Wireless self-organizing network cryptographic key updating and repealing method
A wireless self-organization, network key technology, applied in the public key and key distribution of secure communication, can solve the problems of providing keys, irrevocable, unable to provide individual authentication, etc., to improve efficiency, reduce calculation and communication volume Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described in detail below in conjunction with the accompanying drawings.
[0054] The cipher used in this embodiment is an elliptic curve cipher, and the threshold cipher technology used in threshold segmentation is the polynomial threshold cipher proposed by Shamir.
[0055] In the construction phase of the entire network, there is a key initialization link, in which the password designer sets security parameters to build a trusted key center TA. And the devices participating in the initialization are divided into two types: common devices and server devices, and are initialized separately.
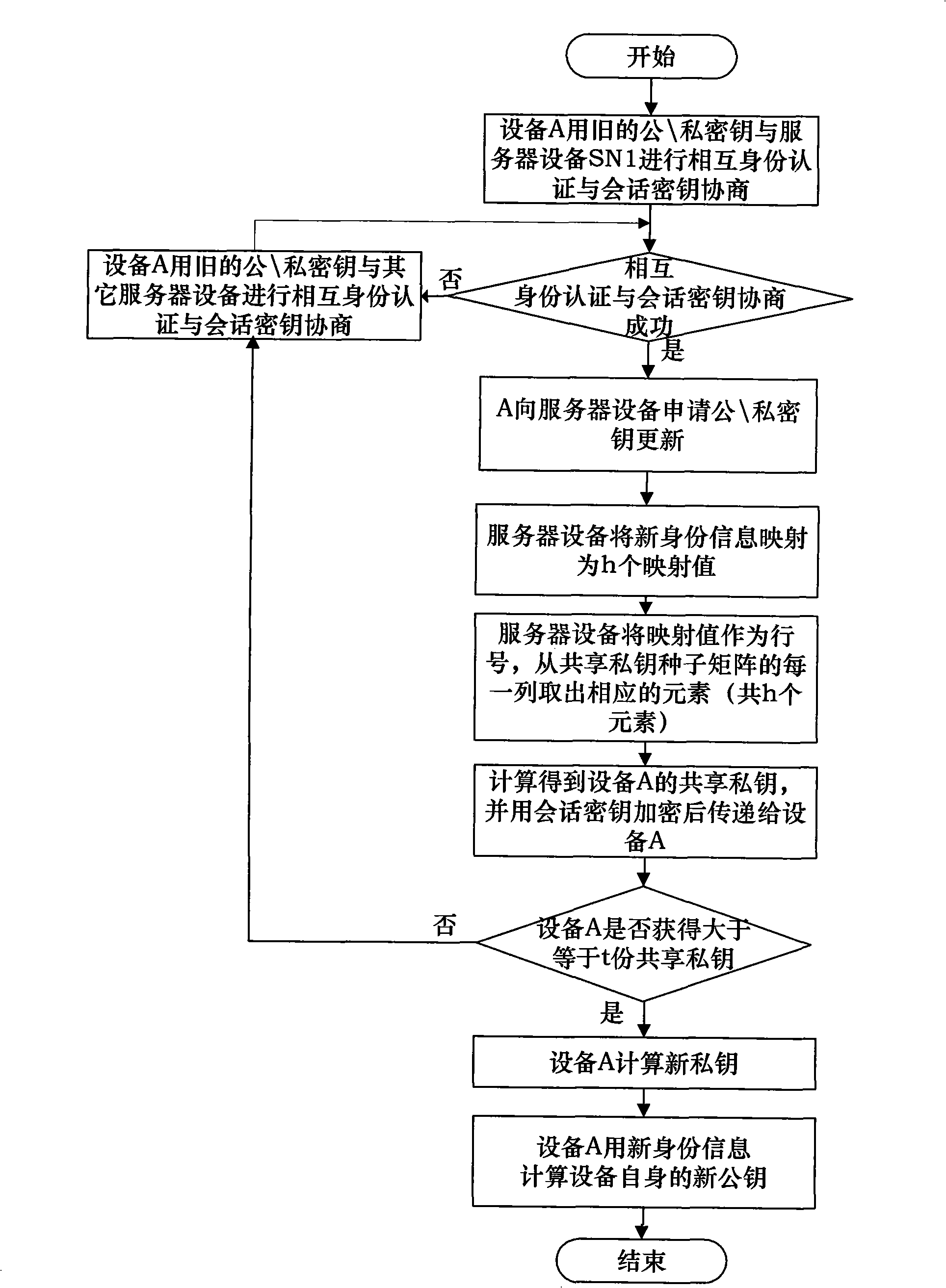
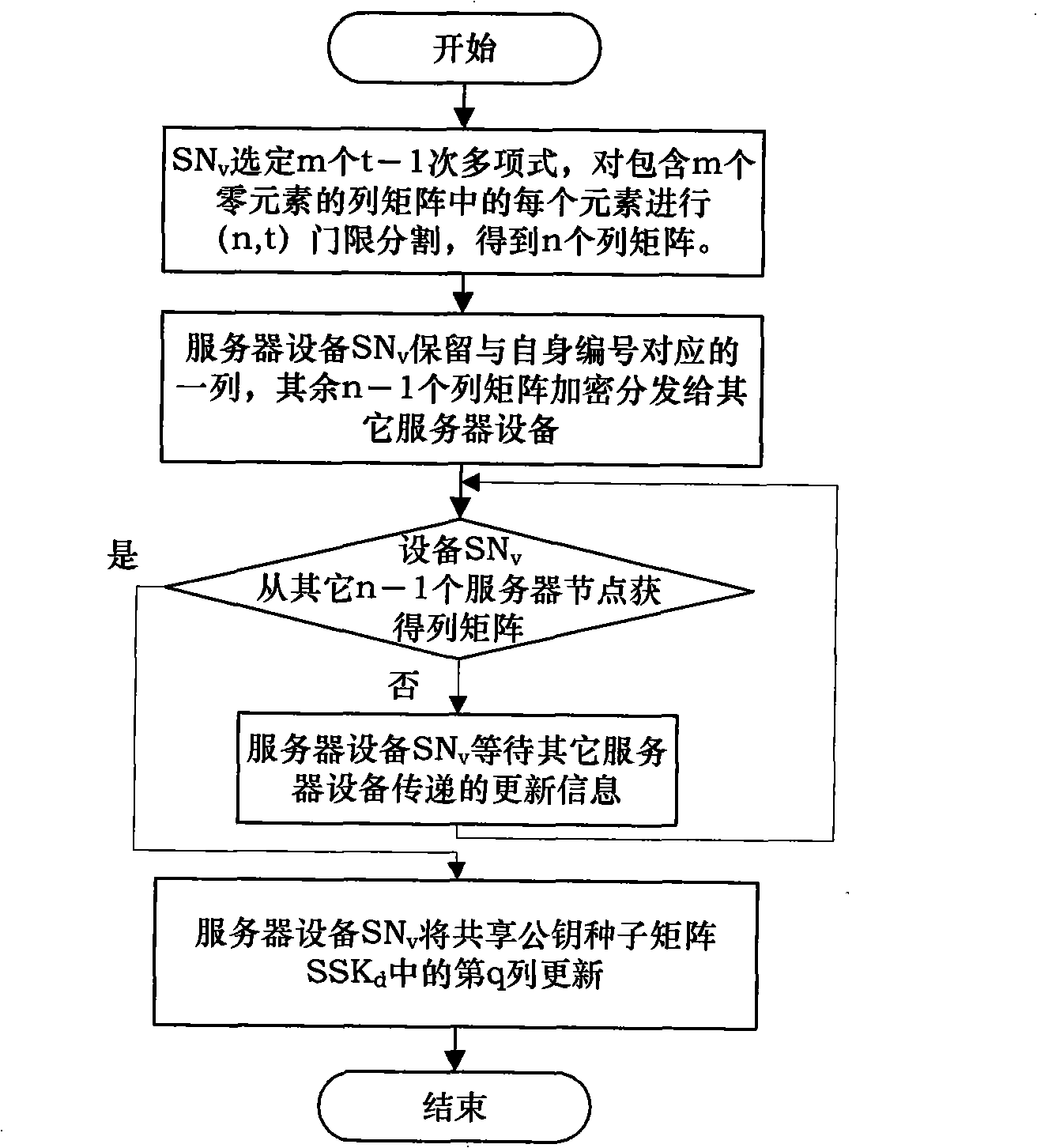
[0056] The initialization process is as figure 1 shown, including the following steps:
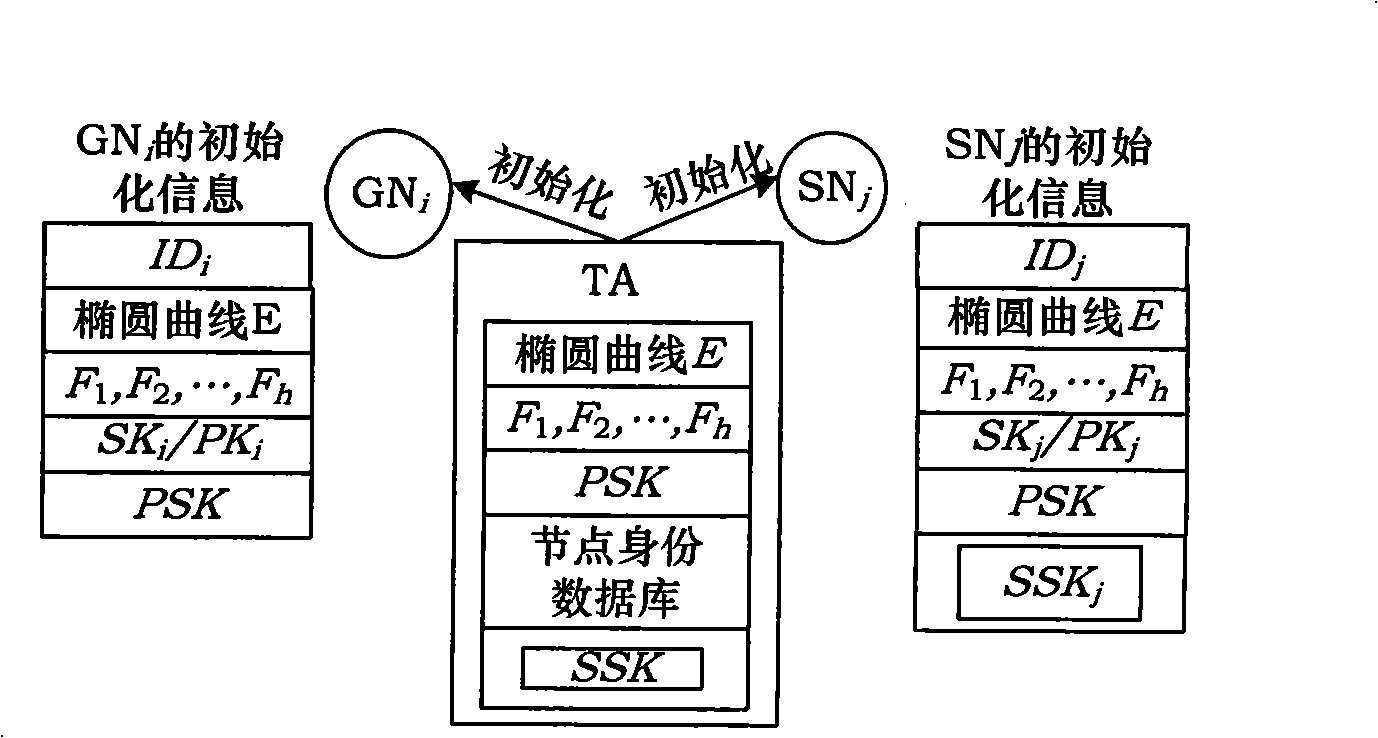
[0057] Step 1: Build a trusted key center TA, and set security parameters according to network security requirements, including: elliptic curve E, h mapping functions F 1 , F 2 ,...,F h , the private key seed matrix SSK and the public key seed matrix ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com