Method and device for firewall policy control
A firewall policy and firewall technology, applied in the field of data communication, can solve the problems that the firewall finds the security domain, cannot carry out policy control and deep security processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
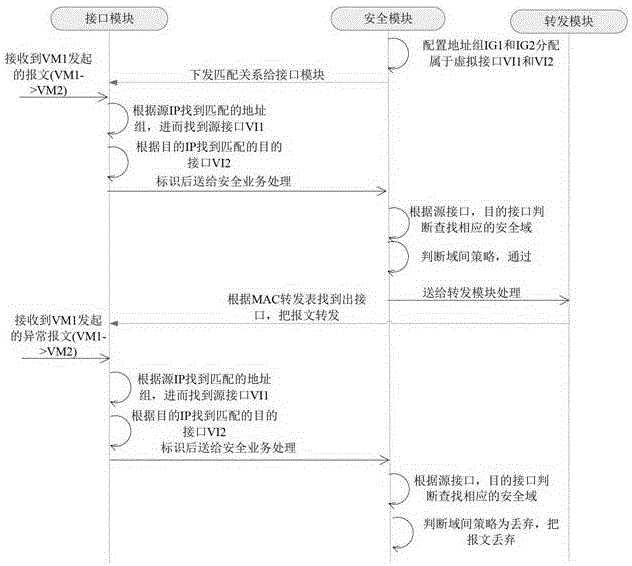
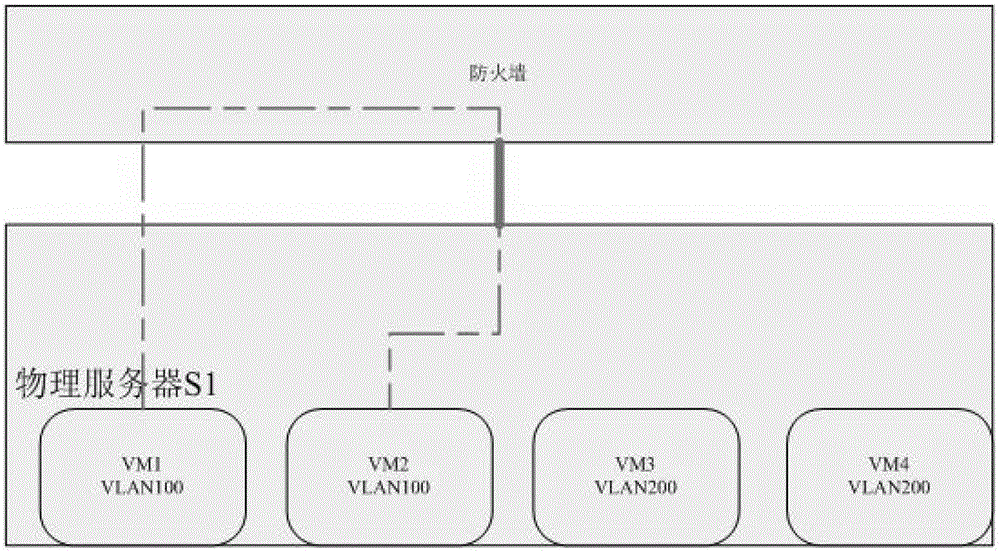
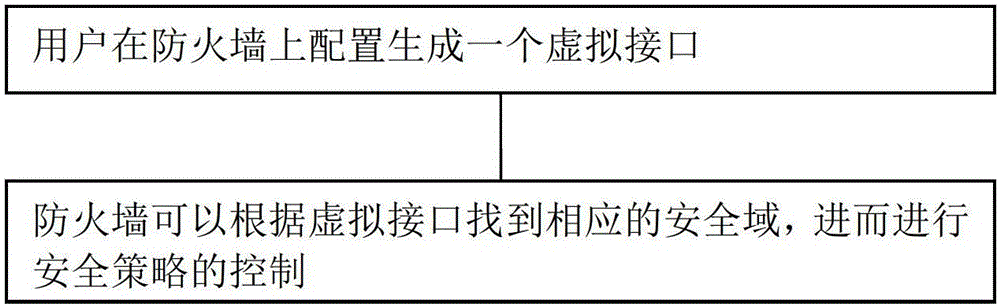
[0018] In order to achieve the purpose of the present invention, the core idea adopted by the present invention is: firstly receive the configuration of the user, and generate a virtual interface on the firewall, which is only used to mark the incoming interface and outgoing interface of the message, but does not participate in the actual message Forward the text and add the virtual interface to the security zone. Further, the virtual interface includes an IP-based address group or a MAC address group. The address group is used to determine the source and destination addresses of the message. When the source address of the message is within the address group range, the incoming interface is changed to the virtual interface, and the destination address of the message is an address within the address group range. , change the packet outbound interface to a virtual interface, and find the corresponding security domain through the virtual interface, so as to realize the firewall p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com