Cognitive radio fairness scheduling method and system
A cognitive radio and fairness technology, applied in wireless communication, electrical components, etc., can solve problems such as high number of collisions and affecting communication quality of unauthorized users, so as to reduce serious impact, reflect fairness, and improve communication service quality Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
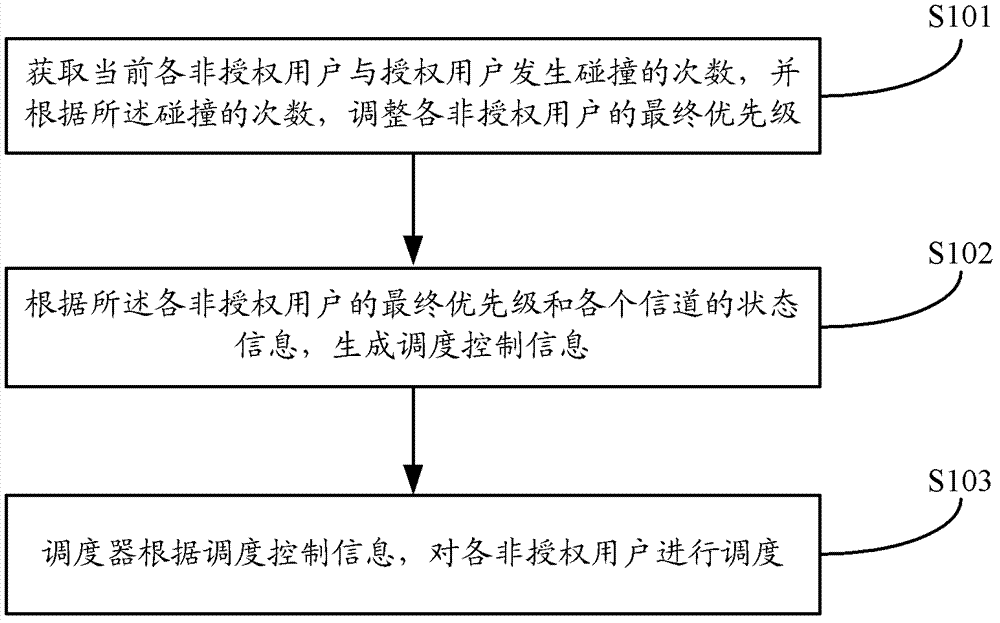
[0075] Taking the number of channels N=6 and the priority determination module working in mode 1 as an example, the scheduling process of the central spectrum management device C for unlicensed users with the same priority is described in detail based on the existing scheduling algorithm to further refine the scheduling priority process .
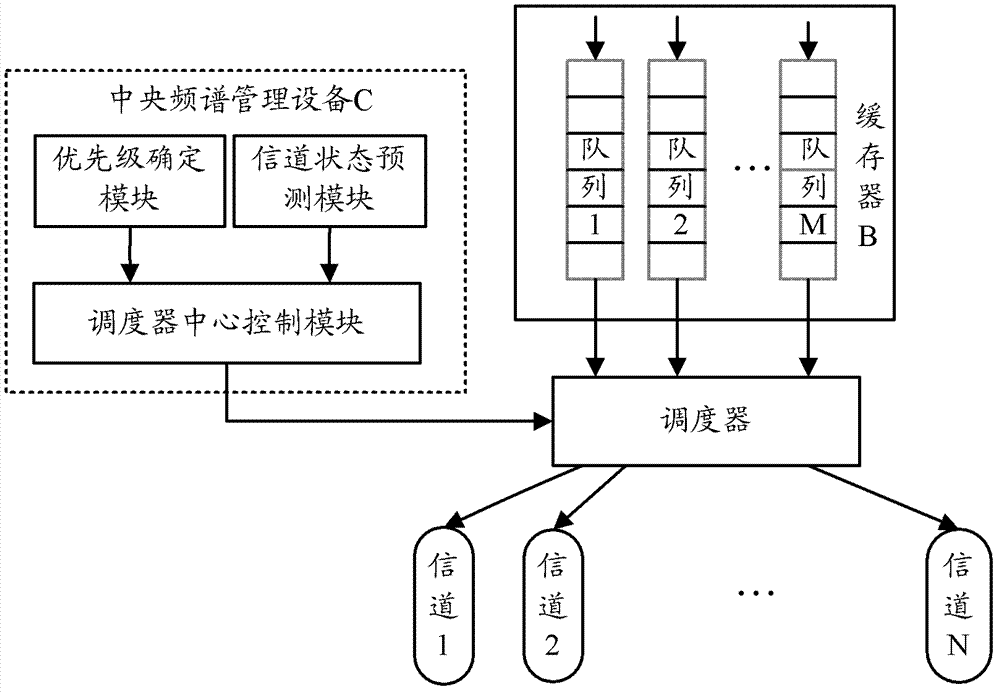
[0076] Assume that before scheduling, there are six unauthorized users b1, b2, b3, b4, b5, and b6 in buffer B, among which b5 and b6 are waiting users and are accessing the main user channel. These six unauthorized users correspond to queues 1, 2, 3, 4, 5, and 6 respectively, and the number of collisions carried by them are 1, 5, 4, 0, 0, and 0 respectively.
[0077] Its channel state and the state of buffer B are as follows Figure 4 And as shown in Table 1:
[0078] Table 1
[0079] channel number
state
user
Cumulative number of collisions
1
1
p1
-
2
2
b4
0
...
Embodiment 2
[0090] This embodiment is an example of joint application with other scheduling algorithms, that is, other scheduling algorithms set initial scheduling priorities for each unauthorized user. In this case, it is a specific example of combining with the solution of the present invention.
[0091] According to the existing scheduling algorithm, if there are 8 unauthorized users b1, b2, b3, b4, b5, b6, b7, b8, the initial scheduling priorities are 1, 2, 3, 3, 5, 6, 6, 8. Among them, b3 and b4 belong to priority 3, and b6 and b7 belong to priority 5.
[0092] Consider the results of the original scheduling algorithm and the number of collisions as the results of scheduling considerations for weighting, and determine the weights of the two according to the status quo of the system. If the collision problem is serious, for example, the number of collisions between unauthorized users and authorized users is greater than the set threshold, the weight corresponding to the initial schedu...
Embodiment 3
[0100] Same as the second embodiment, this embodiment is also another example of joint application with other scheduling algorithms.
[0101] When the collision between unauthorized users and authorized users is not serious, for example, the number of collisions between unauthorized users and authorized users is less than the set threshold, then the weight corresponding to the initial scheduling priority is set to be greater than the weight corresponding to the adjusted priority. That is: the interruption probability of the unauthorized user caused by the collision is very low (such as only 0.05), according to the method in the second embodiment of the method, the weight of the result of setting the number of collisions as the scheduling consideration factor can be set smaller, such as 0.3, Correspondingly, the priority weight of the original scheduling algorithm is 0.7. Other conditions are consistent with method embodiment two, then can obtain the scheduling result as shown ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com