User-centered mobile internet identity managing and identifying method
A mobile Internet and identity management technology, applied in the field of mobile Internet identity management and authentication, can solve problems such as phishing attacks, password fatigue, and low efficiency of password input, and achieve the effect of preventing phishing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The technical solution of the present invention will be described in detail below in conjunction with the drawings and embodiments.
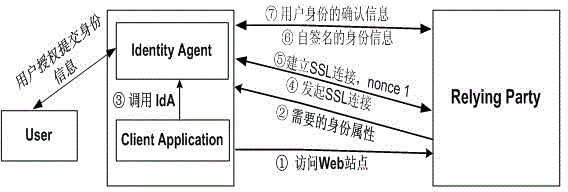
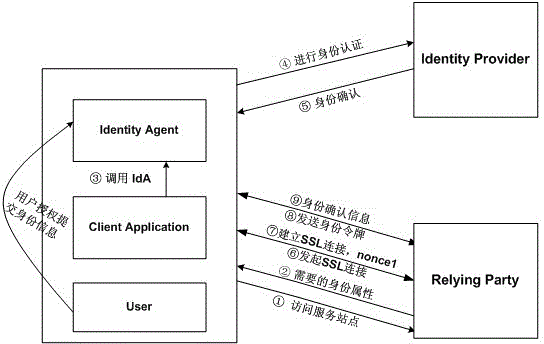
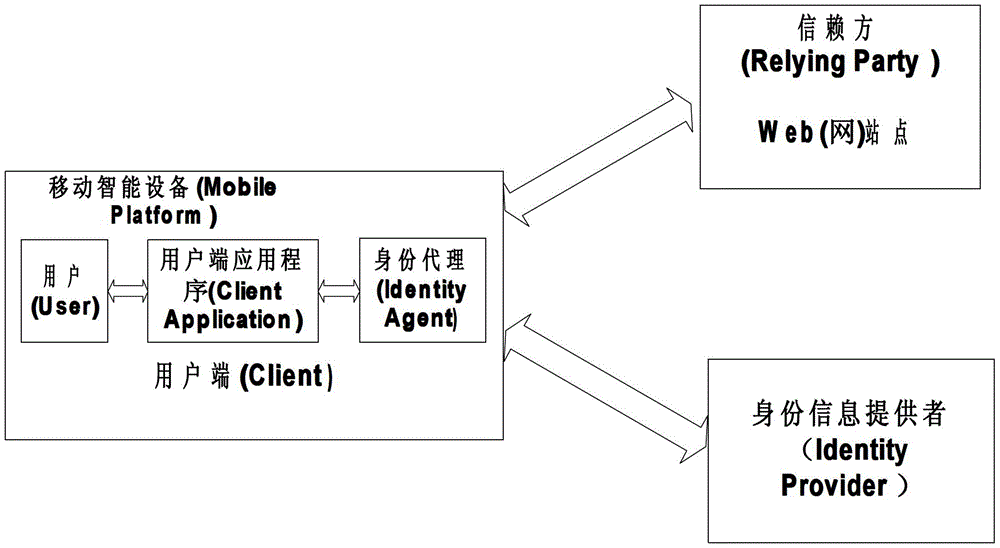
[0046] Such as figure 1 As shown, the operation of the embodiment involves three parties, and the specific operating system consists of a user (User), a client application (Client Application, usually referring to a browser), an identity agent (IdA, Identity Agent), an identity provider (Identity Provider, IdP ) and the Web site (Relying Party, RP) that the user pre-logs in. The user, client application, and identity agent belong to the client side, and the client application and identity agent are set on the client device (such as computer, mobile smart device Mobie Platform, etc.) used by the user. Any browser can be used as the browser, and IdA is an original setting of the present invention, which can be realized by computer software technology during specific implementation, such as on the Android system. RP and IdP are usually a w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com