Security terminal system and authentication and interruption method thereof
A terminal system and security terminal technology, applied in the field of information and data security terminal systems, can solve problems such as hidden dangers of terminal system security by encryption means
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
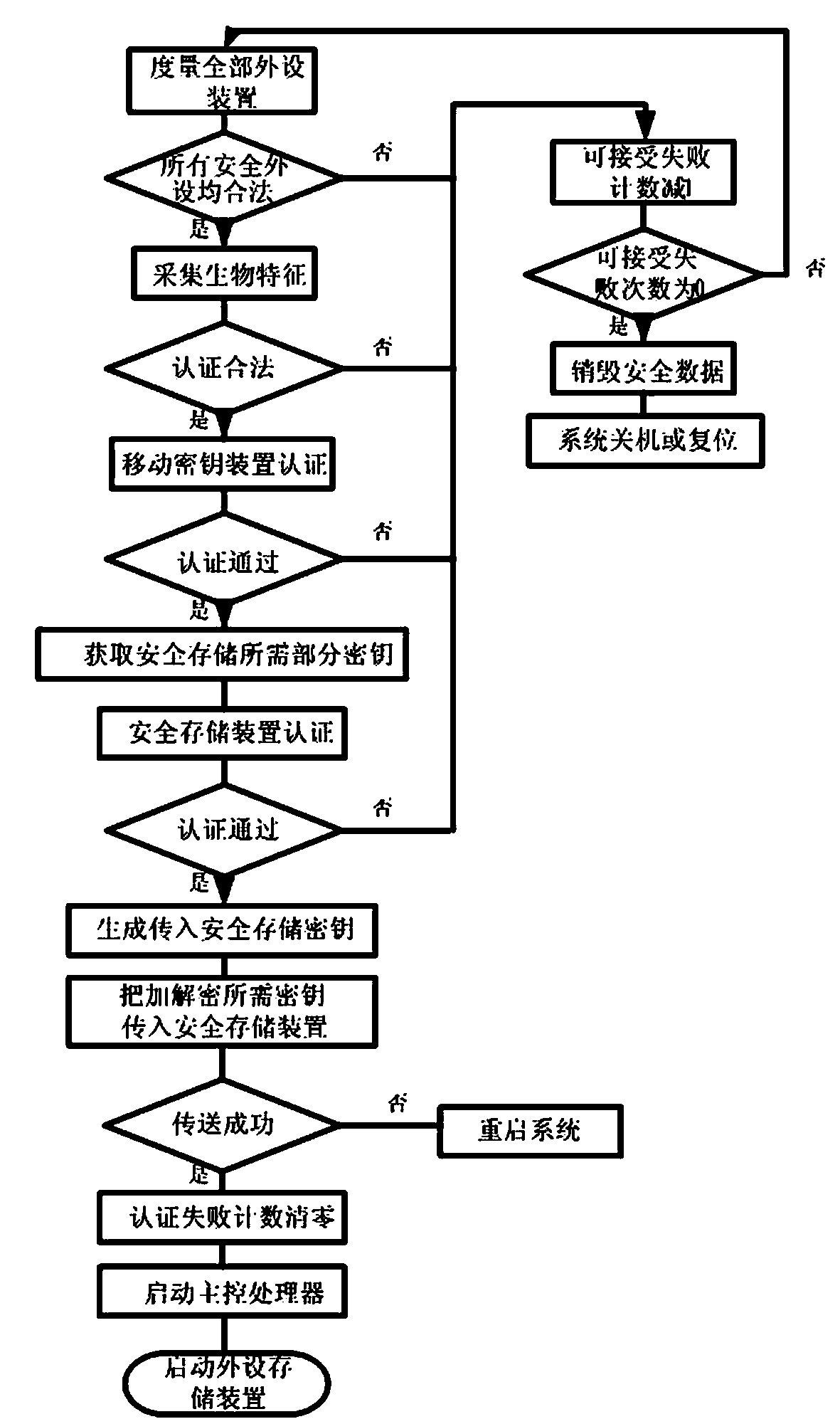
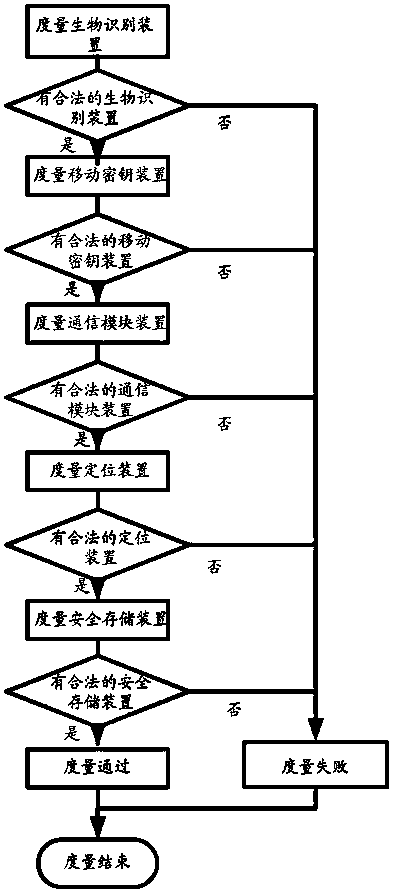
[0044] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
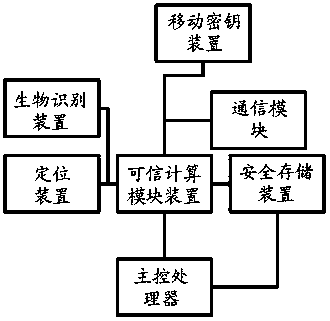
[0045] like figure 1 A secure terminal system shown includes a trusted computing module device, a biometric identification device, a mobile key device, a safe storage device, a positioning device, a communication module and a main control processor.
[0046] The biometric identification device is used to collect biometric features and input identification data to the trusted computing module device;
[0047] The mobile key device is used to send the key to the trusted computing module device;
[0048] The secure storage device stores data, and obtains encryption and decryption keys from the trusted computing module device;
[0049] The positioning device is used to obtain the current geographic location informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com