Anti-phishing method and system
An anti-phishing and consistent technology, applied in the field of Internet security applications, can solve problems such as difficult to distinguish authenticity, achieve the effect of preventing phishing attacks and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below in conjunction with the accompanying drawings.
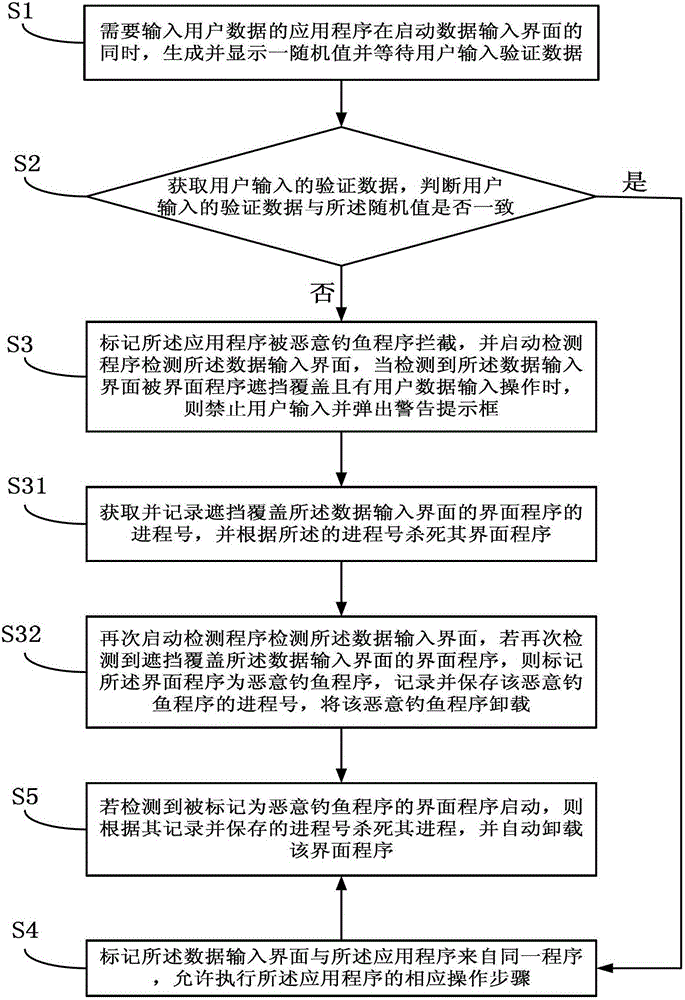
[0030] as attached figure 1 Shown, a kind of anti-phishing method, described method comprises:
[0031] S1. The application program that needs to input user data generates and displays a random value while starting the data input interface and waits for the user to input verification data;
[0032] S2. Obtain the verification data input by the user, and determine whether the verification data input by the user is consistent with the random value;
[0033] S3. When the verification data input by the user is inconsistent with the random value, mark the application program as being intercepted by a malicious phishing program, and start a detection program to detect the data input interface, when it is detected that the data input interface is blocked by the interface program When the cover is covered ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com