Digital audio watermarking method capable of resisting re-recording attack
A watermarking and audio technology, used in speech analysis, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
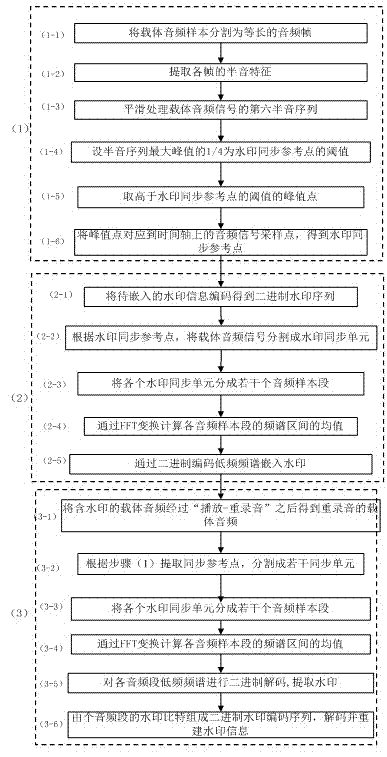
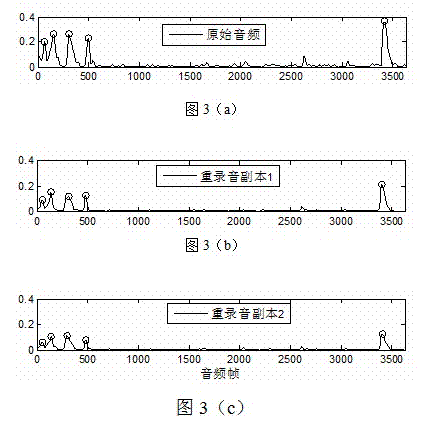
[0025] A kind of digital audio watermarking method of the present invention can resist re-recording attack, its process is as follows figure 1 As shown, the specific steps are as follows:
[0026] (1), Extract watermark synchronization reference point
[0027] (1-1) Divide the carrier audio signal into audio frames of equal length, and the number of audio frames is L, Each audio frame has B =256 sampling points;
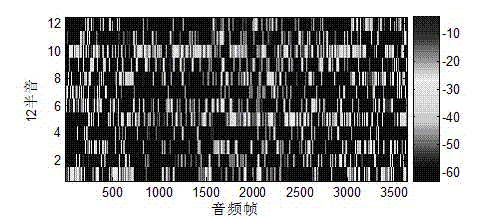
[0028] (1-2) Extract the semitone features of each audio frame: each audio frame is transformed by FFT to obtain the spectral component of each frame, and an octave centered at 1kHz is taken from the spectral component, and the frequency range of 707Hz~1414Hz contains 12 semitones , expressing the semitone feature sequence of the carrier audio signal as C i*j , i Indicates the number of frames, the range is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com