Processing method and processing device of timer
A processing method and timer technology, applied in the field of data processing, can solve problems such as large system overhead, achieve the effect of solving relatively large system overhead, reducing the number of executions, and reducing system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] figure 1 is a flowchart of a timer processing method according to an embodiment of the present application. Such as figure 1 As shown, the processing method of the timer includes:
[0033] Step S102, dividing the triggering time of the timer event into multiple time periods, wherein each time period corresponds to a hash value.
[0034] Preferably, when the trigger time of the timer event is converted into a hash value, it can also be converted according to the accuracy requirement. If the timer accuracy requirement is 1 second, the trigger time of the timer event adopts 32-bit binary data; if the timer accuracy is required to be 0.001 second, the trigger time of the timer event is represented by 64-bit binary data.
[0035] Step S104, inserting the timer events whose trigger time is in the same time period into the same linked list.
[0036] Preferably, the timer events belonging to the same hash value are inserted into the same linked list according to the time se...
Embodiment 2
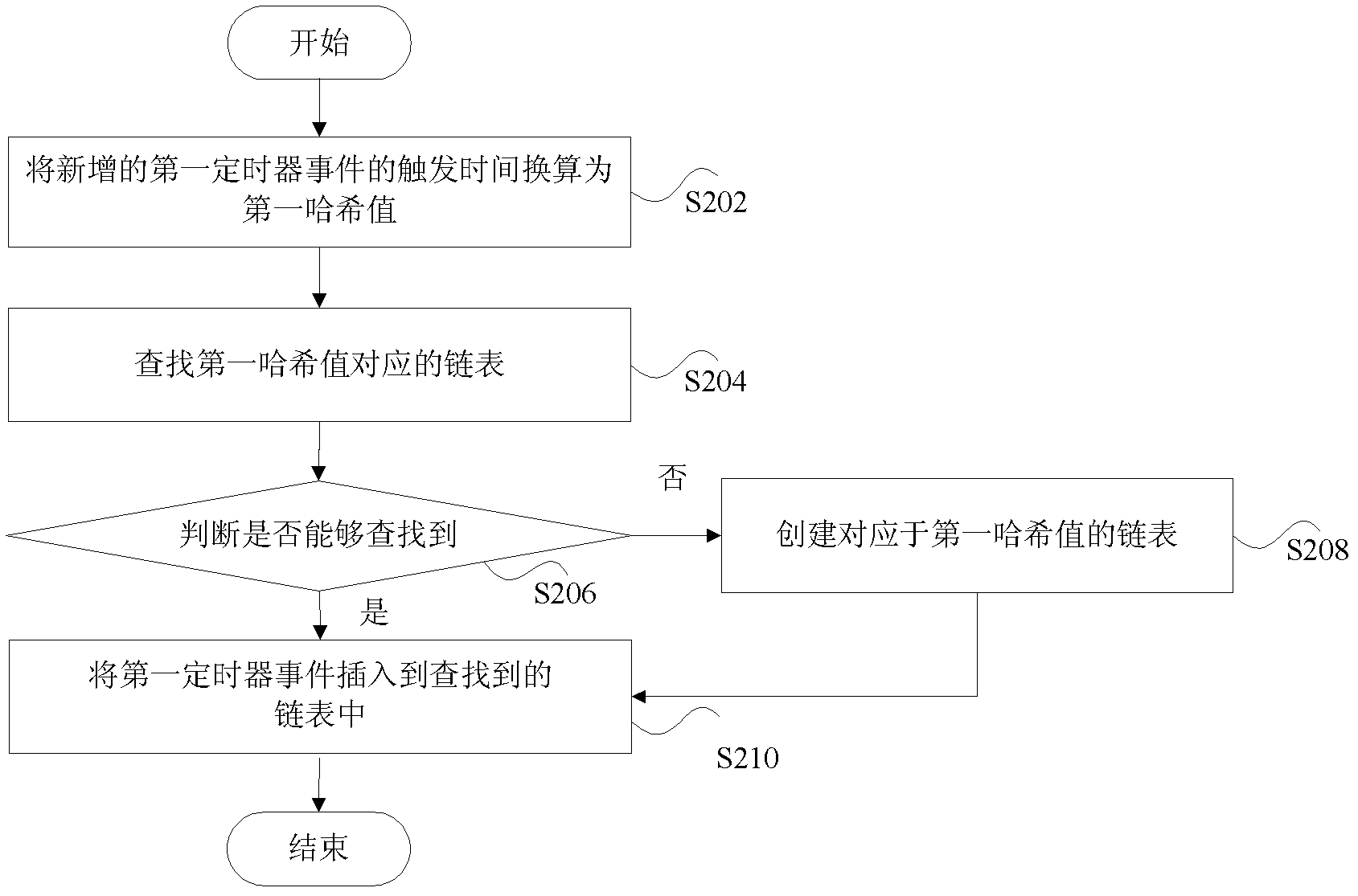
[0042] It should be noted that, the timer processing method in this embodiment may not only include a processing method for existing timer events, but may also include a processing method for newly added timer events. figure 2 That is, it is a flowchart of a method for processing a timer for a new timer event according to an embodiment of the present application.
[0043] Assuming that multiple timer events are newly added, here only the first timer event is added as an example for description, where the first timer event may be any timer event among the multiple newly added timer events. Specifically include the following steps:
[0044] Step S202, converting the triggering time of the first timer event into a first hash value.
[0045] Step S204, searching for a linked list corresponding to the first hash value.
[0046] Step S206, judging whether the linked list corresponding to the first hash value can be found, if the judging result is yes, go to step S210, otherwise g...
Embodiment 3
[0056] Based on the hash table obtained in Embodiment 1 or 2 above, each timer event in the linked list can be executed through scheduling. This embodiment provides a preferred way of scheduling timer events.
[0057] The scheduling process of the embodiment of the present application is described below, and the scheduling process includes the following steps:
[0058] Step S1, after mapping the timer events in each of the linked lists to the hash table, obtaining the current hash value corresponding to the current time period;
[0059] Step S2, looking up the identifier of the linked list corresponding to the current hash value in the hash table;
[0060] Step S3, execute the timer event in the linked list indicated by the identified identifier of the linked list.
[0061] For how to execute the timer event in the linked list indicated by the identified linked list, the present application provides several preferred implementation modes, which specifically include the follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com