Encryption method of hierarchical data in hierarchical tree system
A technology of layered data and encryption methods, applied in the field of data processing, can solve the problems of launching decryption keys, affecting the network information security of enterprises and institutions, and high costs, so as to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
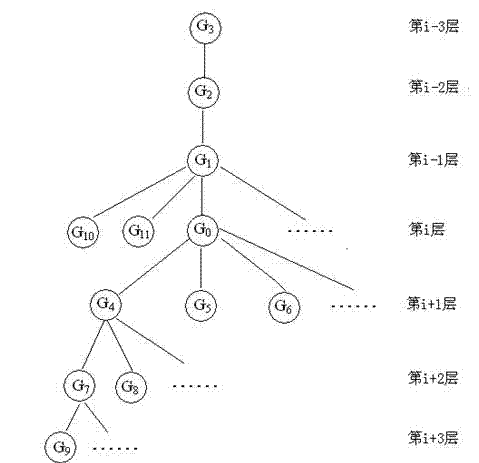
[0037] figure 1 It is a schematic diagram of a tree-like hierarchical system structure in which the group user G0 is the current user: that is, the level of G0 is the i-th layer, and the group user at the level of writing that has an affiliation relationship with G0 at the i-1 layer is G1, and at the The group users at the writing level who have affiliation relationship with G0 on the i-2 layer are G2, and the group users at the writing level who have an affiliation relationship with G0 on the i-3 layer are G3; G4, G5, G6, etc. are at the i+1th level Group users at the writing level who have affiliation relationship with G0, G7, G8, etc. are group users at the writing level who have affiliation relationship with G0 at the i+2 layer, G9, etc. have affiliation relationship with G0 at the i+3 layer Group users at the writing level, G10, G11, etc. are writing-level users that have a common affiliation with the same layer as G0.
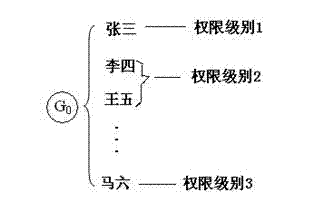
[0038] figure 2 It is a schematic diagram of the...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap