Forgery website monitoring method and system thereof
A technology for counterfeiting websites and monitoring systems, applied in transmission systems, digital transmission systems, data exchange networks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
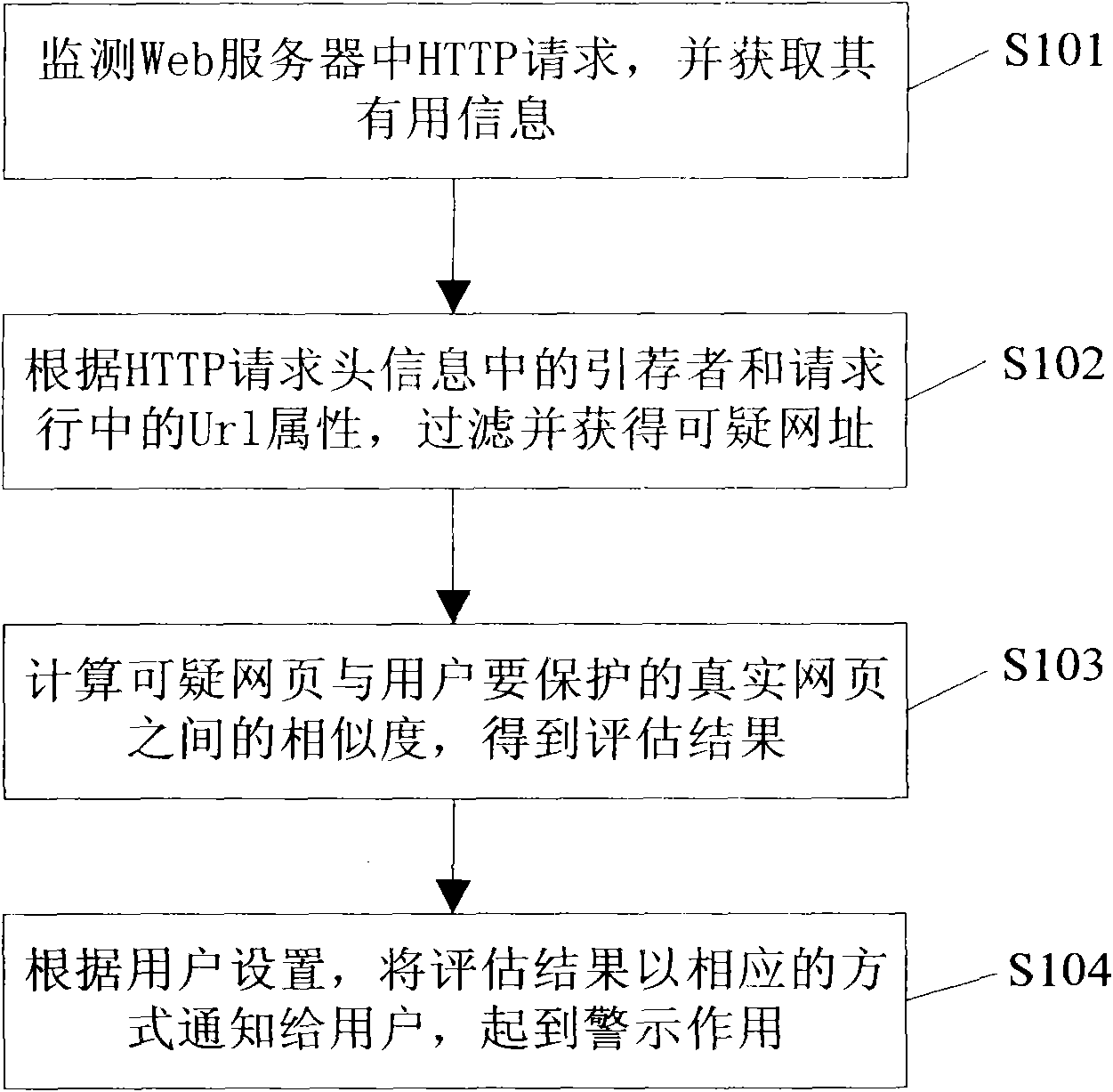
[0059] The technical solutions of the present invention will be further described in more detail in conjunction with the accompanying drawings and specific embodiments.
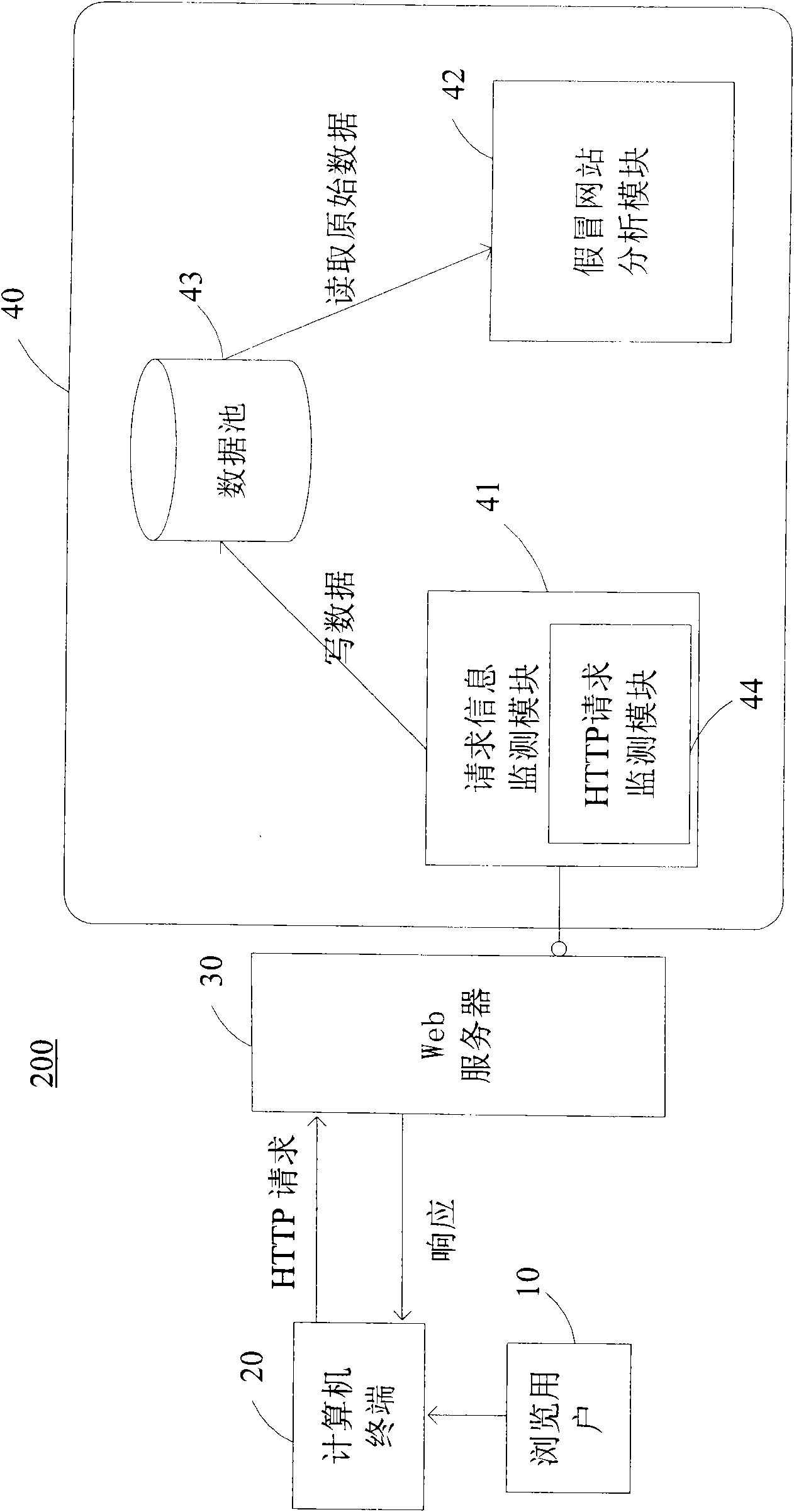
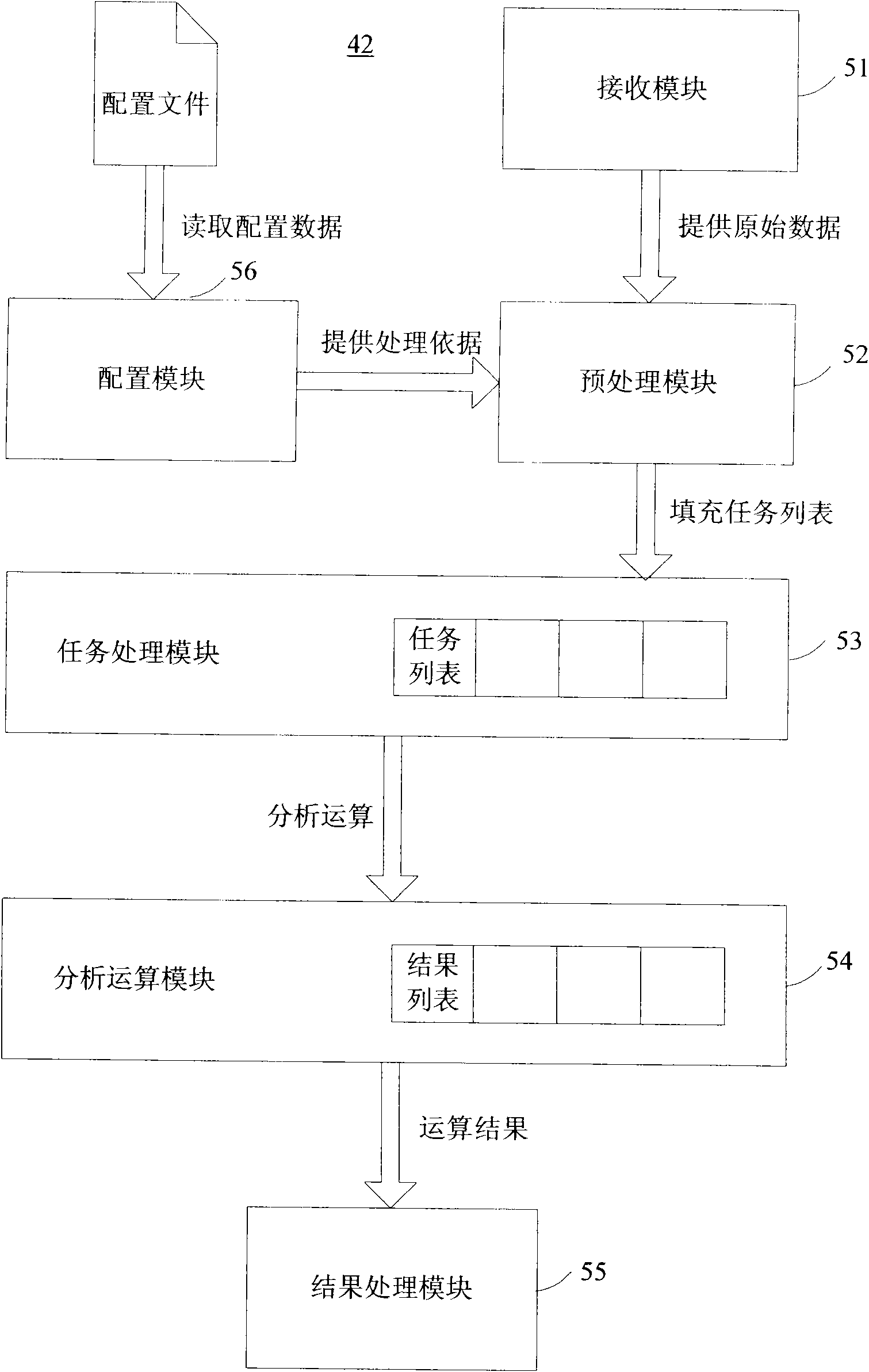
[0060] In one embodiment of the present invention, the present invention assumes that most fake websites contain many resources in real websites (which in fact is true in a large number of instances). In this way, when an Internet browsing user clicks a fake website, it will inevitably send a lot of requests (HTTP Request, referred to as HTTP in this manual) to some resources (such as LOGO pictures, user agreements, help pages, etc.) in the real website. request, including HTTP request header information), and in the request header information (header), there is an HTTP referrer (that is, HTTP Referer, which is a part of the HTTP request header information. When the browser sends a request to the Web server, it usually contains There is real referrer information, which tells the Web server the URL of the webp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com