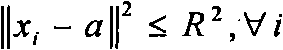User authentication method based on keystroke mode identification
A technology of user authentication and pattern recognition, applied in the field of pattern recognition, can solve problems such as hidden dangers of security and easy leakage of passwords, and achieve the effect of improving security performance and good recognition effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
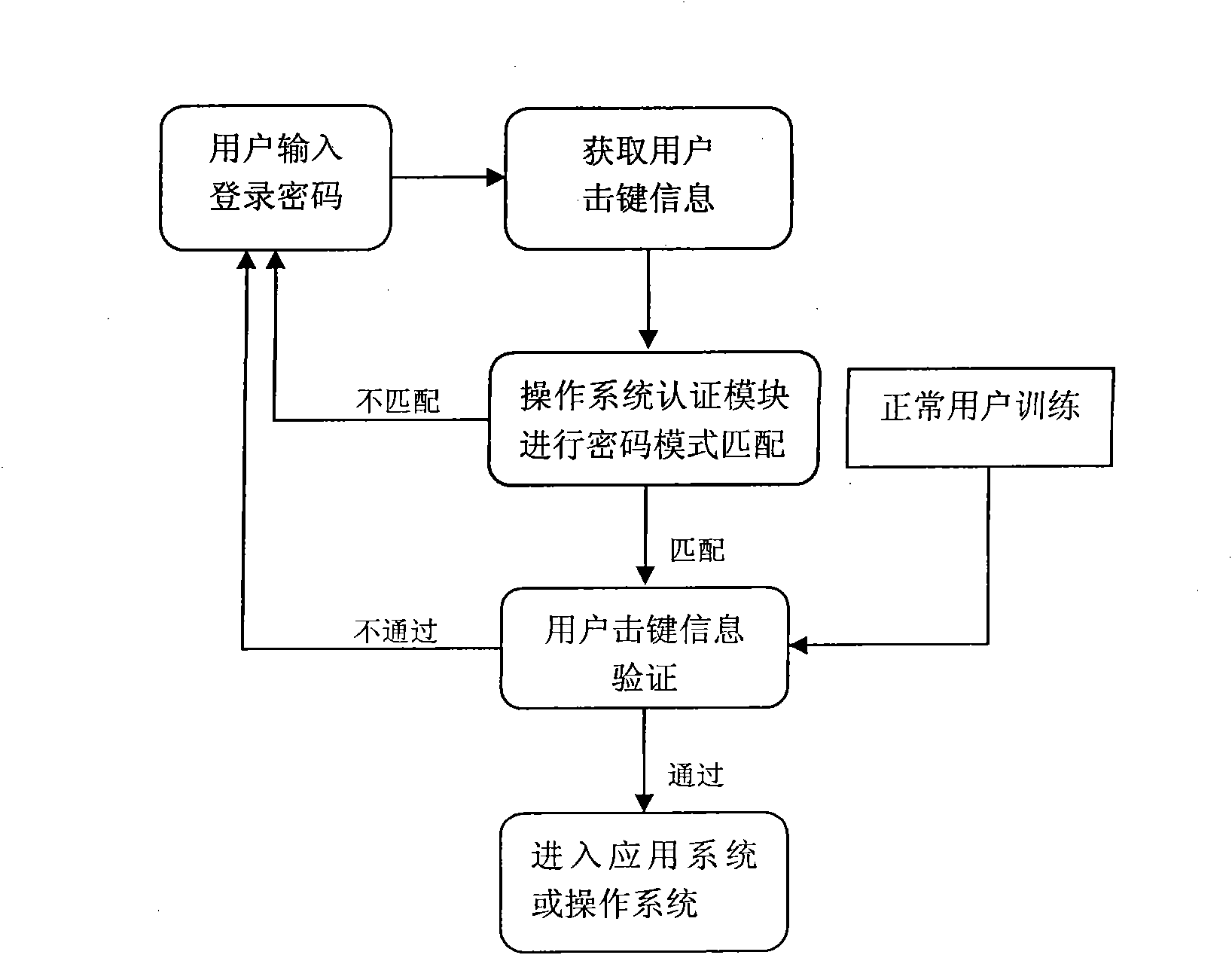
[0017] combine figure 1 , the present invention is based on the user authentication technology of keystroke pattern recognition, and the steps are as follows:
[0018] In the first step, normal users first perform keystroke training.
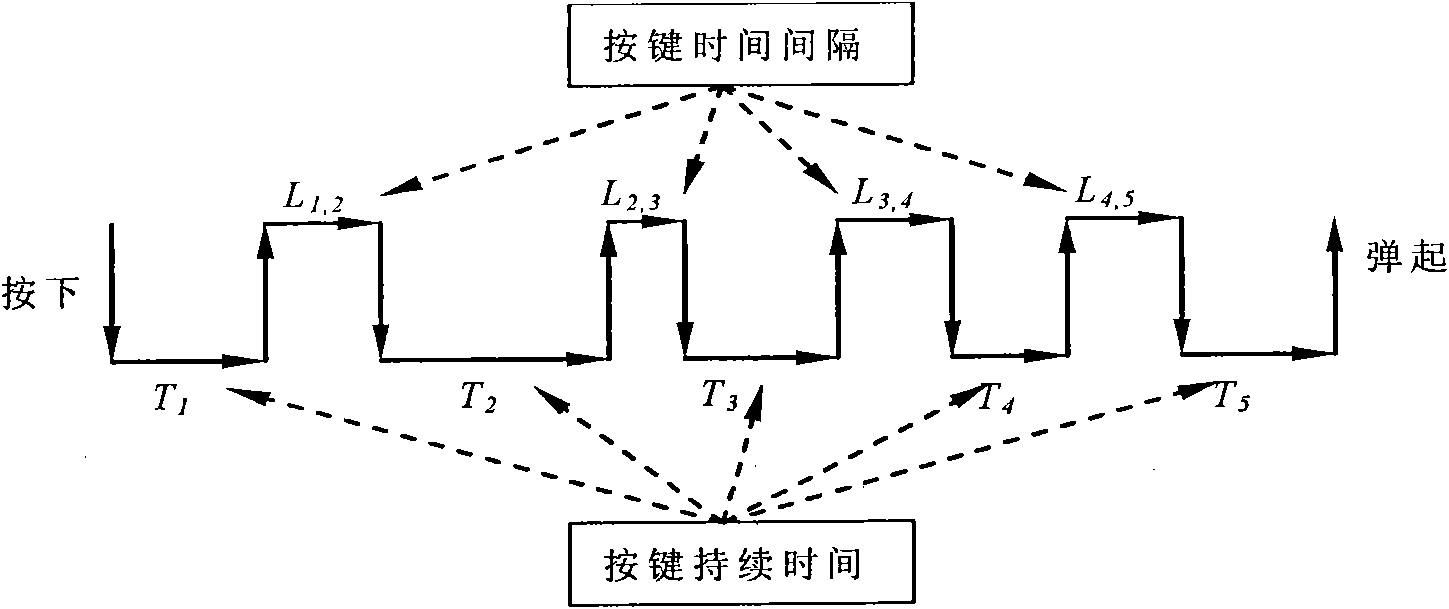
[0019] (a) extracting the keystroke characteristic features of the user according to the keypress duration and keypress time interval, figure 2 The keystroke characteristic feature extraction method diagram, the keystroke duration reflects the pressure characteristics of the user when the keystroke is pressed, and the keystroke time interval reflects the flexibility of the user to switch between different keys.
[0020] The final keystroke pattern is a vector of length 2n-1 composed of , where n is the password length. Due to the speed of the user's keystrokes, the subsequent keystrokes may be pressed before the previous keystrokes are up, so in this feature, Li, i+1 (i=1...n-1) may be negative value.
[0021] (b) Using a single-class class...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com