Method and device for mining cheating user
A technology for users and users, applied in the field of computer communication, it can solve the problems of uneven user level, high probability of cheating, and easy to miss.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
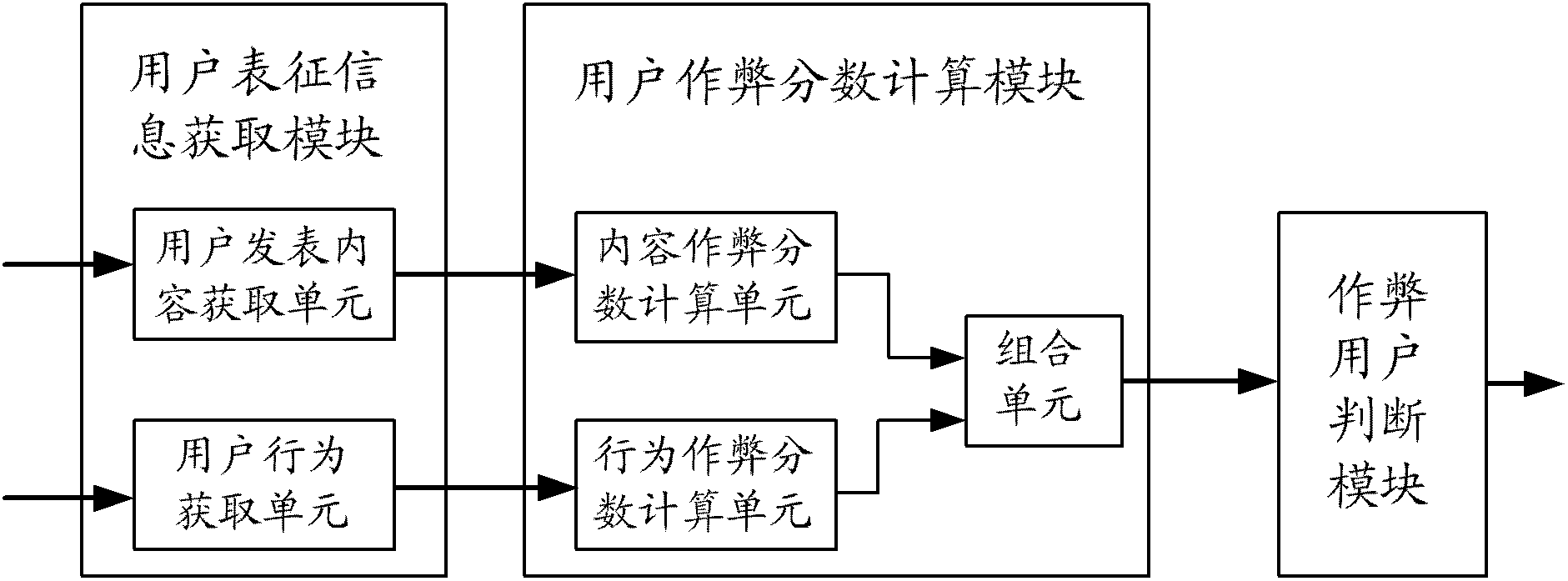
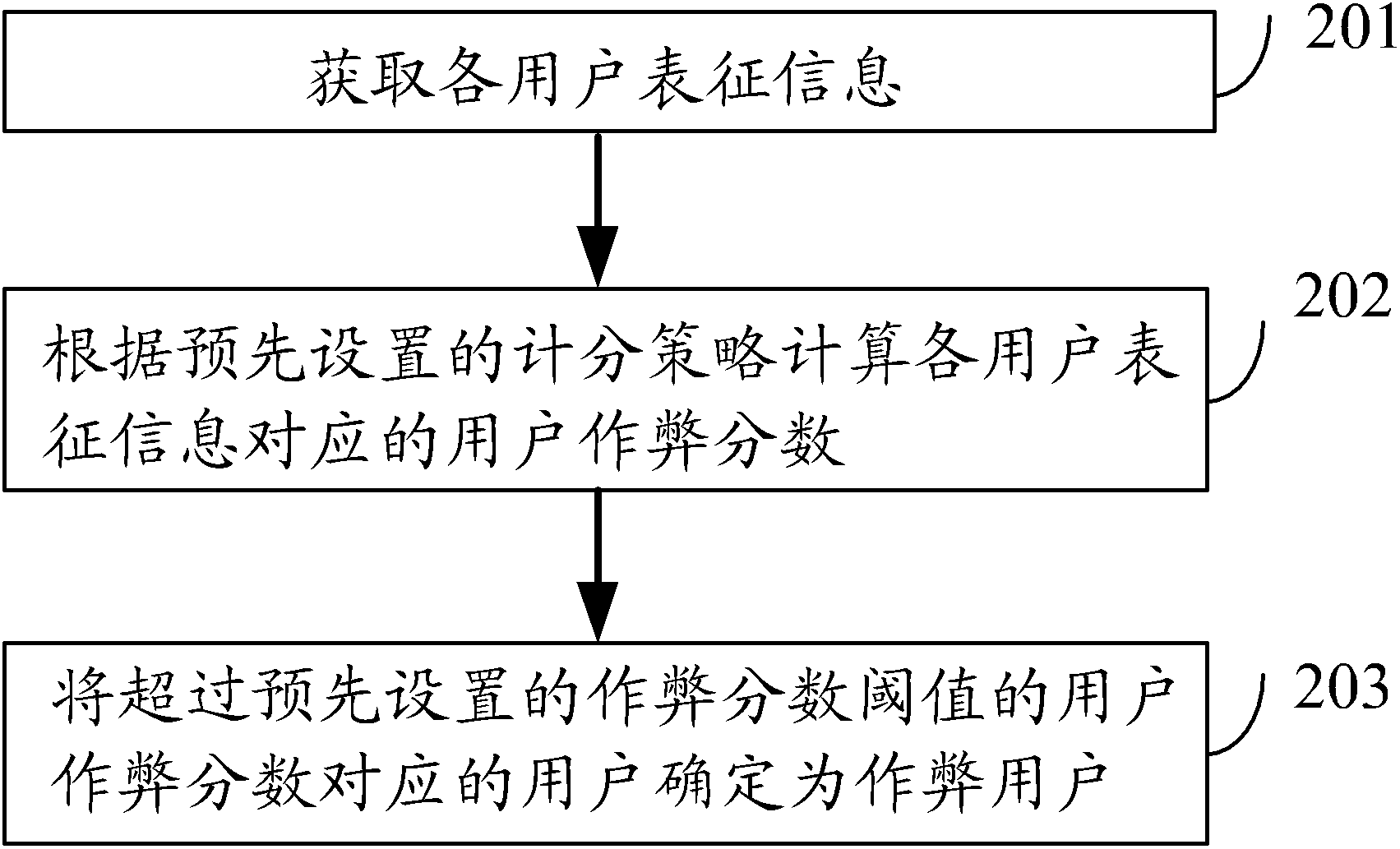
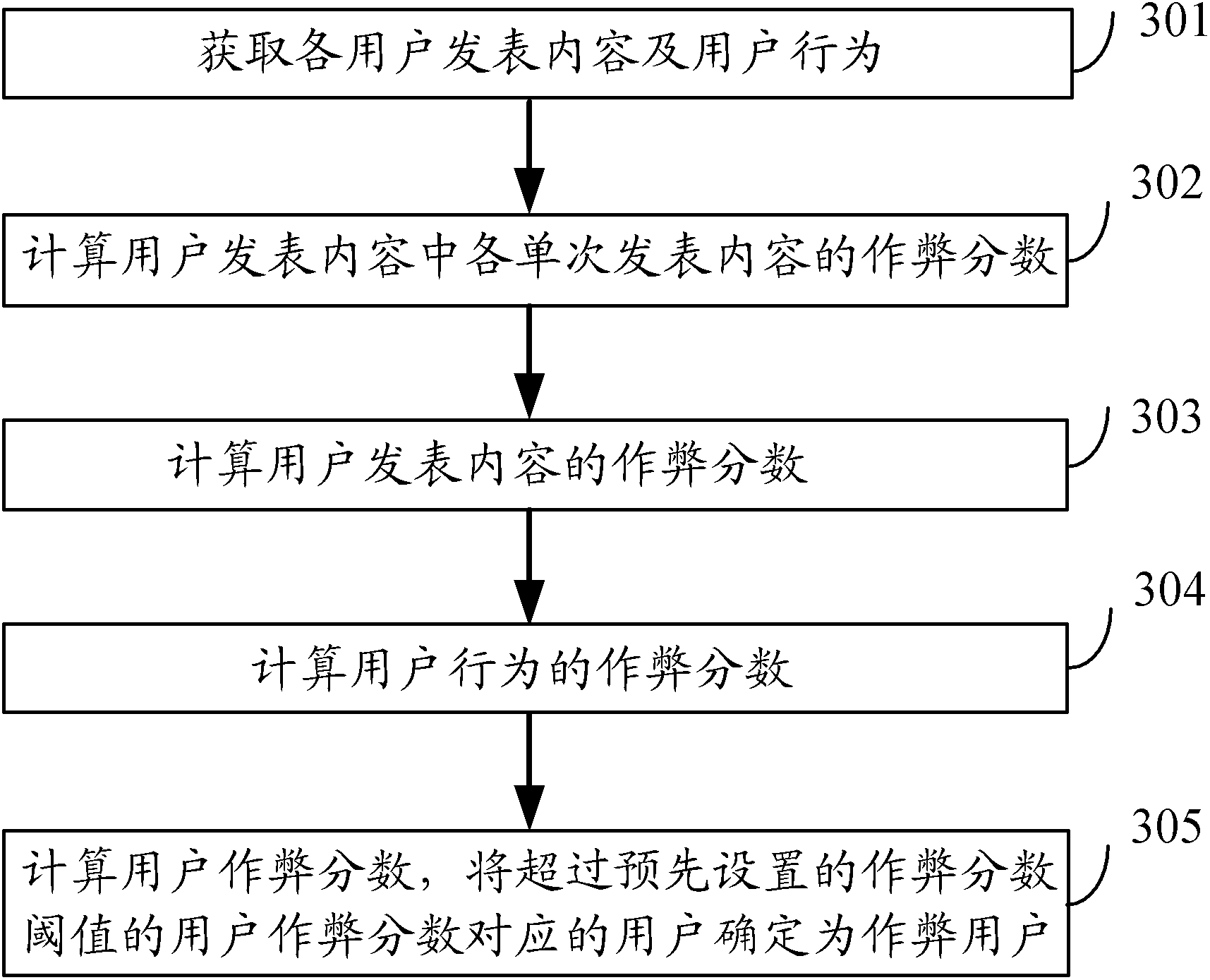
[0077] In view of the fact that the existing anti-cheating method based on webpage link analysis combined with detection and concealment technology in the community fails to effectively identify cheating users, in the embodiment of the present invention, a method for mining cheating users with users as the granularity is proposed, by comprehensively analyzing the published content of users, and / Or, user operation behaviors are used to mine cheating users, thereby reducing the probability of cheating users cheating, solving the problems of few data links in community web pages and low cost of creating cheating data, improving the anti-cheating efficiency of the community, and providing Anti-cheating method.
[0078] figure 1 It is a sche...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com