Identification of a manipulated or defect base station during handover
A flawed, base station technology, applied in security devices, electrical components, transmission systems, etc., can solve problems such as inability to detect sequences, increase UE complexity, etc., and achieve high-granularity effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
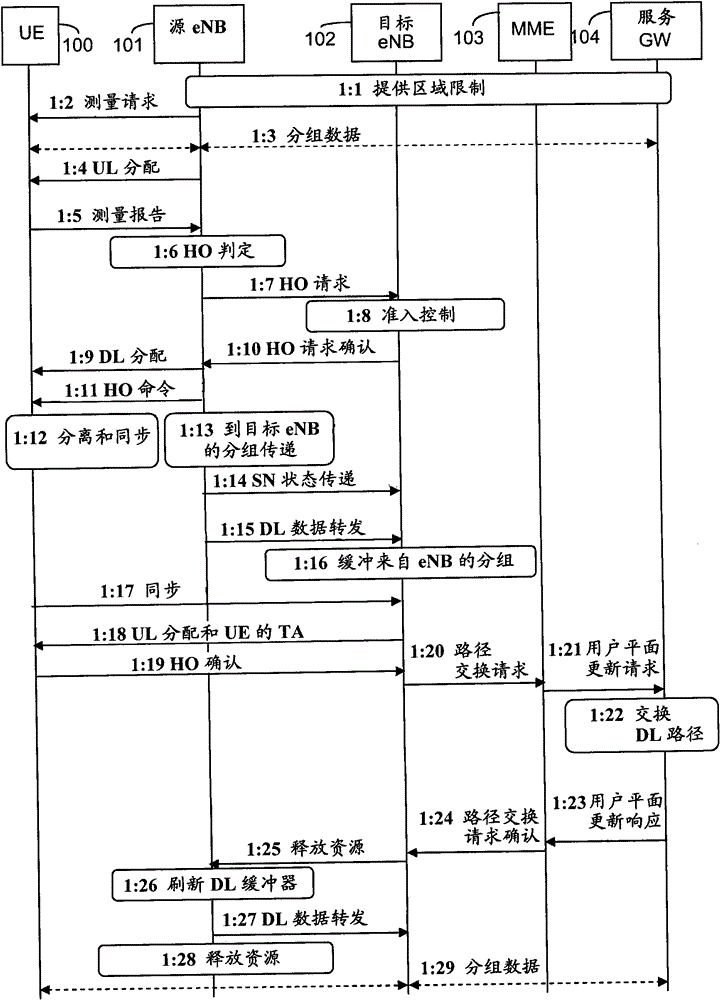
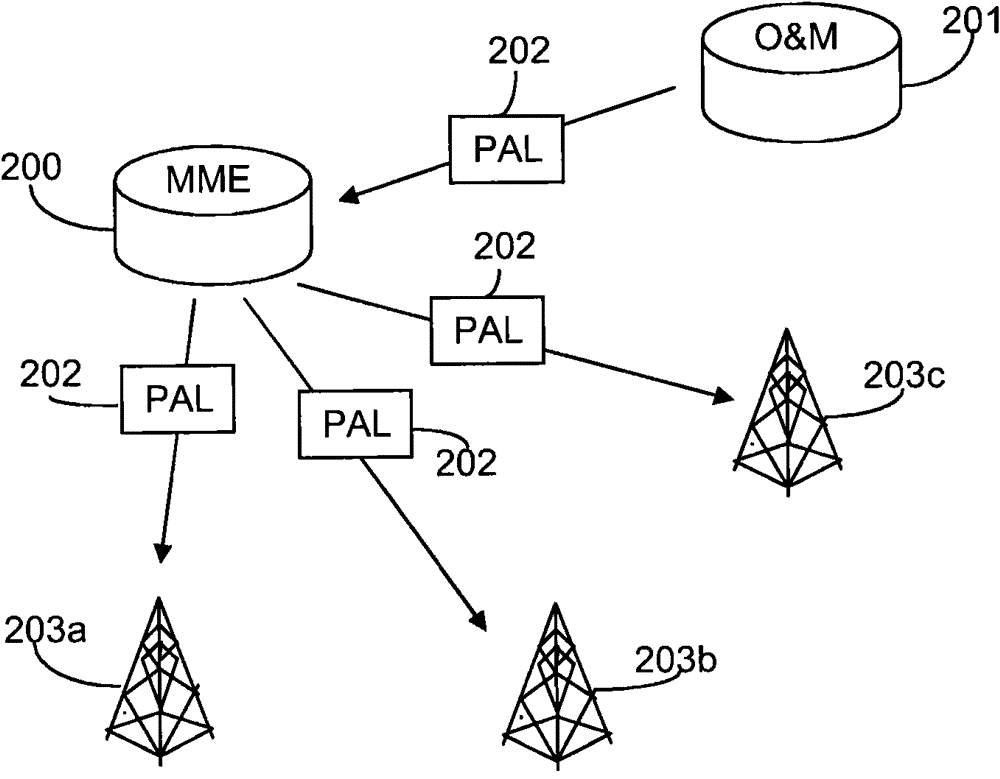
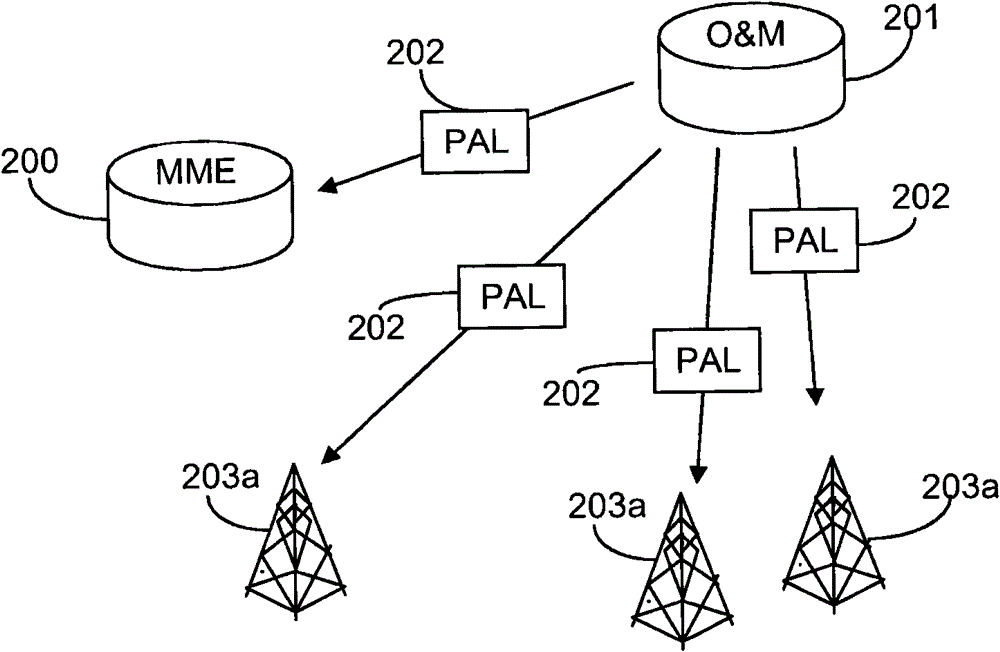
[0052] Briefly, the present invention relates to a method for detecting manipulated or defective base stations during a handover procedure. The invention also relates to a core network node suitable for carrying out the proposed method and a base station suitable for helping to carry out the proposed method. It is to be noted that even though the description herein is provided in the context of E-UTRAN, it is equally applicable where a central network node provides a set of algorithm choices to any kind of radio base station, thereby selecting one or more of the algorithms for protecting them Any system on the link with the UE. Therefore, the following E-UTRAN context should only be considered as an illustrative example of one application of the proposed invention. In particular, it is to be noted that the specific messages mentioned in the example of passing information between entities involved in handover are considered to be exemplary examples only, and thus other alterna...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com