Method and system for protecting network attack
A network attack and network equipment technology, applied in the field of network communication, can solve the problems of increasing the workload of service personnel and poor maintainability, and achieve the effect of reducing human errors and workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
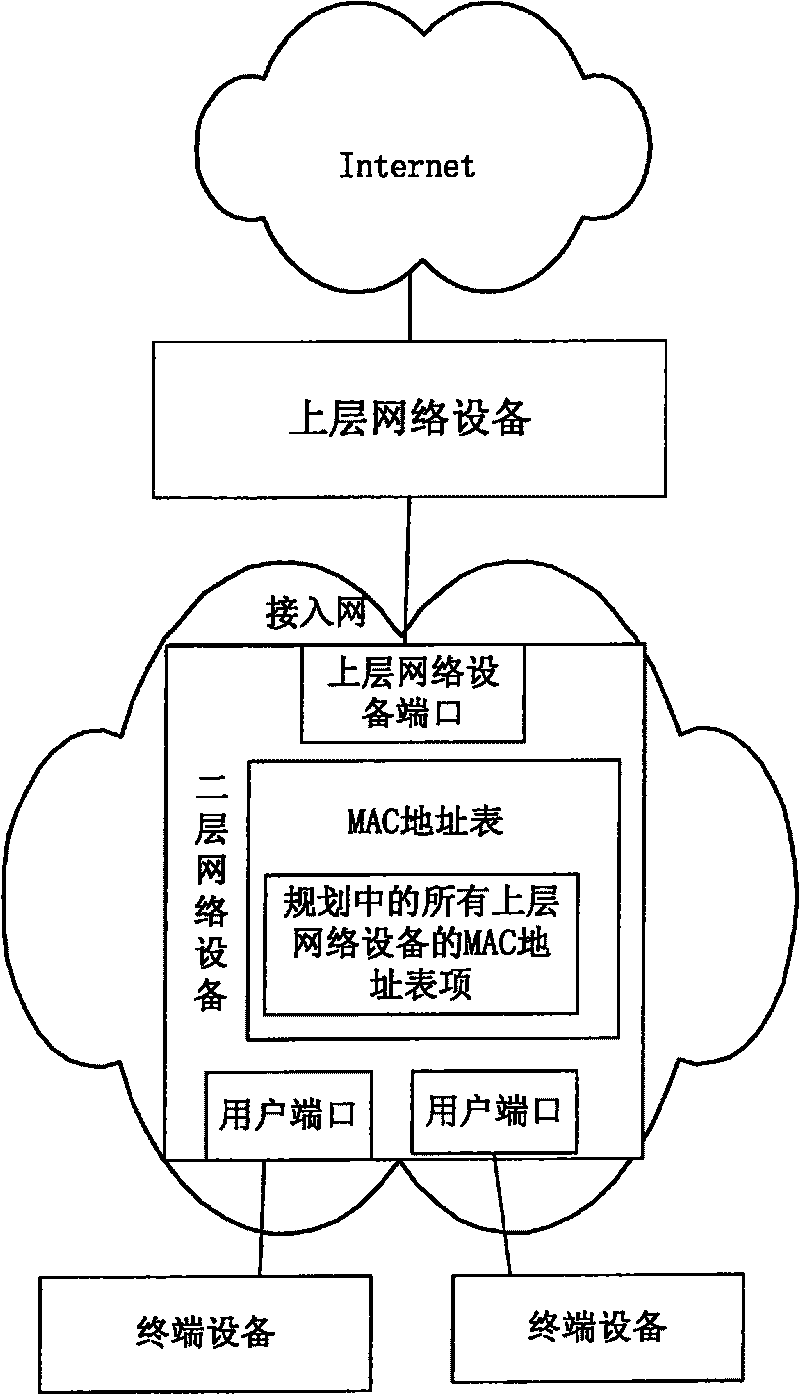
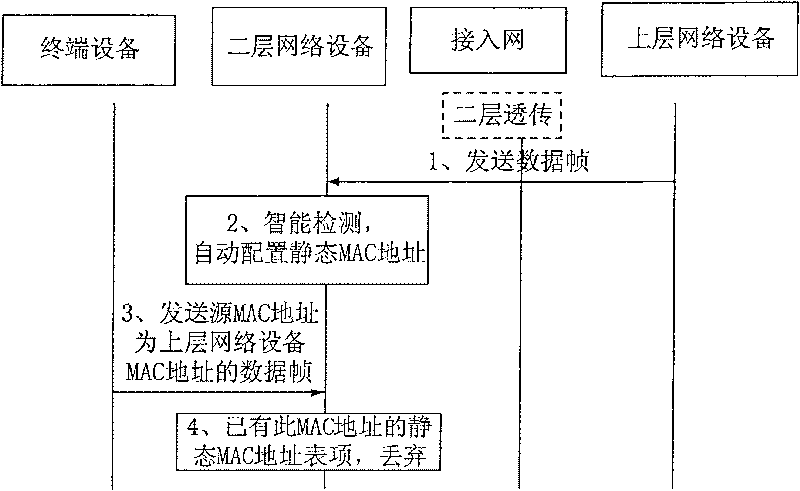
[0066] The core idea of the present invention is to pre-configure the port MAC address entries of all planned upper-layer network devices in the second-layer network equipment, and automatically configure static MAC address entries or Create a dynamic MAC address entry with a special identifier.
[0067] The present invention provides a system for preventing network attacks, such as figure 2 Shown is the framework diagram of the system of the present invention, by figure 2 It can be seen that the system of the present invention includes: a terminal device, a layer-2 network device and an upper-layer network device, and the described terminal device can be a terminal device of a legal user or an attacker's terminal device; the above-mentioned upper-layer network device It can be a three-layer switch, a router, etc.; the two-layer network device can be a bridge, a two-layer switch and a DSLAM; Send the data frame and send it to the destination address of the data frame thr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com