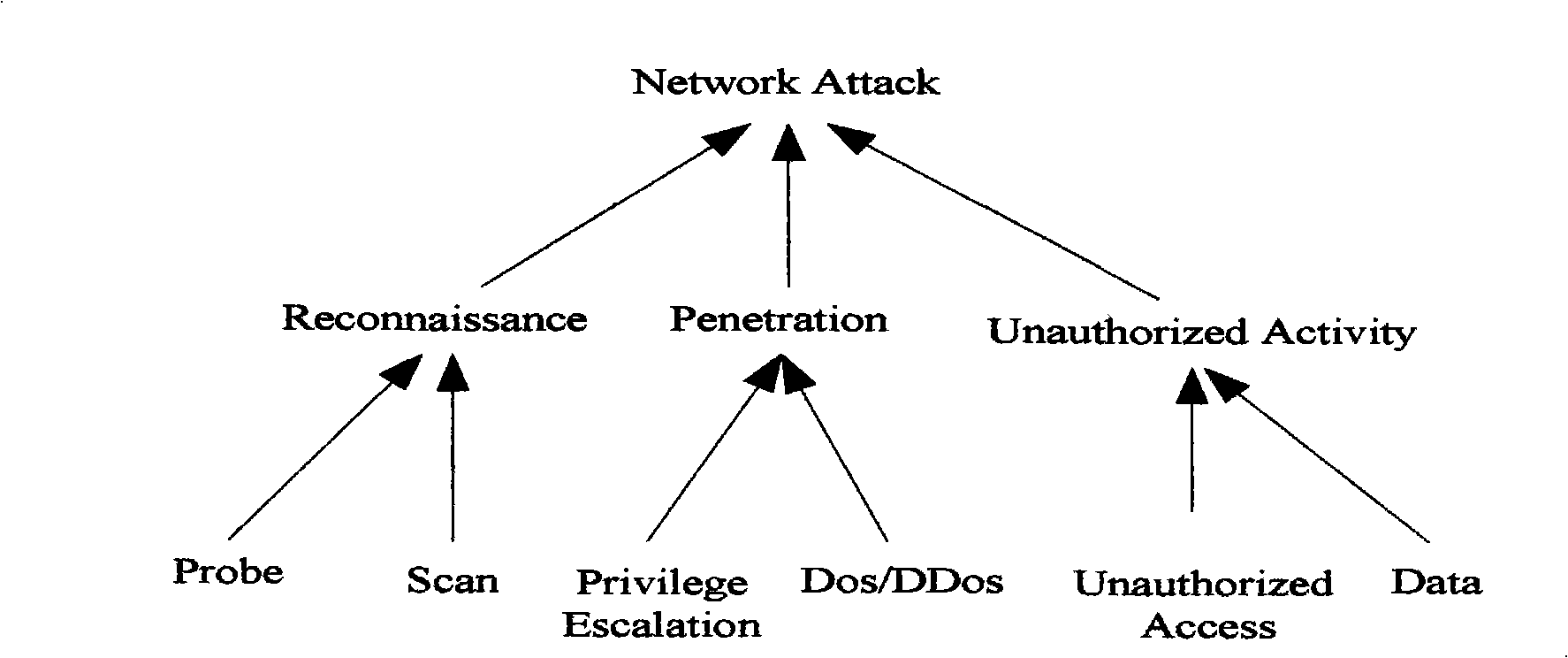
[0101] The present invention mainly includes three main steps of preprocessing of intrusion alarm data, correlation analysis of alarm data and construction of intrusion scene, such as figure 2 shown. The details are as follows:
[0102] 1. Alarm preprocessing
[0103] The present invention adopts the method of alarm aggregation to preprocess the original alarm.
[0104] In order to realize alarm aggregation, it is necessary to extract key attributes from the alarm information generated by IDS to form the original alarm. By calculating the degree of difference between the original alarms, the aggregation of similar alarms is realized, and super alarms are obtained. Since the attribute values of the original alarms are quite different and have different data types, they play different roles in determining the difference between alarm information. Therefore, different calculation methods of difference degree should be adopted for each attribute. After obtaining the degree...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com