Authentication method without certificate duplication for users belonging to different institutions
A user and certificate technology, applied in the transmission system, electrical components, etc., can solve the problems of increased complexity of system management, difficulty in identifying connected users, and limitations of system scalability, and achieve the effect of easy scaling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
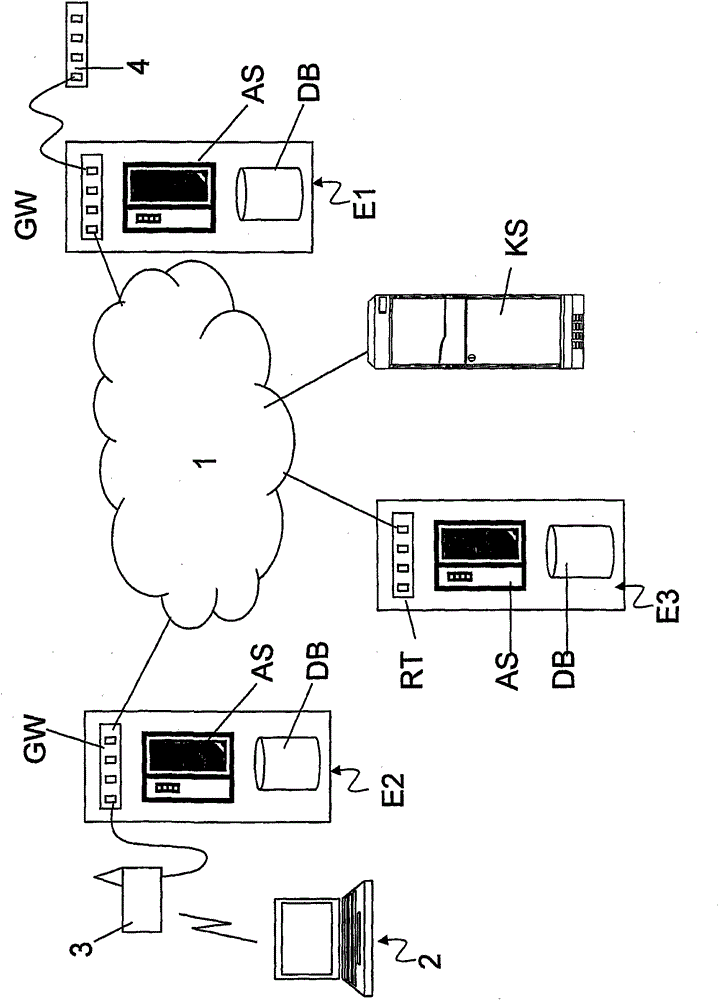
[0039] now refer to figure 1 , shows a federation of organizations (E1, E2, E3) connected to the Internet 1 .
[0040] For the purposes of this description, the term 'organization' refers to any entity that may grant users access to the Internet or operate a structured user management system.
[0041] exist figure 1 In the example of , institutions E1 and E2 are equipped with computer systems, in particular network nodes, which include a gateway GW, an authentication server AS, and a database DB containing information required by users of the authentication institutions.
[0042] The gateway GW performs all firewall functions and filters any unauthorized traffic, while the authentication server AS verifies the user's credentials in a database DB (MySQL or LDAP database, or a password file) or via standard protocols such as RADIUS.
[0043] exist figure 1 In the example of , organization E2 is equipped with access point 3, which provides users with wireless access through ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com