Method for providing protected access of corresponding program
An application, protected technology, used in instruments, digital data authentication, computers, etc., to solve problems such as attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
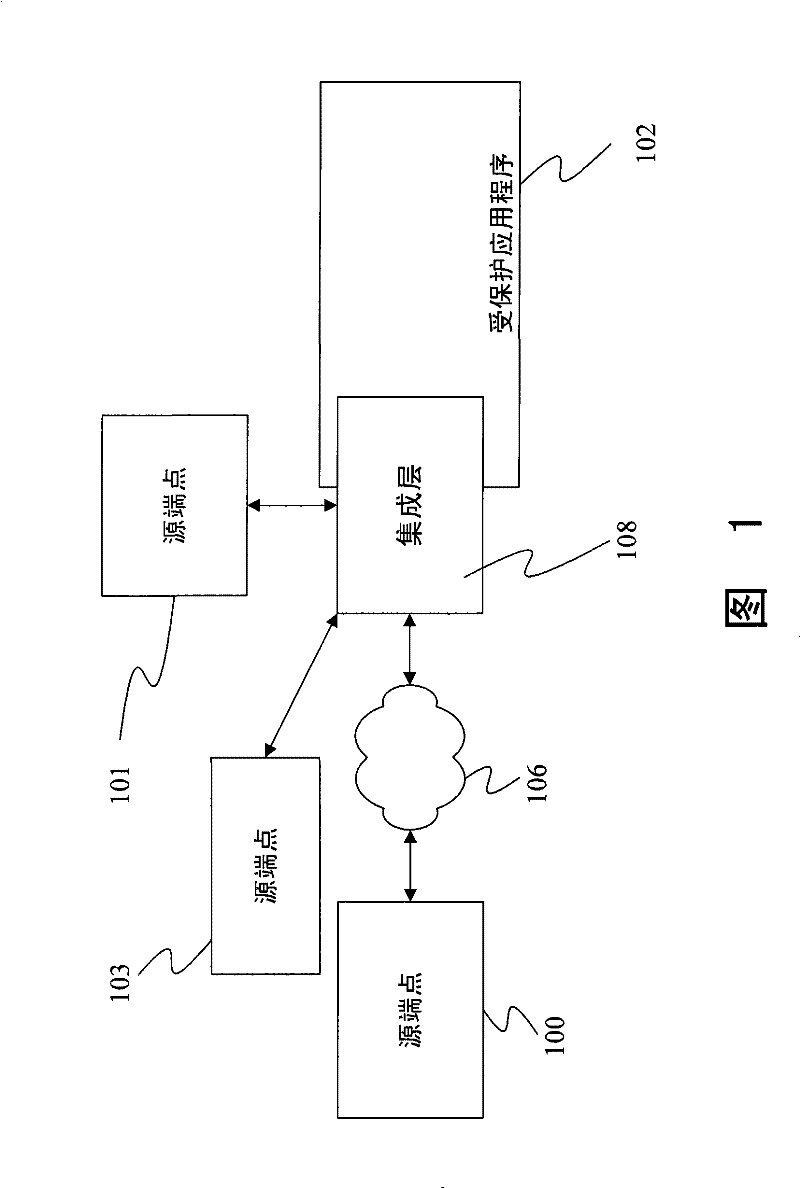
[0018] Embodiments provided herein provide a framework or model for providing protected access to applications. figure 1 Block diagrams are provided showing elements of the general interactions contemplated in the embodiments discussed below.
[0019] exist figure 1 In , an application or user located at source endpoint 100 , source endpoint 101 , or source endpoint 103 accesses protected application 102 . Source endpoints 100 and 103 are considered external endpoints because they are not trusted to provide specific information. Source endpoint 100 accesses protected application 102 through network 106 and integration layer 108 . Source endpoint 103 accesses protected application 102 through integration layer 108 . Source endpoint 101 also accesses protected application 102 through integration layer 108 , but is trusted by protected application 102 .
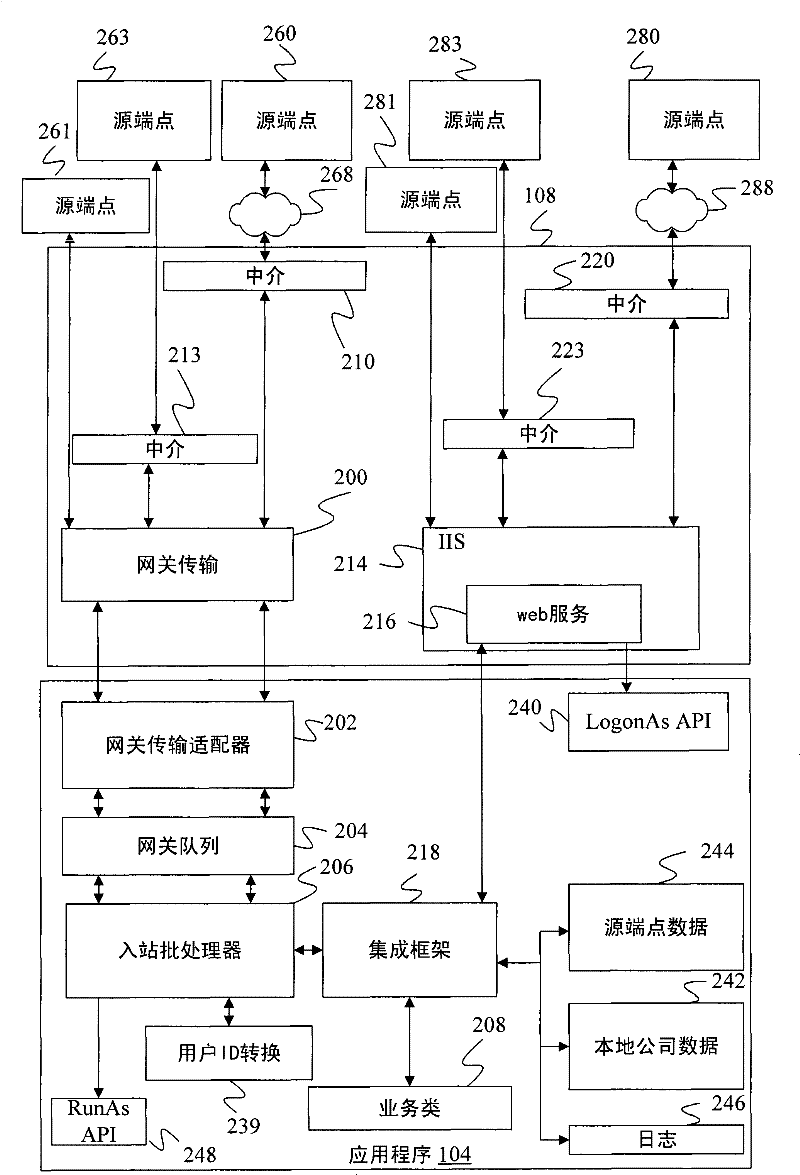
[0020] Integration layer 108 authenticates users who submit messages to integration layer 108 and passes the messages to o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com