Method and system for establishing key between nodes
An establishment method and inter-node technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as increased packet delay, complex distribution and update processes, and attacks on switching devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
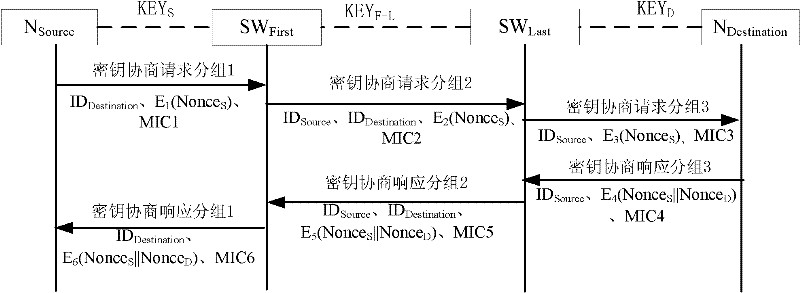
[0069] The node N (Node) defined in the present invention refers to a user terminal STA (STation) and a switching device SW (SWitch) in a local area network. Physical layer devices such as hubs in the LAN are not treated as nodes.
[0070] It is assumed that a secure connection has been established between adjacent switching devices and user terminals in the network through pre-distribution or other security mechanisms, that is, they already have a shared key; The mechanism has established a secure connection, ie already has a shared secret.
[0071] to send source node N Source with destination node N Destination Take the establishment of the key between First refers to the node from which the source node N Source to the destination node N Destination The first switching device that the data packet passes through, the switching device SW Last refers to the node from which the source node N Source to the destination node N Destination The last switching device that the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com