Static state detecting system based on XML (Extensive Makeup Language) middle model and defect mode matching
A static detection and intermediate model technology, applied in software testing/debugging, etc., can solve problems such as the inability to guarantee the discovery of software security vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
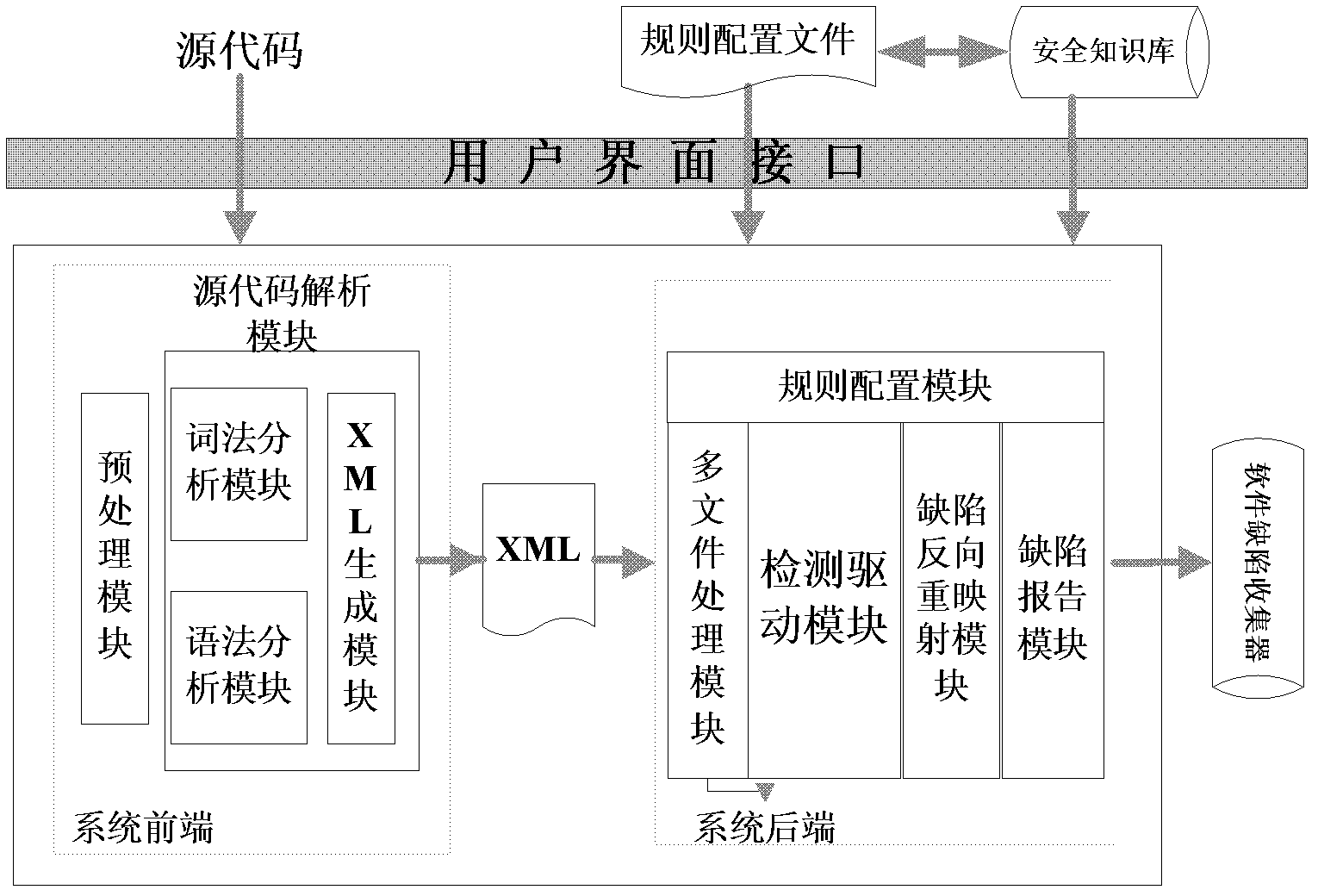
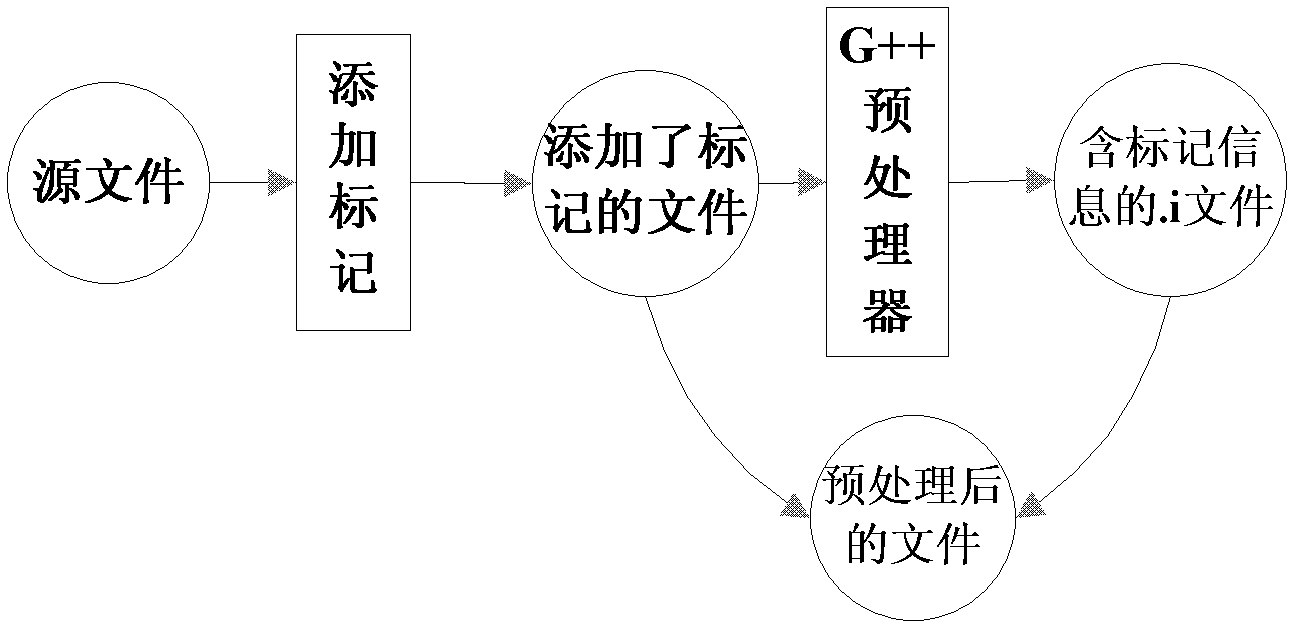
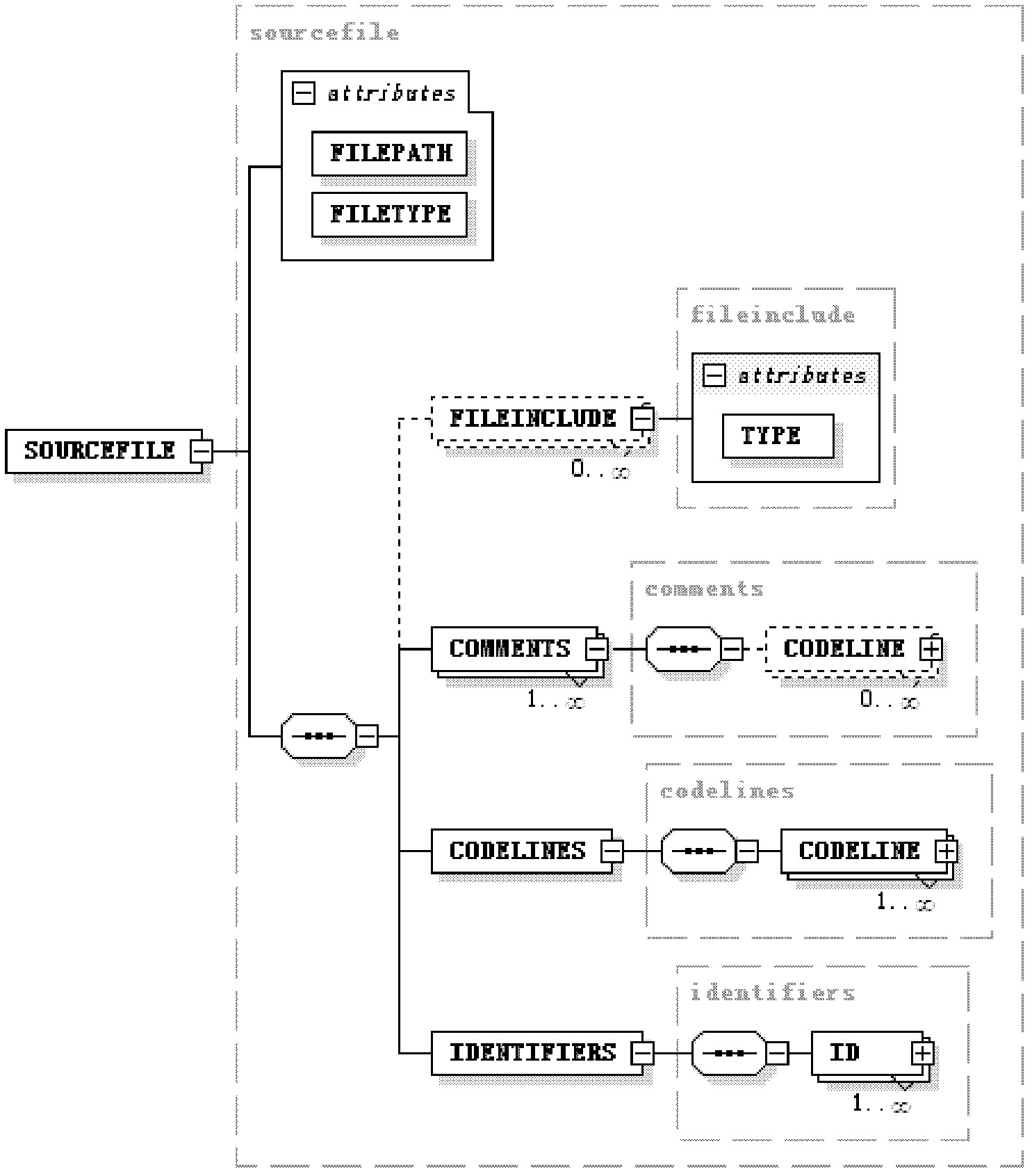
[0089] The specific implementation manner of the present invention will be described in detail below in combination with the technical scheme and accompanying drawings.
[0090] Algorithm 1 below describes the generation process of the syntax tree.
[0091] Algorithm 1.
[0092] Input: CFG G=(V N , VT , S, P) and statement flow Statements=s 1 the s 2 ...s n , where s i = t 1i t 2i ...t mi .
[0093] Output: Tree id and Tree stmt
[0094] Process: RST ree (G,s)
[0095] 1 begins
[0096] 2
[0097] 3 procedure CreateStmt{construct Stmt tree}
[0098] 4 for i:=1 to n do
[0099] 5 procedure CreateId{construct Id tree}
[0100] 6 for j:=1 to m do
[0101] 7 begin / * begin of CreateId * /
[0102] 8 on current state P k :=y , d), Tree stmt (s i-1 , h)>
[0103] 9 gettoken;
[0104] 10 if d≠h then
[0105] 11 d=h;
[0106] 12 if X∈V N then
[0107] 13 goto P h (P h ∈P, h≠k): =id (t y , d), Tree stmt (s i-1 , h)>
[0108] 14 else if X∈V T ’ ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com